Stability and Arms Control in Europe: the Role of Military Forces Within a European Security System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Analysis of Conditions for Danish Defence Policy – Strategic Choices
centre for military studies university of copenhagen An Analysis of Conditions for Danish Defence Policy – Strategic Choices 2012 This analysis is part of the research-based services for public authorities carried out at the Centre for Military Studies for the parties to the Danish Defence Agreement. Its purpose is to analyse the conditions for Danish security policy in order to provide an objective background for a concrete discussion of current security and defence policy problems and for the long-term development of security and defence policy. The Centre for Military Studies is a research centre at the Department of —Political Science at the University of Copenhagen. At the centre research is done in the fields of security and defence policy and military strategy, and the research done at the centre forms the foundation for research-based services for public authorities for the Danish Ministry of Defence and the parties to the Danish Defence Agreement. This analysis is based on research-related method and its conclusions can —therefore not be interpreted as an expression of the attitude of the Danish Government, of the Danish Armed Forces or of any other authorities. Please find more information about the centre and its activities at: http://cms.polsci.ku.dk/. References to the literature and other material used in the analysis can be found at http://cms.polsci.ku.dk/. The original version of this analysis was published in Danish in April 2012. This version was translated to English by The project group: Major Esben Salling Larsen, Military Analyst Major Flemming Pradhan-Blach, MA, Military Analyst Professor Mikkel Vedby Rasmussen (Project Leader) Dr Lars Bangert Struwe, Researcher With contributions from: Dr Henrik Ø. -

Vs - Nur Für Den Dienstgebrauch
VS - NUR FÜR DEN DIENSTGEBRAUCH NATO UNCLASSIFIED NATO UNCLASSIFIED Foreword The term “counterinsurgency” (COIN) is an The document is divided into three parts: emotive subject in Germany. It is generally • Part A provides the basic conceptual accepted within military circles that COIN is an framework as needed to give a better interagency, long-term strategy to stabilise a crises understanding of the broader context. It region. In this context fighting against insurgents specifically describes the overall interagency is just a small part of the holistic approach of approach to COIN. COIN. Being aware that COIN can not be achieved successfully by military means alone, it • Part B shifts the focus to the military is a fundamental requirement to find a common component of the overall task described sense and a common use of terms with all civil previously. actors involved. • Part C contains some guiding principles to However, having acknowledged an Insurgency to stimulate discussions as well as a list of be a group or movement or as an irregular activity, abbreviations and important reference conducted by insurgents, most civil actors tend to documents. associate the term counterinsurgency with the combat operations against those groups. As a The key messages of the “Preliminary Basics for the Role of the Land Forces in COIN“ are: result they do not see themselves as being involved in this fight. For that, espescially in • An insurgency can not be countered by Germany, the term COIN has been the subject of military means alone. much controversy. • Establishing security and state order is a long- Germany has resolved this challenge with two term, interagency and usually multinational steps. -
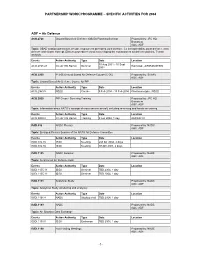
ADF = Air Defence
PARTNERSHIP WORK PROGRAMME – SPECIFIC ACTIVITIES FOR 2004 ADF = Air Defence ACO.2728 Ground Based Air Defence (GBAD) Planning Seminar Proposed by: JFC HQ Brunssum AOC: ADF Topic: GBAD mission planning to include employment principles, joint doctrine, C2 interoperability, point defence, area defence and cluster concept. Discuss procedures used in developing the commanders air defence policies. Terrain analysis. Events Action Authority Type Date Location 30 Aug 2004 - 10 Sept ACO.2728.24 CC-Air HQ Ramst Seminar Halmstad , AIR/RAMSTEIN 2004 ACO.2960 P-3-06 Ground Based Air Defence Course (C-06) Proposed by: SHAPE AOC: ADF Topic: Ground Based Air Defence Course for PfP Events Action Authority Type Date Location ACO.2960.5 NS(S) Course 9 Feb 2004 - 13 Feb 2004 Oberammergau , NS(S) ACO.3009 PfP Cross - Servicing Training Proposed by: JFC HQ Brunssum AOC: ADF Topic: Information about NATO's concept of cross-service aircraft, including re-arming and hands-on training. Events Action Authority Type Date Location ACO.3009.2 CC-Air HQ Ramst Training 9 Jun 2004, 1 day AIRNORTH IS/DI.932 NADC Plenary Proposed by: NADC AOC: ADF Topic: Enlarged Plenary Session of the NATO Air Defence Committee Events Action Authority Type Date Location IS/DI.932.15 IS/DI Meeting 2nd Qtr 2004, 2 days IS/DI.932.16 IS/DI Meeting 4th Qtr 2004, 2 days IS/DI.1155 NADC Seminar Proposed by: NADC AOC: ADF Topic: Seminar on Air Defence topic Events Action Authority Type Date Location IS/DI.1155.11 IS/DI Seminar TBD 2004, 1 day IS/DI.1155.12 IS/DI Seminar TBD 2004, 1 day IS/DI.1191 -

Academic Studies for Officers
University VIENNA and National Defense Academy VIENNA Academic Studies for Officers A Central European Perspective (Presentations of the First International Conference in Vienna, 15 – 19 March 1999) Published by Brigadier-General Gernot ALBRECHT Vienna, April 2001 SUMMARY OF CONTENTS WOLFGANG GREISENEGGER..................................................3 Welcome Address......................................................................................3 ERNEST KÖNIG..........................................................................5 Welcome Address......................................................................................5 GERNOT ALBRECHT .................................................................9 Opening Statement....................................................................................9 ARMIN A. STEINKAMM ............................................................10 The Bundeswehr University [UDBW]..................................................10 JÖRG E. P. KELLER.................................................................17 Academic Officer Training within and for the Armed Forces – a German Perspective ....................................................................................................................17 BEAT A. KÄCH .........................................................................32 The Swiss Military College ....................................................................32 ALTERO FASANO.....................................................................43 -

CPPB Training Providers
CPPB Training Providers Country Organisation Website Armenia Civic Forum http://www.civicforum.am/ Armenia Eurasia Partnership Foundation Armenia http://www.epfarmenia.am/en/ Armenia Regional Studies Center http://regional-studies.org Armenia Society Without Violence http://www.swv.am/index.php/en/#.WEbpvPmLTIV Austria Austrian Armed Forces International Centre www.autint.at Austria Austrian Study Centre for Peace and Conflict Resolution http://www.aspr.peacecastle.eu/ Austria Federal Ministry of Interior - Austria https://www.bmi.gv.at/ Austria Federal Ministry of Interior - Austria, Security Academy https://www.bmi.gv.at/104/start.aspx Austria Human Rights and Research Centre for Human Rights and Democracy www.etc-graz.at/typo3/index.php?id=81 Austria OSCE POLIS https://polis-learn.osce.org/courses Azerbaijan Karuna Center for Peacebuilding http://www.karunacenter.org/our-work.html Azerbaijan NATO International School of Azerbaijan http://www.nisa.az/ Belgium Egmont Royal Institute for International Relations http://www.egmontinstitute.be/ Belgium European Centre for Electoral Support http://www.eces.eu/ Belgium European Security and Defence College https://eeas.europa.eu/topics/common-security-and-defence-policy-csdp/4369 Belgium National Politieacademie (International Training Department) http://police.ac.be/app/html/nl_over.html Belgium Protection International http://protectioninternational.org/what-we-do/capacity-building/ Belgium Royal Higher Institute for Defence http://www.irsd.be/website/ Belgium International Center for Transitional -

Finnish Defence Forces International Centre the Many Faces of Military
Finnish Defence Forces International Finnish Defence Forces Centre 2 The Many Faces of Military Crisis Management Lessons from the Field Edited by Mikaeli Langinvainio Finnish Defence Forces FINCENT Publication Series International Centre 1:2011 1 FINNISH DEFENCE FORCES INTERNATIONAL CENTRE FINCENT PUBLICATION SERIES 1:2011 The Many Faces of Military Crisis Management Lessons from the Field EDITED BY MIKAELI LANGINVAINIO FINNISH DEFENCE FORCES INTERNATIONAL CENTRE TUUSULA 2011 2 Mikaeli Langinvainio (ed.): The Many Faces of Military Crisis Management Lessons from the Field Finnish Defence Forces International Centre FINCENT Publication Series 1:2011 Cover design: Harri Larinen Layout: Heidi Paananen/TKKK Copyright: Puolustusvoimat, Puolustusvoimien Kansainvälinen Keskus ISBN 978–951–25–2257–6 ISBN 978–951–25–2258–3 (PDF) ISSN 1797–8629 Printed in Finland Juvenens Print Oy Tampere 2011 3 Contents Jukka Tuononen Preface .............................................................................................5 Mikaeli Langinvainio Introduction .....................................................................................8 Mikko Laakkonen Military Crisis Management in the Next Decade (2020–2030) ..............................................................12 Antti Häikiö New Military and Civilian Training - What can they learn from each other? What should they learn together? And what must both learn? .....................................................................................20 Petteri Kurkinen Concept for the PfP Training -

Defence White Paper of the Republic of Slovenia
DEFENCE WHITE PAPER OF THE REPUBLIC OF SLOVENIA 2020 Dear Readers, Both in everyday life, and in the operation and development of a country, we occasio- nally need to stop and strategically assess our efforts to see whether they are leading towards the desired objective. The result of our strategic reflection is the Defence White Paper of the Republic of Slovenia, which represents a high level of consistency of views within the defence sector on the future security environment, and on the necessary measures to enhance the country's defence capacity, taking into account real human, economic and other capabilities. The purpose of the Defence White Paper is to define a gradual long-term development of the Republic of Slovenia’s defence system in order to ensure the necessary levels of capacity and preparedness for the implementation of national defence, and the fulfilment of the adopted international obligations. I believe that, through diligent work and analysis, we have acquired a good basis for directing the further development of the defence system, which will be able to function effectively and in accordance with its mission. This document provides guidance for the change, reform and strengthening of both military and non-military defence mechanisms to meet the contemporary security challenges. It provides the starting point for the preparation of planning documents which will specify the key defence objectives by 2035, and the way they are implemented. The security of the country and its citizens is not self-evident and should not be taken for granted. It is a benefit and a value that is directly related to the existence of a nation, a government, a democratic system, the sovereignty of a state, the protection of one's identity, the exercise of human rights, and other interests of nations and states. -

The Evolution of U.S. Military Policy from the Constitution to the Present
C O R P O R A T I O N The Evolution of U.S. Military Policy from the Constitution to the Present Gian Gentile, Michael E. Linick, Michael Shurkin For more information on this publication, visit www.rand.org/t/RR1759 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-0-8330-9786-6 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2017 RAND Corporation R® is a registered trademark. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface Since the earliest days of the Republic, American political and military leaders have debated and refined the national approach to providing an Army to win the nation’s independence and provide for its defense against all enemies, foreign and domestic. -

Three Theories of Just War: Understanding Warfare As a Social Tool Through Comparative Analysis of Western, Chinese, and Islamic Classical Theories of War
THREE THEORIES OF JUST WAR: UNDERSTANDING WARFARE AS A SOCIAL TOOL THROUGH COMPARATIVE ANALYSIS OF WESTERN, CHINESE, AND ISLAMIC CLASSICAL THEORIES OF WAR A THESIS SUBMITTED TO THE GRADUATE DIVISION OF THE UNIVERSITY OF HAWAI‘I AT MĀNOA IN PARTIAL FULFILMENT OF THE REQUIREMENT FOR THE DEGREE OF MASTER OF ARTS IN PHILOSOPHY MAY 2012 By Faruk Rahmanović Thesis Committee: Tamara Albertini, Chairperson Roger T. Ames James D. Frankel Brien Hallett Keywords: War, Just War, Augustine, Sunzi, Sun Bin, Jihad, Qur’an DEDICATION To my parents, Ahmet and Nidžara Rahmanović. To my wife, Majda, who continues to put up with me. To Professor Keith W. Krasemann, for teaching me to ask the right questions. And to Professor Martin J. Tracey, for his tireless commitment to my success. 1 ABSTRACT The purpose of this analysis was to discover the extent to which dictates of war theory ideals can be considered universal, by comparing the Western (European), Classical Chinese, and Islamic models. It also examined the contextual elements that drove war theory development within each civilization, and the impact of such elements on the differences arising in war theory comparison. These theories were chosen for their differences in major contextual elements, in order to limit the impact of contextual similarities on the war theories. The results revealed a great degree of similarities in the conception of warfare as a social tool of the state, utilized as a sometimes necessary, albeit tragic, means of establishing peace justice and harmony. What differences did arise, were relatively minor, and came primarily from the differing conceptions of morality and justice within each civilization – thus indicating a great degree of universality to the conception of warfare. -

Civilians in Cyberwarfare: Conscripts
Civilians in Cyberwarfare: Conscripts Susan W. Brenner* with Leo L. Clarke** ABSTRACT Civilian-owned and -operated entities will almost certainly be a target in cyberwarfare because cyberattackers are likely to be more focused on undermining the viability of the targeted state than on invading its territory. Cyberattackers will probably target military computer systems, at least to some extent, but in a departure from traditional warfare, they will also target companies that operate aspects of the victim nation’s infrastructure. Cyberwarfare, in other words, will penetrate the territorial borders of the attacked state and target high-value civilian businesses. Nation-states will therefore need to integrate the civilian employees of these (and perhaps other) companies into their cyberwarfare response structures if a state is to be able to respond effectively to cyberattacks. While many companies may voluntarily elect to participate in such an effort, others may decline to do so, which creates a need, in effect, to conscript companies for this purpose. This Article explores how the U.S. government can go about compelling civilian cooperation in cyberwarfare without violating constitutional guarantees and limitations on the power of the Legislature and the Executive. * NCR Distinguished Professor of Law and Technology, University of Dayton School of Law. ** Associate, Drew, Cooper & Anding, P.C., Grand Rapids, Michigan. 1011 1012 Vanderbilt Journal of Transnational Law [Vol. 43:1011 TABLE OF CONTENTS I. INTRODUCTION ............................................................. -

US Military Policy in the Middle East an Appraisal US Military Policy in the Middle East: an Appraisal
Research Paper Micah Zenko US and Americas Programme | October 2018 US Military Policy in the Middle East An Appraisal US Military Policy in the Middle East: An Appraisal Contents Summary 2 1 Introduction 3 2 Domestic Academic and Political Debates 7 3 Enduring and Current Presence 11 4 Security Cooperation: Training, Advice and Weapons Sales 21 5 Military Policy Objectives in the Middle East 27 Conclusion 31 About the Author 33 Acknowledgments 34 1 | Chatham House US Military Policy in the Middle East: An Appraisal Summary • Despite significant financial expenditure and thousands of lives lost, the American military presence in the Middle East retains bipartisan US support and incurs remarkably little oversight or public debate. Key US activities in the region consist of weapons sales to allied governments, military-to-military training programmes, counterterrorism operations and long-term troop deployments. • The US military presence in the Middle East is the culmination of a common bargain with Middle Eastern governments: security cooperation and military assistance in exchange for US access to military bases in the region. As a result, the US has substantial influence in the Middle East and can project military power quickly. However, working with partners whose interests sometimes conflict with one another has occasionally harmed long-term US objectives. • Since 1980, when President Carter remarked that outside intervention in the interests of the US in the Middle East would be ‘repelled by any means necessary’, the US has maintained a permanent and significant military presence in the region. • Two main schools of thought – ‘offshore balancing’ and ‘forward engagement’ – characterize the debate over the US presence in the Middle East. -

Military Policy and the Causes of War: Eight Hypotheses
1 MIT / 17.42 / Causes and Prevention of War Stephen Van Evera MILITARY POLICY AND THE CAUSES OF WAR: EIGHT HYPOTHESES I. FIRST MOVE ADVANTAGE (or "crisis instability"). "The greater the advantage that accrues to the side mobilizing or striking first, the greater the risk of war." See Schelling, Arms and Influence, chapter 6 (assigned). A. When does it pay / not pay / to move (mobilize or strike) first? 1. The problem is two-sided. If you have a first-move advantage, it pays your opponent to move first just to deny you the first-move advantage. 2. First-strike vs. first-mobilization advantages. Both are dangerous. B. Dangers raised by a first-move advantage (FMA): 1. Opportunistic war. ("If we strike first we win, so let's strike and capture the benefits of winning!") Not a profound point but many analysts don't get beyond it. 2. Preemptive war. "We fear they will strike, so we must strike." Examples: Israel's 1967 attack on Egypt; Russia's 1914 mobilization. And two extensions: -- "Accidental War." Example: 1890 Battle of Wounded Knee. -- "The Reciprocal Fear of Surprise Attack"--Schelling. ("We fear they fear we fear they will strike; so they may strike; so we must.") This is the common formulation of the problem but the least realistic. History shows that reciprocal fear almost never happens, perhaps because states seldom see themselves as threats to others so they seldom expect others to fear them. 3. The Dangers of Candor--the most serious of these 3 risks. States conceal their grievances and their capabilities because they think: "we must lull them into believing we are weak and benign; otherwise we can't gain surprise." This makes inadvertent war and wars of false optimism more likely.