Code Extension Techniques for Use with the 7-Bit Coded Character Set of American National Standard Code for Information Interchange
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Db2 High Performance Unload for Z/OS User's Guide
5.1 IBM Db2 High Performance Unload for z/OS User's Guide IBM SC19-3777-03 Note: Before using this information and the product it supports, read the "Notices" topic at the end of this information. Subsequent editions of this PDF will not be delivered in IBM Publications Center. Always download the latest edition from the Db2 Tools Product Documentation page. This edition applies to Version 5 Release 1 of Db2 High Performance Unload for z/OS (product number 5655-AA1) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM® Corporation 1999, 2021; Copyright Infotel 1999, 2021. All Rights Reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. © Copyright International Business Machines Corporation . US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this information......................................................................................... vii Chapter 1. Db2 High Performance Unload overview................................................ 1 What does Db2 HPU do?..............................................................................................................................1 Db2 HPU benefits.........................................................................................................................................1 Db2 HPU process and components.............................................................................................................2 -

Using ANSI Color Codes General Configuration of the Shell
LinuxFocus article number 335 http://linuxfocus.org Colorful Shells -- Using ANSI Color Codes by Nico Golde <nico/at/ngolde.de> About the author: At present Nico is still a Abstract: student. Since a few years he keeps very busy with In an ANSI compatible terminal (like xterm, rxvt, konsole ...) text may Linux, he also takes part in be shown in colors different from black/white. This article will a number of Open Source demonstrate text in bold or in color. Projects. _________________ _________________ _________________ Translated to English by: Jürgen Pohl <sept.sapins(at)verizon.net> General In real life every Linux user gets to face the Bash. At first glance that looks very boring, but there are many possibilities to give one’s shell the personal touch. Colored enhancement of the shell prompt make the shell unique as well as better legible. In my description I will refer to the Bash shell. The escape sequences may differ between terminals, for this text I am using an ANSI terminal. Configuration of the Shell Setting of shell colors happens in the personal configuration file of the bash ~/.bashrc or in the global configuration file /etc/bashrc. The appearance of the prompt is being set with the PS1 variable in bashrc. Generally, the entry should look like this: ~/.bashrc: PS1="\s-\v\$ " \s stands for the name of the shell and -\v for its version. At the end of the prompt we are placing a $. Since this gets a bit boring, the following entry - which is default in most Linux distributions - may be used: ~/.bashrc: PS1="\u@\h \w \$ " This stands for user@ current_directory $, which is the normal shell prompt most Linux users are familiar with. -

CS 106 Introduction to Computer Science I
CS 106 Introduction to Computer Science I 07 / 06 / 2021 Instructor: Michael Eckmann Today’s Topics • Introduction • Review the syllabus – including the policies on academic dishonesty and improper collaboration • Introductory comments on programming languages • An example of a simple Python program • Printing Michael Eckmann - Skidmore College - CS 106 - Summer 2021 Who is your instructor? • I'm Mike Eckmann, an Associate Professor in the Computer Science Dept., Skidmore College. I have been at Skidmore since 2004. Before coming to Skidmore I was at Lehigh University in PA. • I studied Mathematics and Computer Engineering and Computer Science all at Lehigh University. • I was employed as a programmer (systems analyst) for eight years. Michael Eckmann - Skidmore College - CS 106 - Summer 2021 1st Homework • Read the syllabus and review the improper collaboration policy (both will be available on our course webpage.) • Read chapter 1 of text. • Will send course webpage and a questionnaire via email later this class. Michael Eckmann - Skidmore College - CS 106 - Summer 2021 Syllabus • Office hours • Collaboration policy – By appointment • Grading scheme • Text book • Workload • Assignments • Student preparation – Programs & HW before class Note: The most up-to-date syllabus will be found on the course web page. Michael Eckmann - Skidmore College - CS 106 - Summer 2021 This semester we will ... • Be introduced to computer science. • Learn programming (in Python)! • Solve problems and learn to think like programmers. • Hopefully have a fun learning experience. Michael Eckmann - Skidmore College - CS 106 - Summer 2021 Computer Science is ... • more than computer programming. Michael Eckmann - Skidmore College - CS 106 - Summer 2021 Programming Languages • Machine • Assembly • High-level – in no particular order – Pascal, C, C++, Basic, Fortran, Java, Python and many, many more .. -

Regular Expressions in Jlex to Define a Token in Jlex, the User to Associates a Regular Expression with Commands Coded in Java
Regular Expressions in JLex To define a token in JLex, the user to associates a regular expression with commands coded in Java. When input characters that match a regular expression are read, the corresponding Java code is executed. As a user of JLex you don’t need to tell it how to match tokens; you need only say what you want done when a particular token is matched. Tokens like white space are deleted simply by having their associated command not return anything. Scanning continues until a command with a return in it is executed. The simplest form of regular expression is a single string that matches exactly itself. © CS 536 Spring 2005 109 For example, if {return new Token(sym.If);} If you wish, you can quote the string representing the reserved word ("if"), but since the string contains no delimiters or operators, quoting it is unnecessary. For a regular expression operator, like +, quoting is necessary: "+" {return new Token(sym.Plus);} © CS 536 Spring 2005 110 Character Classes Our specification of the reserved word if, as shown earlier, is incomplete. We don’t (yet) handle upper or mixed- case. To extend our definition, we’ll use a very useful feature of Lex and JLex— character classes. Characters often naturally fall into classes, with all characters in a class treated identically in a token definition. In our definition of identifiers all letters form a class since any of them can be used to form an identifier. Similarly, in a number, any of the ten digit characters can be used. © CS 536 Spring 2005 111 Character classes are delimited by [ and ]; individual characters are listed without any quotation or separators. -

AVR244 AVR UART As ANSI Terminal Interface
AVR244: AVR UART as ANSI Terminal Interface Features 8-bit • Make use of standard terminal software as user interface to your application. • Enables use of a PC keyboard as input and ascii graphic to display status and control Microcontroller information. • Drivers for ANSI/VT100 Terminal Control included. • Interactive menu interface included. Application Note Introduction This application note describes some basic routines to interface the AVR to a terminal window using the UART (hardware or software). The routines use a subset of the ANSI Color Standard to position the cursor and choose text modes and colors. Rou- tines for simple menu handling are also implemented. The routines can be used to implement a human interface through an ordinary termi- nal window, using interactive menus and selections. This is particularly useful for debugging and diagnostics purposes. The routines can be used as a basic interface for implementing more complex terminal user interfaces. To better understand the code, an introduction to ‘escape sequences’ is given below. Escape Sequences The special terminal functions mentioned (e.g. text modes and colors) are selected using ANSI escape sequences. The AVR sends these sequences to the connected terminal, which in turn executes the associated commands. The escape sequences are strings of bytes starting with an escape character (ASCII code 27) followed by a left bracket ('['). The rest of the string decides the specific operation. For instance, the command '1m' selects bold text, and the full escape sequence thus becomes 'ESC[1m'. There must be no spaces between the characters, and the com- mands are case sensitive. The various operations used in this application note are described below. -

Introduction to C++
GVNS I PUC Computer Science Notes Chapter 7 – INTRODUCTION TO C++ UNIT C – Chapter 7 – INTRODUCTION TO C++ BLUEPRINT 1 MARK 2 MARK 3 MARK 5 MARK TOTAL 1 0 1 1 9 ONE Mark Questions and Answers 1. Who developed “ C++ “ programming language and where? Bjarne Stroustrup designed C++ programming language at AT & T Bell Labs. 2. C++ is a subset of C. True or false? True 3. How can comments be included in a program? Comments can be included in C++ program by writing the comment between the symbols /* and */ or by starting the comment with double front slash ( // ). 4. Define token. A token is the smallest individual unit in a program. 5. Mention two tokens. Two tokens are keyword, identifier. (Note: refer to your textbook for more tokens) 6. What are keywords? Keywords are predefined word with some meanings. 7. Mention any four keywords in C++. The four keywords are int, if, do, for. (Note: refer to your textbook for more keywords) 8. What is a constant? Constants are quantities whose value cannot be changed during the execution of a program. 9. What are escape sequences? Escape sequences are characters that as special meaning and it starts with back slash ( \ ). 10. Mention any two escape sequences. Two escape sequences are \n and \t (Note: refer to your textbook for more escape sequences) 11. What is a string? String is a sequence of characters enclosed in double quotes. 12. What are punctuators? Punctuators are symbols used in a C++ program as seperators. 13. What is an operand? The data items on which operators act are called operands. -

VSI Openvms C Language Reference Manual
VSI OpenVMS C Language Reference Manual Document Number: DO-VIBHAA-008 Publication Date: May 2020 This document is the language reference manual for the VSI C language. Revision Update Information: This is a new manual. Operating System and Version: VSI OpenVMS I64 Version 8.4-1H1 VSI OpenVMS Alpha Version 8.4-2L1 Software Version: VSI C Version 7.4-1 for OpenVMS VMS Software, Inc., (VSI) Bolton, Massachusetts, USA C Language Reference Manual Copyright © 2020 VMS Software, Inc. (VSI), Bolton, Massachusetts, USA Legal Notice Confidential computer software. Valid license from VSI required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. The information contained herein is subject to change without notice. The only warranties for VSI products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. VSI shall not be liable for technical or editorial errors or omissions contained herein. HPE, HPE Integrity, HPE Alpha, and HPE Proliant are trademarks or registered trademarks of Hewlett Packard Enterprise. Intel, Itanium and IA64 are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. Java, the coffee cup logo, and all Java based marks are trademarks or registered trademarks of Oracle Corporation in the United States or other countries. Kerberos is a trademark of the Massachusetts Institute of Technology. -

ANSI® Programmer's Reference Manual Line Matrix Series Printers
ANSI® Programmer’s Reference Manual Line Matrix Series Printers Printronix, LLC makes no representations or warranties of any kind regarding this material, including, but not limited to, implied warranties of merchantability and fitness for a particular purpose. Printronix, LLC shall not be held responsible for errors contained herein or any omissions from this material or for any damages, whether direct, indirect, incidental or consequential, in connection with the furnishing, distribution, performance or use of this material. The information in this manual is subject to change without notice. This document contains proprietary information protected by copyright. No part of this document may be reproduced, copied, translated or incorporated in any other material in any form or by any means, whether manual, graphic, electronic, mechanical or otherwise, without the prior written consent of Printronix, LLC Copyright © 1998, 2012 Printronix, LLC All rights reserved. Trademark Acknowledgements ANSI is a registered trademark of American National Standards Institute, Inc. Centronics is a registered trademark of Genicom Corporation. Dataproducts is a registered trademark of Dataproducts Corporation. Epson is a registered trademark of Seiko Epson Corporation. IBM and Proprinter are registered trademarks and PC-DOS is a trademark of International Business Machines Corporation. MS-DOS is a registered trademark of Microsoft Corporation. Printronix, IGP, PGL, LinePrinter Plus, and PSA are registered trademarks of Printronix, LLC. QMS is a registered -

Data Types in C
Princeton University Computer Science 217: Introduction to Programming Systems Data Types in C 1 Goals of C Designers wanted C to: But also: Support system programming Support application programming Be low-level Be portable Be easy for people to handle Be easy for computers to handle • Conflicting goals on multiple dimensions! • Result: different design decisions than Java 2 Primitive Data Types • integer data types • floating-point data types • pointer data types • no character data type (use small integer types instead) • no character string data type (use arrays of small ints instead) • no logical or boolean data types (use integers instead) For “under the hood” details, look back at the “number systems” lecture from last week 3 Integer Data Types Integer types of various sizes: signed char, short, int, long • char is 1 byte • Number of bits per byte is unspecified! (but in the 21st century, pretty safe to assume it’s 8) • Sizes of other integer types not fully specified but constrained: • int was intended to be “natural word size” • 2 ≤ sizeof(short) ≤ sizeof(int) ≤ sizeof(long) On ArmLab: • Natural word size: 8 bytes (“64-bit machine”) • char: 1 byte • short: 2 bytes • int: 4 bytes (compatibility with widespread 32-bit code) • long: 8 bytes What decisions did the designers of Java make? 4 Integer Literals • Decimal: 123 • Octal: 0173 = 123 • Hexadecimal: 0x7B = 123 • Use "L" suffix to indicate long literal • No suffix to indicate short literal; instead must use cast Examples • int: 123, 0173, 0x7B • long: 123L, 0173L, 0x7BL • short: -

Delimited Escape Sequences
Delimited escape sequences Document #: N2785 Date: 2021-07-28 Project: Programming Language C Audience: Application programmers Proposal category: New feature Reply-to: Corentin Jabot <[email protected]> Aaron Ballman <[email protected]> Abstract We propose an additional, clearly delimited syntax for octal, hexadecimal and universal character name escape sequences to clearly delimit the boundaries of the escape sequence. WG21 has shown an interest in adjusting this feature, and this proposal is intended to keep C and C++ in alignment. This feature is a pure extension to the language that should not impact existing code. Motivation universal-character-name escape sequences As their name does not indicate, universal-character-name escape sequences represent Uni- code scalar values, using either 4, or 8 hexadecimal digits, which is either 16 or 32 bits. However, the Unicode codespace is limited to 0-0x10FFFF, and all currently assigned code- points can be written with 5 or less hexadecimal digits (Supplementary Private Use Area-B non-withstanding). As such, the ~50% of codepoints that need 5 hexadecimal digits to be expressed are currently a bit awkward to write: \U0001F1F8. Octal and hexadecimal escape sequences have variable length \1, \01, \001 are all valid escape sequences. \17 is equivalent to "0x0F" while \18 is equivalent to "0x01" "8" While octal escape sequences accept 1 to 3 digits as arguments, hexadecimal sequences accept an arbitrary number of digits applying the maximal much principle. This is how the Microsoft documentation describes this problem: 1 Unlike octal escape constants, the number of hexadecimal digits in an escape sequence is unlimited. -
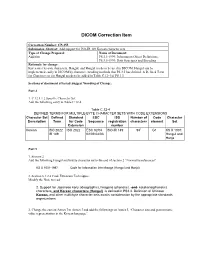
DICOM Correction Item
DICOM Correction Item Correction Number: CP-155 Submission Abstract: Add support for ISO-IR 149 Korean character sets Type of Change Proposal: Name of Document: Addition PS 3.3-1999: Information Object Definitions, PS 3.5-1999: Data Structures and Encoding Rationale for change: Korea uses its own characters, Hangul, and Hangul needs to be used in DICOM. Hangul can be implemented easily in DICOM by character encoding methods that PS 3.5 has defined. A Defined Term for Character set for Hangul needs to be added in Table C.12-4 of PS 3.3 Sections of document affected/ Suggest Wording of Change: Part 3 1. C.12.1.1.2 Specific Character Set Add the following entry to Table C.12-4. Table C.12-4 DEFINED TERMS FOR MULTIPLE-BYTE CHARACTER SETS WITH CODE EXTENSIONS Character Set Defined Standard ESC ISO Number of Code Character Description Term for Code Sequence registration characters element Set Extension number Korean ISO 2022 ISO 2022 ESC 02/04 ISO-IR 149 942 G1 KS X 1001: IR 149 02/09 04/03 Hangul and Hanja Part 5 1. Section 2 Add the following Hangul multi-byte character set to the end of section 2 “Normative references”: KS X 1001-1997 Code for Information Interchange (Hangul and Hanja) 2. Section 6.1.2.4 Code Extension Techniques Modify the Note to read: 2. Support for Japanese kanji (ideographic), hiragana (phonetic), and katakana(phonetic) characters, and Korean characters (Hangul) is defined in PS3.3. Definition of Chinese Korean, and other multi-byte character sets awaits consideration by the appropriate standards organizations. -

Java/Java Characters.Htm Copyright © Tutorialspoint.Com
JJAAVVAA -- CCHHAARRAACCTTEERR CCLLAASSSS http://www.tutorialspoint.com/java/java_characters.htm Copyright © tutorialspoint.com Normally, when we work with characters, we use primitive data types char. Example: char ch = 'a'; // Unicode for uppercase Greek omega character char uniChar = '\u039A'; // an array of chars char[] charArray ={ 'a', 'b', 'c', 'd', 'e' }; However in development, we come across situations where we need to use objects instead of primitive data types. In order to achieve this, Java provides wrapper class Character for primitive data type char. The Character class offers a number of useful class i. e. , static methods for manipulating characters. You can create a Character object with the Character constructor: Character ch = new Character('a'); The Java compiler will also create a Character object for you under some circumstances. For example, if you pass a primitive char into a method that expects an object, the compiler automatically converts the char to a Character for you. This feature is called autoboxing or unboxing, if the conversion goes the other way. Example: // Here following primitive char 'a' // is boxed into the Character object ch Character ch = 'a'; // Here primitive 'x' is boxed for method test, // return is unboxed to char 'c' char c = test('x'); Escape Sequences: A character preceded by a backslash (\) is an escape sequence and has special meaning to the compiler. The newline character \n has been used frequently in this tutorial in System.out.println statements to advance to the next line after the string is printed. Following table shows the Java escape sequences: Escape Sequence Description \t Inserts a tab in the text at this point.