Character Code Structure and Extension Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Microsoft Office Open XML Formats New File Formats for “Office 12”
The Microsoft Office Open XML Formats New File Formats for “Office 12” White Paper Published: June 2005 For the latest information, please see http://www.microsoft.com/office/wave12 Contents Introduction ...............................................................................................................................1 From .doc to .docx: a brief history of the Office file formats.................................................1 Benefits of the Microsoft Office Open XML Formats ................................................................2 Integration with Business Data .............................................................................................2 Openness and Transparency ...............................................................................................4 Robustness...........................................................................................................................7 Description of the Microsoft Office Open XML Format .............................................................9 Document Parts....................................................................................................................9 Microsoft Office Open XML Format specifications ...............................................................9 Compatibility with new file formats........................................................................................9 For more information ..............................................................................................................10 -

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -

MPEG-21 Overview
MPEG-21 Overview Xin Wang Dept. Computer Science, University of Southern California Workshop on New Multimedia Technologies and Applications, Xi’An, China October 31, 2009 Agenda ● What is MPEG-21 ● MPEG-21 Standards ● Benefits ● An Example Page 2 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang MPEG Standards ● MPEG develops standards for digital representation of audio and visual information ● So far ● MPEG-1: low resolution video/stereo audio ● E.g., Video CD (VCD) and Personal music use (MP3) ● MPEG-2: digital television/multichannel audio ● E.g., Digital recording (DVD) ● MPEG-4: generic video and audio coding ● E.g., MP4, AVC (H.24) ● MPEG-7 : visual, audio and multimedia descriptors MPEG-21: multimedia framework ● MPEG-A: multimedia application format ● MPEG-B, -C, -D: systems, video and audio standards ● MPEG-M: Multimedia Extensible Middleware ● ● MPEG-V: virtual worlds MPEG-U: UI ● (29116): Supplemental Media Technologies ● ● (Much) more to come … Page 3 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang What is MPEG-21? ● An open framework for multimedia delivery and consumption ● History: conceived in 1999, first few parts ready early 2002, most parts done by now, some amendment and profiling works ongoing ● Purpose: enable all-electronic creation, trade, delivery, and consumption of digital multimedia content ● Goals: ● “Transparent” usage ● Interoperable systems ● Provides normative methods for: ● Content identification and description Rights management and protection ● Adaptation of content ● Processing on and for the various elements of the content ● ● Evaluation methods for determining the appropriateness of possible persistent association of information ● etc. Page 4 Workshop on New Multimedia Technologies and Applications, Oct. -

IBM Db2 High Performance Unload for Z/OS User's Guide
5.1 IBM Db2 High Performance Unload for z/OS User's Guide IBM SC19-3777-03 Note: Before using this information and the product it supports, read the "Notices" topic at the end of this information. Subsequent editions of this PDF will not be delivered in IBM Publications Center. Always download the latest edition from the Db2 Tools Product Documentation page. This edition applies to Version 5 Release 1 of Db2 High Performance Unload for z/OS (product number 5655-AA1) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM® Corporation 1999, 2021; Copyright Infotel 1999, 2021. All Rights Reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. © Copyright International Business Machines Corporation . US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this information......................................................................................... vii Chapter 1. Db2 High Performance Unload overview................................................ 1 What does Db2 HPU do?..............................................................................................................................1 Db2 HPU benefits.........................................................................................................................................1 Db2 HPU process and components.............................................................................................................2 -

Quadtree Based JBIG Compression
Quadtree Based JBIG Compression B. Fowler R. Arps A. El Gamal D. Yang ISL, Stanford University, Stanford, CA 94305-4055 ffowler,arps,abbas,[email protected] Abstract A JBIG compliant, quadtree based, lossless image compression algorithm is describ ed. In terms of the numb er of arithmetic co ding op erations required to co de an image, this algorithm is signi cantly faster than previous JBIG algorithm variations. Based on this criterion, our algorithm achieves an average sp eed increase of more than 9 times with only a 5 decrease in compression when tested on the eight CCITT bi-level test images and compared against the basic non-progressive JBIG algorithm. The fastest JBIG variation that we know of, using \PRES" resolution reduction and progressive buildup, achieved an average sp eed increase of less than 6 times with a 7 decrease in compression, under the same conditions. 1 Intro duction In facsimile applications it is desirable to integrate a bilevel image sensor with loss- less compression on the same chip. Suchintegration would lower p ower consumption, improve reliability, and reduce system cost. To reap these b ene ts, however, the se- lection of the compression algorithm must takeinto consideration the implementation tradeo s intro duced byintegration. On the one hand, integration enhances the p os- sibility of parallelism which, if prop erly exploited, can sp eed up compression. On the other hand, the compression circuitry cannot b e to o complex b ecause of limitations on the available chip area. Moreover, most of the chip area on a bilevel image sensor must b e o ccupied by photo detectors, leaving only the edges for digital logic. -

OASIS CGM Open Webcgm V2.1
WebCGM Version 2.1 OASIS Standard 01 March 2010 Specification URIs: This Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1-index.html (AUTHORITATIVE) PDF: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1.zip Previous Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1-index.html (AUTHORITATIVE) PDF: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1.zip Latest Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1-index.html PDF: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1.zip Declared XML namespaces: http://www.cgmopen.org/schema/webcgm/ System Identifier: http://docs.oasis-open.org/webcgm/v2.1/webcgm21.dtd Technical Committee: OASIS CGM Open WebCGM TC Chair(s): Stuart Galt, The Boeing Company Editor(s): Benoit Bezaire, PTC Lofton Henderson, Individual Related Work: This specification updates: WebCGM 2.0 OASIS Standard (and W3C Recommendation) This specification, when completed, will be identical in technical content to: WebCGM 2.1 W3C Recommendation, available at http://www.w3.org/TR/webcgm21/. Abstract: Computer Graphics Metafile (CGM) is an ISO standard, defined by ISO/IEC 8632:1999, for the interchange of 2D vector and mixed vector/raster graphics. -

Regular Expressions in Jlex to Define a Token in Jlex, the User to Associates a Regular Expression with Commands Coded in Java
Regular Expressions in JLex To define a token in JLex, the user to associates a regular expression with commands coded in Java. When input characters that match a regular expression are read, the corresponding Java code is executed. As a user of JLex you don’t need to tell it how to match tokens; you need only say what you want done when a particular token is matched. Tokens like white space are deleted simply by having their associated command not return anything. Scanning continues until a command with a return in it is executed. The simplest form of regular expression is a single string that matches exactly itself. © CS 536 Spring 2005 109 For example, if {return new Token(sym.If);} If you wish, you can quote the string representing the reserved word ("if"), but since the string contains no delimiters or operators, quoting it is unnecessary. For a regular expression operator, like +, quoting is necessary: "+" {return new Token(sym.Plus);} © CS 536 Spring 2005 110 Character Classes Our specification of the reserved word if, as shown earlier, is incomplete. We don’t (yet) handle upper or mixed- case. To extend our definition, we’ll use a very useful feature of Lex and JLex— character classes. Characters often naturally fall into classes, with all characters in a class treated identically in a token definition. In our definition of identifiers all letters form a class since any of them can be used to form an identifier. Similarly, in a number, any of the ten digit characters can be used. © CS 536 Spring 2005 111 Character classes are delimited by [ and ]; individual characters are listed without any quotation or separators. -

AVR244 AVR UART As ANSI Terminal Interface
AVR244: AVR UART as ANSI Terminal Interface Features 8-bit • Make use of standard terminal software as user interface to your application. • Enables use of a PC keyboard as input and ascii graphic to display status and control Microcontroller information. • Drivers for ANSI/VT100 Terminal Control included. • Interactive menu interface included. Application Note Introduction This application note describes some basic routines to interface the AVR to a terminal window using the UART (hardware or software). The routines use a subset of the ANSI Color Standard to position the cursor and choose text modes and colors. Rou- tines for simple menu handling are also implemented. The routines can be used to implement a human interface through an ordinary termi- nal window, using interactive menus and selections. This is particularly useful for debugging and diagnostics purposes. The routines can be used as a basic interface for implementing more complex terminal user interfaces. To better understand the code, an introduction to ‘escape sequences’ is given below. Escape Sequences The special terminal functions mentioned (e.g. text modes and colors) are selected using ANSI escape sequences. The AVR sends these sequences to the connected terminal, which in turn executes the associated commands. The escape sequences are strings of bytes starting with an escape character (ASCII code 27) followed by a left bracket ('['). The rest of the string decides the specific operation. For instance, the command '1m' selects bold text, and the full escape sequence thus becomes 'ESC[1m'. There must be no spaces between the characters, and the com- mands are case sensitive. The various operations used in this application note are described below. -
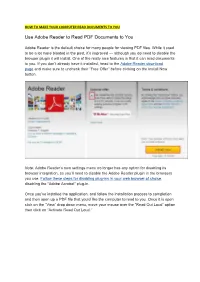
Use Adobe Reader to Read PDF Documents to You
HOW TO MAKE YOUR COMPUTER READ DOCUMENTS TO YOU Use Adobe Reader to Read PDF Documents to You Adobe Reader is the default choice for many people for viewing PDF files. While it used to be a lot more bloated in the past, it’s improved — although you do need to disable the browser plugin it will install. One of the really nice features is that it can read documents to you. If you don’t already have it installed, head to the Adobe Reader download page and make sure to uncheck their “Free Offer” before clicking on the Install Now button. Note: Adobe Reader’s own settings menu no longer has any option for disabling its browser integration, so you’ll need to disable the Adobe Reader plugin in the browsers you use. Follow these steps for disabling plug-ins in your web browser of choice, disabling the “Adobe Acrobat” plug-in. Once you’ve installed the application, and follow the installation process to completion and then open up a PDF file that you’d like the computer to read to you. Once it is open click on the “View” drop down menu, move your mouse over the “Read Out Loud” option then click on “Activate Read Out Loud.” Alternatively, you can click “Ctrl,” “Shift,” and “Y” (Ctrl+Shift+Y) on your keyboard to activate the feature. Once the feature is activated, you can click on a single paragraph to make windows read it back to you. Another option would be to navigate to the “View” menu, then “Read Out Loud” and select an option that fits your needs as shown in the Image below. -

Iso/Iec 14496-14
INTERNATIONAL ISO/IEC STANDARD 14496-14 First edition 2003-11-15 Information technology — Coding of audio-visual objects — Part 14: MP4 file format Technologies de l'information — Codage des objets audiovisuels — Partie 14: Format de fichier MP4 Reference number ISO/IEC 14496-14:2003(E) Licensed to WIMOBILIS DIGITAL TECHNOLOGIES/MARCOS MANENTE ISO Store order #:850777/Downloaded:2007-09-27 Single user licence only, copying and networking prohibited © ISO/IEC 2003 ISO/IEC 14496-14:2003(E) PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat accepts no liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies. In the unlikely event that a problem relating to it is found, please inform the Central Secretariat at the address given below. © ISO/IEC 2003 All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm, without permission in writing from either ISO at the address below or ISO's member body in the country of the requester. -
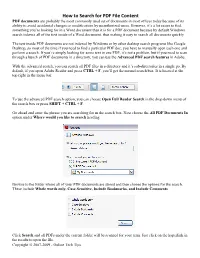
How to Search for PDF File Content
How to Search for PDF File Content PDF documents are probably the most commonly used set of documents in most offices today because of its ability to avoid accidental changes or modifications by unauthorized users. However, it’s a lot easier to find something you’re looking for in a Word document than it is for a PDF document because by default Windows search indexes all of the text inside of a Word document, thus making it easy to search all documents quickly. The text inside PDF documents are not indexed by Windows or by other desktop search programs like Google Desktop, so most of the time if you need to find a particular PDF doc, you have to manually open each one and perform a search. If you’re simply looking for some text in one PDF, it’s not a problem, but if you need to scan through a bunch of PDF documents in a directory, you can use the Advanced PDF search features in Adobe. With the advanced search, you can search all PDF files in a directory and it’s sub-directories in a single go. By default, if you open Adobe Reader and press CTRL + F, you’ll get the normal search box. It is located at the top right in the menu bar. To use the advanced PDF search option, you can choose Open Full Reader Search in the drop down menu of the search box or press SHIFT + CTRL + F. Go ahead and enter the phrase you are searching for in the search box. -

ANSI® Programmer's Reference Manual Line Matrix Series Printers
ANSI® Programmer’s Reference Manual Line Matrix Series Printers Printronix, LLC makes no representations or warranties of any kind regarding this material, including, but not limited to, implied warranties of merchantability and fitness for a particular purpose. Printronix, LLC shall not be held responsible for errors contained herein or any omissions from this material or for any damages, whether direct, indirect, incidental or consequential, in connection with the furnishing, distribution, performance or use of this material. The information in this manual is subject to change without notice. This document contains proprietary information protected by copyright. No part of this document may be reproduced, copied, translated or incorporated in any other material in any form or by any means, whether manual, graphic, electronic, mechanical or otherwise, without the prior written consent of Printronix, LLC Copyright © 1998, 2012 Printronix, LLC All rights reserved. Trademark Acknowledgements ANSI is a registered trademark of American National Standards Institute, Inc. Centronics is a registered trademark of Genicom Corporation. Dataproducts is a registered trademark of Dataproducts Corporation. Epson is a registered trademark of Seiko Epson Corporation. IBM and Proprinter are registered trademarks and PC-DOS is a trademark of International Business Machines Corporation. MS-DOS is a registered trademark of Microsoft Corporation. Printronix, IGP, PGL, LinePrinter Plus, and PSA are registered trademarks of Printronix, LLC. QMS is a registered