APT1: Exposing One of China's Cyber Espionage Units | Mandiant | Fireeye
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oldschool E-Mail Setup Eine Freakshow
Oldschool E-mail Setup Eine Freakshow [email protected] Chemnitzer Linuxtage, 2016 (Screenshot GMX vor >15 Jahren: Waybackmachine zu www.gmx.net) (Screenshot GMX heute) (Screenshot Gmail heute) Lösungen? ● Claws ● Mutt ● Eudora ● Netscape Navigator ● Evolution ● Opera M2 ● GMX ● Outlook ● Gnus ● SquirrelMail ● Hotmail ● The Bat! ● Hushmail ● Thunderbird ● KMail ● … Flußgrafik Email Netz MTA MRA MDA MUA MSA MTA Netz Hipster! ● KISS ● YAGNI ● DRY ● NIH ● Divide And Conquer ● Everything is a file ● No vendor lock-in ● Mißtraue Autoritäten – fördere Dezentralisierung Netz Netz Emails Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools mbox Maildir mh Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools mbox Maildir mh tmp 1439306571.1269_0.elvis ~/Post/Technik/Wikitech new 1448267819.5940_0.spencer ... 1457079728.2000_0.spencer:2, cur 1456839383.9873_0.nepomuk:2,SR 1457166567.23654_0.spencer:2,S ... Client, den ich Remote verwenden kann Leicht erweiterbar Filter Adressen Netz Netz Abholen Pull Subject Maildir Keine Spuren X-List-ID am Server Beliebige Header Client, den ich Remote verwenden kann Leicht erweiterbar Filter Adressen Netz Netz Abholen Pull Subject Maildir Keine Spuren X-List-ID am Server Beliebige Header fetchmail getmail mpop .. -

Modeling and Simulation of Shanghai MAGLEV Train Transrapid with Random Track Irregularities
Modeling and Simulation of Shanghai MAGLEV Train Transrapid with Random Track Irregularities Prof. Shu Guangwei M.Sc. Prof. Dr.-Ing. Reinhold Meisinger Prof. Shen Gang Ph.D. Shanghai Institute of Technology, Shanghai, P.R. China Nuremberg University of Applied Sciences, Nuremberg, Germany Tongji University, Shanghai, P.R. China Abstract The MAGLEV Transrapid is a kind of new type high speed train in the world which is levitated and gui- ded over the track using electro magnetic forces. Because the electro magnets are unstable, they ha- ve to be controlled. Since 2002 the worldwide first commercial use of such a high speed train based on German technology is running successfully in Shanghai Pudong Airport, P.R.China. In this paper modeling of the high speed MAGLEV train Transrapid is discussed, which considered the whole mechanical system of one vehicle with optimized suspension parameters and all controlled electro magnet pairs in vertical and lateral directions. The dynamical simulation code is generated with MATLAB/SIMILINK. For the design of the control system, the optimal Linear Quadratic Control for minimum control energy is used for each single electro magnet. The simulation results are presen- ted with the given vertical and lateral random track irregularities. The research work was carried out together with Prof. Shen Gang, Ph.D. during the time Prof. Dr. Meisinger was visiting professor in Shanghai 2006 and Prof. Shu Guangwei, M.Sc. was visiting profes- sor in Nuremberg 2007. ISSN 1616-0762 Sonderdruck Schriftenreihe der Georg-Simon-Ohm-Fachhochschule Nürnberg Nr. 39, Juli 2007 Schriftenreihe Georg-Simon-Ohm-Fachhochschule Nürnberg Seite 3 1. -

Getting to Yes with China in Cyberspace
Getting to Yes with China in Cyberspace Scott Warren Harold, Martin C. Libicki, Astrid Stuth Cevallos C O R P O R A T I O N For more information on this publication, visit www.rand.org/t/rr1335 Library of Congress Cataloging-in-Publication Data ISBN: 978-0-8330-9249-6 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2016 RAND Corporation R® is a registered trademark Cover Image: US President Barack Obama (R) checks hands with Chinese president Xi Jinping after a press conference in the Rose Garden of the White House September 25, 2015 in Washington, DC. President Obama is welcoming President Jinping during a state arrival ceremony. Photo by Olivier Douliery/ABACA (Sipa via AP Images). Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions.html. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. -

Movie Tv Sho Audio Radio
70 FILM REVIEWS MOVIES 71 NEW MOVIES ONBOARD 72 MOVIES TV SHOWS 74 TV SHOWS AUDIO Entertainment 76 AUDIO/RADIO RADIO © 2018 20TH CENTURY FOX. ALL RIGHTS RESERVED. BAD TIMES AT THE EL ROYALE FILM REVIEWS WANT HELP WITH WHAT TO WATCH THIS MONTH? FILMMAKER AND DIRECTOR KAM RASLAN MAKES THE CASE FOR THESE THREE MOVIES. THE INCREDIBLES Is The Incredibles the best animated movie ever? Yes. Yes, it is. It’s hilariously funny, exciting, moving and visually beautiful. A family of superheroes have to live in witness protection as normal people because superheroes have been deemed a menace to society. Naturally, Mr Incredible hates his boring life as an insurance salesman and his goingplacesmagazine.com children have to hide their superhero skills. But when an opportunity for a return to the old life comes knocking, Mr Incredible puts his entire family at risk, which sounds like a job LOGAN for Elastigirl. Is Logan the best superhero movie ever? EDGE OF TOMORROW Probably. A thunderous Hugh Jackman Because it was made all the way back in Is Edge of Tomorrow the best science fiction | 70 is Wolverine one last time as he plays a 2004, the animation for The Incredibles may movie ever? Maybe not, but it’s definitely | January 2019 January | reluctant father figure to the stunningly not seem quite as plush as, say, Zootopia, the best science fiction movie starring Tom intense young actress Dafne Keen. On a but director Brad Bird (who made his name Cruise, and when it comes to big-budget desperate journey from Mexico to the far with The Simpsons) created such a complete action Hollywood movies, nobody delivers north, the pair are perfectly matched as universe that you instantly forget. -

In Re Equifax Inc. Securities Litigation 17-CV-03463-Consolidated Class
Case 1:17-cv-03463-TWT Document 49 Filed 04/23/18 Page 1 of 198 UNITED STATES DISTRICT COURT NORTHERN DISTRICT OF GEORGIA ATLANTA DIVISION IN RE EQUIFAX INC. SECURITIES Consolidated Case No. LITIGATION 1:17-cv-03463-TWT CONSOLIDATED CLASS ACTION COMPLAINT FOR VIOLATIONS OF THE FEDERAL SECURITIES LAWS Case 1:17-cv-03463-TWT Document 49 Filed 04/23/18 Page 2 of 198 TABLE OF CONTENTS Page I. PRELIMINARY STATEMENT .....................................................................2 II. PARTIES .......................................................................................................10 A. Lead Plaintiff ...................................................................................... 10 B. Defendants .......................................................................................... 10 1. Equifax, Inc. ............................................................................. 10 2. Individual Defendants .............................................................. 12 III. JURISDICTION AND VENUE ....................................................................13 IV. SUMMARY OF THE FRAUD .....................................................................13 A. Equifax’s Business is to Collect and Sell Sensitive Personal Information About Global Consumers ............................................... 13 B. Defendants Knew that Securing the Information Equifax Collected Was Critical to the Company’s Business ........................... 16 C. Defendants Issue Statements Touting Cybersecurity, Compliance with -

THE PROTECTIVE STATE the PLANT FLOOR? the Evolving Role of Governments in Cybersecurity
BROUGHT TO YOU BY THE VISIONEXPERTISE DELIVERED STRAIGHT FROM THE FRONTLINES OF CYBER ATTACKS PAGE 3 STATE OF THE NATIONS A global look at the rise in State sponsered cyber attacks in 2018 PAGE 4 A FINANCIAL STRONGHOLD How one bank is winning the war on cyber crime PAGE 6 WHAT ABOUT THE PROTECTIVE STATE THE PLANT FLOOR? The evolving role of Governments in cybersecurity different threats. With cybersecurity vital to a governments are not even the primary security POLITICAL properly functioning and prosperous economy, provider, such as when they don’t provide it is critical that governments take the lead, and close supervision of, or operational control The role of governments as their that this is recognized by its citizens. over, critical infrastructures operated by the nations’ primary provider of private sector. security against all threats is as So far, the 21st century has seen continued compelling as ever. Yet few still wide scale deregulation and privatisation, This changing global landscape shouldn’t Our six subversive concerns for with many nations’ critical infrastructure – in mean a lesser responsibility for governments industrial environments have difficulty in grasping the rapid increase in interconnectedness and sectors such as energy, transport, finance as legitimate providers of security, but rather and medicine – now in the hands of the that they should work to understand the interdependency to determine how private sector. These sectors are constantly changing world and their role within this new best to use a Regulate, Facilitate, under threat, not least because of increased environment of increasing interconnectedness. PAGE 8 FOLLOW Collaborate (RFC) model for the THE MONEY globalisation of societies and economies. -

View Final Report (PDF)
TABLE OF CONTENTS TABLE OF CONTENTS I EXECUTIVE SUMMARY III INTRODUCTION 1 GENESIS OF THE PROJECT 1 RESEARCH QUESTIONS 1 INDUSTRY SITUATION 2 METHODOLOGY 3 GENERAL COMMENTS ON INTERVIEWS 5 APT1 (CHINA) 6 SUMMARY 7 THE GROUP 7 TIMELINE 7 TYPOLOGY OF ATTACKS 9 DISCLOSURE EVENTS 9 APT10 (CHINA) 13 INTRODUCTION 14 THE GROUP 14 TIMELINE 15 TYPOLOGY OF ATTACKS 16 DISCLOSURE EVENTS 18 COBALT (CRIMINAL GROUP) 22 INTRODUCTION 23 THE GROUP 23 TIMELINE 25 TYPOLOGY OF ATTACKS 27 DISCLOSURE EVENTS 30 APT33 (IRAN) 33 INTRODUCTION 34 THE GROUP 34 TIMELINE 35 TYPOLOGY OF ATTACKS 37 DISCLOSURE EVENTS 38 APT34 (IRAN) 41 INTRODUCTION 42 THE GROUP 42 SIPA Capstone 2020 i The Impact of Information Disclosures on APT Operations TIMELINE 43 TYPOLOGY OF ATTACKS 44 DISCLOSURE EVENTS 48 APT38 (NORTH KOREA) 52 INTRODUCTION 53 THE GROUP 53 TIMELINE 55 TYPOLOGY OF ATTACKS 59 DISCLOSURE EVENTS 61 APT28 (RUSSIA) 65 INTRODUCTION 66 THE GROUP 66 TIMELINE 66 TYPOLOGY OF ATTACKS 69 DISCLOSURE EVENTS 71 APT29 (RUSSIA) 74 INTRODUCTION 75 THE GROUP 75 TIMELINE 76 TYPOLOGY OF ATTACKS 79 DISCLOSURE EVENTS 81 COMPARISON AND ANALYSIS 84 DIFFERENCES BETWEEN ACTOR RESPONSE 84 CONTRIBUTING FACTORS TO SIMILARITIES AND DIFFERENCES 86 MEASURING THE SUCCESS OF DISCLOSURES 90 IMPLICATIONS OF OUR RESEARCH 92 FOR PERSISTENT ENGAGEMENT AND FORWARD DEFENSE 92 FOR PRIVATE CYBERSECURITY VENDORS 96 FOR THE FINANCIAL SECTOR 96 ROOM FOR FURTHER RESEARCH 97 ACKNOWLEDGEMENTS 98 ABOUT THE TEAM 99 SIPA Capstone 2020 ii The Impact of Information Disclosures on APT Operations EXECUTIVE SUMMARY This project was completed to fulfill the including the scope of the disclosure and capstone requirement for Columbia Uni- the disclosing actor. -

Mandarin Oriental Pudong, Shanghai Celebrates Opening With
MANDARIN ORIENTAL PUDONG, SHANGHAI CELEBRATES OPENING WITH ARTISTIC FLAIR AND TWO TEMPTING OFFERS Mandarin Oriental’s newest luxury landmark on the east bank of the Huangpu River debuts with the most extensive hotel collection of Chinese contemporary art in Shanghai, and two tantalizing opening offers Hong Kong, 25 April, 2013 -- Mandarin Oriental Hotel Group is delighted to announce the opening of its second city hotel in China, Mandarin Oriental Pudong, Shanghai. In celebration, the hotel is offering guests two tantalizing packages both priced from CNY 3,600 and available from 25 April to 30 September 2013. Mandarin Oriental Pudong, Shanghai celebrated its opening with the official launch of the hotel’s impressive art collection, curated by the renowned Art Front Gallery and featuring 4,000 original artworks displayed throughout the public spaces and guestrooms. Joining the celebrations were Associate Professor Li Xiao Feng of Fine Arts College Shanghai University, as well as leading Chinese artists Miao Tong, Pan Wei and Kang Qing. “We are delighted to open our newest hotel in this dynamic city,” said Andrew Hirst, Director of Operations – Asia. “Mandarin Oriental Pudong, Shanghai is set to become a new luxury landmark for guests seeking the finest in service and facilities, as well as a riverfront destination for art connoisseurs.” “Mandarin Oriental Pudong, Shanghai provides a stunning backdrop from which to showcase some of China’s most exciting artworks, and is sure to become a destination for both local and international art lovers,” -
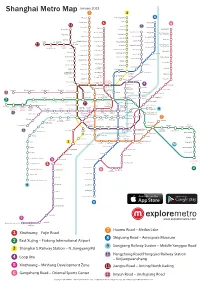
Shanghai Metro Map 7 3
January 2013 Shanghai Metro Map 7 3 Meilan Lake North Jiangyang Rd. 8 Tieli Rd. Luonan Xincun 1 Shiguang Rd. 6 11 Youyi Rd. Panguang Rd. 10 Nenjiang Rd. Fujin Rd. North Jiading Baoyang Rd. Gangcheng Rd. Liuhang Xinjiangwancheng West Youyi Rd. Xiangyin Rd. North Waigaoqiao West Jiading Shuichan Rd. Free Trade Zone Gucun Park East Yingao Rd. Bao’an Highway Huangxing Park Songbin Rd. Baiyin Rd. Hangjin Rd. Shanghai University Sanmen Rd. Anting East Changji Rd. Gongfu Xincun Zhanghuabang Jiading Middle Yanji Rd. Xincheng Jiangwan Stadium South Waigaoqiao 11 Nanchen Rd. Hulan Rd. Songfa Rd. Free Trade Zone Shanghai Shanghai Huangxing Rd. Automobile City Circuit Malu South Changjiang Rd. Wujiaochang Shangda Rd. Tonghe Xincun Zhouhai Rd. Nanxiang West Yingao Rd. Guoquan Rd. Jiangpu Rd. Changzhong Rd. Gongkang Rd. Taopu Xincun Jiangwan Town Wuzhou Avenue Penpu Xincun Tongji University Anshan Xincun Dachang Town Wuwei Rd. Dabaishu Dongjing Rd. Wenshui Rd. Siping Rd. Qilianshan Rd. Xingzhi Rd. Chifeng Rd. Shanghai Quyang Rd. Jufeng Rd. Liziyuan Dahuasan Rd. Circus World North Xizang Rd. Shanghai West Yanchang Rd. Youdian Xincun Railway Station Hongkou Xincun Rd. Football Wulian Rd. North Zhongxing Rd. Stadium Zhenru Zhongshan Rd. Langao Rd. Dongbaoxing Rd. Boxing Rd. Shanghai Linping Rd. Fengqiao Rd. Zhenping Rd. Zhongtan Rd. Railway Stn. Caoyang Rd. Hailun Rd. 4 Jinqiao Rd. Baoshan Rd. Changshou Rd. North Dalian Rd. Sichuan Rd. Hanzhong Rd. Yunshan Rd. Jinyun Rd. West Jinshajiang Rd. Fengzhuang Zhenbei Rd. Jinshajiang Rd. Longde Rd. Qufu Rd. Yangshupu Rd. Tiantong Rd. Deping Rd. 13 Changping Rd. Xinzha Rd. Pudong Beixinjing Jiangsu Rd. West Nanjing Rd. -

Analyzing the Evolution of China's Cyber Espionage Campaigns
Getting Harder to Catch Analyzing the Evolution of China’s Cyber Espionage Campaigns against the United States through a Case Study of APT1 -------- Winnona DeSombre – Comp116 Security Final Paper Advisor: Ming Chow 1. Abstract The relationship between China and the United States is arguably one of the more thorny dynamics in the sphere of international politics, complicated further by each country’s increasing cyber espionage and cyber warfare capabilities. As early as 2007, the US-China Economic and Security Review Commission has labeled China’s espionage efforts “the single greatest risk to the security of American technologies”1. However, as cyber security is a relatively new field in international relations, there is little set precedence for pressing charges or taking other action against individuals or groups conducting cyber attacks or espionage. This paper is composed of three parts: part one contains an overview of China-US relations within the context of the cyber realm and dilemmas in the international sphere regarding formulation of cyber security policy. Part two is a case study of the hacker unit APT1, a hacker unit argued to be the Chinese People’s Liberation Army Unit 61398, which covers both APT1’s history and an analysis of its cyber espionage campaigns. Part three reviews the general trends of APT1 within the context of the 2015 US-China Cyber Agreement and China-US relations regarding cyber security in general, and how the trends can possibly impact future actions of international actors and state-sponsored hacker groups. 2. To the Community: Defining Critical Infrastructure & Setting Policy Boundaries Policy often moves at a slower pace than technical innovation, especially when compared to the exponential rates of technological change in cyber capabilities. -

Cineasia Attendee
HONG KONG CONVENTION & EXHIBITION CENTRE 6-8 DECEMBER 2016 | CINEASIA.COM /CINEASIAEXPO @CINEASIAHK PRESENTING SPONSOR: 2016 ATTENDEE BROCHURE THE ASIAN MARKETPLACE 4 of the T OP TEN The box office in the biggest Asian INTERNATIONAL BOX markets, namely China, Japan, India, OFFICE MARKETS South Korea, Taiwan and Indonesia totaled ARE IN ASIA: $10.5 billion in 2015, just behind the $11.8 CHINA, JAPAN, INDIA, billion achieved in the US and Canada. & SOUTH KOREA WHAT THIS MEANS FOR YOU The Asia-Pacific market continues to be one of the most exciting territories in the world for the movie exhibition business, both for its astonishingly rapid growth and for the high presentation standards of its cinemas. Only at CineAsia will attendees get the chance to hear about the current trends and new state-of-the-art technologies. Nowhere else in Asia can you accomplish as much in a short period of time to sustain, and help grow, your business in the year to come. Join your cinema exhibition, distribution, and motion picture industry colleagues to network; and see product presentations and screenings of major Hollywood films soon to be released in Asia. Attendees will also get the opportunity to visit the Trade Show where you will find the latest equipment, products, and technologies to help make your theatre a must-attend destination. WHY OVER LEARN ABOUT THE LATEST TECHNOLOGICAL ADVANCES AND 1,000 NEWEST TRENDS IN CINEMA ATTENDEES GAIN WITH INSIGHT INTO THE ISSUES FACING THE INDUSTRY 600 FIND TRADE SHOW OUT HOW TO MAKE YOUR THEATRE MORE PROFITABLE EXHIBITORS NETWORK WITH INDUSTRY PEERS TO FORM LASTING BUSINESS RELATIONSHIPS DISCOVER NEW CONTENT, PRODUCTS, SERVICES, TECHNOLOGIES, AND CONCESSIONS AT THE TRADE SHOW TO ENHANCE THE MOVIE-GOING EXPERIENCE SEE PRODUCT PRESENTATIONS AND SCREENINGS FROM MAJOR HOLLYWOOD STUDIOS HONOR THOSE WHO HAVE MADE NOTABLE CONTRIBUTIONS IN THE INDUSTRY DURING THE AWARDS CEREMONY CLICK TO: #CINEASIA REGISTER BOOK HOTEL CONNECT FOLLOW LIKE NETWORK. -

APT28: a Window Into Russia's Cyber Espionage Operations? | Fireeye
SPECIAL REPORT APT28: A WINDOW INTO RUSSIA’S CYBER ESPIONAGE OPERATIONS? SECURITY REIMAGINED APT 28: A Window into Russia’s Cyber Espionage Operations? CONTENTS EXECUTIVE SUMMARY ................................................................................................................................................................................................................................................................................... 3 APT28 TARGETING REFLECTS RUSSIAN INTERESTS ........................................................................................................................................................................ 6 APT28 interest in the Caucasus, Particularly Georgia ........................................................................................................................................................... 7 APT28 Targeting of the Georgian Ministry of Internal Affairs (MIA) ....................................................................................... 8 APT28 Targeting of the Georgian Ministry of Defense ....................................................................................................................................... 9 APT28 Targeting a Journalist Covering the Caucasus ...................................................................................................................................... 10 APT28’s Other Targets in the Caucasus ......................................................................................................................................................................................