List of Applications Updated in ARL #2609
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Imagen Y Diseño # Nombre 1 10 Christmas Templates 2 10 DVD
Imagen Y Diseño # Nombre 1 10 Christmas Templates 2 10 DVD Photoshop PSD layer 3 10 Frames for Photoshop 4 1000 famous Vector Cartoons 5 114 fuentes de estilo Rock and Roll 6 12 DVD Plantillas Profesionales PSD 7 12 psd TEMPLATE 8 123 Flash Menu 9 140 graffiti font 10 150_Dreamweaver_Templates 11 1600 Vector Clip Arts 12 178 Companies Fonts, The Best Collection Of Fonts 13 1800 Adobe Photoshop Plugins 14 2.900 Avatars 15 20/20 Kitchen Design 16 20000$ Worth Of Adobe Fonts! with Adobe Type Manager Deluxe 17 21000 User Bars - Great Collection 18 240+ Gold Plug-Ins for Adobe Dreamweaver CS4 19 30 PSD layered for design.Vol1 20 300.000 Animation Gif 21 32.200 Avatars - MEGA COLLECTION 22 330 templates for Power Point 23 3900 logos de marcas famosas en vectores 24 3D Apartment: Condo Designer v3.0 25 3D Box Maker Pro 2.1 26 3D Button Creator Gold 3.03 27 3D Home Design 28 3D Me Now Professional 1.5.1.1 -Crea cabezas en 3D 29 3D PaintBrush 30 3D Photo Builder Professional 2.3 31 3D Shadow plug-in for Adobe Photoshop 32 400 Flash Web Animations 33 400+ professional template designs for Microsoft Office 34 4000 Professional Interactive Flash Animations 35 44 Cool Animated Cards 36 46 Great Plugins For Adobe After Effects 37 50 BEST fonts 38 5000 Templates PHP-SWISH-DHTM-HTML Pack 39 58 Photoshop Commercial Actions 40 59 Unofficial Firefox Logos 41 6000 Gradientes para Photoshop 42 70 POSTERS Alta Calidad de IMAGEN 43 70 Themes para XP autoinstalables 44 73 Custom Vector Logos 45 80 Golden Styles 46 82.000 Logos Brands Of The World 47 90 Obras -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

BUNDESKARTELLAMT Beschluss in Dem Verwaltungsverfahren 1
BUNDESKARTELLAMT 7. Beschlussabteilung B 7 - 162/05 FÜR DIE VERÖFFENTLICHUNG BESTIMMT FUSIONSVERFAHREN VERFÜGUNG GEMÄSS § 40 ABS. 2 GWB Beschluss In dem Verwaltungsverfahren 1. Adobe Systems Inc., San Jose, CA, USA - Beteiligte zu 1 - 2. Macromedia Inc., San Fransisco, CA, USA - Beteiligte zu 2 - – Verfahrensbevollmächtigte – a. der Beteiligten zu 1 Clifford Chance RA Martin Bechtold RA’in Julia Holtz RA Jürgen Schindler Mainzer Landstraße 46 60325 Frankfurt am Main b. der Beteiligten zu 2 Cleary Gottlieb Steen & Hamilton LLP Dr. Romina Polley Theodor-Heuss-Ring 9 50668 Köln wegen Prüfung eines Zusammenschlussvorhabens nach § 36 des Gesetzes gegen Wettbe- werbsbeschränkungen (GWB) hat die 7. Beschlussabteilung des Bundeskartellamts am 23. Dezember 2005 beschlossen: Seite 2 von 24 1. Das am 02. September 2005 angemeldete Zusammenschlussvorhaben wird freigegeben. 2. Die Gebühr für die Anmeldung wird auf [...] Euro (in Worten: [...] Euro) festgesetzt. Gebührenschuldner ist nach § 80 Abs. 6 Satz 1 Nr. 1 GWB die im Rubrum zu 1. genannte Beteiligte. Gründe I. Sachverhalt 1. Zusammenschlussvorhaben und Verfahren 1. Mit Schreiben vom 02.09.2005, eingegangen per Fax am selben Tag, hat die Beteiligte zu 1 (Adobe) die Absicht angemeldet, sämtliche Geschäftsanteile der Beteiligten zu 2 (Macromedia) zu erwerben. 2. Mit Schreiben vom 30.09.2005, zugegangen am selben Tag, hat die Beschlussabteilung den Beteiligten mitgeteilt, dass sie das Hauptprüfverfahren gemäß § 40 Abs. 1 S. 1 GWB eingeleitet hat. 2. Die beteiligten Unternehmen 3. Adobe ist ein börsennotiertes US-amerikanisches Softwareunternehmen. Die von Adobe entwickelten und vertriebenen Softwareprodukte dienen zur digitalen Bildbearbeitung, Grafik- und Webdesignerstellung und zur digitalen Erstellung von Druckvorlagen. Dar- über hinaus hat Adobe das Dokumentenformat PDF (portable document format) entwi- ckelt. -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

Computer and Information Security Pointer to Homework 2
Computer and Information Security (ECE560, Fall 2020, Duke Univ., Prof. Tyler Bletsch) Pointer to Homework 2 Updated 2020-09-07: Clarified SSH key format Question 0: Accessing the Homework (0 points, but necessary) Homework 2 is encrypted with three stages of encryption. You’ll need to use both your Windows VM and a new Kali Linux VM. The stages are: 1. The inner layer is a VeraCrypt encrypted disk image to be opened in Windows that contains a link to Homework 2; I explain how to find the key for this later in this document. You get to the inner layer by decrypting the outer layer. 2. The outer layer is encrypted with AES and is available for each student on the course site; the secret key is randomly generated per each student and is distributed by the Encrypted Thing Giver web app. 3. The Encrypted Thing Giver accepts an RSA public key, encrypts the random secret key using this public key. As owner of the corresponding private key, you’ll be able to decrypt it in order to obtain the AES key for the outer layer. The steps below will walk you through this crypto journey. You will need to show your work later, so keep notes! Make an SSH key pair You will need an SSH key pair. If you already created one, you can use it as-is (provided it is RSA-based, but most are). If you don’t have an SSH key pair, research how to create one with ssh-keygen. You may wish to do this on your local system, as you can set it up to let you SSH into Duke machines without a password (optional -- see Appendix A at the end of this document). -

Acta Technica Napocensis
151 TECHNICAL UNIVERSITY OF CLUJ-NAPOCA ACTA TECHNICA NAPOCENSIS Series: Applied Mathematics, Mechanics, and Engineering Vol. 58, Issue II, June, 2015 PROGRAMMING CANVAS X Pro 16 USING SCRIPTING TECHNOLOGIES Tiberiu Alexandru ANTAL Abstract: The paper gives a short overview on the Canvas X Pro 16 integrated environment for vector illustration, imaging, presentations, and Web publishing software together with the scripting technologies that can be used to program the product. Some programming examples in VBScript and Visual Basic about how to draw an extruded spur gear are covering most of the features that are useful for the mechanical engineers work. Key words: Canvas X Pro 16, programming, VBScript, Visual Basic, vector graphics. 1. INTRODUCTION scripting reference gives a description based on short examples of how to create scripts to Canvas X Pro 16 belongs to the category of automate Canvas X using AppleScript and vector oriented processing software that creates Visual Basic. Under the Windows operating technical illustrators for many industries as it system scripts can be written in JavaScript and offers a very flexible, scalable and integrated VBScript and executed if Windows Scripting design environment. Some of the names Host is installed. As this is installed by default belonging to the same category of software are: on most versions of Windows running such a Corel Draw, Inkscape, Adobe Illustrator, script is done under the command windows by however Canvas X has the advantage of being the following syntax: very simple and effective. The software covers at a state-of-the-art level the 2D technical illustration, imaging, presentations, and Web publishing domains and integrates simple and known scripting technologies for programming. -

CEH: Certified Ethical Hacker Course Content
CEH: Certified Ethical Hacker Course ID #: 1275-100-ZZ-W Hours: 35 Course Content Course Description: The Certified Ethical Hacker (CEH) program is the core of the most desired information security training system any information security professional will ever want to be in. The CEH, is the first part of a 3 part EC-Council Information Security Track which helps you master hacking technologies. You will become a hacker, but an ethical one! As the security mindset in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment. This course was designed to provide you with the tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”. This course will immerse you into the Hacker Mindset so that you will be able to defend against future attacks. It puts you in the driver’s seat of a hands-on environment with a systematic ethical hacking process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be thought the Five Phases of Ethical Hacking and thought how you can approach your target and succeed at breaking in every time! The ve phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks. The tools and techniques in each of these five phases are provided in detail in an encyclopedic approach to help you identify when an attack has been used against your own targets. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Creating a Patch and Vulnerability Management Program
Special Publication 800-40 Version 2.0 Creating a Patch and Vulnerability Management Program Recommendations of the National Institute of Standards and Technology (NIST) Peter Mell Tiffany Bergeron David Henning NIST Special Publication 800-40 Creating a Patch and Vulnerability Version 2.0 Management Program Recommendations of the National Institute of Standards and Technology Peter Mell Tiffany Bergeron David Henning C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 November 2005 U.S. Department of Commerce Carlos M. Gutierrez, Secretary Technology Administration Michelle O'Neill, Acting Under Secretary of Commerce for Technology National Institute of Standards and Technology William A. Jeffrey, Director CREATING A PATCH AND VULNERABILITY MANAGEMENT PROGRAM Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-40 Version 2.0 Natl. -

INSIDE! Double-Sided DVD Double-Sided
and lots of LINUX LINUX PRO MAGAZINE FREE USB PASSWORD SAFER BOOT DVD other timely Making Secure Boot MANAGER and useful tools work with Linux ISSUE ISSUE 206 Double-Sided DVD JANUARY 2018 JANUARY 2018 JANUARY INSIDE! SAFER Safer Boot Safer UEFI Shim TPM Backup Tools Stacer DDoS Attacks Pi FM Radio Volumio 2 Volumio Radio FM Pi Attacks DDoS Stacer Backup Tools TPM Shim UEFI BOOT Keeping control of the startup process UEFI Tricks Add a custom app that runs from the firmware Automated 5 Backup Tools Pi FM Radio DDoS Attack Stacer Build a stairway Avoiding a denial Clean up your to maker heaven of service nightmare Linux system Issue 206 Jan 2018 FOSSPicks US$ 15.99 CAN$ 17.99 FOSS • qutebrowser 1.0 0 74820 58049 Marke • Storyboarder t • CoreFreq ing • Marketing Free Software Audacity ffmpeg • Fragment synthesizer • Phipps: FOSS Communities Need Equal Rights Tutorials 3 • Digitize Your LPs with Audacity • ffmpeg 01 WWW.LINUXPROMAGAZINE.COM EDITORIAL Welcome TOMORROW’S NEWS Dear Reader, When I started working for this magazine, way back in 2004, of lobbyists and marketing professionals who keep chipping Linux was really picking up momentum. That was back in away at public opinion when everyone else has gone back to those years when every year was supposed to be “the year of their day jobs. the Linux desktop,” and the epic Linux vs. Windows battle Software has no shape or solid edges. The value of a software was revving to a full burn. product is simply what whoever owns it says they will charge One of the best examples of the Linux juggernaut was the city you for it. -
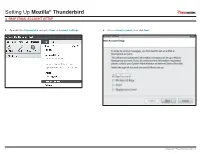
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Fbi Fbi Flash
TLP: GREEN FBI FLASH FBI FBI Liaison Alert System #M-000045-TT The following information was obtained through FBI investigation and is provided in conjunction with the FBI’s statutory requirement to conduct victim notification as outlined in 42 USC § 10607. In furtherance of public-private partnerships, the FBI routinely advises private industry of various cyber threat indicators observed during the course of our investigations. This data is provided in order to help cyber security professionals and systems administrators to guard against the persistent malicious actions of cyber criminals. This product is released at TLP: GREEN. The information in this product is useful for the awareness of all participating organizations as well as with peers within the broader community or sector. Recipients may share this information with peers and partner organizations within their sector or community, but not via publicly accessible channels. SUMMARY The FBI is providing the following information with HIGH confidence: A group of cyber actors utilizing infrastructure located in Iran have been conducting computer network exploitation activity against public and private U.S. organizations, including Cleared Defense Contractors (CDCs), academic institutions, and energy sector companies. The actors typically utilize common computer intrusion techniques such as the use of TOR, open source reconnaissance, exploitation via SQL injection and web shells, and open source tools for further network penetration and persistence. Internet-facing infrastructures, such as web servers, are typical targets for this group. Once the actors penetrate a victim network, the actors exfiltrate network design information and legitimate user credentials for the victim network. Often times, the actors are able to harvest administrative user credentials and use the credentials to move laterally through a network.