Al-Qaeda's Online Media Strategies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Combating Islamic Extremist Terrorism 1
CGT 1/22/07 11:30 AM Page 1 Combating Islamic Extremist Terrorism 1 OVERALL GRADE D+ Al-Qaeda headquarters C+ Al-Qaeda affiliated groups C– Al-Qaeda seeded groups D+ Al-Qaeda inspired groups D Sympathizers D– 1 CGT 1/22/07 11:30 AM Page 2 2 COMBATING ISLAMIC EXTREMIST TERRORISM ive years after the September 11 attacks, is the United States win- ning or losing the global “war on terror”? Depending on the prism through which one views the conflict or the metrics used Fto gauge success, the answers to the question are starkly different. The fact that the American homeland has not suffered another attack since 9/11 certainly amounts to a major achievement. U.S. military and security forces have dealt al-Qaeda a severe blow, cap- turing or killing roughly three-quarters of its pre-9/11 leadership and denying the terrorist group uncontested sanctuary in Afghanistan. The United States and its allies have also thwarted numerous terror- ist plots around the world—most recently a plan by British Muslims to simultaneously blow up as many as ten jetliners bound for major American cities. Now adjust the prism. To date, al-Qaeda’s top leaders have sur- vived the superpower’s most punishing blows, adding to the near- mythical status they enjoy among Islamic extremists. The terrorism they inspire has continued apace in a deadly cadence of attacks, from Bali and Istanbul to Madrid, London, and Mumbai. Even discount- ing the violence in Iraq and Afghanistan, the tempo of terrorist attacks—the coin of the realm in the jihadi enterprise—is actually greater today than before 9/11. -

Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress
Order Code RL32114 Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Updated January 29, 2008 Clay Wilson Specialist in Technology and National Security Foreign Affairs, Defense, and Trade Division Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Summary Cybercrime is becoming more organized and established as a transnational business. High technology online skills are now available for rent to a variety of customers, possibly including nation states, or individuals and groups that could secretly represent terrorist groups. The increased use of automated attack tools by cybercriminals has overwhelmed some current methodologies used for tracking Internet cyberattacks, and vulnerabilities of the U.S. critical infrastructure, which are acknowledged openly in publications, could possibly attract cyberattacks to extort money, or damage the U.S. economy to affect national security. In April and May 2007, NATO and the United States sent computer security experts to Estonia to help that nation recover from cyberattacks directed against government computer systems, and to analyze the methods used and determine the source of the attacks.1 Some security experts suspect that political protestors may have rented the services of cybercriminals, possibly a large network of infected PCs, called a “botnet,” to help disrupt the computer systems of the Estonian government. DOD officials have also indicated that similar cyberattacks from individuals and countries targeting economic, -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

Ep Delegation for Relations with the Palestinian
Delegation for Relations with the Palestinian Legislative Council European Parliament/Palestinian Legislative Council 7th Interparliamentary Meeting East Jerusalem/Ramallah/Gaza/Hebron 29 April -3 May 2007 Report by Mr Kyriacos TRIANTAPHYLLIDES, Chairman of the Delegation CR\671268EN.doc PE 384.740 EN EN I. Introduction The visit of the EP delegation in Palestine was the first official contact between both sides since November 2005. Due to the situation in the region, several attempts to meet earlier had failed. Following the Hamas victory in the legislative elections in January 2006, the EP delegation insisted to meet with the newly elected government of national unity agreed in Mekka in February 2007. The representation of the Commission did not attend the meetings where Ministers from Hamas and the Prime Minister were present. (This is the reasoning for listing participants at the beginning of each meeting report). One week before travelling to Palestine, the Chair, in a meeting on 25 April 2007 with Deputies from the Knesset, announced that the Delegation wished to meet with members of the new government, including Hamas members. The reaction of the Chair of the Knesset delegation was quite positive. It is worth adding that the Israeli authorities were cooperative during the whole visit, especially at the airport in Tel Aviv and on the Gaza border. II. Meetings Monday 30 April 1. Briefing by ECTAO (European Technical Assistance Office for the West Bank and Gaza Strip) on the humanitarian and political situation in the Occupied Palestinian Territories. Location: ECTAO, Jerusalem, 09h00-10h15 Participants: John Kjaer (ECTAO Representative), Roy Dickinson (Head of Operations), Ana Gallo (Head of the Political Section), Mark Gallagher (Head of Section - Economic and Financial Cooperation), Regis Meritan (Head of Section - Infrastructure, Water, Environment, Agriculture and UNRWA), EP Delegation. -

Eyeless in Gaza 21
Acram 1/24/04 1:49 AM Page 19 19 Eyeless Michael Ancram: Good to see you. Lots has happened since we last met.1 I guess you have in Gaza been busy, Gaza has been interesting, I’m keen The liberation of Alan to hear what has been going on. How do you Johnston and the think things will go? imprisonment of Gaza Usamah Hamdan: I will start from the Mecca Agreement. At Mecca there were three Daily in the common Prison important points. The first one was on the else enjoyn’d me, National Unity Government; the second point Where I a Prisoner chain’d, covered the reform of the security services and scarce freely draw called for a new security plan for the Palestinian The air imprison’d also, territories, and the third point was on the reform close and damp, of the PLO and the new political arrangements Unwholsom draught … inside the Palestinian political body. That means John Milton, the relations within the PLO itself, the relations Samson Agonistes between the PLO and the Palestinian Authority, the internal Palestinian relations.2 And we [in the Hamas movement] went back to Gaza and within one month there was the formation of the Usamah Hamden National Unity Government. We started talking about security. There was a security plan that Michael Ancram MP was put forward and that was endorsed by the Jonathan Lehrle government and that was then endorsed by Abu Mark Perry Mazen himself as President.3 When we started to apply that [the security plan] on the ground we faced an important problem – which was that the main General in the security service failed to apply and rejected 1. -
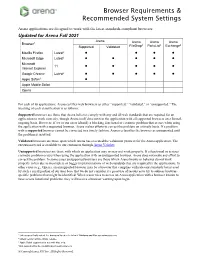
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

Arena Training Guide for Administrators Table of Contents
Arena training guide for administrators Table of contents Preface 4 About this guide 4 Get to know Axiell 4 About Arena 5 Liferay 5 Portlets 5 Language handling 5 Styling 5 Arena architecture 6 Administration in Arena 7 Arena articles 7 Signing in to Arena 7 Signing in to Liferay 8 The Arena administration user interface 8 Accounts 11 User types in Arena 11 Permissions 12 Managing users in Liferay 14 Managing a roles in Liferay 16 Arena portal site administration 17 Admin: installation details 17 Site settings 19 Managing pages 21 Page permissions 21 Navigation 21 Configuring pages 21 Creating a page 22 Deleting a page 23 Arena Nova 25 Focus shortcuts 25 That’s how it works-articles 25 News articles 26 Event articles 26 Branch articles 26 FAQ articles 27 Image resources and image handling 27 Portlets in Arena 28 Symbols in the list of portlets 28 Portlets required for basic Arena functionality 28 Placement of portlets 29 Configuring portlets 30 The control toolbar 30 Look and feel 30 2 Assigning user permissions to portlets and pages 30 Liferay articles 32 Creating a Liferay article 32 Adding a Liferay article on a page 32 Arena articles 33 Approving articles 33 Handling abuse and reviews 34 Admin: moderation 34 Searching in catalogue records 36 Single words 36 Phrases 36 Multiple words 36 Truncation 36 Boolean operators 36 Fuzzy search and the similarity factor 36 Search parameters for catalogue records 37 Search parameters for Arena articles 40 Examples 40 Linking and syntaxes 41 Dynamic links 41 Syntax for similar titles 42 Syntax for other titles by the same author 42 Syntax for dynamic news list 42 3 Preface Simple, stylish and engaging, Arena is perfect for archives, libraries and museums to showcase and organize their collections in the public domain. -

Preventing Violent Extremism in Kyrgyzstan
UNITED STATES INSTITUTE OF PEACE www.usip.org SPECIAL REPORT 2301 Constitution Ave., NW • Washington, DC 20037 • 202.457.1700 • fax 202.429.6063 ABOUT THE REPORT Jacob Zenn and Kathleen Kuehnast This report offers perspectives on the national and regional dynamics of violent extremism with respect to Kyrgyzstan. Derived from a study supported by the United States Institute of Peace (USIP) to explore the potential for violent extremism in Central Asia, it is based on extensive interviews and a Preventing Violent countrywide Peace Game with university students at Kyrgyz National University in June 2014. Extremism in Kyrgyzstan ABOUT THE AUTHORS Jacob Zenn is an analyst on Eurasian and African affairs, a legal adviser on international law and best practices related to civil society and freedom of association, and a nonresident research Summary fellow at the Center of Shanghai Cooperation Organization Studies in China, the Center of Security Programs in Kazakhstan, • Kyrgyzstan, having twice overthrown autocratic leaders in violent uprisings, in 2005 and again and The Jamestown Foundation in Washington, DC. Dr. Kathleen in 2010, is the most politically open and democratic country in Central Asia. Kuehnast is a sociocultural anthropologist and an expert on • Many Kyrgyz observers remain concerned about the country’s future. They fear that underlying Kyrgyzstan, where she conducted field work in the early 1990s. An adviser on the Central Asia Fellows Program at the socioeconomic conditions and lack of public services—combined with other factors, such as Elliott School of International Affairs at George Washington drug trafficking from Afghanistan, political manipulation, regional instability in former Soviet University, she is a member of the Council on Foreign Union countries and Afghanistan, and foreign-imported religious ideologies—create an envi- Relations and has directed the Center for Gender and ronment in which violent extremism can flourish. -

The Nutshell Studies of Unexplained Death Stephanie Witt
School of Graduate and Professional Studies 100 Campus Circle, Owings Mills, Maryland 21117 1-877-468-6852 accelerate.stevenson.edu STEVENSON UNIVERSITY FORENSICS JOURNAL VOLUME 4 EDITORIAL BOARD EDITOR-IN-CHIEF Carolyn Hess Johnson, Esq. PUBLISHER Carolyn Hess Johnson, Esq. EDITORS Abigail Howell Stephanie Witt COVER PHOTO Bruce Goldfarb Assistant to the Chief Medical Examiner, Maryland DESIGN & LAYOUT Chip Burkey Cassandra Bates Stevenson University Marketing and Public Relations Office Copyright © 2013, author(s) and Stevenson University Forensics Journal. No permission is given to copy, distribute or reproduce this article in any format without prior explicit written permission from the article’s author(s) who hold exclusive rights to impose usage fee or royalties. FORENSICS JOURNAL Welcome to our fourth annual Stevenson University Forensics Journal. This year, as always, we bring fresh voices and perspectives from all aspects and areas of the field. I am pleased to note that a new section has been added this year, highlighting the process of library research in the vast field of Forensic Studies. Our Stevenson University librarians bring the research pro- cess into the twenty-first century by showcasing a variety of on-line resources available to researchers. Also of note is the connection between our cover photo and the interview conducted with Dr. David Fowler, Chief Medical Examiner for the State of Maryland. Assistant Editor Stephanie Witt joins the Journal as a contributor to explain the fascinating Nutshell Series of Unexplained Deaths. We are privileged this year to have the Honorable Lynne A. Battaglia providing her insights into the Court’s perspective on the prominent role of forensic evidence in modern litigation. -

9/11 Report”), July 2, 2004, Pp
Final FM.1pp 7/17/04 5:25 PM Page i THE 9/11 COMMISSION REPORT Final FM.1pp 7/17/04 5:25 PM Page v CONTENTS List of Illustrations and Tables ix Member List xi Staff List xiii–xiv Preface xv 1. “WE HAVE SOME PLANES” 1 1.1 Inside the Four Flights 1 1.2 Improvising a Homeland Defense 14 1.3 National Crisis Management 35 2. THE FOUNDATION OF THE NEW TERRORISM 47 2.1 A Declaration of War 47 2.2 Bin Ladin’s Appeal in the Islamic World 48 2.3 The Rise of Bin Ladin and al Qaeda (1988–1992) 55 2.4 Building an Organization, Declaring War on the United States (1992–1996) 59 2.5 Al Qaeda’s Renewal in Afghanistan (1996–1998) 63 3. COUNTERTERRORISM EVOLVES 71 3.1 From the Old Terrorism to the New: The First World Trade Center Bombing 71 3.2 Adaptation—and Nonadaptation— ...in the Law Enforcement Community 73 3.3 . and in the Federal Aviation Administration 82 3.4 . and in the Intelligence Community 86 v Final FM.1pp 7/17/04 5:25 PM Page vi 3.5 . and in the State Department and the Defense Department 93 3.6 . and in the White House 98 3.7 . and in the Congress 102 4. RESPONSES TO AL QAEDA’S INITIAL ASSAULTS 108 4.1 Before the Bombings in Kenya and Tanzania 108 4.2 Crisis:August 1998 115 4.3 Diplomacy 121 4.4 Covert Action 126 4.5 Searching for Fresh Options 134 5. -

Beining and Evans
THE INSTITUTE FOR MIDDLE EAST STUDIES IMES CAPSTONE PAPER SERIES IS A BOMBER JUST A BOMBER? A MULTILEVEL ANALYSIS OF WOMEN SUICIDE BOMBERS1 CARA BEINING KARI EVANS APRIL 2014 THE INSTITUTE FOR MIDDLE EAST STUDIES THE ELLIOTT SCHOOL OF INTERNATIONAL AFFAIRS THE GEORGE WASHINGTON UNIVERSITY © OF CARA BEINING AND KARI EVANS, 2014 Beining and Evans TABLE OF CONTENTS ACKNOWLEDGEMENTS…………………………………………………………………….. 3 INTRODUCTION………………………………………………………………………………. 4 A Note on Terms……………………………………………………………………………….. 5 Defining the Problem…………………………………………………………………………... 9 Methodology………………………………………………………………………………….. 12 I. THE GLOBAL TREND…………………………………………………………………….. 17 II. ENVIRONMENTAL FACTORS………………………………………………………….. 22 Palestine………………………………………………………………………………………. 25 Iraq……………………………………………………………………………………………. 28 The Role of the Environment…………………………………………………………………. 30 III. ORGANIZATIONAL LEVEL…………………………………………………………… 32 Hamas…………………………………………………………………………………………. 34 Al-Qaeda in Iraq………………………………………………………………………………. 40 Role of the Organization……………………………………………………………………… 46 IV: INDIVIDUAL LEVEL……………………………………………………………………. 49 Examples from Palestine……………………………………………………………………… 52 Examples from Iraq…………………………………………………………………………… 56 Role of the Individual………………………………………………………………………….58 V. CONCLUSION……………………………………………………………………………... 60 The Big Picture………………………………………………………………………………...60 Recommendations…………………………………………………………………………….. 62 APPENDIX I ………………………………..…………………………………………………. 73 APPENDIX II…………………….…………………………………………………………….. 79 APPENDIX III…………………………….…………………………………………………… -

Considering the Creation of a Domestic Intelligence Agency in the United States
HOMELAND SECURITY PROGRAM and the INTELLIGENCE POLICY CENTER THE ARTS This PDF document was made available CHILD POLICY from www.rand.org as a public service of CIVIL JUSTICE the RAND Corporation. EDUCATION ENERGY AND ENVIRONMENT Jump down to document6 HEALTH AND HEALTH CARE INTERNATIONAL AFFAIRS The RAND Corporation is a nonprofit NATIONAL SECURITY research organization providing POPULATION AND AGING PUBLIC SAFETY objective analysis and effective SCIENCE AND TECHNOLOGY solutions that address the challenges SUBSTANCE ABUSE facing the public and private sectors TERRORISM AND HOMELAND SECURITY around the world. TRANSPORTATION AND INFRASTRUCTURE Support RAND WORKFORCE AND WORKPLACE Purchase this document Browse Books & Publications Make a charitable contribution For More Information Visit RAND at www.rand.org Explore the RAND Homeland Security Program RAND Intelligence Policy Center View document details Limited Electronic Distribution Rights This document and trademark(s) contained herein are protected by law as indicated in a notice appearing later in this work. This electronic representation of RAND intellectual property is provided for non-commercial use only. Unauthorized posting of RAND PDFs to a non-RAND Web site is prohibited. RAND PDFs are protected under copyright law. Permission is required from RAND to reproduce, or reuse in another form, any of our research documents for commercial use. For information on reprint and linking permissions, please see RAND Permissions. This product is part of the RAND Corporation monograph series. RAND monographs present major research findings that address the challenges facing the public and private sectors. All RAND mono- graphs undergo rigorous peer review to ensure high standards for research quality and objectivity.