New Internet Protocol Standard That Would Help Centralize Internet Control in the Hands of the State
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tech Companies Call for 'Aggressive' NSA Reforms at White House Meeting
http://www.theguardian.com/world/2013/dec/17/techco mpaniescallaggressivensareformswhitehouse Tech companies call for 'aggressive' NSA reforms at White House meeting • Executives say programs have undermined user trust • White House had tried to gear meeting towards healthcare site [1] • Pressure mounts on day after judge's ruling against NSA Dominic Rushe in New York, Paul Lewis and Spencer Ackerman in Washington The Guardian, Tuesday 17 December 2013 17.24 EST President Obama vicepresident Joe Biden meet with executives from leading tech companies at the White House. Photograph: Michael Reynolds/EPA The top leaders from world’s biggest technology companies called on the US to "move aggressively" to reform the National Security Agency’s controversial surveillance operations after discussions with President Obama on Tuesday, resisting attempts by the White House to portray the encounter as covering a range of broader priorities. Executives from 15 companies, including Google, Apple, Yahoo and Twitter, used a facetoface meeting with Obama and vicepresident Joe Biden to express their concern that the NSA’s wideranging surveillance activities had undermined the trust of their users. The meeting came a day after a federal judge ruled that the NSA’s bulk collection of Americans’ phone records was “almost Orwellian” in scope and probably a violation of the US constitution [2]. Some of the tech companies represented at the White House have already expressed deep concern at the wideranging nature of NSA surveillance, and the way it apparently draws information from their systems without their knowledge. -
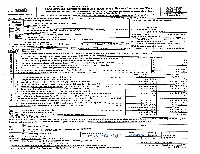
2012 Form 990 Or 990‐EZ
THE GERMAN MARSHALL FUND OF THE Form 990 (2012) UNITED STATES 52-0954751 Page 2 Part III Statement of Program Service Accomplishments Check if Schedule O contains a response to any question in this Part III X 1 Briefly describe the organization's mission: THE GERMAN MARSHALL FUND OF THE UNITED STATES (GMF) STRENGTHENS TRANSATLANTIC COOPERATION ON REGIONAL, NATIONAL, AND GLOBAL CHALLENGES AND OPPORTUNITIES IN THE SPIRIT OF THE MARSHALL PLAN. 2 Did the organization undertake any significant program services during the year which were not listed on the prior Form 990 or 990-EZ? ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Yes X No If "Yes," describe these new services on Schedule O. 3 Did the organization cease conducting, or make significant changes in how it conducts, any program services?~~~~~~ Yes X No If "Yes," describe these changes on Schedule O. 4 Describe the organization's program service accomplishments for each of its three largest program services, as measured by expenses. Section 501(c)(3) and 501(c)(4) organizations are required to report the amount of grants and allocations to others, the total expenses, and revenue, if any, for each program service reported. 4a (Code: ) (Expenses $ 7,315,551. including grants of $ 5,420,595. ) (Revenue $ ) CIVIL SOCIETY AND GRANT-MAKING GRANTMAKING IS ONE OF GMF'S CORE MISSIONS, AND THROUGH THIS PROCESS, GMF SUPPORTS A WIDE RANGE OF INSTITUTIONS AND INDIVIDUALS WORKING ON TRANSATLANTIC POLICY ISSUES. GMF AWARDS GRANTS PRIMARILY THROUGH FOUR MAJOR GRANTMAKING PROGRAMS - THE BALKAN TRUST FOR DEMOCRACY; THE BLACK SEA TRUST FOR REGIONAL COOPERATION; THE FUND FOR BELARUS DEMOCRACY; AND THE MIDDLE EAST AND NORTH AFRICA. -

Saving Multilateralism: Renovating the House of Global Economic
paper series saViNG MULTiLaTeraLisM RENOVATING THE HOUSE OF GLOBAL ECONOMIC GOVERNANCE FOR THE 21ST CENTURY JeNNifer HiLLMaN The German marshall Fund oF The uniTed sTaTes © 2010 The German Marshall Fund of the United States. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means without permission in writing from the German Marshall Fund of the United States (GMF). Please direct inquiries to: The German Marshall Fund of the United States 1744 R Street, NW Washington, DC 20009 T 1 202 683 2650 F 1 202 265 1662 E [email protected] This publication can be downloaded for free at http://www.gmfus.org/publications/index.cfm. Limited print copies are also available. To request a copy, send an e-mail to [email protected]. GMF Paper Series The GMF Paper Series presents research on a variety of transatlantic topics by staff, fellows, and partners of the German Marshall Fund of the United States. The views expressed here are those of the author and do not necessarily represent the view of GMF. Comments from readers are welcome; reply to the mailing address above or by e-mail to [email protected]. About GMF The German Marshall Fund of the United States (GMF) is a non-partisan American public policy and grant-making institu- tion dedicated to promoting greater cooperation and understanding between North America and Europe. GMF does this by supporting individuals and institutions working on transatlantic issues, by convening leaders to discuss the most pressing transatlantic themes, and by examining ways in which transatlantic cooperation can address a variety of global policy challenges. -

2004Letter from the President
A BOUT GMF he German Marshall Fund of the United States (GMF) is an American public policy and grantmaking institution Tdedicated to promoting greater cooperation and understanding between the United States and Europe. GMF does this by supporting individuals and institutions working on transatlantic issues, by convening leaders to discuss the most pressing transatlantic themes, and by examining ways in which transatlantic cooperation can address a variety of global policy challenges. In addition, GMF supports a number of initiatives to strengthen democracies. Founded in 1972 through a gift from Germany as a permanent memorial to Marshall Plan assistance, GMF maintains a strong presence on both sides of the Atlantic. In addition to its headquarters in Washington, DC, GMF has five offices in Europe: Belgrade, Berlin, Bratislava, Brussels, and Paris. TABLE OF CONTENTS 2004LETTER FROM THE PRESIDENT . .2 HIGHLIGHTS . .4 Marshall Forum on Transatlantic Affairs International Commission on the Balkans Transatlantic Trends 2004 Public Opinion Survey Trade and Poverty Forum Call to Action Transatlantic Speaker Series Turning an Eye to Turkey PROGRAM AREAS . .8 TRANSATLANTIC POLICY PROGRAM . .9 POLICY DIALOGUE . .9 NATO Summit Trade and Development Program Bundestag Forum on the United States Black Sea Conference Series U.S.–EU Summit Think Tank Symposium Wider Europe Conference Transatlantic Journalists Forum Frozen Conflicts SUPPORT FOR INSTITUTIONS . .16 Foreign Policy Key Institution Program Central and Eastern Europe Key Institution Program Immigration and Integration Key Institution Program SUPPORT FOR INDIVIDUALS . .18 Transatlantic Fellows Program Research Fellowship Program Journalism Fellowship Program TRANSATLANTIC LEADERS PROGRAM . .20 Marshall Memorial Fellowship Congress–Bundestag Forum Transatlantic Initiatives Fund Transatlantic Community Foundation Fellowship Journalism Study Tours APSA Congressional Fellowship Manfred Wörner Seminar STRENGTHENING DEMOCRACIES . -

Dhruva Jaishankar Fellow, Foreign Policy, Brookings India
Dhruva Jaishankar Fellow, Foreign Policy, Brookings India 6 Dr. Jose P. Rizal Marg, 2nd Floor, Chanakyapuri, New Delhi, 110021 India D: 91.11.2415.7772 | M: 91.92.0550.6701 | E: [email protected] @d_jaishankar djaishankar83 dhruvajaishankar EMPLOYMENT Brookings Institution India Center, New Delhi, India 2016-present Fellow, Foreign Policy S. Rajaratnam School of International Studies (RSIS), Singapore 2015-2016 Visiting Fellow, South Asia Program The German Marshall Fund of the United States (GMF), Washington DC, USA 2009-2016 Transatlantic Fellow, Asia Program (2012-present) Program Officer, Asia Program (2009-2012) The Brookings Institution, Washington DC, USA 2007-2009 Senior Research Assistant, 21st Century Defense Initiative (2009) Research Assistant, Foreign Policy Studies (2007-2009) CNN-IBN Television, New Delhi, India 2006 News Writer and Correspondent, World News Desk Edward N. Luttwak, Chevy Chase, Md., USA 2006 Research Assistant The Aspen Institute, Washington DC, USA 2005 Brent Scowcroft Award Fellow, Aspen Strategy Group EDUCATION Master of Arts in Security Studies (M.A.) 2011 Georgetown University, Washington DC, USA Edmund A. Walsh School of Foreign Service Concentration: International Security. Honors for Outstanding Academic Achievement, 2011. Security Studies Program Scholarship, 2009-2011. Bachelor of Arts (B.A.) 2005 Macalester College, Saint Paul, Minn., USA Majors: History & Classics. Minor: Geology. Yahya Armajani Endowed Prize in History, 2005. DeWitt Wallace Scholarship, 2001-2005. 1 SELECT CONFERENCE PRESENTATIONS AND LECTURES “India – and Indians – as Global Leaders,” O.P. Jindal School, Sonipat, Haryana, August 1, 2016. “India and the Liberal International Order,” New Zealand-India Research Institute and Victoria University of Wellington, New Zealand, June 8, 2016. -

Annual Report 2007
OFFICES Washington • Berlin • Bratislava • Paris Brussels • Belgrade • Ankara • Bucharest www.gmfus.org Annual Report 2007 The German Marshall Fund of the United States Board List (GMF) is a nonpartisan American public policy and Guido Goldman grantmaking institution dedicated to promoting greater Co-chair cooperation and understanding between the United States and Europe. Marc Leland Co-chair GMF does this by supporting individuals and institutions working on transatlantic issues, by convening leaders to Calvin Dooley discuss the most pressing transatlantic themes, and by Marc Grossman examining ways in which transatlantic cooperation can David Ignatius address a variety of global policy challenges. In addition, Nike Irvin GMF supports a number of initiatives to strengthen Scott Klug democracies. Roman Martinez IV Richard Powers Founded in 1972 through a gift from Germany as a J. Thomas Presby permanent memorial to Marshall Plan assistance, GMF John Ross maintains a strong presence on both sides of the Atlantic. Barbara Shailor In addition to its headquarters in Washington, DC, GMF Amity Shlaes has seven offices in Europe: Berlin, Bratislava, Paris, Jenonne Walker Brussels, Belgrade, Ankara, and Bucharest. J. Robinson West Suzanne Woolsey Leah Zell Wanger Craig Kennedy President Illustrations by Brian Hubble Table of Contents 2 Letter from the President 30 Grantmaking Black Sea Trust Launch 4 Convening Balkan Trust for Democracy Brussels Forum Trust for Civil Society in Central and Eastern Europe Marshall Plan 60th Anniversary Foreign -

Key Findings 2005 Transatlantic Trends 2005 Partners
Key Findings 2005 Transatlantic Trends 2005 Partners 1985 © © 2005 Methodology: TNS Opinion & Social was commissioned to conduct the survey using Computer Assisted Telephone Interviews in all countries except Poland, Slovakia, and Turkey, where lower telephone penetration necessitated the use of face-to-face interviews. In all countries a random sample of approximately 1,000 men and women, 18 years of age and older, were interviewed. Interviews were conducted between May 30, 2005 and June 17 2005. For results based on the total national sample in each of the 11 countries surveyed, one can say with 95% confidence that the margin of error attributable to sam- pling and other random effects is plus or minus 3 percentage points. For results based on the total European sample, the margin of margin of error is plus or minus 1 percentage point. The average response rate for the eleven countries surveyed was 24.6%. Europe-wide figures are weighted on the basis of the size of the adult population in each country. The 2004 and 2005 Europe 9 averages (EU9) represents the com- bined responses of France, Germany, Italy, the Netherlands, Poland, Portugal, Slovakia, Spain, and the United Kingdom, while the Europe 10 average (E10) represents responses from these same countries plus Turkey. The Europe-wide average from 2002 (EU6)was constructed using responses from France, Germany, Italy, the Netherlands, Poland, and the United Kingdom, while the 2003 Europe-wide average, also referred to as the Europe-7 average (EU7), uses responses from these same countries plus Portugal. For ease of presentation both the EU6 and EU7 averages are listed as part of the Europe 9 average throughout the text. -

2 0 0 6 a N N U a L R E P O
WASHINGTON, DC 1744 R Street NW Washington, DC 20009 T 1 202 745 3950 F 1 202 265 1662 E [email protected] BERLIN Oranienburger Str. 13/14 10178 Berlin, Germany T 49 30 28 88 13 0 F 49 30 28 88 13 10 BRATISLAVA Transatlantic Center for Central and Eastern Europe Štúrova 3 811 02 Bratislava, Slovak Republic T 421 2 5931 1522 F 421 2 5931 1405 PARIS 30 rue Galilée 75116 Paris, France T 33 1 47 23 47 18 F 33 1 47 23 48 16 BRUSSELS Transatlantic Center Résidence Palace Rue de la Loi 155 Wetstraat 1040 Brussels, Belgium T 32 2 238 5270 F 32 2 238 5299 BELGRADE Balkan Trust for Democracy Dobraˇcina 44 11000 Belgrade, Republic of Serbia T 381 11 30 36 454 F 381 11 32 88 022 ANKARA 2006 ANNUAL REPORT Tunus Cad. No.15/4 Kavaklıdere 06680 Ankara, Turkey T 90 312 425 6677 F 90 312 425 3399 www.gmfus.org THE GERMAN MARSHALL FUND OF THE UNITED StATES (GMF) is a nonpartisan American public policy and grantmaking institution dedicated to promoting greater cooperation and understanding between the United States and Europe. GMF does this by supporting individuals and institutions working on transatlantic issues, by convening leaders to discuss the most pressing transatlantic themes, and by examining ways in which transatlantic cooperation can address a variety of global policy challenges. In addition, GMF supports a number of initiatives to strengthen democracies. Founded in 1972 through a gift from Germany as a permanent memorial to Marshall Plan assistance, GMF maintains a strong presence on both sides of the Atlantic. -

GMF3732 Annual Report
2003 A B OUT GMF he German Marshall Fund of the United States (GMF) is an American public policy and grantmaking institution dedicated Tto promoting greater cooperation and understanding between the United States and Europe. GMF does this by supporting individuals and institutions working on transatlantic issues, by convening leaders to discuss the most pressing transatlantic themes, and by examining ways in which transatlantic cooperation can address a variety of global policy challenges. All GMF activities are organized within three principal program areas: Transatlantic Policy, Transatlantic Leaders, and Wider Europe. In addition, GMF has developed a strong Central and Eastern Europe program aimed at furthering democratic consolidation and promoting integration into European and transatlantic institutions. Founded in 1972 through a gift from Germany as a permanent memorial to Marshall Plan assistance, GMF maintains a strong presence on both sides of the Atlantic. In addition to its headquarters in Washington, DC, GMF has five offices in Europe: Belgrade, Berlin, Bratislava, Brussels, and Paris. 2003TABLE OF CONTENTS LETTER FROM THE PRESIDENT . .2 HIGHLIGHTS . .4 Transatlantic Trends 2003 U.S.–EU Think Tank Symposium Balkan Trust for Democracy Peter R. Weitz Journalism Prizes Strategic Discussion with Henry Kissinger GMF Transatlantic Center in Brussels Trade and Poverty Forum Inaugurated PROGRAM AREAS . .8 TRANSATLANTIC POLICY PROGRAM . .9 POLICY DIALOGUE . .9 Transatlantic Trends 2003 Public Opinion Survey Trade and Poverty Forum Bundestag Forum on the United States Agriculture, Genetically Modified Organisms, and Trade Tremezzo Meeting SUPPORT FOR INSTITUTIONS . .12 Foreign Policy Key Institution Program Central and Eastern Europe Key Institution Program Immigration and Integration Key Institution Program SUPPORT FOR INDIVIDUALS . -

Download the Full
Transatlantic 360 Take Photo: J.S. Photographer Looking Ahead to the German Elections GMF Experts From Across the Atlantic On Their Expectations For The New Bundestag Americans only have eyes for Angela Merkel. When Washington: American leadership is not always a we look across the Atlantic at the German election, given. An opening has been created, and it is up to we cannot imagine that anyone other than Merkel the next German chancellor to grab it. could lead Europe’s most powerful economy. Merkel has become the indispensable European. Paris: Merkel has lost a liberal ally and gained adversaries. She understands that there is no Merkel looks poised to glide to victory on September alternative to the political partnership with Macron. 24 and secure a fourth term in office. Even if she succeeds, we would be mistaken to assume that Brussels: There is a striking difference between German politics is static. Merkel’s dominance of the expectations for a new German government Germany’s highest office masks a shifting political and the reality of the campaigns. The risk is that landscape with a record seven parties likely to be Merkel will continue to muddle-through. represented in Parliament. Ankara: Turkey has played a surprisingly prominent Assuming the CDU is the big winner later this role in the last months of the campaign. Ankara is month, Merkel will set out to build a new coalition. waiting to see if rhetoric will become reality. Some argue that the path of least resistance would be Bucharest: Romania expects the new German for Merkel to restart another Grand Coalition. -

Microsoft Ecosystem Phone: (425) 882-8080
Microsoft Corporation 1 Microsoft Way, Redmond, WA, 98052 Microsoft Ecosystem Phone: (425) 882-8080 www.microsoft.com Outside Relationships Microsoft Corporation (Washington Corporation) Securities Outside Relationships Regulation and Regulators Regulators Capital Suppliers Customers Equity Structure NASDAQ Listing Customers Suppliers Capital DebtDebt StructureStructure Debt ( $63.3B @ 6/30/20) Credit Ratings: Aaa (Moody’s), AAA (S&P) Rules Bond Equity Securities Bond Financing 2039 Notes: $559M @ 5.20% 2022-2042 Notes: $1,650M @ 2.13-3.50% 2021-2056 Notes: $16,955M @ 1.55-3.95% Dividends and Common Significant Regulators Common Stock Share Repurchase Program Holders 2023-2043 Notes: $2,919M @ 2.38-4.88% Stock Repurchases Shareholders Authorized: 24 Billion Shares Authorized: $40 Billion US Securities 2020-2040 Notes: $1,571M @ 3.00-4.50% 2022-2057 Notes: $12,385M @ 2.40-4.50% Vanguard 2021-2033 Notes: $4,549M @ 2.13-3.13% Equity and Outstanding: 7.57 Billion Shares Available: $31.7 Billion Group Capital Exchange 2021-2041 Notes: $1,270M @ 4.00-5.30% 2020-2055 Notes: $15,549M @ 2.00-4.75% 2050-2060 Notes: $10,000M @ 2.53-2.68% Recordholders: 91,674 Expiration: None (7.70%) Commission BlackRock Fund The NASDAQ GovernanceGovernance Corporate Matters Advisors Stock Market Board of Directors Human Resources Sales and Finance and Legal (4.55%) John W. Thompson (Chair) Satya Nadella John W. Stanton (A, RPP) SSgA Funds Compensation & Benefits Marketing Accounting Cyber Security Management Reid G. Hoffman Sandra E. Peterson (C, GN) Emma N. Walmsley (C, R) Strategic Planning Acquisitions (3.97%) Culture Privacy Hugh F. Johnston (A) Penny S. -

Microsoft: New Wine in an Old Bottle?
HK1039 ALI FARHOOMAND MICROSOFT: NEW WINE IN AN OLD BOTTLE? Within four weeks of becoming the new CEO of Microsoft, Satya Nadella laid out the major challenges that awaited him in the two letters he sent to everyone at Microsoft.1 He defined Microsoft’s battlefield as the “mobile-first and cloud-first world.” 2 That was where Microsoft needed to get its products and technology right, to build platforms and ecosystems and to integrate Nokia devices, services and the new mobile capabilities. In order to do so, Microsoft needed to zero in on a mobile and cloud-first world and do new things. In his view, “industry does not respect tradition – it only respects innovation.” And in order to innovate, he needed his 130,000-strong staff around the world to lead and help drive cultural change, to find Microsoft’s swing so that the team was “in such perfect unison that no single action by any one is out of synch with those of all the others.”3 Many challenges awaited Microsoft in its transformative journey. On platforms, the future of Windows was not clear. On devices, Microsoft needed to find ways to woo application developers to build its mobile ecosystem. On integration, the company had to find ways to transfer and to grow the mobile capability acquired from Nokia. And most importantly, Nadella had to figure out how he could achieve cultural changes to focus everyone on innovation via collaboration. The Business Legacy Business Performance When Steve Ballmer retired, he left behind a record high revenue year in 2013 but a trail of sluggish stock performance [see Exhibit 1 for the company’s revenue and net income figures 1 Nadella, S.