Signal Handlers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Distributed Programming I (Socket - Nov'09)
Distributed programming I (socket - nov'09) Warning for programmers network programming is dangerously close to O.S. Network programming: sockets kernel, and therefore: It can easily hang the O.S. verify the results of every operation, without assuming anything as granted Antonio Lioy < [email protected] > APIs can vary in details that are minimal but important consider every possible situation to create english version created and modified by “portable” programs Marco D. Aime < [email protected] > we will try to use Posix 1.g Politecnico di Torino Dip. Automatica e Informatica ISO/OSI, TCP/IP, network programming Exercise – copying data copy the content of file F1 (first parameter on the application command line) into file F2 (second parameter on the 7. application details application command line) user 6. presentation (l6: XDR/XML/... process l5: RPC/SOAP/...) 5. session network programming 4. transport TCP UDP SCTP interface 3. network IPv4, IPv6 kernel communication 2. data link device driver details 1. physical and hardware OSI model IP suite ref. UNP Intro copyfile.c Error messages Error functions must contain at least: best to define standard error reporting functions [ PROG ] program name which accept: [ LEVEL ] error level (info, warning, error, bug) a format string for the error [ TEXT ] error signalling, the most specific as possible a list of parameters to be printed (e.g. input file name and line where the problem has UNP, appendix D.4 (D.3 in 3rd edition) occurred) errno? termination? log level [ ERRNO ] system error number and/or name (if applicable) err_msg no no LOG_INFO err_quit no exit(1) LOG_ERR suggested format: err_ret yes no LOG_INFO err_sys yes exit(1) LOG_ERR ( PROG ) LEVEL - TEXT : ERRNO err_dump yes abort( ) LOG_ERR errlib.h errlib.c © A.Lioy - Politecnico di Torino (2009) B-1 Distributed programming I (socket - nov'09) stdarg.h stdarg.h usage example variable list of arguments (ANSI C) create a function named my_printf declared with an ellipsis (. -

Pdp11-40.Pdf
processor handbook digital equipment corporation Copyright© 1972, by Digital Equipment Corporation DEC, PDP, UNIBUS are registered trademarks of Digital Equipment Corporation. ii TABLE OF CONTENTS CHAPTER 1 INTRODUCTION 1·1 1.1 GENERAL ............................................. 1·1 1.2 GENERAL CHARACTERISTICS . 1·2 1.2.1 The UNIBUS ..... 1·2 1.2.2 Central Processor 1·3 1.2.3 Memories ........... 1·5 1.2.4 Floating Point ... 1·5 1.2.5 Memory Management .............................. .. 1·5 1.3 PERIPHERALS/OPTIONS ......................................... 1·5 1.3.1 1/0 Devices .......... .................................. 1·6 1.3.2 Storage Devices ...................................... .. 1·6 1.3.3 Bus Options .............................................. 1·6 1.4 SOFTWARE ..... .... ........................................... ............. 1·6 1.4.1 Paper Tape Software .......................................... 1·7 1.4.2 Disk Operating System Software ........................ 1·7 1.4.3 Higher Level Languages ................................... .. 1·7 1.5 NUMBER SYSTEMS ..................................... 1-7 CHAPTER 2 SYSTEM ARCHITECTURE. 2-1 2.1 SYSTEM DEFINITION .............. 2·1 2.2 UNIBUS ......................................... 2-1 2.2.1 Bidirectional Lines ...... 2-1 2.2.2 Master-Slave Relation .. 2-2 2.2.3 Interlocked Communication 2-2 2.3 CENTRAL PROCESSOR .......... 2-2 2.3.1 General Registers ... 2-3 2.3.2 Processor Status Word ....... 2-4 2.3.3 Stack Limit Register 2-5 2.4 EXTENDED INSTRUCTION SET & FLOATING POINT .. 2-5 2.5 CORE MEMORY . .... 2-6 2.6 AUTOMATIC PRIORITY INTERRUPTS .... 2-7 2.6.1 Using the Interrupts . 2-9 2.6.2 Interrupt Procedure 2-9 2.6.3 Interrupt Servicing ............ .. 2-10 2.7 PROCESSOR TRAPS ............ 2-10 2.7.1 Power Failure .............. -

Beej's Guide to Unix IPC
Beej's Guide to Unix IPC Brian “Beej Jorgensen” Hall [email protected] Version 1.1.3 December 1, 2015 Copyright © 2015 Brian “Beej Jorgensen” Hall This guide is written in XML using the vim editor on a Slackware Linux box loaded with GNU tools. The cover “art” and diagrams are produced with Inkscape. The XML is converted into HTML and XSL-FO by custom Python scripts. The XSL-FO output is then munged by Apache FOP to produce PDF documents, using Liberation fonts. The toolchain is composed of 100% Free and Open Source Software. Unless otherwise mutually agreed by the parties in writing, the author offers the work as-is and makes no representations or warranties of any kind concerning the work, express, implied, statutory or otherwise, including, without limitation, warranties of title, merchantibility, fitness for a particular purpose, noninfringement, or the absence of latent or other defects, accuracy, or the presence of absence of errors, whether or not discoverable. Except to the extent required by applicable law, in no event will the author be liable to you on any legal theory for any special, incidental, consequential, punitive or exemplary damages arising out of the use of the work, even if the author has been advised of the possibility of such damages. This document is freely distributable under the terms of the Creative Commons Attribution-Noncommercial-No Derivative Works 3.0 License. See the Copyright and Distribution section for details. Copyright © 2015 Brian “Beej Jorgensen” Hall Contents 1. Intro................................................................................................................................................................1 1.1. Audience 1 1.2. Platform and Compiler 1 1.3. -

Embedded C Programming I (Ecprogrami)
To our customers, Old Company Name in Catalogs and Other Documents On April 1st, 2010, NEC Electronics Corporation merged with Renesas Technology Corporation, and Renesas Electronics Corporation took over all the business of both companies. Therefore, although the old company name remains in this document, it is a valid Renesas Electronics document. We appreciate your understanding. Renesas Electronics website: http://www.renesas.com April 1st, 2010 Renesas Electronics Corporation Issued by: Renesas Electronics Corporation (http://www.renesas.com) Send any inquiries to http://www.renesas.com/inquiry. Notice 1. All information included in this document is current as of the date this document is issued. Such information, however, is subject to change without any prior notice. Before purchasing or using any Renesas Electronics products listed herein, please confirm the latest product information with a Renesas Electronics sales office. Also, please pay regular and careful attention to additional and different information to be disclosed by Renesas Electronics such as that disclosed through our website. 2. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 3. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. 4. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. -

POSIX Signals
CSE 410: Systems Programming POSIX Signals Ethan Blanton Department of Computer Science and Engineering University at Buffalo Introduction Signals Blocking Concurrency Sending Signals Summary References POSIX Signals POSIX signals are another form of interprocess communication. They are also a way to create concurrency in programs. For these two reasons, they are rather complicated and subtle! Signals provide a simple message passing mechanism. © 2018 Ethan Blanton / CSE 410: Systems Programming Introduction Signals Blocking Concurrency Sending Signals Summary References Signals as Messages POSIX signals are asynchronous messages. Asynchronous means that their reception can occur at any time.1 The message is the reception of the signal itself. Each signal has a number, which is a small integer. POSIX signals carry no other data. 1Almost. We’ll see how to control it later. © 2018 Ethan Blanton / CSE 410: Systems Programming Introduction Signals Blocking Concurrency Sending Signals Summary References Signal Types There are two basic types of POSIX signals: Reliable signals Real-time signals Real-time signals are much more complicated. In particular, they can carry data. We will discuss only reliable signals in this lecture. © 2018 Ethan Blanton / CSE 410: Systems Programming Introduction Signals Blocking Concurrency Sending Signals Summary References Asynchronous Reception From the point of view of the application: Signals can be blocked or ignored Enabled signals may be received between any two processor instructions A received signal can run a user-defined function called a signal handler This means that enabled signals and program code must very carefully manipulate shared or global data! © 2018 Ethan Blanton / CSE 410: Systems Programming Introduction Signals Blocking Concurrency Sending Signals Summary References Signals POSIX defines a number of signals by name and number. -

Operating Systems What Is an Operating System Real-Time
Operating Systems Babak Kia Adjunct Professor Boston University College of Engineering Email: bkia -at- bu.edu ENG SC757 - Advanced Microprocessor Design What is an Operating System z Operating System handles • Memory Addressing & Management • Interrupt & Exception Handling • Process & Task Management • File System • Timing • Process Scheduling & Synchronization z Examples of Operating Systems • RTOS – Real-Time Operating System • Single-user, Single-task: example PalmOS • Single-user, Multi-task: MS Windows and MacOS • Multi-user, Multi-task: UNIX 2 Real-Time Operating Systems z Operating systems come in two flavors, real-time versus non real-time z The difference between the two is characterized by the consequences which result if functional correctness and timing parameters are not met in the case of real-time operating systems z Real-time operating systems themselves have two varieties, soft real-time systems and hard real- time systems z Examples of real-time systems: • Food processing • Engine Controls • Anti-lock breaking systems 3 1 Soft versus Hard Real-Time z In a soft real-time system, tasks are completed as fast as possible without having to be completed within a specified timeframe z In a hard real-time operating system however, not only must tasks be completed within the specified timeframe, but they must also be completed correctly 4 Foreground/Background Systems z The simplest forms of a non real-time operating systems are comprised of super-loops and are called foreground/background systems z Essentially this is an application -
Reentrant Code
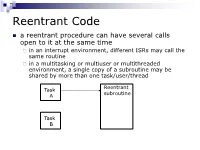
Reentrant Code a reentrant procedure can have several calls open to it at the same time in an interrupt environment, different ISRs may call the same routine in a multitasking or multiuser or multithreaded environment, a single copy of a subroutine may be shared by more than one task/user/thread Reentrant Task subroutine A Task B Reentrant Code Characteristics requirements: 1. any parameters or local variables must be on the stack frame 2. registers may be used for parameters and local variables but must be saved on or restored from the stack at beginning/end of the subroutine 3. guarantee that each call of the subroutine will create a separate stack frame to maintain data integrity 4. no self-modifying code Recursion recursive code must be reentrant recursive reentrant but reentrant recursive e.g. calculating 3! using recursion main move.w number,D0 pass the number jsr fact start recursive rtn move.w D0,result store the factorial stop #$2700 number dc.w 3 result ds.w 1 fact link A6,#-2 Stack structure move.w D0,-2(A6) subq.w #1,D0 bne push move.w -2(A6),D0 bra return push jsr fact mulu -2(A6),D0 return unlk A6 rts end main SP ->/////// A much more complex example: X: array [0..30] of words Y: longword Z, ALPHA, N: byte call order is S/R demo(X, Y, Z, ALPHA, N ) N is passed/returned by value, all others are passed by reference demo(X[w:31], Y[l], Z[b], ALPHA[b], N[b]) main CLR.W D2 zero entire word MOVE.B N,D2 N to low byte MOVE.W D2,-(SP) N on stack PEA ALPHA push arguments PEA Z in reverse order PEA Y PEA X JSR demo call -

Programming with POSIX Threads II
Programming with POSIX Threads II CS 167 IV–1 Copyright © 2008 Thomas W. Doeppner. All rights reserved. Global Variables int IOfunc( ) { extern int errno; ... if (write(fd, buffer, size) == –1) { if (errno == EIO) fprintf(stderr, "IO problems ...\n"); ... return(0); } ... } CS 167 IV–2 Copyright © 2008 Thomas W. Doeppner. All rights reserved. Unix was not designed with multithreaded programming in mind. A good example of the implications of this is the manner in which error codes for failed system calls are made available to a program: if a system call fails, it returns –1 and the error code is stored in the global variable errno. Though this is not all that bad for single-threaded programs, it is plain wrong for multithreaded programs. Coping • Fix Unix’s C/system-call interface • Make errno refer to a different location in each thread – e.g. #define errno __errno(thread_ID) CS 167 IV–3 Copyright © 2008 Thomas W. Doeppner. All rights reserved. The ideal way to solve the “errno problem” would be to redesign the C/system-call interface: system calls should return only an error code. Anything else to be returned should be returned via result parameters. (This is how things are done in Windows NT.) Unfortunately, this is not possible (it would break pretty much every Unix program in existence). So we are stuck with errno. What can we do to make errno coexist with multithreaded programming? What would help would be to arrange, somehow, that each thread has its own private copy of errno. I.e., whenever a thread refers to errno, it refers to a different location from any other thread when it refers to errno. -

UNIT: 4 DISTRIBUTED COMPUTING Introduction to Distributed Programming
UNIT: 4 DISTRIBUTED COMPUTING Introduction To Distributed Programming: • Distributed computing is a model in which components of a software system are shared among multiple computers. Even though the components are spread out across multiple computers, they are run as one system. This is done in order to improve efficiency and performance. • Distributed computing allows different users or computers to share information. Distributed computing can allow an application on one machine to leverage processing power, memory, or storage on another machine. Some applications, such as word processing, might not benefit from distribution at all. • In parallel computing, all processors may have access to a shared memory to exchange information between processors. In distributed computing, each processor has its own private memory (distributed memory). Information is exchanged by passing messages between the processors. • Distributed computing systems are omnipresent in today’s world. The rapid progress in the semiconductor and networking infrastructures have blurred the differentiation between parallel and distributed computing systems and made distributed computing a workable alternative to high- performance parallel architectures. • However attractive distributed computing may be, developing software for such systems is hardly a trivial task. Many different models and technologies have been proposed by academia and industry for developing robust distributed software systems. • Despite a large number of such systems, one fact is clear that the software -

Introduction to POSIX Signals
Introduction to POSIX Signals Michael Jantz Prasad Kulkarni Douglas Niehaus Introduction ● This lab is an introduction to signals in Unix systems. – In it, you will learn about some common uses for signals. – You will also construct a small program that uses signals. ● Unpack the starter code, then make and tag it: – bash> tar zxvf eecs678-signals-lab.tar.gz – cd signals/; make; ctags -R EECS 678 Signals Lab 2 Signals ● A signal is a short message that may be sent to a process or a group of processes. ● The only information given to a process is usually the number identifying the signal; there is no room in standard signals for arguments, a message or other accompanying information. ● Signals serve two main purposes: – To make a process aware that a specific event has occurred. – To cause a process to execute a signal handler function included in its code. EECS 678 Signals Lab 3 Interrupts vs. Signals ● Signals and interrupts are very similar in their behavior ● Important difference: interrupts are sent to the operating system by the hardware, signals are sent to the process by the operating system, or other processes through the OS ● Important similarity: both signals and interrupts associate handlers with asynchronous events which interrupt current processing, thus inserting the handler into current code path ● Signals can thus be thought of as an interrupt in software: – However, note that signals have nothing to do with Soft-IRQs. The name seems related, but these are a method for deferring much of the processing associated with a hardware-interrupt into a less restrictive execution context inside the OS. -

POSIX Signal Handling in Java
Technical Document Series POSIX Signal Handling in Java POSIX Signal Handling In Java Introduction POSIX signals inform a running process of external events, such as the user wishing to kill the process, or the operating system signaling an impending shutdown, or the process being suspended or reinstated; or the process may have violated a resource constraint, such as excessive CPU usage or attempts to access areas outside its permitted memory space, and is asked to shutdown. In short, POSIX signals serve many different purposes. Some are even up to interpretation, such as the HUP (HangUP) signal, which is commonly used to inform a process that something about its environment has changed and the process should adjust accordingly. Some programs may interpret this to mean that the configuration has changed and needs to be reloaded; or the log file has been moved for archiving purposes and a new one should be started. The use of signals is widespread, especially on Unix-based operating systems, but Java provides no standard interface for a Java application to hear and react to them. This document shows you how to get around this limitation. The Good, the Bad, and the Ugly The good news is that there is a way to intercept POSIX signals and react to them in Java. This would allow your Java program to avoid being killable with ^C (SIGINT), for example, even ignore termination requests from the operating system (SIGTERM). Neither of these is necessarily a good idea, of course, unless you know exactly why you would want to catch these signals and either handle them yourself or ignore them altogether. -

Lecture 14: Paging
Lecture 14: Paging Fall 2018 Jason Tang Slides based upon Operating System Concept slides, http://codex.cs.yale.edu/avi/os-book/OS9/slide-dir/index.html Copyright Silberschatz, Galvin, and Gagne, 2013 "1 Topics • Memory Mappings! • Page Table! • Translation Lookaside Bu$ers! • Page Protection "2 Memory Mapped • Logical address translated not to memory but some other location! • Memory-mapped I/O (MMIO): hardware redirects read/write of certain addresses to physical device! • For example, on x86, address 0x3F8 usually mapped to first serial port! • Memory-mapped file (mmap): OS redirects read/write of mapped memory region to file on disk! • Every call to read() / write() involves a system call! • Writing to a pointer faster, and OS can translate in the background (also see upcoming lecture) "3 Memory-Mapped File • In Linux, typical pattern is to:! • Open file, using open() function! • Optional: preallocate file size, using ftruncate()! • Create memory mapping, using mmap() function! • Do work, and then release mapping using munmap() function! • Kernel might not write data to disk until munmap() "4 mmap() function void *mmap(void *addr, size_t length, int prot, int flags, int fd, off_t offset) • addr is target address of mapping, or NULL to let kernel decide! • length is number of bytes to map! • prot defines what mapping protection (read-only or read/write)! • flags sets other options! • fd is file descriptor that was returned by open()! • offset is o$set into file specified by fd "5 mmap() example part 1 • See man page for each of these functions