Volume 4, Number 2 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Head 122 — HONG KONG POLICE FORCE
Head 122 — HONG KONG POLICE FORCE Controlling officer: the Commissioner of Police will account for expenditure under this Head. Estimate 2002–03................................................................................................................................... 12,445.8m Establishment ceiling 2002–03 (notional annual mid-point salary value) representing an estimated 34 597 non-directorate posts at 31 March 2002 reducing by 337 posts to 34 260 posts at 31 March 2003......................................................................................................................................... 9,473.1m In addition there will be 77 directorate posts at 31 March 2002 and at 31 March 2003. Capital Account commitment balance................................................................................................. 305.3m Controlling Officer’s Report Programmes Programme (1) Maintenance of Law and These programmes contribute to Policy Area 9: Internal Security Order in the Community (Secretary for Security). Programme (2) Prevention and Detection of Crime Programme (3) Reduction of Traffic Accidents Programme (4) Operations Detail Programme (1): Maintenance of Law and Order in the Community 2000–01 2001–02 2001–02 2002–03 (Actual) (Approved) (Revised) (Estimate) Financial provision ($m) 6,223.6 5,995.3 5,986.4 6,081.8 (–3.7%) (–0.1%) (+1.6%) Aim 2 The aim is to maintain law and order through the deployment of efficient and well-equipped uniformed police personnel throughout the land regions. Brief Description 3 Law -

What Are the Key Characteristics of Organised Crime? 7 How Does Organised Crime Affect Us? 8 How Are We Responding? 9
Correspondence should be addressed to: Chief Executive Officer Australian Crime Commission PO Box 1936 Canberra City ACT 2601 Telephone: 02 6243 6666 (from within Australia) 61 2 6243 6666 (international) Facsimile: 02 6243 6687 (from within Australia) 61 2 6243 6687 (international) Published May 2015 © Commonwealth of Australia 2015. This work is copyright. Apart from any use as permitted under the Copyright Act 1968, no part may be reproduced by any process without written permission from the Chief Executive Officer, Australian Crime Commission. ISSN 2202-3925 1 ORGANISED CRIME IN AUSTRALIA 2015 AUSTRALIAN CRIME COMMISSION CEO FOREWORD MR CHRIS DAWSON APM Organised Crime in Australia 2015 is the Australian Crime Commission’s biennial public report that delivers a current picture of the serious and organised crime environment in Australia. It outlines the existing and emerging organised crime threats impacting the Australian community and national interests. 2 Serious and organised crime is growing in sophistication and constantly adopting new and advanced technologies to undertake illegal activities. It exploits the internet and other technologies to target the community through activities such as online scams, cybercrime and the theft of personal identity information stored electronically. It is expanding its reach globally and injecting itself into new markets—both legitimate and illegitimate—in order to increase its opportunities to generate illicit wealth. It works to conceal unlawfully derived profits, seeking to intermingle those funds with legitimately earned money. These activities significantly affect the wellbeing of families and communities across Australia. Serious and organised crime diverts funds out of the legitimate economy and undermines the profitability of lawful businesses. -

Regulating Undercover Agents' Operations and Criminal
This document is downloaded from CityU Institutional Repository, Run Run Shaw Library, City University of Hong Kong. Regulating undercover agents’ operations and criminal Title investigations in Hong Kong: What lessons can be learnt from the United Kingdom and South Australia Author(s) Chen, Yuen Tung Eutonia (陳宛彤) Chen, Y. T. E. (2012). Regulating undercover agents’ operations and criminal investigations in Hong Kong: What lessons can be learnt Citation from the United Kingdom and South Australia (Outstanding Academic Papers by Students (OAPS)). Retrieved from City University of Hong Kong, CityU Institutional Repository. Issue Date 2012 URL http://hdl.handle.net/2031/6855 This work is protected by copyright. Reproduction or distribution of Rights the work in any format is prohibited without written permission of the copyright owner. Access is unrestricted. Page | 1 LW 4635 INDEPENDENT RESEARCH Topic: Regulating Undercover Agents’ Operations and Criminal Investigations in Hong Kong: What Lessons can be learnt from the United Kingdom and South Australia? Student Name: CHEN Yuen Tung Eutonia1 Date: 13th April 2012 Word Count: 9570 (excluding cover page, footnote and bibliography) Number of Pages: 39 Abstract It is not a dispute that undercover police officers have a proper role to play in contemporary law enforcement. However, there is no clear legislation in Hong Kong on the issue of whether the undercover agent is, at law, an offender of crime(s). This paper would examine the limitations of the prevailing undercover policing laws in Hong Kong and suggest possible recommendations. In particular, a comparative study of the United Kingdom and South Australia would be made to investigate whether Hong Kong should enact a legislation regulating undercover operations and criminal investigations. -
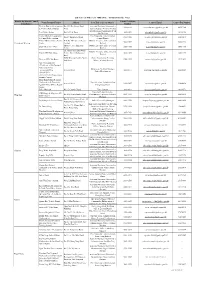
List of Access Officer (For Publication)
List of Access Officer (for Publication) - (Hong Kong Police Force) District (by District Council Contact Telephone Venue/Premise/FacilityAddress Post Title of Access Officer Contact Email Conact Fax Number Boundaries) Number Western District Headquarters No.280, Des Voeux Road Assistant Divisional Commander, 3660 6616 [email protected] 2858 9102 & Western Police Station West Administration, Western Division Sub-Divisional Commander, Peak Peak Police Station No.92, Peak Road 3660 9501 [email protected] 2849 4156 Sub-Division Central District Headquarters Chief Inspector, Administration, No.2, Chung Kong Road 3660 1106 [email protected] 2200 4511 & Central Police Station Central District Central District Police Service G/F, No.149, Queen's Road District Executive Officer, Central 3660 1105 [email protected] 3660 1298 Central and Western Centre Central District Shop 347, 3/F, Shun Tak District Executive Officer, Central Shun Tak Centre NPO 3660 1105 [email protected] 3660 1298 Centre District 2/F, Chinachem Hollywood District Executive Officer, Central Central JPC Club House Centre, No.13, Hollywood 3660 1105 [email protected] 3660 1298 District Road POD, Western Garden, No.83, Police Community Relations Western JPC Club House 2546 9192 [email protected] 2915 2493 2nd Street Officer, Western District Police Headquarters - Certificate of No Criminal Conviction Office Building & Facilities Manager, - Licensing office Arsenal Street 2860 2171 [email protected] 2200 4329 Police Headquarters - Shroff Office - Central Traffic Prosecutions Enquiry Counter Hong Kong Island Regional Headquarters & Complaint Superintendent, Administration, Arsenal Street 2860 1007 [email protected] 2200 4430 Against Police Office (Report Hong Kong Island Room) Police Museum No.27, Coombe Road Force Curator 2849 8012 [email protected] 2849 4573 Inspector/Senior Inspector, EOD Range & Magazine MT. -

Ethical Hacking
Ethical Hacking Alana Maurushat University of Ottawa Press ETHICAL HACKING ETHICAL HACKING Alana Maurushat University of Ottawa Press 2019 The University of Ottawa Press (UOP) is proud to be the oldest of the francophone university presses in Canada and the only bilingual university publisher in North America. Since 1936, UOP has been “enriching intellectual and cultural discourse” by producing peer-reviewed and award-winning books in the humanities and social sciences, in French or in English. Library and Archives Canada Cataloguing in Publication Title: Ethical hacking / Alana Maurushat. Names: Maurushat, Alana, author. Description: Includes bibliographical references. Identifiers: Canadiana (print) 20190087447 | Canadiana (ebook) 2019008748X | ISBN 9780776627915 (softcover) | ISBN 9780776627922 (PDF) | ISBN 9780776627939 (EPUB) | ISBN 9780776627946 (Kindle) Subjects: LCSH: Hacking—Moral and ethical aspects—Case studies. | LCGFT: Case studies. Classification: LCC HV6773 .M38 2019 | DDC 364.16/8—dc23 Legal Deposit: First Quarter 2019 Library and Archives Canada © Alana Maurushat, 2019, under Creative Commons License Attribution— NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) https://creativecommons.org/licenses/by-nc-sa/4.0/ Printed and bound in Canada by Gauvin Press Copy editing Robbie McCaw Proofreading Robert Ferguson Typesetting CS Cover design Édiscript enr. and Elizabeth Schwaiger Cover image Fragmented Memory by Phillip David Stearns, n.d., Personal Data, Software, Jacquard Woven Cotton. Image © Phillip David Stearns, reproduced with kind permission from the artist. The University of Ottawa Press gratefully acknowledges the support extended to its publishing list by Canadian Heritage through the Canada Book Fund, by the Canada Council for the Arts, by the Ontario Arts Council, by the Federation for the Humanities and Social Sciences through the Awards to Scholarly Publications Program, and by the University of Ottawa. -

2020 Cross-Border Corporate Criminal Liability Survey 2020 Cross-Border Corporate Criminal Liability Survey
2019 ANNUAL M&A REVIEW 2020 CROSS-BORDER CORPORATE CRIMINAL LIABILITY SURVEY 2020 CROSS-BORDER CORPORATE CRIMINAL LIABILITY SURVEY TABLE OF CONTENTS INTRODUCTION . 1 MIDDLE EAST . 106 GLOSSARY . 4 ISRAEL . 107 AFRICA . 5 SAUDI ARABIA. 113 SOUTH AFRICA. .. 6 UNITED ARAB EMIRATES . 117 ASIA PACIFIC . 10 NORTH AMERICA . 121 AUSTRALIA . .11 CANADA . 122 CHINA . 16 MEXICO . 126 HONG KONG . 20 UNITED STATES . 131 INDIA . 25 SOUTH AMERICA . .. 135 INDONESIA . 30 ARGENTINA . 136 JAPAN . 34 BRAZIL . 141 SINGAPORE . 38 CHILE . 145 TAIWAN (REPUBLIC OF CHINA) . 43 VENEZUELA . 149 CENTRAL AMERICA . 47 CONTACTS . 152 COSTA RICA . 48 EUROPE . 52 BELGIUM . 53 FRANCE . 57 GERMANY . 62 ITALY . 69 NETHERLANDS. .. 76 RUSSIA . 84 SPAIN . 87 SWITZERLAND . 92 TURKEY . 96 UKRAINE . 99 UNITED KINGDOM . 103 Jones Day White Paper 2020 CROSS-BORDER CORPORATE CRIMINAL LIABILITY SURVEY INTRODUCTION For any company, the risk that employees or agents may countries, and the ability of industry participants to engage in criminal conduct in connection with their work assert (accurately or inaccurately) that a competitor has and thereby potentially expose the company (or at least broken the law . Multinational companies are at ever- the responsible individuals) to criminal, administrative, increasing risk of aggressive criminal enforcement, and/or civil liability is ever present; for multinational often across numerous jurisdictions at once . companies, which are necessarily subject to the laws To be sure, aggressive enforcement of corporate of multiple jurisdictions, this risk is only heightened . crime can help ensure that such crime is appropriately How a company manages the risk of corporate criminal punished and deterred and that the rights and interests liability, in particular, can not only determine its success, of victims are honored through a criminal proceeding . -

Seventh United Nations Survey of Crime Trends and Operations of Criminal Justice Systems, Table Comments by Country
UNITED NATIONS NATIONS UNIES Office on Drugs and Crime Division for Policy Analysis and Public Affairs Seventh United Nations Survey of Crime Trends and Operations of Criminal Justice Systems, covering the period 1998 - 2000 Comments by Table 1. Police personnel, by sex, and financial resources Alternative reference date to 31 December POLICE 1. Police personnel, by sex, and financial resources Alternative reference date to 31 December England & Wales 30 September Japan 1 April 2. Crimes recorded in criminal (police) statistics, by type of crime including attempts to commit crimes What is (are) the source(s) of the data provided in this table? Australia Recorded Crime Statistics 2000 (cat: 4510.0) Australian Bureau of Statistics (ABS) Azerbaijan Reports on crimes Barbados Royal Barbados Police Force, Research and Development Department Bulgaria Ministry of Interior - Regular Report Canada Canadian Centre for Justice Statistics, Uniform Crime Report and Homicide Survey, Statistics Canada. Chile S.I.E.C (Sistema Integrado Estadistico de Carabineros) Colombia Policia Nacional, Direccion Central de Policia Judicial, Centro de Investigaciones Criminologicas Côte d'Ivoire Direction Centrale de la police Judiciaire Czech Republic Recording and Statistical System of Crime maintained by the Police of the Czech Republic Denmark Statistics of reported crimes, National Commissioner of Police, Department E. Dominica Criminal Records Office Friday, March 19, 2004 Page 1 of 22 2. Crimes recorded in criminal (police) statistics, by type of crime includi What is (are) the source(s) of the data provided in this table? England & Wales Recorded crime database Finland Statistics Finland: Yearbook of Justice Statistics (SVT) Georgia Ministry of Internal Affairs of Georgia. -

ANZSOC Newsletter 4(2)
Volume 4, Issue 2 September 2007 From the desk of the President: ANZSOC’s history and identity A new development for the Society is the ANZSOC Let the Conference begin Presidential speaker. With the endorsement of the Committee of Management, I chose Mark Finnane as the inaugural speaker. In recent years Mark has Welcome all to the th turned his historian’s eye to how criminology 20 annual developed in Australia by examining its key people, conference of the institutions (such as ANZSOC and the Australian Australian and New Institute of Criminology), and links to other countries. Zealand Society of His conference plenary will canvass these themes, Criminology! with commentary by longstanding members of the Our senior members Society. Following his plenary is a panel session, will know that the ‘What’s in a Name?’, which considers the Society’s term ‘annual’ is identity in a global context. used loosely because this year The bottom line marks the 40th A major development this year was changing the anniversary of the membership fees. Current fees have not been founding of the Society. David Biles, foundation covering the costs of publishing, printing, and mailing honorary secretary, volunteered to bring the Society the journal to our members. There was a good deal of into being (see Biles's tribute to Allen Bartholomew in soul searching among the Committee of Management the ANZJCrim 2005, Vol. 38, No. 1, pp. 1-3). He wrote about how best to balance the competing interests of letters, made phone calls, drafted a Constitution, and fiscal responsibility and maintaining a strong identified people who could serve as officers and membership base. -

New South Wales Recorded Crime Statistics
Statistical Report Series NEW SOUTH WALES RECORDED CRIME STATISTICS Quarterly Update September 2017 NSW Statistical Areas and Local Government Areas NSW Bureau of Crime Statistics and Research NSW Recorded Crime Statistics, September Quarter 2017 2 CONTENTS SECTION 1: OVERVIEW OF TRENDS IN RECORDED CRIME, BY OFFENCE TYPE . 3 Table 1.1 Trends in recorded criminal incidents for major offences, over the 60 months to September 2017, NSW . 4 Table 1.2 Number and trends in recorded criminal incidents for 62 offences, over the 24 months to September 2017, NSW . 5 SECTION 2: TRENDS, RATE COMPARISONS AND RECORDED CRIMINAL INCIDENTS FOR MAJOR OFFENCES, NSW REGIONS AND LGAS . 7 Table 2.1A Trends in recorded criminal incidents for major offences, over the 24 months to September 2017, NSW SAs . 8 Table 2.1B Ratio to NSW rate of recorded criminal incidents per 100,000 population for major offences, over the 12 months to September 2017, NSW SAs . 8 Table 2.1C Number of recorded criminal incidents for major offences, over the 12 months to September 2017, NSW SAs . 9 Table 2.1D Number of recorded criminal incidents for major offences, over the 12 months to September 2016, NSW SAs . 9 Table 2.2A Trends in recorded criminal incidents for major offences, over the 24 months to September 2017, Greater Sydney SAs . 10 Table 2.2B Ratio to NSW rate of recorded criminal incidents per 100,000 population for major offences, over the 12 months to September 2017, Greater Sydney SAs . 10 Table 2.2C Number of recorded criminal incidents for major offences, over the 12 months to September 2017, Greater Sydney SAs . -

A Report on the Current Attitudes and Experiences of Hong Kong Police Officers
A report on the current attitudes and experiences of Hong Kong police officers Professor Ben Bradford and Dr Julia Yesberg 2nd December 2019 1 Contents Executive Summary ....................................................................................... 3 Introduction .................................................................................................... 5 1. Background ................................................................................................ 5 2. Methodology ............................................................................................... 8 3. Findings .................................................................................................... 10 3.1 Experiences, activities and attitudes ........................................................... 10 3.1.1 General views on police-public relations ................................................................ 10 3.1.2 Peaceful Public Order Events ................................................................................ 12 3.1.3 Violent Public Order Events ................................................................................... 15 3.2 Work patterns, confrontation, use of force and injury ............................... 17 3.3 Relationships within the police organisation .............................................. 19 3.3.1 Police identity ......................................................................................................... 19 3.3.2 Peer support .......................................................................................................... -

Audrey Fagan
Valedictory – Audrey Fagan Delivered by AFP Commissioner many positive comments from parents Mick Keelty APM of juveniles about her caring and professional approach to her duties. “It is with much sadness that we join During 1982, Audrey was also sworn in together today to farewell a dear friend as a Special Constable of the NSW Police. and one the AFP’s fi nest police offi cers – Assistant Commissioner Audrey Ann Audrey soon displayed her capability as Fagan. an investigator and the following year was temporarily moved to the National It is testament to Audrey’s distinguished Criminal Investigation Branch where she career and commitment to the Canberra investigated specialist fraud off ences as community that the AFP is joined today part of the Medifraud Squad in the AFP’s by so many of the community’s leaders to Central Region of South Australia. pay their respects. In September 1985, Audrey commenced During her 26-year career with the AFP, duties as a detective at the Woden CIB Audrey made an indelible mark on our and in August 1986 Audrey transferred organisation, not only in an operational to Christmas Island where she undertook sense but as a leader and a fi ne role specialist community policing and Department and in the same year model to women, not just within the AFP national policing duties for the AFP. completed her training to be designated but the broader community. Audrey’s role in the investigation of a as a detective. In 1992 Audrey took up She was a dedicated mother and wife murder on the Island attracted praise from duties in the Internal Investigation Branch. -

Australian Federal Police
Chapter 10 Australian Federal Police 10.1 Australian police have been involved in peacekeeping operations since 1964 when officers were sent to Cyprus as part of the United Nations Force (UNFICYP).1 However, police involvement in overseas deployments, including peacekeeping, has increased in the last decade: the Australian Federal Police (AFP) is currently deployed in Cyprus, Solomon Islands, Sudan, Timor-Leste, Nauru, Tonga, Vanuatu, Cambodia and Afghanistan.2 As of January 2008, the total number of AFP officers deployed to international missions was 323. This number rose to 393 with the additional 70 who went to Timor-Leste in February 2008. The majority of deployed AFP officers are serving in peacekeeping operations in Solomon Islands (208) and in Timor-Leste (130).3 10.2 In this chapter, the committee examines the changing nature of peacekeeping operations and its impact on the AFP. It looks at the AFP's preparedness and capacity to meet the growing demands of these operations and its pre-deployment training regime, taking account of any additional skills required for peacekeeping. Changing AFP contribution 10.3 Police carry out the function of maintaining law and order for the community. Their role in peacekeeping operations, while consistent with this broad function, presents particular challenges for AFP personnel. They are expected to deliver a police service and exercise discretion in a country that may have a different political and legal system and where law and order and the judicial system are failing or broken down completely. Increasingly, they are required to operate in multidimensional situations and actively participate in capacity building.