362856-Sample.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Publisher Preview
DON’T REST YOUR HEADA Game of Insomnia in the Mad City by Fred Hicks Concept, Writing, Editing, & Typesetting Fred Hicks Art Fred Hicks, www.istockphoto.com, Photoshop Valued Input Christine Hicks, Rob Donoghue, Leonard Balsera, Mike Holmes, Matthew Gandy Playtesting Ashwath Ganesan, Cori May, Morgan Collins, Jim DelRosso, Judd Karlman, Jeff Lower, Kolja Loeblich, Darren Hill, Ian Dixon, Andrew Guffick Copyright Copyright © 2006, Fred Hicks and Evil Hat Productions, LLC All Rights Reserved DON’T REST YOUR HEAD The.Five.Questions.In.Play.............38 Contents Scene Framing ....................................38 Introduction.....................................2 Opening Scene ...................................39 What.This.Is......................................3 Trajectory ............................................39 Flashback ............................................40 What.You.Need................................3 First Contact ......................................41 Running.on.Fumes............................5 Revelation ...........................................42 Creating.Characters........................10 Resolution ...........................................43 Answer Questions .............................10 The.Mad.City..................................45 What’s Been Keeping You Awake? ..10 Getting There .....................................45 What Just Happened to You? ..........11 The City Slumbering .........................46 What’s on the Surface? ....................11 The Locals ...........................................46 -

Fate-Core-Electronic.Pdf
CHARACTERS LIVE AT THE EHP0001 CORE OF FATE A High Priestess of the barbarian hordes, an undead Wild West gunslinger, and a SYSTEM • CORE FATE Second Lieutenant of the Intergalactic Security Forces are about as di erent as they come, but they’ve got one thing in common: they need a strong engine to drive their stories. Fate Core is that engine. Fate Core is the latest evolution of the award-winning Fate roleplaying game system from Evil Hat Productions. We’ve streamlined and clarifi ed the rules while maintaining the system’s trademark fl exibility. Name your game; Fate Core can make it happen. Inside, you’ll discover: ➤ Easy-to-follow rules for character and world creation. ➤ Rock-solid storytelling advice for players and GMs to produce the best play experience. ➤ Clearly-defi ned systems to guide players both new and old. ➤ New and improved approaches to character actions, aspects, compels… and more! TELL YOUR TALE. ROLL THE DICE. EMBRACE YOUR FATE! LEONARD BRIAN JEREMY RYAN MIKE BALSERA ENGARD KELLER MACKLIN OLSON EHP0001 • ISBN 978-1-61317-029-8 • $25.00 US www.evilhat.com • @EvilHatO cial facebook.com/EvilHatProductions CHARACTERS LIVE AT THE EHP0001 CORE OF FATE A High Priestess of the barbarian hordes, an undead Wild West gunslinger, and a SYSTEM • CORE FATE Second Lieutenant of the Intergalactic Security Forces are about as di erent as they come, but they’ve got one thing in common: they need a strong engine to drive their stories. Fate Core is that engine. Fate Core is the latest evolution of the award-winning Fate roleplaying game system from Evil Hat Productions. -

Space Combat Demo
Welcome to Diaspora – Diaspora is a self-contained role-playing game, building on FATE (and particularly Spirit of the Century). It’s a game about the future, with humanity scattered through the stars living in clusters of six to ten systems, making do in a hostile universe. FTL travel is challenging, and reaction drives push large ships between planets, draining reaction mass, and avoiding dangers along the way. Diaspora is about stories, and is designed as a toolkit to facilitate telling hard(ish) SF stories at your game table. You build the setting of a cluster of systems, and then you inhabit it with your characters. It comes with a series of minigames – none of which need to be used, but which provide mechani- cal means to determine outcomes to stories that are in the process of being told. One chapter describes personal combat, and has a gritty feel, because shooting things with a shotgun in a spacesuit can be fun. Another makes social combat into a tactical game – so that players make strategic decisions about how they behave at a cocktail party, or when being tortured in other ways. A third minigame allows platoon combat, because sometimes a story needs a good hovertank battle. Finally, there is space combat, which we have included here as a sample chapter. Space Combat in Diaspora is abstracted: a one-dimensional map tracks rival vectors of a few fragile ships blazing away at each other. It’s also lethal, as it should be, and military and technically superior ships have an easier time. -

CORE of FATE a High Priestess of the Barbarian Hordes
CHARACTERS LIVE AT THE EHP0001 CORE OF FATE A High Priestess of the barbarian hordes, an undead Wild West gunslinger, and a SYSTEM • CORE FATE Second Lieutenant of the Intergalactic Security Forces are about as di erent as they come, but they’ve got one thing in common: they need a strong engine to drive their stories. Fate Core is that engine. Fate Core is the latest evolution of the award-winning Fate roleplaying game system from Evil Hat Productions. We’ve streamlined and clarifi ed the rules while maintaining the system’s trademark fl exibility. Name your game; Fate Core can make it happen. Inside, you’ll discover: ➤ Easy-to-follow rules for character and world creation. ➤ Rock-solid storytelling advice for players and GMs to produce the best play experience. ➤ Clearly-defi ned systems to guide players both new and old. ➤ New and improved approaches to character actions, aspects, compels… and more! TELL YOUR TALE. ROLL THE DICE. EMBRACESample YOUR FATE! file LEONARD BRIAN JEREMY RYAN MIKE BALSERA ENGARD KELLER MACKLIN OLSON EHP0001 • ISBN 978-1-61317-029-8 • $25.00 US www.evilhat.com • @EvilHatO cial facebook.com/EvilHatProductions CORE SYSTEM LEONARD BALSERA LEAD SYSTEM DEVELOPMENT BRIAN ENGARD AssISTANT DEVELOPMENT MIKE OLSON AssISTANT DEVELOPMENT RYAN MACKLIN AssISTANT DEVELopment • EDITING JEREMY KELLER Editing • LaYout • INTERIOR GRAPHIC DESIGN FRED HICKS ART DIRection • COVER DESign • PRINT PRODUCTION KURT KOMODA COVER ARt • INTERIOR ART SEAN NITTNER PROJECT MANAGEMENT CHRIS HANRAHAN BRAND MARKETING FATE WAS ORIGINALLY CREATED BY SampleROB DONOGHUE AND FRED H ICKSfile An Evil Hat Productions Publication www.evilhat.com • [email protected] @EvilHatOfficial on Twitter facebook.com/EvilHatProductions Fate Core System Copyright © 2013 Evil Hat Productions, LLC. -

The Platinum Appendix
SHANNON APPELCLINE SHANNON A HISTORY OF THE ROLEPLAYING GAME INDUSTRY THE PLATINUM APPENDIX SHANNON APPELCLINE This supplement to the Designers & Dragons book series was made possible by the incredible support given to us by the backers of the Designers & Dragons Kickstarter campaign. To all our backers, a big thank you from Evil Hat! _Journeyman_ Antoine Pempie Carlos Curt Meyer Donny Van Zandt Gareth Ryder-Han- James Terry John Fiala Keith Zientek malifer Michael Rees Patrick Holloway Robert Andersson Selesias TiresiasBC ^JJ^ Anton Skovorodin Carlos de la Cruz Curtis D Carbonell Dorian rahan James Trimble John Forinash Kelly Brown Manfred Gabriel Michael Robins Patrick Martin Frosz Robert Biddle Selganor Yoster Todd 2002simon01 Antonio Miguel Morales CURTIS RICKER Doug Atkinson Garrett Rooney James Turnbull John GT Kelroy Was Here Manticore2050 Michael Ruff Nielsen Robert Biskin seraphim_72 Todd Agthe 2Die10 Games Martorell Ferriol Carlos Gustavo D. Cardillo Doug Keester Garry Jenkins James Winfield John H. Ken Manu Marron Michael Ryder Patrick McCann Robert Challenger Serge Beaumont Todd Blake 64 Oz. Games Aoren Flores Ríos D. Christopher Doug Kern Gary Buckland James Wood John Hartwell ken Bronson Manuel Pinta Michael Sauer Patrick Menard Robert Conley Sérgio Alves Todd Bogenrief 6mmWar Apocryphal Lore Carlos Ovalle Dawson Dougal Scott Gary Gin Jamie John Heerens Ken Bullock Guerrero Michael Scholl Patrick Mueller-Best Robert Daines Sergio Silvio Todd Cash 7th Dimension Games Aram Glick Carlos Rincon D. Daniel Wagner Douglas Andrew Gary Kacmarcik Jamie MacLaren John Hergenroeder Ken Ditto Manuel Siebert Michael Sean Manley Patrick Murphy Robert Dickerson Herrera Gea Todd Dyck 9thLevel Aram Zucker-Scharff caroline D.J. -

Leonard Balsera Brian Engard Jeremy Keller Ryan
LEONARD BRIAN JEREMY RYAN MIKE BALSERA ENGARD KELLER MACKLIN OLSON CHARACTERS LIVE AT THE CORE OF FATE A High Priestess of the barbarian hordes, an undead Wild West gunslinger, and a Second Lieutenant of the Intergalactic Security Forces are about as dif erent as they come, but they’ve got one thing in common: they need a strong engine to drive their stories. Fate Core is that engine. Fate Core is the latest evolution of the award-winning Fate roleplaying game system from Evil Hat Productions. We’ve streamlined and clarifi ed the rules while maintaining the system’s trademark fl exibility. Name your game; Fate Core can make it happen. Inside, you’ll discover: Easy-to-follow rules for character and world creation. Rock-solid storytelling advice for players and GMs to produce the best play experience. Clearly-defi ned systems to guide players both new and old. New and improved approaches to character actions, aspects, compels… and more! TELL YOUR TALE. ROLL THE DICE. EMBRACE YOUR FATE! EHP0001 • ISBN 978-1-61317-029-8 • $25.00 US www.evilhat.com • @EvilHatOf cial facebook.com/EvilHatProductions CORE SYSTEM LEONARD BALSERA LEAD SYSTEM DEVELOPMENT BRIAN ENGARD ASSISTANT DEVELOPMENT MIKE OLSON ASSISTANT DEVELOPMENT RYAN MACKLIN ASSISTANT DEVELOPMENT • EDITING JEREMY KELLER EDITING • LAYOUT • INTERIOR GRAPHIC DESIGN FRED HICKS ART DIRECTION • COVER DESIGN • PRINT PRODUCTION KURT KOMODA COVER ART • INTERIOR ART SEAN NITTNER PROJECT MANAGEMENT CHRIS HANRAHAN BRAND MARKETING FATE WAS ORIGINALLY CREATED BY ROB DONOGHUE AND FRED HICKS An Evil Hat Productions Publication www.evilhat.com • [email protected] @EvilHatOfcial on Twitter facebook.com/EvilHatProductions Fate Core System Copyright © 2013 Evil Hat Productions, LLC. -

Mindjammer — the Roleplaying Game Published by Mindjammer Press Ltd, Written and Developed by Sarah Newton 35 Altham Grove, Harlow, Essex, CM20 2PQ
Credits Mindjammer — The Roleplaying Game Published by Mindjammer Press Ltd, written and developed by Sarah Newton 35 Altham Grove, Harlow, Essex, CM20 2PQ Cover Art by Paul Bourne Distributed by Modiphius Entertainment Ltd, 35 Turneville Road, London, W14 9PS Layout and Graphic Design by Michal E. Cross Publicity and Promotion by Modiphius Entertainment. Interior Art by Earl Geier, Jason Juta, Fil Kearney, For publicity and promotion details contact Eric Lofgren, Marco Morte, Andreas Schroth, Ian Stead, [email protected]. Jeff Ward, Andy Wintrip Fate Core System by Leonard Balsera, Brian Engard, Graphic Design Elements by Josephe Vandel & Paul Bourne Jeremy Keller, Ryan Macklin, Mike Olson Commonality Space Schematic by Jason Juta Fate™ is a trademark of Evil Hat Productions, LLC. The Powered by Fate logo is © Evil Hat Productions, LLC and Planet and Starmap Sheets by Ian Stead is used with permission. Deckplans and Logos by Ian Stead The Fate Core font is © Evil Hat Productions, LLC and is used with permission. The Four Actions icons were designed by Additional Cartography by Sarah Newton Jeremy Keller. Edited by Sarah Newton Proofreading by T. R. Knight, Sarah Newton Mindjammer Working Group: Michal E. Cross, Sarah Newton would like to thank: All the Mindjammer Ben Monroe, Graham Spearing, Ian Stead, Tom Zunder fans, for their encouragement, support, and patience. You guys are awesome! Chris McWilliam, husband, co-pilot, Produced & Art Directed by Chris McWilliam and fellow adventurer in the Mindscape; Fred, Lenny, & Sarah Newton and Rob at Evil Hat, for creating Fate and releasing it to the community to let us make games like this; Michal Enquiries: [email protected] Cross, for his insight, patience, and endless creativity in making this book’s layout so gorgeous; Simon Rogers and Mindjammer Press Ltd is a private limited company, Ralf Schemmann at Profantasy, for letting us use their reg. -

By Phil Masters
The Small Folk A Wainscot Roleplaying Game by Phil Masters Sample file 1 The Open Gaming License, Version 1.0a The following text is the property of Wizards of the 2. The License: This License applies to any Open 11. Use of Contributor Credits: You may not market or Coast, Inc. and is Copyright 2000 Wizards of the Game Content that contains a notice indicating that the advertise the Open Game Content using the name of Coast, Inc (“Wizards”). All Rights Reserved. Open Game Content may only be Used under and in any Contributor unless You have written permission 1. Definitions: (a) “Contributors” means the copyright terms of this License. You must affix such a notice to from the Contributor to do so. and/or trademark owners who have contributed Open any Open Game Content that you Use. No terms may 12 Inability to Comply: If it is impossible for You to Game Content; (b) “Derivative Material” means be added to or subtracted from this License except as comply with any of the terms of this License with copyrighted material including derivative works and described by the License itself. No other terms or respect to some or all of the Open Game Content due to translations (including into other computer languages), conditions may be applied to any Open Game Content statute, judicial order, or governmental regulation then potation, modification, correction, addition, extension, distributed using this License. You may not Use any Open Game Material so affected. upgrade, improvement, compilation, abridgment or 3.Offer and Acceptance: By Using the Open Game 13 Termination: This License will terminate other form in which an existing work may be recast, Content You indicate Your acceptance of the terms of automatically if You fail to comply with all terms herein transformed or adapted; (c) “Distribute” means to this License. -
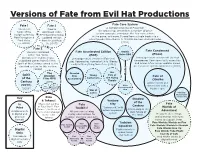
Fate Versions Guide
Versions of Fate from Evil Hat Productions Fate 1 Fate 2 Fate Core System A complete rewrite of Fate from House-rule Free to the ground up. Streamlines a number of prior hacks of the download, Indie- system concepts, introduces the four core actions Fudge system by RPG-Award-winning, of the game, and more. Turned from a single book into a Rob Donoghue & updated version robust product line thanks to 10,000+ backers via Kickstarter. Fred Hicks. from Fred & Rob. [2013] [c. 2000] [c. 2003] Fate 3 Versions contained Fate Accelerated Edition Atomic Fate Condensed within two “indie (FAE) Robo RPG (FCon) blockbuster,” commercially Low-page-count version of Fate that Low-page-count version of Fate that published games from Evil Hat. uses Approaches instead of Skills. Blends compresses Core down to its essentials Spirit of the Century served as the easily with anything from Core. [2013] and makes a few minor updates based standard system for this version. on 7 years of system experience. [2020] [2006] The Dresden Do: Spirit Dresden Files Young Fate of Modes Fate of of the Files RPG Accelerated Centurions the Flying Temple Cthulhu [2010] Century Action horror and The Kaiju (SOTC) Our time travel with a Paranet Incorporated [2006] World Papers Mythos spin. War of RPG Ashes Uprising: The Dystopian Dice Universe RPG Key Shadow & Tokens! Venture of the Check out our line City Fate In Fate Century Print of Fate Dice™, Fate “Superpunk” with Worlds of Points™, the Deck of Toolkits! Action-pulp in the Available both All-you-can-eat plug extensive powers Adventure! Fate, and Campaign system dark future of in digital and Coins’ Fate & play rules options for the 1980s Ready-made settings physical Tokens! making Fate Core your own. -

Assorted Sheets for Icons
Assorted sheets Sample file 1. Denitions: 9. Updating the License: Wizards or its designated Agents may publish (a) "Contributors" means the copyright and/or trademark owners who have updated versions of this License. You may use any authorized version contributed Open Game Content; of this License to copy, modify and distribute any Open Game Content (b) "Derivative Material" means copyrighted material including originally distributed under any version of this License. derivative works and translations (including into other computer 10. Copy of this License: You MUST include a copy of this License with languages), potation, modication, correction, addition, extension, every copy of the Open Game Content You Distribute. upgrade, improvement, compilation, abridgment or other form in 11. Use of Contributor Credits: You may not market or advertise the which an existing work may be recast, transformed or adapted; Open Game Content using the name of any Contributor unless You (c) "Distribute" means to reproduce, license, rent, lease, sell, broadcast, have written permission from the Contributor to do so. publicly display, transmit or otherwise distribute; 12. Inability to Comply: If it is impossible for You to comply with any of (d) "Open Game Content" means the game mechanic and includes the the terms of this License with respect to some or all of the Open Game methods, procedures, processes and routines to the extent such Content due to statute, judicial order, or governmental regulation then content does not embody the Product Identity and is an enhancement You may not Use any Open Game Material so aected. over the prior art and any additional content clearly identied as Open 13. -

The Hollow West a Role Playing Game of Fantastic Adventures in the Hollow Earth
D101 Games Presents for Your Entertainment. The Hollow West A Role Playing Game of Fantastic Adventures in The Hollow Earth. By Newt Newport. Using the Fortune System by Paul Mitchener. Editor: Paul Mitchener. Cover art: Jon Hodgeson. All internal art from public domain sources. Playtesters The Tandle Hill Posse: Mark Conry, Guy Milner, John Ruddy, Lynn Yin. The Furnace Posse: Paul Baldwalski, Remi Fayomi, Tom Lock, Malcolm McMahon, Andrew Sangar, Andrew Whiteoak. Contents A Players’ Guide to the Hollow West Chapter 1 About this Book 4 Chapter 2 The Hollow West 7 Chapter 3 Game Concepts 11 Chapter 4 Characters Sample file 13 Chapter 5 Extras 19 Chapter 6 Playing the Game 30 The Referee’s Guide to the Hollow Earth Chapter 7 Secrets of the Hollow Earth 40 Chapter 8 Factions 46 Chapter 9 People 51 Chapter 10 Monsters 68 Chapter 11 Thrilling Locations 76 Chapter 12 Hitting the Trail 86 Chapter 13 The Great Dinosaur Hunt of 1896 94 Chapter 14 The Great Secret at the Centre of the Hollow Earth 114 Index 116 Character Sheet 118 Other Fortune/Fate Games by D101 Games Hunters of Alexandria More information d101games.com Maximum Thanks to: Paul Mitchener for putting together the Fortune variant, letting me use it, and helping immeasurably with development of this game. The Tandle Hill Posse: John, Guy, Lynn and Mr C for exploring and discovering the Hollow West through play. Copyright Notice This work is based on the Fate Core System and Fate Accelerated Edition (found at http://www.faterpg.com/), products of Evil Hat Productions, LLC, developed, authored, and edited by Leonard Balsera, Brian Engard, Jeremy Keller, Ryan Macklin, Mike Olson, Clark Valentine, Amanda Valentine, Fred Hicks, and Rob Donoghue, and licensed for our use under the Creative Commons Attribution 3.0 Unported license (http://creativecommons.org/licenses/by/3.0/). -

170689-Sample.Pdf
An Evil Hat Productions Publication www.evilhat.com • [email protected] @EvilHatOfficial on Twitter facebook.com/EvilHatProductions In association with One Seven Design www.onesevendesign.com • [email protected] @john_harper on Twitter Blades in the Dark Copyright © 2017 John Harper. All rights reserved. First published in 2017 by Evil Hat Productions, LLC. 10125 Colesville Rd #318, Silver Spring MD 20901 Evil Hat Productions and the Evil Hat logo are trademarks owned by Evil Hat Productions, LLC. All rights reserved. Evil Hat product number: EHP0030 Digital Release, March 28, 2017. v8.2 Printed in the USA. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior express permission of the publisher. That said, if you’re doing it for personal use, go right ahead. For those working at a copy shop, this means the person standing at your counter can make copies of this thing. This is “express permission.” Carry on. This book was produced using Adobe Creative Suite. Typefaces: Minion Pro, Kirsty, Ugly Qua. Sample file CREDITS John Harper Game Design, Writing, Layout, Art, and Cartography Stras Acimovic Sean Nittner Consulting Designer Developmental Editor Additional Material by Stras Acimovic, Vandel J. Arden, Duamn Figueroa, Dylan Green, Sean Nittner, and Andrew Shields Fred Hicks Director of Operations for Evil Hat Sean Nittner Director of Projects for Evil Hat Carrie Harris Marketing Manager for Evil Hat Chris Hanrahan Business Development for Evil Hat Karen Twelves Copy Editor Rita Tatum Indexer Visit the website for character sheets and other game materials Samplewww.bladesinthedark.com file THANKS Adam Koebel, Adam Minnie, Alex Crossley, Andrew Shields, Anthony Turner, Asteyni, Blake Hutchins, Brandon Amancio, Brandon Hilliard, Brendan Adkins, Chris Bennett, Clinton Dreisbach, Daniel Levine, Dave Turner, Duamn Figueroa, Ed Ouellette, Eric Levanduski, Fred Hicks, Greg Stolze, J.P.