The Art & Skill of Radio-Telegraph (3Rd Edition)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
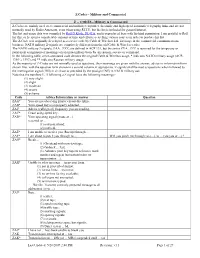
Z-Signals Are Completely Different from the Old Cable & Wireless Codes
Z Codes – Military and Commercial Z - CODES - Military & Commercial Z-Codes are mainly used over commercial and military teleprinter, facsimile and high speed automatic telegraphy links and are not normally used by Radio Amateurs, even when using RTTY, but the list is included for general interest. The list and usage data was compiled by Ralf D.Kloth, DL4TA, and is reproduced here with his kind permission. I am grateful to Ralf for this, as he spent a considerable amount of time and effort researching various sources in order to produce his list. The Z-Code was originally developed as a service code by Cable & Wireless Ltd. for usage in the commercial communications business. NATO military Z-signals are completely different from the old Cable & Wireless codes. The NATO military Z-signals, ZAA...ZXZ, are defined in ACP 131, but the series ZYA...ZZZ is reserved for the temporary or permanent assignment of meanings on an intra-military basis by any nation, service or command. In the following table, a non-annotated code denotes the original Cable & Wireless usage, * indicates NATO military usage (ACP- 131(E), 1997) and ** indicates Russian military usage. As the majority of Z-Codes are not normally used as questions, their meanings are given with the answer, advice or information form shown first, with the question form shown in a second column, if appropriate. Z signals shall be read as questions when followed by the interrogation signal (IMI) in civil use or preceded by the prosign (INT) in NATO military use. Note that the numbers 1...5 following a Z signal have the following meanings:- (1) very slight (2) slight (3) moderate (4) severe (5) extreme Code Advice Information or Answer Question ZAA* You are not observing proper circuit discipline. -

Printf and Primitive Types
CS 241 Data Organization using C printf and Primitive Types Instructor: Joel Castellanos e-mail: [email protected] Web: http://cs.unm.edu/~joel/ Office: Farris Engineering Center Room 2110 8/29/2019 1 Read: Kernighan & Ritchie Read ◼ Due Thursday, Aug 22 1.1: Getting Started 1.2: Variables and Arithmetic Expressions 1.3: The For Statement 1.4: Symbolic Constants ◼ Due Tuesday, Aug 27 (first iclicker quiz) 1.5: Character Input and Output ◼ Due Thursday, Aug 29 1.6: Arrays 2 2 1 Quiz: Basic Syntax One of these things is not like the others. One of these things does not belong. Can you tell which thing is not like the others before the end of this quiz? a) int a = 40 * 2*(1 + 3); b) int b = (10 * 10 * 10) + 2 c) int c = (2 + 3) * (2 + 3); d) int d = 1/2 + 1/3 + 1/4 + 1/5 + 1/6; e) int e = 1/2 - 1/4 + 1/8 - 1/16; 3 3 printf function printf("Name %s, Num=%d, pi %10.2f", "bob", 123, 3.14 ); Output: Name bob, Num=123, pi 3.14 printf format specifiers: %s string (null terminated char array) %c single char %d signed decimal int %f float %10.2f float with at least 10 spaces, 2 decimal places. %lf double 4 4 2 printf function: %d //%d: format placeholder that prints an int as a // signed decimal number. #include <stdio.h> void main(void) { int x = 512; Output: printf("x=%d\n", x); x=512 printf("[%2d]\n", x); [512] printf("[%6d]\n", x); [ 512] printf("[%-6d]\n", x); [512 ] printf("[-%6d]\n", x); [- 512] } 5 5 printf function: %f #include <stdio.h> void main(void) { float x = 3.141592653589793238; double z = 3.141592653589793238; printf("x=%f\n", x); printf("z=%f\n", z); printf("x=%20.18f\n", x); printf("z=%20.18f\n", z); } x=3.141593 Output: z=3.141593 x=3.141592741012573242 6 z=3.141592653589793116 6 3 Significant Figures Using /usr/bin/gcc on moons.unm.edu, a float has 7 significant figures. -

The Compression Problem Computational Thinking in This Discussion, We Will Look at the Compression Problem
Squeezing Ten Pounds of Data in a Five Pound Sack - or - The Compression Problem Computational Thinking In this discussion, we will look at the compression problem. Along the way, we will see several examples of computational thinking: • representations allow the computer to store and work with letters, images, or music by representing them with a numeric code; • patterns or repeated strings in text can be used by a computer for compres- sion; • index tables allow us to replace a long idea with a short word or number; Reading assignment Read Chapter 7, pages 105{121, \9 Algorithms that Changed the Future". The Compression Problem for Traveling When you pack for a trip, you want to minimize the number of suitcases and bags you take, but maximize the things you can transport. Sometimes it takes several repackings, rolling and squashing and rearranging, before you are satisfied. The Compression Problem for File Storage Your computer hard disk has a limited amount of storage. The information in a single movie or song could easily fill up your entire computer memory. This doesn't happen because the information is compressed in several ways. The Compression Problem for Data Transmission Data must be transferred from one place to another, over networks with limited capacity. In North America, 70% of Internet traffic involves services that are streaming data, such as movies or music. When the local network is overloaded, a movie becomes unwatchable, music becomes noise, users are dissatisfied. Solving the compression problem with more capacity One solution to these problems is to increase capacity: Buy more suitcases or bigger ones. -

Ascii, Baudot, and the Radio Amateur
ASCII, BAUDOT AND THE RADIO AMATEUR George W. Henry, Jr. K9GWT Copyright © 1980by Hal Communications Corp., Urbana, Illinois HAL COMMUNICATIONS CORP. BOX365 ASCII, BAUDOT, AND THE RADIO AMATEUR The 1970's have brought a revolution to amateur radio RTTY equipment separate wire to and from the terminal device. Such codes are found in com and techniques, the latest being the addition of the ASCII computer code. mon use with computer and line printer devices. Radio amateurs in the Effective March 17, 1980, radio amateurs in the United States have been United States are currently authorized to use either the Baudot or ASCII authorized by the FCC to use the American Standard Code for Information serial asynchronous TTY codes. Interchange(ASCII) as well as the older "Baudot" code for RTTY com munications. This paper discusses the differences between the two codes, The Baudot TTY Code provides some definitions for RTTY terms, and examines the various inter facing standards used with ASCII and Baudot terminals. One of the first data codes used with mechanical printing machines uses a total of five data pulses to represent the alphabet, numerals, and symbols. Constructio11 of RTTY Codes This code is commonly called the Baudot or Murray telegraph code after the work done by these two pioneers. Although commonly called the Baudot Mark Ull s,.ce: code in the United States, a similar code is usually called the Murray code in other parts of the world and is formally defined as the International Newcomers to amateur radio RTTY soon discover a whole new set of terms, Telegraphic Alphabet No. -

A Look at Telegraph Codes
Compression, Correction, Confidentiality, and Comprehension: A Look at Telegraph Codes Steven M. Bellovin Columbia University [email protected] Abstract Telegraph codes are a more-or-less forgotten part of technological history. In their day, though, they were ubiquitous and sophisticated. They also laid the groundwork for many of today’s communications technologies, including encryption, compression, and error correction. Beyond that, reading them pro- vides a snapshot into culture. We look back, describing them in modern terms, and noting some of the tradeoffs considered. 1 Introduction Most cryptologists have heard of telegraph codes. Often, though, our knowledge is cursory. We’ve forgotten what we read in Kahn [9], and perhaps remember little more than the basic concept: a word, phrase, or sentence is represented by a single codeword. In fact, telegraph codes were far more sophisticated, and laid the groundwork for many later, fundamental advances. Looked at analytically, telegraph codes fulfilled four primary functions: compression, correction, confi- dentiality, and comprehension. Beyond that, they offer a window into the past: the phrases they can be used to represent give insight into daily lives of the time. This paper, based primarily on my own small collection of codebooks, illustrates some of these points. For typographical simplicity, I have written codewords LIKE THIS, while plaintext is written this way. 2 Compression Compression was the original goal of telegraph codes. Early trans-Atlantic telegrams were extremely expen- sive — $100 for twenty words in 1866 [8] — so brevity was very important. Early telegraph codes had two ancestors, codes for semaphore networks and naval signaling [9]. -

Letter Circular 45: Construction and Operation of a Simple
' «i -•aif -ISe • 1-b Publication of the Letter DEPARTMENT OF COM'lERCE Circular BUREAU OF STANDARDS LC 45 WASHINGTON, D. 0. CONSTRUCTION AND OPERATION OF A SIMPLE RAD IOTELEGP.APHI C CODE PRACTICE SET.* (Prepared at request of the States Relations Service, United States Department of Agriculture for use by Boys 1 and Girls 1 Radio Clubs.) Introduction This pamphlet describes apparatus which may be used for the pur- pose of learning the radio telegraph code. The apparatus is very easy to set up and operate. It is intended to be used at radio club meet- ing places or in places where a number of radio students are accustomed to assemble. Those who construct the simple radio receiving sets des- cribed in the first two pamphlets of this series will probably hear many signals which are in code. The Code Practice Set is therefore made a part of this series so shat the international Morse Code may be learned. The cost of the complete outfit will be about $5*70 or, if one constructs the telegraph key, she. cost will be reduced to about $3«b0 It is assumed that those who use this outfit have radio receiving sets and can bring their telephone receivers (“phones") to connect to the other apparatus. It is also assumed that it will not be necessary to purchase the table upon which the parts are mounted. It is desirable *This is the third of a series of pamphlets describing the construction of radio equipment. The two publications which nave been issued are Letter Receiving Circular 43 , "Construction and Opera-cion of a Very Simple Radio Equipment," and Letter Circular 44, "Construction and Operation of a Two- Circuit Radio Receiving Equipment with Crystal Detector." These describe the construction and operation of simple receiving sets. -

Documents of the CCIR (Los Angeles, 1959)
This electronic version (PDF) was scanned by the International Telecommunication Union (ITU) Library & Archives Service from an original paper document in the ITU Library & Archives collections. La présente version électronique (PDF) a été numérisée par le Service de la bibliothèque et des archives de l'Union internationale des télécommunications (UIT) à partir d'un document papier original des collections de ce service. Esta versión electrónica (PDF) ha sido escaneada por el Servicio de Biblioteca y Archivos de la Unión Internacional de Telecomunicaciones (UIT) a partir de un documento impreso original de las colecciones del Servicio de Biblioteca y Archivos de la UIT. (ITU) ﻟﻼﺗﺼﺎﻻﺕ ﺍﻟﺪﻭﻟﻲ ﺍﻻﺗﺤﺎﺩ ﻓﻲ ﻭﺍﻟﻤﺤﻔﻮﻇﺎﺕ ﺍﻟﻤﻜﺘﺒﺔ ﻗﺴﻢ ﺃﺟﺮﺍﻩ ﺍﻟﻀﻮﺋﻲ ﺑﺎﻟﻤﺴﺢ ﺗﺼﻮﻳﺮ ﻧﺘﺎﺝ (PDF) ﺍﻹﻟﻜﺘﺮﻭﻧﻴﺔ ﺍﻟﻨﺴﺨﺔ ﻫﺬﻩ .ﻭﺍﻟﻤﺤﻔﻮﻇﺎﺕ ﺍﻟﻤﻜﺘﺒﺔ ﻗﺴﻢ ﻓﻲ ﺍﻟﻤﺘﻮﻓﺮﺓ ﺍﻟﻮﺛﺎﺋﻖ ﺿﻤﻦ ﺃﺻﻠﻴﺔ ﻭﺭﻗﻴﺔ ﻭﺛﻴﻘﺔ ﻣﻦ ﻧﻘﻼ ً◌ 此电子版(PDF版本)由国际电信联盟(ITU)图书馆和档案室利用存于该处的纸质文件扫描提供。 Настоящий электронный вариант (PDF) был подготовлен в библиотечно-архивной службе Международного союза электросвязи путем сканирования исходного документа в бумажной форме из библиотечно-архивной службы МСЭ. © International Telecommunication Union INTERNATIONAL RADIO CONSULTATIVE COMMITTEE C.C.I.R. DOCUMENTS OF THE IXth PLENARY ASSEMBLY LOS ANGELES, 1959 VOLUME III REPORTS Published by the INTERNATIONAL TELECOMMUNICATION UNION GENEVA, 1959 INTERNATIONAL RADIO CONSULTATIVE COMMITTEE C.C.I.R. DOCUMENTS OF THE IXth PLENARY ASSEMBLY LOS ANGELES, 1959 VOLUME III REPORTS Published by the INTERNATIONAL TELECOMMUNICATION UNION GENEVA, 1959 PAGE -

W3PGA Pearl Harbor Special Event
Fall is here! The Aero Aerial The Newsletter of the Aero Amateur Radio Club Middle River, MD Volume 14, Issue 10 October 2018 Editor Georgeann Vleck KB3PGN Officers Committees President Joe Miko WB3FMT Repeater Phil Hock W3VRD Jerry Cimildora N3VBJ Vice-President Jerry Cimildora N3VBJ VE Testing Pat Stone AC3F Recording Lou Kordek AB3QK Public Bob Landis WA3SWA Secretary Service Corresponding Pat Stone AC3F Webmaster, Jerry Cimildora N3VBJ Secretary Facebook Treasurer Warren Hartman W3JDF Trustee Dave Fredrick KB3KRV Resource Ron Distler W3JEH Club Nets Joe Miko WB3FMT Coordinator Contests Bob Venanzi ND3D Charles Whittaker KB3EK Website: http://w3pga.org Facebook: https://www.facebook.com/pages/Aero-Amateur-Radio-Club/719248141439348 About the Aero Amateur Radio Club Meetings The Aero Amateur Radio Club meets at 7:30 pm on the first and third Wednesdays of the month at Essex SkyPark, 1401 Diffendall Road, Essex. Meetings begin at 7:30 p.m. local time. Meetings are canceled if Baltimore County Public Schools are closed or dismiss early. Repeaters W3PGA 2 M : INPUT : 147.84 MHz, OUTPUT : 147.24 MHz, PL 123.0 W3PGA 70 Cm: INPUT : 444.575 MHz, OUTPUT : 449.575 MHz, PL123.0 W3JEH 1.25 M: INPUT : 222.24 MHz, OUTPUT : 223.84 MHz Club Nets Second Wednesday Net – 10 Meters (28.445 MHz) @ 8 p.m. Local Time Fourth Wednesday Net – 2 Meters (147.24 MHz Repeater) @ 8 p.m. Local Time Fifth Wednesday Net – 70 Centimeters (449.575 MHz Repeater) @ 8 p.m. Local Time Radio License Exams The Aero Amateur Radio Club sponsors Amateur Radio License Exams with the ARRL VEC. -

The Unicode Standard, Version 4.0--Online Edition
This PDF file is an excerpt from The Unicode Standard, Version 4.0, issued by the Unicode Consor- tium and published by Addison-Wesley. The material has been modified slightly for this online edi- tion, however the PDF files have not been modified to reflect the corrections found on the Updates and Errata page (http://www.unicode.org/errata/). For information on more recent versions of the standard, see http://www.unicode.org/standard/versions/enumeratedversions.html. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and Addison-Wesley was aware of a trademark claim, the designations have been printed in initial capital letters. However, not all words in initial capital letters are trademark designations. The Unicode® Consortium is a registered trademark, and Unicode™ is a trademark of Unicode, Inc. The Unicode logo is a trademark of Unicode, Inc., and may be registered in some jurisdictions. The authors and publisher have taken care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. The Unicode Character Database and other files are provided as-is by Unicode®, Inc. No claims are made as to fitness for any particular purpose. No warranties of any kind are expressed or implied. The recipient agrees to determine applicability of information provided. Dai Kan-Wa Jiten used as the source of reference Kanji codes was written by Tetsuji Morohashi and published by Taishukan Shoten. -

The Unicode Standard, Version 3.0, Issued by the Unicode Consor- Tium and Published by Addison-Wesley
The Unicode Standard Version 3.0 The Unicode Consortium ADDISON–WESLEY An Imprint of Addison Wesley Longman, Inc. Reading, Massachusetts · Harlow, England · Menlo Park, California Berkeley, California · Don Mills, Ontario · Sydney Bonn · Amsterdam · Tokyo · Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and Addison-Wesley was aware of a trademark claim, the designations have been printed in initial capital letters. However, not all words in initial capital letters are trademark designations. The authors and publisher have taken care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. The Unicode Character Database and other files are provided as-is by Unicode®, Inc. No claims are made as to fitness for any particular purpose. No warranties of any kind are expressed or implied. The recipient agrees to determine applicability of information provided. If these files have been purchased on computer-readable media, the sole remedy for any claim will be exchange of defective media within ninety days of receipt. Dai Kan-Wa Jiten used as the source of reference Kanji codes was written by Tetsuji Morohashi and published by Taishukan Shoten. ISBN 0-201-61633-5 Copyright © 1991-2000 by Unicode, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or other- wise, without the prior written permission of the publisher or Unicode, Inc. -

Operating Signals
UNCLASSIFIED ACP 131(F) COMMUNICATIONS INSTRUCTIONS - OPERATING SIGNALS ACP 131(F) APRIL 2009 Original UNCLASSIFIED UNCLASSIFIED ACP 131(F) FOREWORD 1. The Combined Communications-Electronics Board (CCEB) is comprised of the five member nations, Australia, Canada, New Zealand, United Kingdom and United States and is the Sponsoring Authority for all Allied Communications Publications (ACPs). ACPs are raised and issued under common agreement between the member nations. 2. ACP 131(F), COMMUNICATIONS INSTRUCTIONS - OPERATING SIGNALS is an UNCLASSIFIED CCEB publication. 3. This publication contains Allied military information for official purposes only. 4. It is permitted to copy or make extracts from this publication. 5. This ACP is to be maintained and amended in accordance with the provisions of the current version of ACP 198. i Original UNCLASSIFIED UNCLASSIFIED ACP 131(F) THE CCEB LETTER OF PROMULGATION FOR ACP 131(F) 1. The purpose of this Combined Communication Electronics Board (CCEB) Letter of Promulgation is to implement ACP 131(F) within the Armed Forces of the CCEB Nations. ACP 131(F) COMMUNICATIONS INSTRUCTIONS OPERATING SIGNALS, is an UNCLASSIFIED publication developed for Allied use and, under the direction of the CCEB Principals. It is promulgated for guidance, information, and use by the Armed Forces and other users of military communications facilities. 2. ACP 131(F) is effective on receipt for CCEB Nations. NATO Military Committee (NAMILCOM) will promulgate the effective status separately for NATO nations and Strategic Commands. EFFECTIVE STATUS Publication Effective for Date Authority ACP 131(F) CCEB On Receipt LOP 3. This ACP will be reviewed periodically as directed by the CCEB Permanent Secretary. -

The Webinar Will Begin Shortly
The webinar will begin shortly [email protected] | (800) 443-6183 | www.sdsusa.com Webinar Exploring the Technology and Details of Securing FTP on z/OS and Beyond MAINFRAME SECURITY SECURE FTP for z/OS About Us sdsusa.com Quality Mainframe Software since 1982 ►Expert development & technical support teams based in Minneapolis, MN. ►25+ products for z/OS, z/VM, z/VSE, and distributed platforms. ►Hundreds of organizations worldwide rely on SDS solutions. ►Focus on mainframe security and compliance. ►Cost savings and legacy tool replacements: DO MORE WITH LESS! ►Long-standing global partnerships complement SDS software. ►Recognized as cybersecurity trend-setter. MAINFRAME SECURITY SECURE FTP for z/OS About SSH.com Brief Company Introduction Presenters Jan Hlinovsky Colin van der Ross Product Manager, Tectia SSH Server for z/OS Sr. Systems Engineer A Data Set’s Journey Demonstration of from z/OS to Unix the z/OS SFTP topics and Back Again covered by Jan MAINFRAME SECURITY SECURE FTP for z/OS Tectia SSH Server for IBM z/OS A Data Set’s Journey from z/OS to Unix and Back Again Jan Hlinovsky, Product Manager for Tectia on z [email protected] Storing text format data on a computer • Computers operate with bits that are commonly collected into bytes. One byte, 8 bits, sometimes expressed as two hexadecimal values, can express 2^8=256 different values. • In the 60s the ASCII code standardization and mainframe development were happening in parallel. ASCII code was 7 bit and its development stems from telegraph code. EBCDIC was 8 bit and is related to coding used with punch cards, and it was used in IBM system/360.