Thoughts on Force Protection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CNA's Integrated Ship Database
CNA’s Integrated Ship Database Second Quarter 2012 Update Gregory N. Suess • Lynette A. McClain CNA Interactive Software DIS-2012-U-003585-Final January 2013 Photo credit “Description: (Cropped Version) An aerial view of the aircraft carriers USS INDEPENDENCE (CV 62), left, and USS KITTY HAWK (CV 63), right, tied up at the same dock in preparation for the change of charge during the exercise RIMPAC '98. Location: PEARL HARBOR, HAWAII (HI) UNITED STATES OF AMERICA (USA) The USS INDEPENDENCE was on its way to be decommissioned, it was previously home ported in Yokosuka, Japan. The crew from the USS INDEPENDENCE cross decked onto the USS KITTY HAWK and brought it back to Atsugi, Japan. The USS INDEPENDENCE was destined for a ship yard in Washington. Source: ID"DN-SD- 00-01114 / Service Depicted: Navy / 980717-N-3612M-001 / Operation / Series: RIMPAC `98. Author: Camera Operator: PH1(NAC) JAMES G. MCCARTER,” Jul. 17, 1998, WIKIMEDIA COMMONS, last accessed Dec. 20, 2012, at http://commons.wikimedia.org/wiki/File:USS_Independence_(CV- 62)_and_USS_Kitty_Hawk_(CV-63)_at_Pearl_Harbor_crop.jpg Approved for distribution: January 2013 Dr. Barry Howell Director, Warfare Capabilities and Employment Team Operations and Tactics Analysis This document represents the best opinion of CNA at the time of issue. It does not necessarily represent the opinion of the Department of the Navy. APPROVED FOR PUBLIC RELEASE. DISTRIBUTION UNLIMITED. Copies of this document can be obtained through the Defense Technical Information Center at www.dtic.mil or contact CNA Document Control and Distribution Section at 703-824-2123. Copyright 2013 CNA This work was created in the performance of Federal Government Contract Number N00014-11-D-0323. -

The Terrorist Naval Mine/Underwater Improvised Explosive Device Threat
Walden University ScholarWorks Walden Dissertations and Doctoral Studies Walden Dissertations and Doctoral Studies Collection 2015 Port Security: The eT rrorist Naval Mine/ Underwater Improvised Explosive Device Threat Peter von Bleichert Walden University Follow this and additional works at: https://scholarworks.waldenu.edu/dissertations Part of the Public Policy Commons This Dissertation is brought to you for free and open access by the Walden Dissertations and Doctoral Studies Collection at ScholarWorks. It has been accepted for inclusion in Walden Dissertations and Doctoral Studies by an authorized administrator of ScholarWorks. For more information, please contact [email protected]. Walden University College of Social and Behavioral Sciences This is to certify that the doctoral dissertation by Peter von Bleichert has been found to be complete and satisfactory in all respects, and that any and all revisions required by the review committee have been made. Review Committee Dr. Karen Shafer, Committee Chairperson, Public Policy and Administration Faculty Dr. Gregory Dixon, Committee Member, Public Policy and Administration Faculty Dr. Anne Fetter, University Reviewer, Public Policy and Administration Faculty Chief Academic Officer Eric Riedel, Ph.D. Walden University 2015 Abstract Port Security: The Terrorist Naval Mine/Underwater Improvised Explosive Device Threat by Peter A. von Bleichert MA, Schiller International University (London), 1992 BA, American College of Greece, 1991 Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy Public Policy and Administration Walden University June 2015 Abstract Terrorist naval mines/underwater improvised explosive devices (M/UWIEDs) are a threat to U.S. maritime ports, and could cause economic damage, panic, and mass casualties. -

Air Base Defense Rethinking Army and Air Force Roles and Functions for More Information on This Publication, Visit
C O R P O R A T I O N ALAN J. VICK, SEAN M. ZEIGLER, JULIA BRACKUP, JOHN SPEED MEYERS Air Base Defense Rethinking Army and Air Force Roles and Functions For more information on this publication, visit www.rand.org/t/RR4368 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-1-9774-0500-5 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2020 RAND Corporation R® is a registered trademark. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface The growing cruise and ballistic missile threat to U.S. Air Force bases in Europe has led Headquarters U.S. -

Fall 2014 1 MC
FALL 2014 TABLE OF CONTENTS MCO VISION ……………………………………………...3 WELCOME ABOARD……………………………………..4-5 CO FAREWELL…………………………………………....6-7 SUMMER CRUISE/OCS…………………………………...8-9 NEW STUDENT ORIENTATION……………………...…..10-11 MIDSHIPMEN OF THE SEMESTER ………………….….12-14 HALOWEEN RUN……………………………...………….15-16 MEDAL OF HONOR SCHOLARSHIP…………………….17 ADMIRAL HOWARD VISIT…...………………………….18 MILITARY BALL…………………………………………...19 FALL COMISSIONING…………………………………….20 Vision for the Unit I envision a unit that is not a collection of individuals pushing for the common goal of Commissioning in the Navy and Marine Corps, but a team who collectively challenges, inspires, and holds each other accountable for the standards that we must maintain as future officers. As each class progresses though the unit, overcoming different trials and learning from new experience, I want them to build a sense of pride in their work and begin to develop a sense of dedication and humility for those who they are charged with supervising as they begin to hold billets within the Midshipman Company. As future officers, the midshipmen need to learn that they are in place to serve their people. This should reflect in their actions while they are in this unit. I want this unit to run in as close accordance to the fleet as possible, to include many duties and responsibilities, to ensure that they have the time management and leadership qualities that will be expected of them after they leave Savannah State University. We need to ensure that the fleet is receiving the most well-rounded and committed junior officers as it can get so that Marines and Sailors are getting the leaders that they deserve. -

Naval Accidents 1945-1988, Neptune Papers No. 3
-- Neptune Papers -- Neptune Paper No. 3: Naval Accidents 1945 - 1988 by William M. Arkin and Joshua Handler Greenpeace/Institute for Policy Studies Washington, D.C. June 1989 Neptune Paper No. 3: Naval Accidents 1945-1988 Table of Contents Introduction ................................................................................................................................... 1 Overview ........................................................................................................................................ 2 Nuclear Weapons Accidents......................................................................................................... 3 Nuclear Reactor Accidents ........................................................................................................... 7 Submarine Accidents .................................................................................................................... 9 Dangers of Routine Naval Operations....................................................................................... 12 Chronology of Naval Accidents: 1945 - 1988........................................................................... 16 Appendix A: Sources and Acknowledgements........................................................................ 73 Appendix B: U.S. Ship Type Abbreviations ............................................................................ 76 Table 1: Number of Ships by Type Involved in Accidents, 1945 - 1988................................ 78 Table 2: Naval Accidents by Type -

USS Cliff on Sprague (FFG 16) Lower the Ship’S Motor Whaleboat Into the I
1 I. 1 an S- NOVEMBER 1994 NUMBER 931 L Sailors assignedto USS Cliff on Sprague (FFG 16) lower the ship’s motor whaleboat into the I OPERATIONS TRAINING 6 Burke-class: fleet-friendly 30 Virtual shipdriving 8 Future missile defense 32 1 st classes have the ,conn 10 Tomahawks on target, on time 34 The struggle to earn ESWS 12 USS Port Royal (CG 73) 36 Aegis Training Center respondsto fleet 14 Marines ... Forward from the sea 37 First women undergo Aegis training 18 USS Wasp (LHD 1) 38 Reserve ships exercise in Atlantic 20 Enlisted skippers 40 Prep0 ships pack punch 21 Precom duty-the right stuff 42 SWOS instructors excel 26 Sustain gives ships alift 44 Haze gray and fightingfit 46 On the surface- Who’s who’! 2 CHARTHOUSE 48 SHIPMATES On the Covers Front cower: USS Deyo (DD 989) and other battle group ships followed in the wakeUSS of George Washington (CVN 73) as they returnedto Norfolk earlier this year. (Photoby PHI (AW) Troy D. Summers) Back cower: 1994 Sailors of the Year. (Photos by PHC(AW) Joseph Dorey andPHI Dolores L. Anglin) Correction: The Navy celebrated 21its 9th birthday vice its21 8th as writ- ten in the October magazine. ed. I Cha~house ? 2 ALL HANDS Hispar ,,- . Asinn-1ent to increase Islander a Americt a Islander VADM Skip Bowman them aswe Specific details of the ac 1 pull out of the planwill be annc:ed - For the Record drawdown. By way of introduction, I’m proud We are to report as your head cheerleader - continuing a officially your new Chief of Naval Per- sonnel - “your” Chief of Naval Person- nel, because my job is to be your ad- vocate,yourspokesman in initiatibes. -

US Military Policy in the Middle East: an Appraisal
Research Paper Micah Zenko US and the Americas Programme | October 2018 US Military Policy in the Middle East An Appraisal US Military Policy in the Middle East: An Appraisal Contents Summary 2 1 Introduction 3 2 Domestic Academic and Political Debates 7 3 Enduring and Current Presence 11 4 Security Cooperation: Training, Advice and Weapons Sales 21 5 Military Policy Objectives in the Middle East 27 Conclusion 31 About the Author 33 Acknowledgments 34 1 | Chatham House US Military Policy in the Middle East: An Appraisal Summary • Despite significant financial expenditure and thousands of lives lost, the American military presence in the Middle East retains bipartisan US support and incurs remarkably little oversight or public debate. Key US activities in the region consist of weapons sales to allied governments, military-to-military training programmes, counterterrorism operations and long-term troop deployments. • The US military presence in the Middle East is the culmination of a common bargain with Middle Eastern governments: security cooperation and military assistance in exchange for US access to military bases in the region. As a result, the US has substantial influence in the Middle East and can project military power quickly. However, working with partners whose interests sometimes conflict with one another has occasionally harmed long-term US objectives. • Since 1980, when President Carter remarked that outside intervention in the interests of the US in the Middle East would be ‘repelled by any means necessary’, the US has maintained a permanent and significant military presence in the region. • Two main schools of thought – ‘offshore balancing’ and ‘forward engagement’ – characterize the debate over the US presence in the Middle East. -

Not for Publication Until Released by the House Armed Service Committee
NOT FOR PUBLICATION UNTIL RELEASED BY THE HOUSE ARMED SERVICE COMMITTEE STATEMENT OF THE HONORABLE RAY MABUS SECRETARY OF THE NAVY BEFORE THE HOUSE ARMED SERVICES COMMITTEE ON 16 APRIL 2013 NOT FOR PUBLICATION UNTIL RELEASED BY THE HOUSE ARMED SERVICES COMMITTEE 1 Secretary of the Navy 5/19/2009 - Present Ray Mabus Ray Mabus is the 75th United States Secretary of the Navy and leads America's Navy and Marine Corps. As Secretary of the Navy, Mabus is responsible for conducting the affairs of the Department of the Navy, including recruiting, organizing, equipping, training and mobilizing. Additionally, he oversees the construction and repair of naval ships, aircraft, and facilities, and formulates and implements policies and programs consistent with the national security policies established by the President and the Secretary of Defense. Secretary Mabus is responsible for an annual budget in excess of $170 billion and leadership of almost 900,000 people. Upon assumption of office and throughout his tenure, Mabus has prioritized improving the quality of life of Sailors, Marines and their families, decreasing the Department’s dependence on fossil fuels, strengthening partnerships and revitalizing the Navy’s shipbuilding program. Leading the world’s only global Navy, Mabus has traveled almost 670 thousand miles to over 95 countries to maintain and develop relationships with national and international officials and visit with Sailors and Marines forward deployed or stationed around the world. He has traveled to Afghanistan on ten separate occasions, in recognition of the sacrifice and service of Sailors and Marines deployed in combat zones. To prepare service members and their families for the high tempo operations of today’s Navy and Marine Corps, Mabus announced in 2012 the “21st Century Sailor and Marine” initiative, designed to build and maintain the most resilient and ready force possible. -

Change of Command, 25 June 2015
Calhoun: The NPS Institutional Archive Institutional Publications Institutional Publications (Other) 2015-06-25 Change of Command, 25 June 2015 Naval Postgraduate School Monterey, California: Naval Postgraduate School http://hdl.handle.net/10945/46476 Change of Command 25 June 2015 Naval Support Activity Monterey front lawn Welcome Aboard! Commanding Officer, Naval Support Activity Monterey extends a cordial "Welcome Aboard," to our guests and friends. Today marks the second change of command since the installation was established on 30 September 2010. We are pleased that you can join us today in sharing this important event in the command's history. Please join Captain Bertelsen and Captain Faller for a reception in the Trident Room following the ceremony. PREPARED FOR WAR. COMMITTED TO PEACE. Schedule of Events REMARKS Captain Timothy Faller ARRIVAL OF OFFICIAL PARTY* Commanding Officer, Naval Support Activity Monterey NATIONAL ANTHEM* i.. READING OF ORDERS* INVOCATION* Captain Timothy Faller Lieutenant Commander John Van Dyke READING OF ORDERS* WELCOME Captain Kevin Bertelsen Captain Timothy Faller Commanding Officer, REMARKS Naval Support Activity Monterey Captain Kevin Bertelsen Commanding Officer, REMARKS Naval Support Activity Monterey r Rear Admiral Patrick Lorge i' Commander, Navy Region Southwest BENEDICTION* Lieutenant Commander John Van Dyke *Guests please rise for these events Rear Admiral Patrick Lorge, USN He served as executive Commander, Navy Region Southwest assistant to the Assis tant to the Chairman, ear Admiral Patrick Lorge, a native of Turnersville, Joint Chiefs of Staff un R New Jersey, graduated from the U.S. Naval Acade til March 2004. my In 1981. He completed flight training in April 1983 Reporting to Naval Air and remained as a flight instructor in VT-26. -

Unmanned Underwater Vehicle Independent Test and Evaluation
Unmanned Underwater Vehicle Independent Test and Evaluation William P. Ervin, J. Patrick Madden, and George W. Pollitt he Johns Hopkins University Applied Physics Laboratory (APL) has a long history of contributing to unmanned undersea or underwater vehicle (UUV) programs sponsored by several Navy acquisition program offices. Those contributions span the systems engineering realm, including leadership of independent test and evaluation for prototypes and systems fielded for military use. One of the most endur- ing relationships has been with Program Manager Naval Sea Systems Command (Expedi- tionary Missions) (PMS-408) for its acquisition of UUVs applied to mine countermeasures (MCM) missions. Since 2002, APL has served as the independent test and evaluation agent for the Mk 18 UUV family of systems. The fielding of key components of the Mk 18 UUV family of systems was accelerated as part of an Office of the Secretary of Defense “Fast- Lane” program to meet an operational need in theater. As a result, Commander Fifth Fleet now has an improved operational MCM capability, including advanced sensors. OVERVIEW In December 2011, the Office of the Secretary of the UOES period was to develop mine countermeasures Defense approved a Fast-Lane initiative to provide (MCM) concepts of operations (CONOPS) for inte- Mk 18 Mod 2 Kingfish unmanned underwater vehicle gration with other MCM platforms in theater and to (UUV) systems and associated sensors and upgrades receive operator feedback that could be used to improve to Commander Fifth Fleet (C5F) on an accelerated the design. A second wave of Mk 18 Mod 2 UUVs basis. Seven months later, in July 2012, wave 1 of the arrived in theater in February 2013. -

Navy Shipboard Lasers for Surface, Air, and Missile Defense: Background and Issues for Congress
Navy Shipboard Lasers for Surface, Air, and Missile Defense: Background and Issues for Congress Ronald O'Rourke Specialist in Naval Affairs June 12, 2015 Congressional Research Service 7-5700 www.crs.gov R41526 Navy Shipboard Lasers for Surface, Air, and Missile Defense Summary Department of Defense (DOD) development work on high-energy military lasers, which has been underway for decades, has reached the point where lasers capable of countering certain surface and air targets at ranges of about a mile could be made ready for installation on Navy surface ships over the next few years. More powerful shipboard lasers, which could become ready for installation in subsequent years, could provide Navy surface ships with an ability to counter a wider range of surface and air targets at ranges of up to about 10 miles. The Navy and DOD have conducted development work on three principal types of lasers for potential use on Navy surface ships—fiber solid state lasers (SSLs), slab SSLs, and free electron lasers (FELs). One fiber SSL prototype demonstrator developed by the Navy is the Laser Weapon System (LaWS). The Navy in August 2014 installed a LaWS system on the USS Ponce, a ship operating in the Persian Gulf as an interim Afloat Forward Staging Base (AFSB[I]), to conduct continued evaluation of shipboard lasers in an operational setting. The Navy reportedly anticipates moving to a shipboard laser program of record in “the FY2018 time frame” and achieving an initial operational capability (IOC) with a shipboard laser in FY2020 or FY2021. Although the Navy is developing laser technologies and prototypes of potential shipboard lasers, and has a generalized vision for shipboard lasers, the Navy currently does not yet have a program of record for procuring a production version of a shipboard laser. -
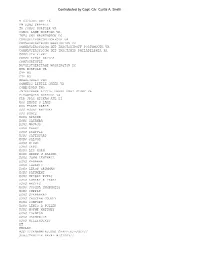
Final Message from USNS Grapple
Contrubuted by Capt. Civ. Curtis A. Smith R 032030Z OCT 16 FM USNS GRAPPLE TO COMSC NORFOLK VA COMSC LANT NORFOLK VA INFO CNO WASHINGTON DC COMUSFLTFORCOM NORFOLK VA COMNAVSEASYSCOM WASHINGTON DC COMNAVSEASYSCOM DET INACTSHIPOFF PORTSMOUTH VA COMNAVSEASYSCOM DET INACTSHIP PHILADELPHIA PA COMSIXTH FLEET COMSC EURAF NAPLES COMFOURTHFLT NAVHISTHERITAGE WASHINGTON DC NVR NORFOLK VA CTF 80 CTF 83 MOBDIVSALU TWO COMNECC LITTLE CREEK VA COMEODGRU TWO JNTEXPBASE LITTLE CREEK FORT STORY VA FLEAWEACEN NORFOLK VA CDR JPAC HICKAM AFB HI USS EMORY S LAND USS FRANK CABLE USS MOUNT WHITNEY USS PONCE USNS APACHE USNS CATAWBA USNS NAVAJO USNS GRASP USNS GRAPPLE USNS SAFEGUARD USNS SALVOR USNS SIOUX USNS ZEUS USNS BIG HORN USNS HENRY J KAISER USNS JOHN LENTHALL USNS KANAWHA USNS LARAMIE USNS LEROY GRUMMAN USNS PATUXENT USNS MEDGAR EVERS USNS ROBERT E PEARY USNS ARCTIC USNS JOSHUA HUMPHREYS USNS SUPPLY USNS SPEARHEAD USNS CHOCTAW COUNTY USNS COMFORT USNS LEWIS B PULLER USNS MOUNT WHITNEY USNS TRENTON USNS BRUNSWICK USNS MILLINOCKET BT UNCLAS MSGID/GENADMIN/USNS GRAPPLE/-/OCT// SUBJ/GRAPPLE NAVAL HISTORY// REF/A/RMG/CNO/261701ZJUL16// AMPN/NAVADMIN DIRECTING INACTIVATION STATUS AND NAVAL HISTORY MESSAGE// 1. USS GRAPPLE (ARS-53) WAS THE FINAL SAFEGUARD CLASS RESCUE AND SALVAGE SHIPS TO BE BUILT AT Peterson Builders, Sturgeon Bay, WI. It WAS LAUNCHED ON 8 December 1984. GRAPPLE IS THE SECOND SHIP IN THE NAVY TO BEAR THIS NAME. TRANSFERRED TO MSC IN 2013, GRAPPLE (T-ARS 53) SUBSEQUENTLY UNDERWENT A SHIPYARD PERIOD FOR CONVERSION PERIOD FOR OPERATION BY MSC CIVILIAN MARINERS. 2. SOME HIGHLIGHTS FROM HER SERVICE: A.) 1987 -USS GRAPPLE TOWED OCEAN MINESWEEPERS USS INFLICT, FEARLESS AND ILLUSIVE TO THE PERSIAN GULF TO SUPPORT US NAVY ESCORT OPERATIONS IN OPERATION EARNEST WILL.