Post-Graduate Diploma in Cyber Security Information Security Assurance: Framework, Standards & Industry Best Practices (PGDCS-05)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Discussion Paper 2019/01 – the Climate Reporting Emergency: a New Zealand Case Study
Discussion Paper 2019/01 – The Climate Reporting Emergency: A New Zealand case study Discussion Paper 2019/01 The Climate Reporting Emergency: A New Zealand case study October 2019 Title Discussion Paper 2019/01 – The Climate Reporting Emergency: A New Zealand case study Published Copyright © McGuinness Institute Limited, October 2019 ISBN – 978-1-98-851820-6 (paperback) ISBN – 978-1-98-851821-3 (PDF) This document is available at www.mcguinnessinstitute.org and may be reproduced or cited provided the source is acknowledged. Prepared by The McGuinness Institute, as part of Project 2058. Research team Wendy McGuinness, Eleanor Merton, Isabella Smith and Reuben Brady Special thanks to Lay Wee Ng and Mace Gorringe Designers Becky Jenkins and Billie McGuinness Editor Ella Reilly For further McGuinness Institute information Phone (04) 499 8888 Level 2, 5 Cable Street PO Box 24222 Wellington 6142 New Zealand www.mcguinnessinstitute.org Disclaimer The McGuinness Institute has taken reasonable care in collecting and presenting the information provided in this publication. However, the Institute makes no representation or endorsement that this resource will be relevant or appropriate for its readers’ purposes and does not guarantee the accuracy of the information at any particular time for any particular purpose. The Institute is not liable for any adverse consequences, whether they be direct or indirect, arising from reliance on the content of this publication. Where this publication contains links to any website or other source, such links are provided solely for information purposes, and the Institute is not liable for the content of such website or other source. Publishing The McGuinness Institute is grateful for the work of Creative Commons, which inspired our approach to copyright. -

BSI Standards Publication
BS EN IEC 62430:2019 BSI Standards Publication Environmentally conscious design (ECD) — Principles, requirements and guidance BS EN IEC 62430:2019 BRITISH STANDARD EUROPEAN STANDARD EN IEC 62430 NORME EUROPÉENNE National foreword EUROPÄISCHE NORM December 2019 This British Standard is the UK implementation of EN IEC 62430:2019. It is identical to IEC 62430:2019. It supersedes BS EN 62430:2009, which ICS 13.020.01 Supersedes EN 62430:2009 and all of its amendments is withdrawn. and corrigenda (if any) The UK participation in its preparation was entrusted to Technical Committee GEL/111, Electrotechnical environment committee. English Version A list of organizations represented on this committee can be obtained on request to its secretary. Environmentally conscious design (ECD) - Principles, This publication does not purport to include all the necessary provisions requirements and guidance of a contract. Users are responsible for its correct application. (IEC 62430:2019) © The British Standards Institution 2020 Published by BSI Standards Limited 2020 Écoconception (ECD) - Principes, exigences et Umweltbewusstes Gestalten (ECD) - Grundsätze, recommandations Anforderungen und Leitfaden ISBN 978 0 580 96347 6 (IEC 62430:2019) (IEC 62430:2019) ICS 13.020.01; 29.020; 31.020; 43.040.10 This European Standard was approved by CENELEC on 2019-11-26. CENELEC members are bound to comply with the CEN/CENELEC Compliance with a British Standard cannot confer immunity from Internal Regulations which stipulate the conditions for giving this European Standard the status of a national standard without any alteration. legal obligations. Up-to-date lists and bibliographical references concerning such national standards may be obtained on application to the CEN-CENELEC This British Standard was published under the authority of the Management Centre or to any CENELEC member. -

Toolkit on Environmental Sustainability for the ICT Sector Toolkit September 2012
!"#"$%&&'()$*+%(,-."/0%1,-*(2- -------!"#"&*+$,-3*4%1*/%15- .*+%(*#-7(/"1A6()B"1,)/5-C%(,%1+'&- D%1-!"#"$%&&'()$*+%(,-- 6.789:;7!<-=9>37-;!6=7-=7- >9.?8@- Toolkit on environmental sustainability for the ICT !"#"$%&&'()$*+%(,-."/0%1,-*(2- -------!"#"&*+$,-3*4%1*/%15- !"#"$%&&'()$*+%(,-."/0%1,-*(2- sector -------!"#"&*+$,-3*4%1*/%15- .*+%(*#-7(/"1A6()B"1,)/5.*+%(*#-7(/"1A-C%(,%1+'&- 6()B"1,)/5-C%(,%1+'&- D%1-!"#"$%&&'()$*+%(,D%1---!"#"$%&&'()$*+%(,-- 6.789:;7!<-=9>37-;!6=7-=7-6.789:;7!<-=9>37-;!6=7-=7- >9.?8@- >9.?8@- Toolkit on environmental sustainability for the ICT sector Toolkit September 2012 About ITU-T and Climate Change: itu.int/ITU-T/climatechange/ Printed in Switzerland Geneva, 2012 E-mail: [email protected] Photo credits: Shutterstock® itu.int/ITU-T/climatechange/ess Acknowledgements This toolkit was developed by ITU-T with over 50 organizations and ICT companies to establish environmental sustainability requirements for the ICT sector. This toolkit provides ICT organizations with a checklist of sustainability requirements; guiding them in efforts to improve their eco-efficiency, and ensuring fair and transparent sustainability reporting. The toolkit deals with the following aspects of environmental sustainability in ICT organizations: sustainable buildings, sustainable ICT, sustainable products and services, end of life management for ICT equipment, general specifications and an assessment framework for environmental impacts of the ICT sector. The authors would like to thank Jyoti Banerjee (Fronesys) and Cristina Bueti (ITU) who gave up their time to coordinate all comments received and edit the toolkit. Special thanks are due to the contributory organizations of the Toolkit on Environmental Sustainability for the ICT Sector for their helpful review of a prior draft. -

Report on Standardizing Operating Procedures in Ethics Assessment
Report on standardizing operating procedures in ethics assessment Deliverable D7.1 Authors part I: Signe Annette Bøgh and Katrine Bergh Skriver (Danish Standards) Authors part II: Marlou Bijlsma and Thamar Zijlstra (NEN, Nederlands Normalisatie Instituut) Contributors: Rowena Rodrigues; Trilateral Research Ltd, Erich Griessler; Institut für Höhere Studien, Rok Benčin; ZRC SAZU: Research Centre of the Slovenian Academy of Sciences and Arts, July 2017 Contact details for corresponding author: Signe Annette Bøgh (Danish Standards), [email protected] Marlou Bijlsma (NEN, Nederlands Normalisatie Instituut), [email protected] This deliverable and the work described in it is part of the project Stakeholders Acting Together on the Ethical Impact Assessment of Research and Innovation - SATORI - which received funding from the European Commission’s Seventh Framework Programme (FP7/2007-2013) under grant agreement n° 612231 Deliverable 7.1 Standardizing ethics assessment Content Content ....................................................................................................................... 1 Abstract ...................................................................................................................... 3 Executive Summary ..................................................................................................... 4 1. Introduction ............................................................................................................. 5 1.1 Objectives............................................................................................................................. -

Standards News Late March 2012 Volume 16, Number 6
PLASA Standards News Late March 2012 Volume 16, Number 6 Table of Contents Eight PLASA Standards in Public Review.........................................................................................................1 RDM and sACN Developers Conference and Plugfest Invitation......................................................................3 ANSI Seeks Comments on ISO Traffic Safety Management Proposal.............................................................3 WTO Notifications............................................................................................................................................. 3 Togo Notification TGO/2................................................................................................................................ 3 Ukraine Notification UKR/72.......................................................................................................................... 4 Uganda Notification UGA/217....................................................................................................................... 4 ANSI Public Review Announcements...............................................................................................................5 Due 23 April 2012.......................................................................................................................................... 5 Due 30 April 2012.......................................................................................................................................... 5 Due 8 May -
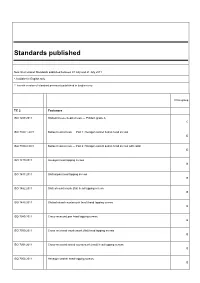
Standards Published
Standards published New International Standards published between 01 July and 31 July 2011 * Available in English only ** French version of standard previously published in English only Price group TC 2 Fasteners ISO 1207:2011 Slotted cheese head screws — Product grade A C ISO 7380-1:2011 Button head screws — Part 1: Hexagon socket button head screws D ISO 7380-2:2011 Button head screws — Part 2: Hexagon socket button head screws with collar D ISO 1479:2011 Hexagon head tapping screws B ISO 1481:2011 Slotted pan head tapping screws B ISO 1482:2011 Slotted countersunk (flat) head tapping screws B ISO 1483:2011 Slotted raised countersunk (oval) head tapping screws B ISO 7049:2011 Cross-recessed pan head tapping screws B ISO 7050:2011 Cross-recessed countersunk (flat) head tapping screws B ISO 7051:2011 Cross-recessed raised countersunk (oval) head tapping screws B ISO 7053:2011 Hexagon washer head tapping screws B TC 5 Ferrous metal pipes and metallic fittings ISO 7186:2011 * Ductile iron products for sewerage applications R ISO 7005-1:2011 * Pipe flanges — Part 1: Steel flanges for industrial and general service piping systems E TC 6 Paper, board and pulps ISO 12625-1:2011 * Tissue paper and tissue products — Part 1: General guidance on terms R TC 8 Ships and marine technology ISO 28002:2011 * Security management systems for the supply chain — Development of resilience in the supply chain — Requirements with guidance for use U TC 20 Aircraft and space vehicles ISO 22072:2011 * Aerospace — Electrohydrostatic actuator (EHA) — Characteristics -

Alphabetical Index
ALPHABETICAL INDEX A Abbreviations Activities relevant to metrics, rubber compounding ingredients 1367 performance metrics SLS ISO/TS 37151 plastics 1559 smart community infrastructures 1507 Abrasive paper 844 Adaptors, bayonet cap 164 Absorbent cotton 285, 1414 Additive elements in lubricating oils gauze 1414 SLS ASTM D 4684 lint 337 Adhesion testers SLS ASTM D4541 viscose gauze 1414 Adhesives Absorbing blood sodium polyacrylate resin 1650-1& 2 ceramic tile 1375 a.c. paper 660 air-break circuit-breakers 1175 polyvinyl acetate based 869 cartridge fuse links 1552 test method SLS ISO 13007-2 electronic control gear 1645-1 & 2 Adjustable ball cup 462 output, stabilized power supplies 1128 Admixtures, ac/dc supplied electronic ballast concrete, mortar, grout EN 934-1 d.c. out put, power supplies 992 conformity, marking, labelling EN 934-2, EN 934-3, tubular fluorescent lamps 1239 Acceptance Quality limit (AQL)(sampling schemes) EN 934-4, EN 934-5 double sampling SLS ISO 3951-3 sampling EN 934-6 single sampling SLS ISO 3951-2single quality Adventure tourism safety management systems SLS ISO characteristic and single SLS ISO 3951-1 21101 declared quality levels SLS ISO 3951-4 Aerated water, glass bottles for 291 inspection variables SLS ISO 3951-5 Aerials Accessories fitted to LPG container 1215 Acetate yarn, gelatin & oil size in 174 sound reception 1008 (withdrawn) Acetic acid salt spray (AASS) test SLS ISO 9227 TV broadcasting 1008 (withdrawn) Acetylene, dissolved 666 Aflatoxin , in food, methods of test 962 Acid After-shave lotion 1031 -

Training Handbook: Sustainable Construction Imprint Title: Training Handbook: Sustainable Construction
Training Handbook: Sustainable Construction Imprint Title: Training Handbook: Sustainable Construction Authors: Wuppertal Institut - Gokarakonda, Sriraj Moore,Christopher Published: Wuppertal Institute 2018 Project title: SusBuild - Up-scaling and mainstreaming sustainable building practices in western China Work Package: 1 Funded by: European Commision Contact: Chun Xia-Bauer Doeppersberg 19 42103 Wuppertal (Germany) e-mail: [email protected] SUSBUILD Training Handbook for Sustainable Construction Table of contents Table of contents 1 Introduction 6 1.1 Sustainable construction 6 1.1.1 Dimensions of Sustainability 6 1.1.2 Sustainable Construction Phase 7 2 Policies, labelling systems and standards related to sustainable construction in Europe 9 2.1 Technical standards related to green construction in Europe 9 2.1.1 European Level 9 2.1.2 CEN/TC 350 - Sustainability of construction works 9 2.1.2.1 EN 15643-1:2010 - Sustainability assessment of buildings - Part 1: General framework 11 2.1.2.2 EN 15643-2:2011 - Assessment of buildings - Part 2: Framework for the assessment of environmental performance 11 2.1.2.3 EN 15643-3:2012 - Assessment of buildings. Framework for the assessment of social performance 11 2.1.2.4 EN 15643-4:2012 - Assessment of buildings. Framework for the assessment of economic performance 12 2.1.2.5 EN 15978:2011 - Assessment of environmental performance of buildings. Calculation method 12 2.1.2.6 EN 16309:2014 - Assessment of social performance of buildings – Methods 12 2.1.2.7 EN 16627:2015 - Assessment of economic performance of buildings - Calculation methods 13 2.1.2.8 EN 15804:2012+A1:2013 - Environmental product declarations. -

Universidad De Oviedo Doctorado En Economía Y Empresa Tesis Doctoral Implicaciones En La Gestión Estratégica De Las Empresas
UNIVERSIDAD DE OVIEDO DOCTORADO EN ECONOMÍA Y EMPRESA TESIS DOCTORAL IMPLICACIONES EN LA GESTIÓN ESTRATÉGICA DE LAS EMPRESAS DE LA INTEGRACIÓN DE LOS SISTEMAS DE GESTIÓN DE LA CALIDAD, MEDIO AMBIENTE Y SEGURIDAD Y SALUD LABORAL, BASADOS EN ESTÁNDARES INTERNACIONALES. EL CASO DE ECUADOR. AUTORA: MARCIA ALMEIDA GUZMÁN DIRECTOR: DR. FRANCISCO JAVIER IGLESIAS RODRÍGUEZ 2018 RESUMEN DEL CONTENIDO DE TESIS DOCTORAL 1.- Título de la Tesis Español/Otro Idioma: Inglés: IMPLICACIONES EN LA GESTIÓN IMPLICATIONS OF QUALITY, ESTRATÉGICA DE LAS EMPRESAS DE LA ENVIRONMENT AND SAFETY AND WORK INTEGRACIÓN DE LOS SISTEMAS DE HEALTH IMSs BASED ON INTERNATIONAL GESTIÓN DE LA CALIDAD, MEDIO STANDARDS, IN THE STRATEGIC AMBIENTE Y SEGURIDAD Y SALUD MANAGEMENT OF FIRMS. THE CASE OF LABORAL, BASADOS EN ESTÁNDARES ECUADOR. INTERNACIONALES. EL CASO DE ECUADOR. 2.- Autor Nombre: DNI/Pasaporte/NIE: Marcia Almeida Guzmán Programa de Doctorado: Programa de Doctorado en Economía y Empresa Órgano responsable: Comisión Académica del Programa de Doctorado RESUMEN (en español) El propósito de esta investigación es el de estudiar las consecuencias que se derivan en la gestión estratégica de las organizaciones ecuatorianas, en un proceso de integración de los sistemas de gestión de Calidad, Medio Ambiente y Seguridad y Salud Laboral, basados en estándares internacionales. Con el fin de lograr encontrar la evidencia (Reg.2018) empírica de la experiencia particular de dichas organizaciones, se aplica un método deductivo hipotético que parte en primer lugar del análisis del soporte teórico así como 010 - del estudio de los sistemas de gestión certificables más ampliamente implantados a nivel mundial (ISO 9001, ISO 14001 y OHSAS 18001, actualmente en proceso de VOA - migración hacia la ISO 45001) junto con los procesos más habitualmente utilizados en su integración. -

Product Environmental Information and Product Policies
Product Environmental Information and Product Policies How Product Environmental Footprint (PEF) changes the situation? Product Environmental Information and Product Policies How Product Environmental Footprint (PEF) changes the situation? Ari Nissinen, Johanna Suikkanen and Hanna Salo TemaNord 2019:549 Product Environmental Information and Product Policies How Product Environmental Footprint (PEF) changes the situation? Ari Nissinen, Johanna Suikkanen and Hanna Salo ISBN 978-92-893-6350-1 (PDF) ISBN 978-92-893-6351-8 (EPUB) http://dx.doi.org/10.6027/tn2019-549 TemaNord 2019:549 ISSN 0908-6692 Standard: PDF/UA-1 ISO 14289-1 © Nordic Council of Ministers 2019 This publication was funded by the Nordic Council of Ministers. However, the content does not necessarily reflect the Nordic Council of Ministers’ views, opinions, attitudes or recommendations Disclaimer This publication was funded by the Nordic Council of Ministers. However, the content does not necessarily reflect the Nordic Council of Ministers’ views, opinions, attitudes or recommendations. Rights and permissions This work is made available under the Creative Commons Attribution 4.0 International license (CC BY 4.0) https://creativecommons.org/licenses/by/4.0. Translations: If you translate this work, please include the following disclaimer: This translation was not pro- duced by the Nordic Council of Ministers and should not be construed as official. The Nordic Council of Ministers cannot be held responsible for the translation or any errors in it. Adaptations: If you adapt this work, please include the following disclaimer along with the attribution: This is an adaptation of an original work by the Nordic Council of Ministers. Responsibility for the views and opinions expressed in the adaptation rests solely with its author(s). -
International Standard Iso 26000:2010(E)
INTERNATIONAL ISO STANDARD 26000 First edition 2010-11-01 Guidance on social responsibility Lignes directrices relatives à la responsabilité sociétale I would like to express my deep appreciation on behalf of the International Organization for Standardization for your dedication and contribution to the development of ISO 26000:2010 and I am pleased to provide you with your personal copy of this standard. Rob Steele Secretary General Single-user license, for personal use only, external distribution, networking and other uses prohibited Reference number ISO 26000:2010(E) © ISO 2010 ISO 26000:2010(E) PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat accepts no liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies. In the unlikely event that a problem relating to it is found, please inform the Central Secretariat at the address given below. COPYRIGHT PROTECTED DOCUMENT © ISO 2010 All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm, without permission in writing from either ISO at the address below or ISO's member body in the country of the requester. -
Engineering Design Process of Face Masks Based on Circularity and Life Cycle Assessment in the Constraint of the COVID-19 Pandemic
sustainability Article Engineering Design Process of Face Masks Based on Circularity and Life Cycle Assessment in the Constraint of the COVID-19 Pandemic Núria Boix Rodríguez 1,* , Giovanni Formentini 1 , Claudio Favi 1 and Marco Marconi 2 1 Department of Engineering and Architecture, University of Parma, 43124 Parma, Italy; [email protected] (G.F.); [email protected] (C.F.) 2 Department of Economics, Engineering, Society and Business Organization, Università degli Studi della Tuscia, 01100 Viterbo, Italy; [email protected] * Correspondence: [email protected]; Tel.: +39-0521-90-6344 Abstract: Face masks are currently considered key equipment to protect people against the COVID-19 pandemic. The demand for such devices is considerable, as is the amount of plastic waste generated after their use (approximately 1.6 million tons/day since the outbreak). Even if the sanitary emergency must have the maximum priority, environmental concerns require investigation to find possible mitigation solutions. The aim of this work is to develop an eco-design actions guide that supports the design of dedicated masks, in a manner to reduce the negative impacts of these devices on the environment during the pandemic period. Toward this aim, an environmental assessment based on life cycle assessment and circularity assessment (material circularity indicator) of different types of masks have been carried out on (i) a 3D-printed mask with changeable filters, (ii) a surgical Citation: Boix Rodríguez, N.; mask, (iii) an FFP2 mask with valve, (iv) an FFP2 mask without valve, and (v) a washable mask. Formentini, G.; Favi, C.; Marconi, M. Results highlight how reusable masks (i.e., 3D-printed masks and washable masks) are the most Engineering Design Process of Face sustainable from a life cycle perspective, drastically reducing the environmental impacts in all Masks Based on Circularity and Life categories.