Session Management Exposed
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SEO Footprints
SEO Footprints Brought to you by: Jason Rushton Copyright 2013 Online - M a r k e t i n g - T o o l s . c o m Page 1 Use these “Footprints” with your niche specific keywords to find Backlink sources. Some of the footprints below have already been formed into ready made search queries. TIP* If you find a footprint that returns the results you are looking for, there is no need to use the rest in that section. For example if I am looking for wordpress sites that allow comments and the search query “powered by wordpress” “YOUR YOUR KEYWORDS” returns lots of results there is no need to use all of the others that target wordpress sites as a lot of them will produce similar results. I would use one or two from each section. You can try them out and when you find one you like add it to your own list of favourites. Blogs “article directory powered by wordpress” “YOUR YOUR KEYWORDS” “blog powered by wordpress” “YOUR YOUR KEYWORDS” “blogs powered by typepad” “YOUR YOUR KEYWORDS” “YOURYOUR KEYWORDS” inurl:”trackback powered by wordpress” “powered by blogengine net 1.5.0.7” “YOUR YOUR KEYWORDS” “powered by blogengine.net” “YOUR YOUR KEYWORDS” “powered by blogengine.net add comment” “YOUR YOUR KEYWORDS” “powered by typepad” “YOUR YOUR KEYWORDS” “powered by wordpress” “YOUR YOUR KEYWORDS” “powered by wordpress review theme” “YOUR YOUR KEYWORDS” “proudly powered by wordpress” “YOUR YOUR KEYWORDS” “remove powered by wordpress” “YOUR YOUR KEYWORDS” Copyright 2013 Online - M a r k e t i n g - T o o l s . -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Locating Exploits and Finding Targets
452_Google_2e_06.qxd 10/5/07 12:52 PM Page 223 Chapter 6 Locating Exploits and Finding Targets Solutions in this chapter: ■ Locating Exploit Code ■ Locating Vulnerable Targets ■ Links to Sites Summary Solutions Fast Track Frequently Asked Questions 223 452_Google_2e_06.qxd 10/5/07 12:52 PM Page 224 224 Chapter 6 • Locating Exploits and Finding Targets Introduction Exploits, are tools of the hacker trade. Designed to penetrate a target, most hackers have many different exploits at their disposal. Some exploits, termed zero day or 0day, remain underground for some period of time, eventually becoming public, posted to newsgroups or Web sites for the world to share. With so many Web sites dedicated to the distribution of exploit code, it’s fairly simple to harness the power of Google to locate these tools. It can be a slightly more difficult exercise to locate potential targets, even though many modern Web application security advisories include a Google search designed to locate potential targets. In this chapter we’ll explore methods of locating exploit code and potentially vulnerable targets.These are not strictly “dark side” exercises, since security professionals often use public exploit code during a vulnerability assessment. However, only black hats use those tools against systems without prior consent. Locating Exploit Code Untold hundreds and thousands of Web sites are dedicated to providing exploits to the gen- eral public. Black hats generally provide exploits to aid fellow black hats in the hacking community.White hats provide exploits as a way of eliminating false positives from auto- mated tools during an assessment. Simple searches such as remote exploit and vulnerable exploit locate exploit sites by focusing on common lingo used by the security community. -
Software Übersicht
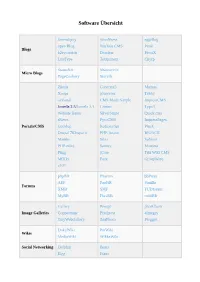
Software Übersicht Serendipity WordPress eggBlog open Blog Nucleus CMS Pixie Blogs b2evolution Dotclear PivotX LifeType Textpattern Chyrp StatusNet Sharetronix Micro Blogs PageCookery Storytlr Zikula Concrete5 Mahara Xoops phpwcms Tribiq ocPortal CMS Made Simple ImpressCMS Joomla 2.5/Joomla 3.1 Contao Typo3 Website Baker SilverStripe Quick.cms sNews PyroCMS ImpressPages Portals/CMS Geeklog Redaxscript Pluck Drupal 7/Drupal 8 PHP-fusion BIGACE Mambo Silex Subrion PHP-nuke Saurus Monstra Pligg jCore Tiki Wiki CMS MODx Fork GroupWare e107 phpBB Phorum bbPress AEF PunBB Vanilla Forums XMB SMF FUDforum MyBB FluxBB miniBB Gallery Piwigo phpAlbum Image Galleries Coppermine Pixelpost 4images TinyWebGallery ZenPhoto Plogger DokuWiki PmWiki Wikis MediaWiki WikkaWiki Social Networking Dolphin Beatz Elgg Etano Jcow PeoplePods Oxwall Noahs Classifieds GPixPixel Ad Management OpenX OSClass OpenClassifieds WebCalendar phpScheduleIt Calenders phpicalendar ExtCalendar BlackNova Traders Word Search Puzzle Gaming Shadows Rising MultiPlayer Checkers phplist Webmail Lite Websinsta maillist OpenNewsletter Mails SquirrelMail ccMail RoundCube LimeSurvey LittlePoll Matomo Analytics phpESP Simple PHP Poll Open Web Analytics Polls and Surveys CJ Dynamic Poll Aardvark Topsites Logaholic EasyPoll Advanced Poll dotProject Feng Office Traq phpCollab eyeOSh Collabtive Project PHProjekt The Bug Genie Eventum Management ProjectPier TaskFreak FlySpray Mantis Bug tracker Mound Zen Cart WHMCS Quick.cart Magento Open Source Point of Axis osCommerce Sale TheHostingTool Zuescart -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

In Support of DITA)
Collaborative Focus Areas project (in support of DITA) In addition to the requirements already defined which are specific to this project, I have compiled a list of standard measures for evaluating any Free and Open Source Software (FOSS) technology. FOSS Technology Requirements 1. Community How viable is the community supporting the product? Are there independent contributors? How active are mailing lists, web sites? Is the community healthy, friendly and welcoming to newcomers? 2. Low Entry Barrier How easy is it to get started? Is the product a turn-key solution with immediate value after download? How consistent is the documentation, how hard is it to familiarize oneself with the codebase? 3. Product Maturity How robust is the underlying code? Are sound software engineering practices in use? Is the architecture clean and consistent? Are changes to the code regression-tested? 4. Industrial Strength How much does the product scale? How flexible and stable is the product, how well does it perform? Is it secure? 5. Off The Shelf Components How much does the product make use of standard components? Is the architecture modular to accomodate external code? 6. Feature Set Does the product have a conservative feature set, or does it have many bells and whistles? 7. Standards Compliance How much does the product use and interoperate with standards? 8. Usability Is the user interface understandable for non-technical persons? Is it consistent? Does it follow usability best practice? 9. Platform How well does the application fit into our infrastructure? 10. Security What is the profile and track record of the community vis-a-vis security best-practices? How often is the project listed in security vulnerability alerts, and what is the response time? 11. -

Openstackでnecが実現する 「OSSクラウド」の世界
OpenStackでNECが実現する 「OSSクラウド」の世界 2013年3月12日 日本電気株式会社 プラットフォームマーケティング戦略本部 OSS推進室 技術主幹 高橋 千恵子 目次 ▐ OSSの動向 ▐ NECのOSS/Linux事業 ▐ OSSプラットフォームへの取り組み 高可用Linuxプラットフォーム OSSミドルウェアの活用 ▐ OSSクラウド OpenStackへの取り組み OSSクラウドソリューション ~沖縄クラウドサービス基盤~ OpenFlow+OpenStack ▐ 最後に ●本資料に掲載された社名、商品名は各社の商標または登録商標です。 Page 1 © NEC Corporation 2013 OSSの動向 Page 2 © NEC Corporation 2013 OSSコミュニティによるプロジェクト ▐ 全般 ・・・・・SaaS型アプリケーションが増加/著名OSSのベンダー配布、有償サポートや買収が進む OSS定点観測は、freecode.com にて実施。 ▐ インフラ系・・・仮想化やクラウド基盤関係のOSSが注目される/システム、ネット管理OSSの伸びがある サイトでの人気度(300以上)で順位付け。 OSSプロジェクトは2012.4時点で32.4万件。 ▐ デプロイメント系・・PostgreSQL、mySQLが高人気 これらのDB管理、DBクラスタリングOSSも伸びている ビジネス用途を中心に表示。 ▐ アプリ系・・・・SaaS型グループウェアOSS、ソフトウェア分類を越えた統合的な著名OSSの伸びがある コンシューマ・プライベート系は除く。 コンテンツアプリケーション •PHProject [GW] エンジニ コラボレーティブ •EGroupware CRM ERM SCM • Dokuwiki [Wiki] • jGnash アリング • WebGUI [CMF] • phpBB [GW] •OBM [GW] • Enterprise CRM and ア • Tiki Tiki CMS Groupware • ProcessMaker • CorneliOS [CMS] • Ariadne Groupware System • Task Juggler [PM] • Blender オペレーション • TinyMCE [DCM] • XODA • Simple Groupware [GW] プ • OpenWebMail[webmail]• Teamwork [GW] • Dolibarr • Achievo [PM] • mxGraph 製造管理 • Drupal [CMS] • mnoGoSerch • LedgerSMB • white_dune • eZpublish [publish FW]• Managing • ZIm [blog] • Plans [GW] • The Apache Open リ • Tine2.0 [CRM&GW] • GnuCash • Jgraph • OTRS • XWiki [Wiki] • Midgard • Zimbra [GW] for Business • Elastix • GroupOffice [GW] • Twiki [KB] • TUTOS[ERP&PM] • graphviz • FUDForum • OpenSearch Project コンシューマ 系 • SquirrelMail [Webmail] • Time Trex • BRL-CAD • Asterisk • Plone CMS Server • Citadel [bbs] • -

Mining Software Engineering Data for Useful Knowledge Boris Baldassari
Mining Software Engineering Data for Useful Knowledge Boris Baldassari To cite this version: Boris Baldassari. Mining Software Engineering Data for Useful Knowledge. Machine Learning [stat.ML]. Université de Lille, 2014. English. tel-01297400 HAL Id: tel-01297400 https://tel.archives-ouvertes.fr/tel-01297400 Submitted on 4 Apr 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. École doctorale Sciences Pour l’Ingénieur THÈSE présentée en vue d’obtenir le grade de Docteur, spécialité Informatique par Boris Baldassari Mining Software Engineering Data for Useful Knowledge preparée dans l’équipe-projet SequeL commune Soutenue publiquement le 1er Juillet 2014 devant le jury composé de : Philippe Preux, Professeur des universités - Université de Lille 3 - Directeur Benoit Baudry, Chargé de recherche INRIA - INRIA Rennes - Rapporteur Laurence Duchien, Professeur des universités - Université de Lille 1 - Examinateur Flavien Huynh, Ingénieur Docteur - Squoring Technologies - Examinateur Pascale Kuntz, Professeur des universités - Polytech’ Nantes - Rapporteur Martin Monperrus, Maître de conférences - Université de Lille 1 - Examinateur 2 Preface Maisqual is a recursive acronym standing for “Maisqual Automagically Improves Software QUALity”. It may sound naive or pedantic at first sight, but it clearly stated at one time the expectations of Maisqual. -

How to Install and Secure Egroupware
Need a license? or more flexibility? How to Install and Secure eGroupWare How To Install and Secure eGroupWare eGroupWare, why e ? decide for yourself, we could never pick one! enterprise, extended, extreme … groupware 2 How To Install and Secure eGroupWare The author and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. This document is published under the: Creative Commons Attribution-ShareAlike License For information on obtaining permissions for use of this material from this work, please submit your request to Reiner Jung [email protected] Linux is a trademark from Linus Torvalds Red Hat, Red Hat Network, RPM are trademarks or reghistered trademarks of RedHat Inc. in the United States and other countries SSH and Secure Shell are trademarks from SSH Communication Security Inc. Microsoft and Windows are either registered trademarks or trademarks of Microsoft Corporation in United States and/or other contries All other trademarks and copyrights referred to are the property of their respective owners expl0it labs offer packaging and open source security development expl0it press is responsible for publishing HOWTOs, white papers and more expl0it consulting offer security consulting in the enterprise Date published 5-Jan-05 3 How To Install and Secure eGroupWare Table -

Strategie Per Far Decollare Un Forum
Ebook Pratico Strategie per far decollare un Forum Guida scritta da Giorgio Taverniti e promossa da Madri Internet Marketing "So bene di toccare un argomento di nicchia, come so bene che non ci sono ebook su questo argomento in Italia. Se “metto la mia esperienza” (gratis naturalmente) maturata in oltre due anni di gestione di Forum è perché credo nello spirito di condivisione delle risorse per un miglioramento mio personale e per un miglioramento globale. Con questo Ebook voglio trasmettere a tutti l'esperienza che mi avete concesso di fare, ho imparato tutto questo grazie a voi, cari utenti a tutti i livelli del Forum GT (http://www.giorgiotave.it/forum/). Se vuoi vedere una mia breve video/intervista clicca qui: http://www.youtube.com/watch?v=afNq1UZr2WY Per scaricare questa guida e ripubblicarla nel tuo sito segui questo indirizzo: http://www.giorgiotave.it/guida_forum/strategie.zip Generale Premessa A mente fredda: i concorrenti ed il target La Board: ovvero il gestionale da usare per il tuo forum Riflessioni Generali I Forum I Tipi di Forum Ruoli del Forum L'Area Privata Moderatori [Usabilità] Opzioni interessanti per il Forum Siamo con i Motori [vBulletin] Ottimizzazione della board [PhpBB] Ottimizzazione della board Indicizzazione Forum Il SEO ed il TrustRank Interazione tra il forum ed il sito Interazione tra il forum ed il blog Promozione Quando un forum è vincente Come pubblicizzare il forum all'esterno Network intorno al Forum Un pochino di Psicologia Livelli e spazi per gli utenti Psicologia e Fidelizzazione in un Forum Forum -

Vpsville Community Forum by Fudforum 2.7.7 4
Subject: DNS & Domains Posted by Jayson Wonder on Thu, 04 Dec 2008 21:04:59 GMT View Forum Message <> Reply to Message Hi, I am strongly considering your services. I am moving 5 sites with domains from a Shared hosting package to a VPS I guess. I think I want a value server and probably can configure most things except the DNS server or DNS configuration for Virtual domains / sites. 1) Is there any initial setup support for this type of situation or am I totally on my own for the initial config? 2) I'm new to VPS's so excuse the ignorance but do I need to have a separate IP for each domain or site I host? 3) Will I have access to my own SSL certificates or shared certificates? I am curious about this as some sites will run e-commerce software of some type. 4) Also I am confused about the control panels... Do I have access to this type of software on a value server or only on a Host-in-ABox? Thanks, Subject: Re: DNS & Domains Posted by staff on Thu, 04 Dec 2008 21:50:20 GMT View Forum Message <> Reply to Message Hi, Here are some answers to your questions: 1. The value plans are self managed so we don't install or configure apache for you, you'd have to do that yourself. 2. You do not need a separate IP for each domain you host, but you do need a separate IP for each SSL site you host. 3. -

PHP Expert Debugger I PHP Expert Editor HP Expert Debugger to Darmowe I Ła- P Twe W Użyciu Narzędzie Służące Do Debuggowania Skryptów Napisanych W PHP
Spis treści Spis treści POCZĄTKI Co nowego w PHP6? 18 Richard Davey Jedenastego listopada, 2005 roku w Paryżu odby- Będzie się działo... ło się spotkanie twórców platformy PHP. Kluczo- wym elementem spotkania była dyskusja nad wy- oś wisi w powietrzu – chciało by się rzec. Wielki- znaczeniem przyszłych kierunków rozwoju dla tej mi krokami zbliża się PHP6, Oracle kupuje Zenda C technologii. – jedyną prawdziwą „firmę od PHP”, a Microsoft szko- li i egzaminuje deweloperów technologii Open Source, w tym PHP. Już teraz w siedzibach Microsoftu na ca- łym świecie możemy zdobyć tytuł Zend Certified En- TECHNIKI gineer. Czy nadchodzi więc rewolucja? Czy wydarze- Strumieniowa transmisja nia te zwiastują jakieś zmiany? I tak i nie. PHP6 nie przyniesie totalnie dźwięku przez HTTP przełomowych rozwiązań. Będzie to raczej ewolucja, ale starannie za- z wykorzystaniem Ampache 22 planowana, przemyślana i jak najbardziej potrzebna. O tym, co się zmie- Karl Vollmer ni w PHP, a co nie, przeczytacie w artykule Richarda Davey'a, Co nowe- Do stworzenia portalu multimedialnego nie trze- go w PHP6? ba drogich, komercyjnych, wydzielonych serwerów. Z drugiej strony, mianem rewolucyjnego przedsięwzięcia określiłbym Wystarczą PHP, serwer Apache oraz baza MySQL. Zend Collaboration Project, a w szczególności Zend PHP Framework. Faktem jest, że kolejne frameworki dla PHP powstają prawie jak grzyby Wzorce projektowe w akcji, po deszczu, ale wybór odpowiedniego narzędzia nadal jest bardzo trudny czyli ciąg dalszy Niezbędnika i często kończy się porażką, szczególnie w przypadku programistów, któ- dewelopera PHP 28 rzy po takie rozwiązanie sięgają po raz pierwszy. Zend PHP Framework Piotr Szarwas jest szansą dla deweloperów na wybór profesjonalnego, solidnego i rozwi- Czytelny i przejrzysty kod.