Scripting Languages Tend to Stress flexibility, Rapid Development, Local Customization, And
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
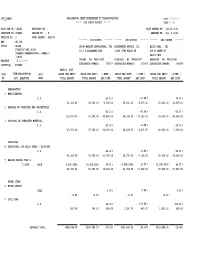
Bid Check Report * * * Time: 14:04
DOT_RGGB01 WASHINGTON STATE DEPARTMENT OF TRANSPORTATION DATE: 05/28/2013 * * * BID CHECK REPORT * * * TIME: 14:04 PS &E JOB NO : 11W101 REVISION NO : BIDS OPENED ON : Jun 26 2013 CONTRACT NO : 008498 REGION NO : 9 AWARDED ON : Jul 1 2013 VERSION NO : 2 WORK ORDER# : XL4078 ------- LOW BIDDER ------- ------- 2ND BIDDER ------- ------- 3RD BIDDER ------- HWY : SR 104 TITLE : SR104 ORION MARINE CONTRACTORS, INC. BLACKWATER MARINE, LLC QUIGG BROS., INC. KINGSTON TML SLIPS 1112 E ALEXANDER AVE 12019 76TH PLACE NE 819 W STATE ST DOLPHIN PRESERVATION - PHASE 4 98520-5934 11W101 PROJECT : NH-2013(079) TACOMA WA 984214102 KIRKLAND WA 980342437 ABERDEEN WA 985200281 COUNTY(S) : KITSAP CONTRACTOR NUMBER : 100767 CONTRACTOR NUMBER : 100874 CONTRACTOR NUMBER : 680000 ENGR'S. EST. ITEM ITEM DESCRIPTION UNIT PRICE PER UNIT/ PRICE PER UNIT/ % DIFF./ PRICE PER UNIT/ % DIFF./ PRICE PER UNIT/ % DIFF./ NO. EST. QUANTITY MEAS TOTAL AMOUNT TOTAL AMOUNT AMT.DIFF. TOTAL AMOUNT AMT.DIFF. TOTAL AMOUNT AMT.DIFF. PREPARATION 1 MOBILIZATION L.S. -25.20 % -25.48 % 40.00 % 25,000.00 18,700.00 -6,300.00 18,630.00 -6,370.00 35,000.00 10,000.00 2 REMOVAL OF STRUCTURE AND OBSTRUCTION L.S. -56.10 % -65.08 % -56.71 % 115,500.00 50,700.00 -64,800.00 40,338.00 -75,162.00 50,000.00 -65,500.00 3 DISPOSAL OF CREOSOTED MATERIAL L.S. -21.05 % -8.99 % -15.79 % 47,500.00 37,500.00 -10,000.00 43,228.35 -4,271.65 40,000.00 -7,500.00 STRUCTURE 4 STRUCTURAL LOW ALLOY STEEL - DOLPHINS L.S. -

Chapter 12 Calc Macros Automating Repetitive Tasks Copyright
Calc Guide Chapter 12 Calc Macros Automating repetitive tasks Copyright This document is Copyright © 2019 by the LibreOffice Documentation Team. Contributors are listed below. You may distribute it and/or modify it under the terms of either the GNU General Public License (http://www.gnu.org/licenses/gpl.html), version 3 or later, or the Creative Commons Attribution License (http://creativecommons.org/licenses/by/4.0/), version 4.0 or later. All trademarks within this guide belong to their legitimate owners. Contributors This book is adapted and updated from the LibreOffice 4.1 Calc Guide. To this edition Steve Fanning Jean Hollis Weber To previous editions Andrew Pitonyak Barbara Duprey Jean Hollis Weber Simon Brydon Feedback Please direct any comments or suggestions about this document to the Documentation Team’s mailing list: [email protected]. Note Everything you send to a mailing list, including your email address and any other personal information that is written in the message, is publicly archived and cannot be deleted. Publication date and software version Published December 2019. Based on LibreOffice 6.2. Using LibreOffice on macOS Some keystrokes and menu items are different on macOS from those used in Windows and Linux. The table below gives some common substitutions for the instructions in this chapter. For a more detailed list, see the application Help. Windows or Linux macOS equivalent Effect Tools > Options menu LibreOffice > Preferences Access setup options Right-click Control + click or right-click -

Marcelo Camargo (Haskell Camargo) – Résumé Projects
Marcelo Camargo (Haskell Camargo) – Résumé https://github.com/haskellcamargo [email protected] http://coderbits.com/haskellcamargo Based in Joinville / SC – Brazil Knowledge • Programming languages domain: ◦ Ada, AdvPL, BASIC, C, C++, C#, Clipper, Clojure, CoffeeScript, Common LISP, Elixir, Erlang, F#, FORTRAN, Go, Harbour, Haskell, Haxe, Hy, Java, JavaScript, Ink, LiveScript, Lua, MATLAB, Nimrod, OCaml, Pascal, PHP, PogoScript, Processing, PureScript, Python, Ruby, Rust, Self, Shell, Swift, TypeScript, VisualBasic [.NET], Whip, ZPL. • Markup, style and serialization languages: ◦ Markdown, reStructuredText, [X] HTML, XML, CSS, LESS, SASS, Stylus, Yaml, JSON, DSON. • Database management systems: ◦ Oracle, MySQL, SQL Server, IBM DB2, PostgreSQL. • Development for operating systems: ◦ Unix based, Windows (CE mobile included), Android, Firefox OS. • Parsers and compilers: ◦ Macros: ▪ Sweet.js, preprocessor directives. ◦ Parser and scanner generators: ▪ ANTLR, PEG.js, Jison, Flex, re2c, Lime. • Languages: ◦ Portuguese (native) ◦ English (native) ◦ Spanish (fluent) ◦ French (fluent) ◦ Turkish (intermediate) ◦ Chinese (mandarin) (intermediate) ◦ Esperanto (intermediate) Projects • Prelude AdvPL – a library that implements functional programming in AdvPL and extends its syntax to a more expressive one; it's a port of Haskell's Prelude; • Frida – a LISP dialect that runs on top of Node.js; • PHPP – A complete PHP preprocessor with a grammar able to identify and replace tokens and extend/modify the language syntax, meant to be implemented -

Rexx Programmer's Reference
01_579967 ffirs.qxd 2/3/05 9:00 PM Page i Rexx Programmer’s Reference Howard Fosdick 01_579967 ffirs.qxd 2/3/05 9:00 PM Page iv 01_579967 ffirs.qxd 2/3/05 9:00 PM Page i Rexx Programmer’s Reference Howard Fosdick 01_579967 ffirs.qxd 2/3/05 9:00 PM Page ii Rexx Programmer’s Reference Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2005 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 0-7645-7996-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1MA/ST/QS/QV/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, e-mail: [email protected]. LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COM- PLETENESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WAR- RANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. -

Humidity Definitions
ROTRONIC TECHNICAL NOTE Humidity Definitions 1 Relative humidity Table of Contents Relative humidity is the ratio of two pressures: %RH = 100 x p/ps where p is 1 Relative humidity the actual partial pressure of the water vapor present in the ambient and ps 2 Dew point / Frost the saturation pressure of water at the temperature of the ambient. point temperature Relative humidity sensors are usually calibrated at normal room temper - 3 Wet bulb ature (above freezing). Consequently, it generally accepted that this type of sensor indicates relative humidity with respect to water at all temperatures temperature (including below freezing). 4 Vapor concentration Ice produces a lower vapor pressure than liquid water. Therefore, when 5 Specific humidity ice is present, saturation occurs at a relative humidity of less than 100 %. 6 Enthalpy For instance, a humidity reading of 75 %RH at a temperature of -30°C corre - 7 Mixing ratio sponds to saturation above ice. by weight 2 Dew point / Frost point temperature The dew point temperature of moist air at the temperature T, pressure P b and mixing ratio r is the temperature to which air must be cooled in order to be saturated with respect to water (liquid). The frost point temperature of moist air at temperature T, pressure P b and mixing ratio r is the temperature to which air must be cooled in order to be saturated with respect to ice. Magnus Formula for dew point (over water): Td = (243.12 x ln (pw/611.2)) / (17.62 - ln (pw/611.2)) Frost point (over ice): Tf = (272.62 x ln (pi/611.2)) / (22.46 - -

Beginning Portable Shell Scripting from Novice to Professional
Beginning Portable Shell Scripting From Novice to Professional Peter Seebach 10436fmfinal 1 10/23/08 10:40:24 PM Beginning Portable Shell Scripting: From Novice to Professional Copyright © 2008 by Peter Seebach All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN-13 (pbk): 978-1-4302-1043-6 ISBN-10 (pbk): 1-4302-1043-5 ISBN-13 (electronic): 978-1-4302-1044-3 ISBN-10 (electronic): 1-4302-1044-3 Printed and bound in the United States of America 9 8 7 6 5 4 3 2 1 Trademarked names may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Lead Editor: Frank Pohlmann Technical Reviewer: Gary V. Vaughan Editorial Board: Clay Andres, Steve Anglin, Ewan Buckingham, Tony Campbell, Gary Cornell, Jonathan Gennick, Michelle Lowman, Matthew Moodie, Jeffrey Pepper, Frank Pohlmann, Ben Renow-Clarke, Dominic Shakeshaft, Matt Wade, Tom Welsh Project Manager: Richard Dal Porto Copy Editor: Kim Benbow Associate Production Director: Kari Brooks-Copony Production Editor: Katie Stence Compositor: Linda Weidemann, Wolf Creek Press Proofreader: Dan Shaw Indexer: Broccoli Information Management Cover Designer: Kurt Krames Manufacturing Director: Tom Debolski Distributed to the book trade worldwide by Springer-Verlag New York, Inc., 233 Spring Street, 6th Floor, New York, NY 10013. -

Bringing GNU Emacs to Native Code
Bringing GNU Emacs to Native Code Andrea Corallo Luca Nassi Nicola Manca [email protected] [email protected] [email protected] CNR-SPIN Genoa, Italy ABSTRACT such a long-standing project. Although this makes it didactic, some Emacs Lisp (Elisp) is the Lisp dialect used by the Emacs text editor limitations prevent the current implementation of Emacs Lisp to family. GNU Emacs can currently execute Elisp code either inter- be appealing for broader use. In this context, performance issues preted or byte-interpreted after it has been compiled to byte-code. represent the main bottleneck, which can be broken down in three In this work we discuss the implementation of an optimizing com- main sub-problems: piler approach for Elisp targeting native code. The native compiler • lack of true multi-threading support, employs the byte-compiler’s internal representation as input and • garbage collection speed, exploits libgccjit to achieve code generation using the GNU Com- • code execution speed. piler Collection (GCC) infrastructure. Generated executables are From now on we will focus on the last of these issues, which con- stored as binary files and can be loaded and unloaded dynamically. stitutes the topic of this work. Most of the functionality of the compiler is written in Elisp itself, The current implementation traditionally approaches the prob- including several optimization passes, paired with a C back-end lem of code execution speed in two ways: to interface with the GNU Emacs core and libgccjit. Though still a work in progress, our implementation is able to bootstrap a func- • Implementing a large number of performance-sensitive prim- tional Emacs and compile all lexically scoped Elisp files, including itive functions (also known as subr) in C. -

An Evaluation of Go and Clojure
An evaluation of Go and Clojure A thesis submitted in partial satisfaction of the requirements for the degree Bachelors of Science in Computer Science Fall 2010 Robert Stimpfling Department of Computer Science University of Colorado, Boulder Advisor: Kenneth M. Anderson, PhD Department of Computer Science University of Colorado, Boulder 1. Introduction Concurrent programming languages are not new, but they have been getting a lot of attention more recently due to their potential with multiple processors. Processors have gone from growing exponentially in terms of speed, to growing in terms of quantity. This means processes that are completely serial in execution will soon be seeing a plateau in performance gains since they can only rely on one processor. A popular approach to using these extra processors is to make programs multi-threaded. The threads can execute in parallel and use shared memory to speed up execution times. These multithreaded processes can significantly speed up performance, as long as the number of dependencies remains low. Amdahl‘s law states that these performance gains can only be relative to the amount of processing that can be parallelized [1]. However, the performance gains are significant enough to be looked into. These gains not only come from the processing being divvied up into sections that run in parallel, but from the inherent gains from sharing memory and data structures. Passing new threads a copy of a data structure can be demanding on the processor because it requires the processor to delve into memory and make an exact copy in a new location in memory. Indeed some studies have shown that the problem with optimizing concurrent threads is not in utilizing the processors optimally, but in the need for technical improvements in memory performance [2]. -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

Project1: Build a Small Scanner/Parser
Project1: Build A Small Scanner/Parser Introducing Lex, Yacc, and POET cs5363 1 Project1: Building A Scanner/Parser Parse a subset of the C language Support two types of atomic values: int float Support one type of compound values: arrays Support a basic set of language concepts Variable declarations (int, float, and array variables) Expressions (arithmetic and boolean operations) Statements (assignments, conditionals, and loops) You can choose a different but equivalent language Need to make your own test cases Options of implementation (links available at class web site) Manual in C/C++/Java (or whatever other lang.) Lex and Yacc (together with C/C++) POET: a scripting compiler writing language Or any other approach you choose --- must document how to download/use any tools involved cs5363 2 This is just starting… There will be two other sub-projects Type checking Check the types of expressions in the input program Optimization/analysis/translation Do something with the input code, output the result The starting project is important because it determines which language you can use for the other projects Lex+Yacc ===> can work only with C/C++ POET ==> work with POET Manual ==> stick to whatever language you pick This class: introduce Lex/Yacc/POET to you cs5363 3 Using Lex to build scanners lex.yy.c MyLex.l lex/flex lex.yy.c a.out gcc/cc Input stream a.out tokens Write a lex specification Save it in a file (MyLex.l) Compile the lex specification file by invoking lex/flex lex MyLex.l A lex.yy.c file is generated -

Javascript Tomasz Pawlak, Phd Marcin Szubert, Phd Institute of Computing Science, Poznan University of Technology Presentation Outline
INTERNET SYSTEMS JAVASCRIPT TOMASZ PAWLAK, PHD MARCIN SZUBERT, PHD INSTITUTE OF COMPUTING SCIENCE, POZNAN UNIVERSITY OF TECHNOLOGY PRESENTATION OUTLINE • What is JavaScript? • Historical Perspective • Basic JavaScript • JavaScript: The Good Parts • JavaScript: The Bad Parts • Languages that compile to JavaScript • ECMAScript 6 MODERN WEB APPLICATION DATABASE SERVER HTML defines structure and content, CSS sets the formatting and appearance, JavaScript adds interactivity to a webpage and allows to create rich web applications. WHY JAVASCRIPT? • JavaScript is the language of the web browser — it is the most widely deployed programming language in history • At the same time, it is one of the most despised and misunderstood programming languages in the world • The amazing thing about JavaScript is that it is possible to get work done with it without knowing much about the language, or even knowing much about programming. It is a language with enormous expressive power. It is even better when you know what you’re doing — JAVASCRIPT: THE GOOD PARTS , DOUGLAS CROCKFORD WHY JAVASCRIPT? • Q: If you had to start over, what are the technologies, languages, paradigms and platforms I need to be up- to-date and mastering in my new world of 2014? • A: Learn one language you can build large systems with AND also learn JavaScript. • JavaScript is the language of the web. The web will persist and the web will win. That's why I suggest you learn JavaScript — S C O T T HANSELMAN , 2 0 1 4 WHAT IS JAVASCRIPT? • JavaScript is a cross-platform, object-oriented, functional, lightweight, small scripting language. • JavaScript contains a standard library of built-in objects, such as Array and Math, and a core set of language elements such as operators, control structures, and statements. -

GNU M4, Version 1.4.7 a Powerful Macro Processor Edition 1.4.7, 23 September 2006
GNU M4, version 1.4.7 A powerful macro processor Edition 1.4.7, 23 September 2006 by Ren´eSeindal This manual is for GNU M4 (version 1.4.7, 23 September 2006), a package containing an implementation of the m4 macro language. Copyright c 1989, 1990, 1991, 1992, 1993, 1994, 2004, 2005, 2006 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License.” i Table of Contents 1 Introduction and preliminaries ................ 3 1.1 Introduction to m4 ............................................. 3 1.2 Historical references ............................................ 3 1.3 Invoking m4 .................................................... 4 1.4 Problems and bugs ............................................. 8 1.5 Using this manual .............................................. 8 2 Lexical and syntactic conventions ............ 11 2.1 Macro names ................................................. 11 2.2 Quoting input to m4........................................... 11 2.3 Comments in m4 input ........................................ 11 2.4 Other kinds of input tokens ................................... 12 2.5 How m4 copies input to output ................................ 12 3 How to invoke macros........................