Embedded Linux from Scratch in 45 Minutes (On RISC-V)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -

Data ONTAP® 8.2 Commands: Manual Page Reference for 7-Mode, Volume 1
Data ONTAP® 8.2 Commands: Manual Page Reference For 7-Mode, Volume 1 NetApp, Inc. Telephone: +1 (888) 463-8277 Part Number: 215-07976_A0 495 East Java Drive Fax: +1(408) 822-4501 May 2013 Sunnyvale, CA 94089 Support telephone: +1(888) 4-NETAPP U.S. Web: www.netapp.com Feedback: [email protected] Table of Contents ...................... 1 About the Data ONTAP Commands: Manual Page Reference, Volume 1 .3.... Manual Pages by Section in This Volume and Complete Index of Both Volumes .5.. acpadmin ................... 18 aggr ..................... 20 arp ..................... 41 autosupport ................... 43 backup .................... 53 bmc ..................... 55 bootfs .................... 57 cdpd ..................... 58 cf ..................... 61 charmap .................... 64 cifs ..................... 66 cifs_access ................... 68 cifs_adupdate .................. 70 cifs_audit ................... 71 cifs_branchcache .................. 72 cifs_broadcast .................. 74 cifs_changefilerpwd .7................ 5 cifs_comment ............. ..... 76 cifs_domaininfo .................. 77 cifs_help .................... 79 cifs_homedir ................... 80 cifs_lookup ................... 81 cifs_nbalias ................... 82 cifs_prefdc ................... 83 cifs_resetdc ................... 85 cifs_restart ................... 86 cifs_sessions ................... 87 cifs_setup ................... 91 cifs_shares ................... 93 cifs_sidcache ................... 102 cifs_stat .................... 104 cifs_terminate -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

Building a Beowulf Cluster
Building a Beowulf cluster Åsmund Ødegård April 4, 2001 1 Introduction The main part of the introduction is only contained in the slides for this session. Some of the acronyms and names in this paper may be unknown. In Appendix B we includ short descriptions for some of them. Most of this is taken from “whatis” [6] 2 Outline of the installation ² Install linux on a PC ² Configure the PC to act as a install–server for the cluster ² Wire up the network if that isn’t done already ² Install linux on the rest of the nodes ² Configure one PC, e.g the install–server, to be a server for your cluster. These are the main steps required to build a linux cluster, but each step can be done in many different ways. How you prefer to do it, depends mainly on personal taste, though. Therefor, I will translate the given outline into this list: ² Install Debian GNU/Linux on a PC ² Install and configure “FAI” on the PC ² Build the “FAI” boot–floppy ² Assemble hardware information, and finalize the “FAI” configuration ² Boot each node with the boot–floppy ² Install and configure a queue system and software for running parallel jobs on your cluster 3 Debian The choice of Linux distribution is most of all a matter of personal taste. I prefer the Debian distri- bution for various reasons. So, the first step in the cluster–building process is to pick one of the PCs as a install–server, and install Debian onto it, as follows: ² Make sure that the computer can boot from cdrom. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

For the Abstract.The-Revision Deletion, Orcreation,Of Sentences Is
DOCUMENT REBUKE ED 071 886 LI.004 082 AUTHOR Mathis, Betty. Ann TITLE Techniques for the Evaluation and IMprovement of Computer-Produced Abstracts. INSTITUTION Ohio State Univ".Colulbus..Computer and Information Science, Research.Center.. SPONS AGENCY National Science Foundation, Washington, D.C. REPORT NO OSU-CISRC-TR-15 . PUB DATE Dec 72 NOTE 275p.;(202 References) EDRS PRICE MF-30.65 HC-49.87 DESCRIPTORS *Abstracting;,,Abstracts; Algorithms; *Automation; CoMputers; *Electrohit Data Processing; Evaluation; Periodicals IDENTIFIERS *Automatic Abstracting ABSTRACT An automatic abstracting system, named ADAM, implemented on the IBM 370, receives journal.articles as input and produces abstracts as output. An algorithm has- been.developed which considers every sentence in the input text and rejects sentences which, are not suitable for inclusion in the abstract. All sentences which are not rejected are included in the set of sentences which are candidates for inclusion in the abstract.,The quality of the abstracts can be evaluated by means of a two -step evaluation procedUre.,The 'first step determines the conforMity of the abstracts to the defined criteria for an acceptable abstract The aecond step provides an objective evaluation criterion for abstract quality based on a.compsrison of the abstract with 'its parent documere,-. Based on the results of this evaluation, several techniques have been developed to improve the quality of the abstracts. These procedures -modify the form, arrangement, and content of the sentences selected for the abstract.The-revision deletion, orcreation,of sentences is perfOrmed according to a number of generalized ruletwhich are based on the structural characteriitics of the sentences.. This modification produces' abstracts in which the flow of ideas is improved and which represent a more nearly cohcrent:whole..(AuthorISJ) - - TECIfigICAL REPORT SERIES 4 CO1PUTE13 1r1fiFilliTTO S. -
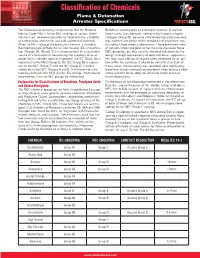
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced. -

Oracle® Linux 7 Managing File Systems
Oracle® Linux 7 Managing File Systems F32760-07 August 2021 Oracle Legal Notices Copyright © 2020, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Filesystem Considerations for Embedded Devices ELC2015 03/25/15
Filesystem considerations for embedded devices ELC2015 03/25/15 Tristan Lelong Senior embedded software engineer Filesystem considerations ABSTRACT The goal of this presentation is to answer a question asked by several customers: which filesystem should you use within your embedded design’s eMMC/SDCard? These storage devices use a standard block interface, compatible with traditional filesystems, but constraints are not those of desktop PC environments. EXT2/3/4, BTRFS, F2FS are the first of many solutions which come to mind, but how do they all compare? Typical queries include performance, longevity, tools availability, support, and power loss robustness. This presentation will not dive into implementation details but will instead summarize provided answers with the help of various figures and meaningful test results. 2 TABLE OF CONTENTS 1. Introduction 2. Block devices 3. Available filesystems 4. Performances 5. Tools 6. Reliability 7. Conclusion Filesystem considerations ABOUT THE AUTHOR • Tristan Lelong • Embedded software engineer @ Adeneo Embedded • French, living in the Pacific northwest • Embedded software, free software, and Linux kernel enthusiast. 4 Introduction Filesystem considerations Introduction INTRODUCTION More and more embedded designs rely on smart memory chips rather than bare NAND or NOR. This presentation will start by describing: • Some context to help understand the differences between NAND and MMC • Some typical requirements found in embedded devices designs • Potential filesystems to use on MMC devices 6 Filesystem considerations Introduction INTRODUCTION Focus will then move to block filesystems. How they are supported, what feature do they advertise. To help understand how they compare, we will present some benchmarks and comparisons regarding: • Tools • Reliability • Performances 7 Block devices Filesystem considerations Block devices MMC, EMMC, SD CARD Vocabulary: • MMC: MultiMediaCard is a memory card unveiled in 1997 by SanDisk and Siemens based on NAND flash memory. -

EM316LNXNM-OT Network Manager with Linux
EM316LNXNM-OT Network Manager with Linux Fiber Driver Optical Multi-Service Platform Published 2012/10/17 15:28:24 P/N 1275005-100 Revision E6 ( -build r21138- ) For EM316LNXNM v4.7 fdr 39 built Oct 16 2012 - 19:07:17 EM316LNXNM-OT Preface Copyright © 2012 MRV Communications, Inc. All rights reserved. No part of the contents of this document may be reproduced in any form or by any other means without written permission from the publisher. Fiber Driver, Media Cross Connect, MegaVision, and other MRV product names and terms belong to MRV Communications or affiliates. All other brand names or trademarks referenced are the property of their respective owners. This document includes electronic links and URLs that may require internet access. Some references may not be obvious on printed pages. The user assumes sole responsibility for applying the information supplied in product documents. MRV Communications reserves the right to make changes to technical specifications and documentation without notice. This document represents the most recent product versions at the time of writing, which may differ from previous releases. To ensure maximum functionality, use the latest software updates and documents. Contact customer support regarding previous product revisions and documents. PN 1275005-100 Rev E6 intro- 2 EM316LNXNM-OT Preface Table of Contents 1. Support and Safety .......................................................................................................... 1 1.1. Customer Support ................................................................................................ -

Dwarf's Guide to Debian GNU/Linux
Dwarf’s Guide to Debian GNU/Linux 2001 Dale Scheetz Dwarf’s Guide to Debian GNU/Linux Copyright c 2001 Dale Scheetz Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with the Invariant Sections being Chapter 1 Introduction, with no Front-Cover Texts, and with the Back-Cover Texts being “The early development of the material in this work was produced with the financial support of Planet Linux. This support was intrumental in bringing this project to completion.” A copy of the license is included in the section entitled “Appendix 9: GNU Free Documentation License” which can be found on page 271. Trademark Acknowledgements All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. The publisher cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. Apple and Macintosh are registered trademarks of Apple Computer, Inc. CP/M is a registered trademark of Caldera, Inc. IBM is a registered trademark of International Business Machines, Inc. MS is a trademark of Microsoft Corporation. Windows is a trademark of Microsoft Corporation. X Window System is a registered trademark of X Consortium, Inc. ii dedicated to Linux users everywhere iii CREDITS First I want to thank Ian Murdock for writing the History section. His per- spectives on those early years have helped latecomers like Dwarf understand the founding principles upon which Debian is based. -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification.