The Impact of Qos Changes Towards Network Performance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Traffic Management in Multi-Service Access Networks
MARKETING REPORT MR-404 Traffic Management in Multi-Service Access Networks Issue: 01 Issue Date: September 2017 © The Broadband Forum. All rights reserved. Traffic Management in Multi-Service Access Networks MR-404 Issue History Issue Approval date Publication Date Issue Editor Changes Number 01 4 September 2017 13 October 2017 Christele Bouchat, Original Nokia Comments or questions about this Broadband Forum Marketing Draft should be directed to [email protected] Editors Francois Fredricx Nokia [email protected] Florian Damas Nokia [email protected] Ing-Jyh Tsang Nokia [email protected] Innovation Christele Bouchat Nokia [email protected] Leadership Mauro Tilocca Telecom Italia [email protected] September 2017 © The Broadband Forum. All rights reserved 2 of 16 Traffic Management in Multi-Service Access Networks MR-404 Executive Summary Traffic Management is a widespread industry practice for ensuring that networks operate efficiently, including mechanisms such as queueing, routing, restricting or rationing certain traffic on a network, and/or giving priority to some types of traffic under certain network conditions, or at all times. The goal is to minimize the impact of congestion in networks on the traffic’s Quality of Service. It can be used to achieve certain performance goals, and its careful application can ultimately improve the quality of an end user's experience in a technically and economically sound way, without detracting from the experience of others. Several Traffic Management mechanisms are vital for a functioning Internet carrying all sorts of Over-the-Top (OTT) applications in “Best Effort” mode. Another set of Traffic Management mechanisms is also used in networks involved in a multi-service context, to provide differentiated treatment of various services (e.g. -

From Telkom to Hellkom1: a Critical Reflection on the Current Telecommunication Policy in South Africa from a Social Justice Perspective
ARTICLE IN PRESS + MODEL The International Information & Library Review (2008) xx,1e7 available at www.sciencedirect.com journal homepage: www.elsevier.com/locate/iilr To talk or not to talk? From Telkom to Hellkom1: A critical reflection on the current telecommunication policy in South Africa from a social justice perspective S.R. Ponelis a, J.J. Britz a,b,* a Department of Information Science, School of Information Technology, University of Pretoria, 0002 Pretoria, South Africa b School of Information Studies, University of Wisconsin-Milwaukee, 3210 N, Maryland Avenue, Milwaukee WI 53211, United States KEYWORDS Abstract With the development of new information and communication technologies, the Telecommunications; right to communicate assumes new dimensions, since it is almost impossible to fully participate Right to communicate; in the globalized world without access to modern information and communication technolo- South Africa; gies. South Africa held its first democratic elections in 1994 and has subsequently returned Telkom; to the international arena. Its citizens should rightly expect to be able to participate in all that Social justice this return offers, not only politically, but also economically and socially. Telecommunications are vital to making such participation possible. In recognition of this fact, the newly elected government developed policies and enacted legislation to ensure that the telecommunications sector, and specifically the sole fixed line service provider Telkom, provides South African citi- zens affordable access to the telecommunications infrastructure whilst providing acceptable levels of service. However, rather than meeting its obligation to the government and the people of South Africa, Telkom has misused its monopoly. The social injustice that this situa- tion creates is critically examined against the background of the right to communicate based on Rawls’ principles of social justice and Sen’s capability approach. -

Analysing TCP Performance When Link Experiencing Packet Loss
Analysing TCP performance when link experiencing packet loss Master of Science Thesis [in the Programme Networks and Distributed System] SHAHRIN CHOWDHURY KANIZ FATEMA Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering Göteborg, Sweden, October 2013 The Author grants to Chalmers University of Technology and University of Gothenburg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he/she is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he/she has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Analysing TCP performance when link experiencing packet loss SHAHRIN CHOWDHURY, KANIZ FATEMA © SHAHRIN CHOWDHURY, October 2013. © KANIZ FATEMA, October 2013. Examiner: TOMAS OLOVSSON Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering SE-412 96 Göteborg Sweden Telephone + 46 (0)31-772 1000 Department of Computer Science and Engineering Göteborg, Sweden October 2013 Acknowledgement We are grateful to our supervisor and examiner Tomas Olovsson for his valuable time and assistance in compilation for this thesis. -
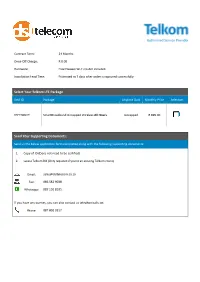
Authorised Service Provider Select Your Telkom LTE Package Send
Authorised Service Provider Contract Term: 24 Months Once-Off Charge: R 0.00 Hardware: Free Huawei Wi-Fi router included. Installation Lead Time: Estimated at 7 days after order is captured successfully. Select Your Telkom LTE Package Deal ID Package Anytime Data Monthly Price Selection DSF1908019 SmartBroadband Uncapped Wireless All Hours Uncapped R 899.00 Send Your Supporting Documents: Send us the below application form completed along with the following supporting documents: 1. Copy of ID (Does not need to be certified) 2. Latest Telkom Bill (Only required if you're an existing Telkom client) Email: [email protected] Fax: 086 582 9038 Whatsapp: 087 150 8595 If you have any queries, you can also contact us telephonically on: Phone: 087 802 0917 Delivery Address: You will need to personally sign for the delivery Consumer Application Form Address 1: Agent to complete: Address 2: New application Change of ownership Suburb: Porting of mobile number Customer relocation Service required Fixed Mobile Convergence City: Agent name Campaign name Postal Code: Order no. Account no. System customer ID. Supporting documentation • Proof of identification: Copy of SA ID or passport (including work permit) • Copy of your most recent payslip and three months’ bank statements • Copy of proof of residence (utility bill not older than three months) MASTER DEALER CODE: F2 • For porting purposes, account number at donor/existing service provider required ORIGINAL 1. Customer details Are you an existing customer? Yes No If yes, what is your existing number? Title Surname First names SA Citizen Yes No Identity/Passport no. Passport expiry date Gender M F Date of birth Contact details Home no. -

GENERATION TECHNOLOGY Your Mall Is Now Powered by Fibre - Move to High-Speed Connectivity Today
MEET THE FUTURE TODAY WITH NEXT GENERATION TECHNOLOGY Your mall is now powered by Fibre - move to high-speed connectivity today. Meet the Future Today with Next-Generation Data Solutions Congratulations! Your mall is now powered by Boltspeed Fibre. Take advantage of high- speed connectivity that enables next-generation solutions to help you reduce operational costs, increase productivity and grow your business. Speak to your business consultant today to find out about tailor-made solutions just for you so that we can take your business into the future, today. Why is Telkom the best suited to provide you with a customised solution? The best tech you can rely on to keep you connected Telkom’s network has been the backbone of South Africa’s fixed internet operations for most of the country’s online history. It’s also incredibly secure, with multiple redundancies and network monitoring giving it the best availability and uptime in South Africa. We are the largest WiFi network in SA with over 6000 WiFi hotspots, boosting our already great 3G network. Added to our unparalleled fibre and copper networks, and the rollout of our superfast LTE-Advanced network throughout the country, you can be assured that we’ve got you covered wherever you are. And this comes with all the tech you’d expect from a leading ICT partner. So you can add IT & Cloud services, Hardware and Software, Managed Print Services, Electronic Document Management and Mobility solutions – anything you can think of – to your existing Telkom solution quickly and easily. The best value for your money Together, Telkom and Business Connexion create an end-to-end ICT partner with the breadth and scale to take your business into the future. -

Adaptive Method for Packet Loss Types in Iot: an Naive Bayes Distinguisher
electronics Article Adaptive Method for Packet Loss Types in IoT: An Naive Bayes Distinguisher Yating Chen , Lingyun Lu *, Xiaohan Yu * and Xiang Li School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China; [email protected] (Y.C.); [email protected] (X.L.) * Correspondence: [email protected] (L.L.); [email protected] (X.Y.) Received: 31 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: With the rapid development of IoT (Internet of Things), massive data is delivered through trillions of interconnected smart devices. The heterogeneous networks trigger frequently the congestion and influence indirectly the application of IoT. The traditional TCP will highly possible to be reformed supporting the IoT. In this paper, we find the different characteristics of packet loss in hybrid wireless and wired channels, and develop a novel congestion control called NB-TCP (Naive Bayesian) in IoT. NB-TCP constructs a Naive Bayesian distinguisher model, which can capture the packet loss state and effectively classify the packet loss types from the wireless or the wired. More importantly, it cannot cause too much load on the network, but has fast classification speed, high accuracy and stability. Simulation results using NS2 show that NB-TCP achieves up to 0.95 classification accuracy and achieves good throughput, fairness and friendliness in the hybrid network. Keywords: Internet of Things; wired/wireless hybrid network; TCP; naive bayesian model 1. Introduction The Internet of Things (IoT) is a new network industry based on Internet, mobile communication networks and other technologies, which has wide applications in industrial production, intelligent transportation, environmental monitoring and smart homes. -

WELCOME to the WORLD of ETSI an Overview of the European Telecommunication Standards Institute
WELCOME TO THE WORLD OF ETSI An overview of the European Telecommunication Standards Institute © ETSI 2016. All rights reserved © ETSI 2016. All rights reserved European roots, global outreach ETSI is a world-leading standards developing organization for Information and Communication Technologies (ICT) Founded initially to serve European needs, ETSI has become highly- respected as a producer of technical standards for worldwide use © ETSI 2016. All rights reserved Products & services Technical specifications and standards with global application Support to industry and European regulation Specification & testing methodologies Interoperability testing © ETSI 2016. All rights reserved Membership Over 800 companies, big and small, from 66 countries on 5 continents Manufacturers, network operators, service and content providers, national administrations, ministries, universities, research bodies, consultancies, user organizations A powerful and dynamic mix of skills, resources and ambitions © ETSI 2016. All rights reserved Independence Independent of all other organizations and structures Respected for neutrality and trustworthiness Esteemed for our world-leading Intellectual Property Rights (IPR) Policy © ETSI 2016. All rights reserved Collaboration Strategic collaboration with numerous global and regional standards-making organizations and industry groupings Formally recognized as a European Standards Organization, with a global perspective Contributing technical standards to support regulation Defining radio frequency requirements for -

A Comparison of Voip Performance on Ipv6 and Ipv4 Networks
A Comparison of VoIP Performance on IPv6 and IPv4 Networks Roman Yasinovskyy, Alexander L. Wijesinha, Ramesh K. Karne, and Gholam Khaksari Towson University increasingly used on the Internet today. The increase Abstract—We compare VoIP performance on IPv6 in IPv6 packet size due to the larger addresses is and IPv4 LANs in the presence of varying levels of partly offset by a streamlined header with optional background UDP traffic. A conventional softphone is extension headers (the header fields in IPv4 for used to make calls and a bare PC (operating system- fragmentation support and checksum are eliminated less) softphone is used as a control to determine the impact of system overhead. The performance measures in IPv6). are maximum and mean delta (the time between the As the growing popularity of VoIP will make it a arrival of voice packets), maximum and mean jitter, significant component of traffic in the future Internet, packet loss, MOS (Mean Opinion Score), and it is of interest to compare VoIP performance over throughput. We also determine the relative frequency IPv6 and IPv4. The results would help to determine if distribution for delta. It is found that mean values of there are any differences in VoIP performance over delta for IPv4 and IPv6 are similar although maximum values are much higher than the mean and show more IPv6 compared to IPv4 due to overhead resulting variability at higher levels of background traffic. The from the larger IPv6 header (and packet size). We maximum jitter for IPv6 is slightly higher than for IPv4 focus on comparing VoIP performance with IPv6 and but mean jitter values are approximately the same. -

Impact of Packet Losses on the Quality of Video Streaming
Master Thesis Electrical Engineering Thesis no: MEE10:44 June 2010 Impact of Packet Losses on the Quality of Video Streaming JOHN Samson Mwela & OYEKANLU Emmanuel Adebomi School of Computing Internet : www.bth.se/com School of Computing Blekinge Institute of Technology Phone : +46 457 38 50 00 Blekinge Institute of Technology Box 520 Fax : + 46 457 271 25 Box 520 i SE – 371 79Karlskrona SE – 372 25 Ronneby Sweden Sweden This thesis is submitted to the School of Computing at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering. The thesis is equivalent to 20 weeks of full time studies. Contact Information: Author(s): JOHN Samson Mwela Blekinge Institute of Technology E-mail: [email protected] OYEKANLU Emmanuel Adebomi Blekinge Institute of Technology E-mail: [email protected] Supervisor Tahir Nawaz Minhas School of Computing Examiner Dr. Patrik Arlos, PhD School of Computing School of Computing Blekinge Institute of Technology Box 520 SE – 371 79 Karlskrona Sweden i ABSTRACT In this thesis, the impact of packet losses on the quality of received videos sent across a network that exhibit normal network perturbations such as jitters, delays, packet drops etc has been examined. Dynamic behavior of a normal network has been simulated using Linux and the Network Emulator (NetEm). Peoples’ perceptions on the quality of the received video were used in rating the qualities of several videos with differing speeds. In accordance with ITU’s guideline of using Mean Opinion Scores (MOS), the effects of packet drops were analyzed. Excel and Matlab were used as tools in analyzing the peoples’ opinions which indicates the impacts that different loss rates has on the transmitted videos. -

What Causes Packet Loss IP Networks
What Causes Packet Loss IP Networks (Rev 1.1) Computer Modules, Inc. DVEO Division 11409 West Bernardo Court San Diego, CA 92127, USA Telephone: +1 858 613 1818 Fax: +1 858 613 1815 www.dveo.com Copyright © 2016 Computer Modules, Inc. All Rights Reserved. DVEO, DOZERbox, DOZER Racks and DOZER ARQ are trademarks of Computer Modules, Inc. Specifications and product availability are subject to change without notice. Packet Loss and Reasons Introduction This Document To stream high quality video, i.e. to transmit real-time video streams, over IP networks is a demanding endeavor and, depending on network conditions, may result in packets being dropped or “lost” for a variety of reasons, thus negatively impacting the quality of user experience (QoE). This document looks at typical reasons and causes for what is generally referred to as “packet loss” across various types of IP networks, whether of the managed and conditioned type with a defined Quality of Service (QoS), or the “unmanaged” kind such as the vast variety of individual and interconnected networks across the globe that collectively constitute the public Internet (“the Internet”). The purpose of this document is to encourage operators and enterprises that wish to overcome streaming video quality problems to explore potential solutions. Proven technology exists that enables transmission of real-time video error-free over all types of IP networks, and to perform live broadcasting of studio quality content over the “unmanaged” Internet! Core Protocols of the Internet Protocol Suite The Internet Protocol (IP) is the foundation on which the Internet was built and, by extension, the World Wide Web, by enabling global internetworking. -

02 Eassy Submarine Cable
IMPACT ASSESSMENT CASE STUDIES FROM SOUTHERN AFRICA Compiled by Paul Scherzer SAIEA E&D Consulting Services Client: Telkom SA Southern African Institute for Environmental Assessment ... working for a better Africa ROUTING OF THE EASSy SUBMARINE CABLE, SOUTH AFRICA Compiled by Paul Scherzer E&D Consulting Services Client: Telkom SA ROUTING OF THE EASSy SUBMARINE CABLE, SOUTH AFRICA Aims of the Project Brief description of the development and alternatives considered Telkom SA operates existing submarine fibre- Submarine telecommunication cables form a vital optic telecommunication cables in South African part of the global communications network. Fibre waters from two landing locations, one on the optic cables are essentially tiny glass fibres which west coast and the other at Mtunzini on the east. transmit digital pulses converted by computers at The South Africa Far East (SAFE) submarine cable was landed at Mtunzini in 2001. The existing cable station and shore-based infrastructure at Mtunzini had capacity for an additional cable. Telkom SA proposed to land another cable, the East Africa Submarine System telecommunica- tions cable (EASSy), on the main beach of Mtunzini. The aim of the proposed EASSy cable was to Figure 2: Illustration of cables enhance telecommunication links along the east and increasing levels of armouring coast of Africa, as this region relies exclusively on satellite which is expensive and limited in capacity. each end of the cable. A typical lightweight cable has a 17 mm outer diameter and comprises a welded steel tube housing multiple fibre pairs in a stress-free environment. In order to protect the cable, depending on the level of risk, the number and diameter of armour wires surrounding the cable is increased, with a high strength double armoured cable having an outer diameter of Figure 1: Route of the proposed EASSy cable approximately 45 mm (Figure 2). -

Telkom Workshop with the Portfolio Committee on Communications in Parliament
Telkom Workshop with the Portfolio Committee on Communications in Parliament 06 – 07 October 2004 Terms of Reference The Portfolio Committee on Communications has requested Telkom to present on the technical and regulatory aspects of its business 2 Introducing the Telkom Delegation • Nkenke Kekana Group Executive – Regulatory & Public Policy • Benitto Lekalakala Executive – Parliament, Policy & Legislation • Wally Broeders Executive – Integrated Network Planning • Jack Tlokana Senior Specialist – RC: Advanced Technology • Graham Keet Senior Specialist – RC: Special Markets • Josephine Mabotja Senior Specialist – Competition Law & Economics • Izaak Coetzee Senior Specialist - Regulatory Economics • Nozicelo Ngcobo Senior Specialist – Research and Strategy • Keso Mbali Senior Specialist - Multi-media and Convergence • Maphelo Mvunelwa Specialist – Parliamentary Liaison 3 Agenda items • Overview of the Current • Interconnection Regulatory Environment • Carrier Pre-Selection • Overview of the Expected Regulatory Environment • Number Portability • Telkom Licences • Network Planning and Management • Numbering Plans • Square Kilometre Array (SKA) • COA/CAM • Convergence 4 Overview of the Current Regulatory Environment in South Africa International Telecommunications Reform • Early 1990’s - end of telecommunications natural monopoly across the world as administered by governments • Economic and technological developments necessitated a review of the treatment of telecommunications • WTO, ITU, EU and other international bodies reassessed the increasing