Publisher: Syngress Pub Date: September 2005 Print ISBN-10: 1-59749
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SEO Footprints
SEO Footprints Brought to you by: Jason Rushton Copyright 2013 Online - M a r k e t i n g - T o o l s . c o m Page 1 Use these “Footprints” with your niche specific keywords to find Backlink sources. Some of the footprints below have already been formed into ready made search queries. TIP* If you find a footprint that returns the results you are looking for, there is no need to use the rest in that section. For example if I am looking for wordpress sites that allow comments and the search query “powered by wordpress” “YOUR YOUR KEYWORDS” returns lots of results there is no need to use all of the others that target wordpress sites as a lot of them will produce similar results. I would use one or two from each section. You can try them out and when you find one you like add it to your own list of favourites. Blogs “article directory powered by wordpress” “YOUR YOUR KEYWORDS” “blog powered by wordpress” “YOUR YOUR KEYWORDS” “blogs powered by typepad” “YOUR YOUR KEYWORDS” “YOURYOUR KEYWORDS” inurl:”trackback powered by wordpress” “powered by blogengine net 1.5.0.7” “YOUR YOUR KEYWORDS” “powered by blogengine.net” “YOUR YOUR KEYWORDS” “powered by blogengine.net add comment” “YOUR YOUR KEYWORDS” “powered by typepad” “YOUR YOUR KEYWORDS” “powered by wordpress” “YOUR YOUR KEYWORDS” “powered by wordpress review theme” “YOUR YOUR KEYWORDS” “proudly powered by wordpress” “YOUR YOUR KEYWORDS” “remove powered by wordpress” “YOUR YOUR KEYWORDS” Copyright 2013 Online - M a r k e t i n g - T o o l s . -

Command-Line Sound Editing Wednesday, December 7, 2016
21m.380 Music and Technology Recording Techniques & Audio Production Workshop: Command-line sound editing Wednesday, December 7, 2016 1 Student presentation (pa1) • 2 Subject evaluation 3 Group picture 4 Why edit sound on the command line? Figure 1. Graphical representation of sound • We are used to editing sound graphically. • But for many operations, we do not actually need to see the waveform! 4.1 Potential applications • • • • • • • • • • • • • • • • 1 of 11 21m.380 · Workshop: Command-line sound editing · Wed, 12/7/2016 4.2 Advantages • No visual belief system (what you hear is what you hear) • Faster (no need to load guis or waveforms) • Efficient batch-processing (applying editing sequence to multiple files) • Self-documenting (simply save an editing sequence to a script) • Imaginative (might give you different ideas of what’s possible) • Way cooler (let’s face it) © 4.3 Software packages On Debian-based gnu/Linux systems (e.g., Ubuntu), install any of the below packages via apt, e.g., sudo apt-get install mplayer. Program .deb package Function mplayer mplayer Play any media file Table 1. Command-line programs for sndfile-info sndfile-programs playing, converting, and editing me- Metadata retrieval dia files sndfile-convert sndfile-programs Bit depth conversion sndfile-resample samplerate-programs Resampling lame lame Mp3 encoder flac flac Flac encoder oggenc vorbis-tools Ogg Vorbis encoder ffmpeg ffmpeg Media conversion tool mencoder mencoder Media conversion tool sox sox Sound editor ecasound ecasound Sound editor 4.4 Real-world -

Sound-HOWTO.Pdf
The Linux Sound HOWTO Jeff Tranter [email protected] v1.22, 16 July 2001 Revision History Revision 1.22 2001−07−16 Revised by: jjt Relicensed under the GFDL. Revision 1.21 2001−05−11 Revised by: jjt This document describes sound support for Linux. It lists the supported sound hardware, describes how to configure the kernel drivers, and answers frequently asked questions. The intent is to bring new users up to speed more quickly and reduce the amount of traffic in the Usenet news groups and mailing lists. The Linux Sound HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 1.1. Acknowledgments.............................................................................................................................1 1.2. New versions of this document.........................................................................................................1 1.3. Feedback...........................................................................................................................................2 1.4. Distribution Policy............................................................................................................................2 2. Sound Card Technology.................................................................................................................................3 3. Supported Hardware......................................................................................................................................4 -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

EMEP/MSC-W Model Unofficial User's Guide
EMEP/MSC-W Model Unofficial User’s Guide Release rv4_36 https://github.com/metno/emep-ctm Sep 09, 2021 Contents: 1 Welcome to EMEP 1 1.1 Licenses and Caveats...........................................1 1.2 Computer Information..........................................2 1.3 Getting Started..............................................2 1.4 Model code................................................3 2 Input files 5 2.1 NetCDF files...............................................7 2.2 ASCII files................................................ 12 3 Output files 17 3.1 Output parameters NetCDF files..................................... 18 3.2 Emission outputs............................................. 20 3.3 Add your own fields........................................... 20 3.4 ASCII outputs: sites and sondes..................................... 21 4 Setting the input parameters 23 4.1 config_emep.nml .......................................... 23 4.2 Base run................................................. 24 4.3 Source Receptor (SR) Runs....................................... 25 4.4 Separate hourly outputs......................................... 26 4.5 Using and combining gridded emissions................................. 26 4.6 Nesting.................................................. 27 4.7 config: Europe or Global?........................................ 31 4.8 New emission format........................................... 32 4.9 Masks................................................... 34 4.10 Other less used options......................................... -

RFP Response to Region 10 ESC
An NEC Solution for Region 10 ESC Building and School Security Products and Services RFP #EQ-111519-04 January 17, 2020 Submitted By: Submitted To: Lainey Gordon Ms. Sue Hayes Vertical Practice – State and Local Chief Financial Officer Government Region 10 ESC Enterprise Technology Services (ETS) 400 East Spring Valley Rd. NEC Corporation of America Richardson, TX 75081 Cell: 469-315-3258 Office: 214-262-3711 Email: [email protected] www.necam.com 1 DISCLAIMER NEC Corporation of America (“NEC”) appreciates the opportunity to provide our response to Education Service Center, Region 10 (“Region 10 ESC”) for Building and School Security Products and Services. While NEC realizes that, under certain circumstances, the information contained within our response may be subject to disclosure, NEC respectfully requests that all customer contact information and sales numbers provided herein be considered proprietary and confidential, and as such, not be released for public review. Please notify Lainey Gordon at 214-262-3711 promptly upon your organization’s intent to do otherwise. NEC requests the opportunity to negotiate the final terms and conditions of sale should NEC be selected as a vendor for this engagement. NEC Corporation of America 3929 W John Carpenter Freeway Irving, TX 75063 http://www.necam.com Copyright 2020 NEC is a registered trademark of NEC Corporation of America, Inc. 2 Table of Contents EXECUTIVE SUMMARY ................................................................................................................................... -

Locating Exploits and Finding Targets
452_Google_2e_06.qxd 10/5/07 12:52 PM Page 223 Chapter 6 Locating Exploits and Finding Targets Solutions in this chapter: ■ Locating Exploit Code ■ Locating Vulnerable Targets ■ Links to Sites Summary Solutions Fast Track Frequently Asked Questions 223 452_Google_2e_06.qxd 10/5/07 12:52 PM Page 224 224 Chapter 6 • Locating Exploits and Finding Targets Introduction Exploits, are tools of the hacker trade. Designed to penetrate a target, most hackers have many different exploits at their disposal. Some exploits, termed zero day or 0day, remain underground for some period of time, eventually becoming public, posted to newsgroups or Web sites for the world to share. With so many Web sites dedicated to the distribution of exploit code, it’s fairly simple to harness the power of Google to locate these tools. It can be a slightly more difficult exercise to locate potential targets, even though many modern Web application security advisories include a Google search designed to locate potential targets. In this chapter we’ll explore methods of locating exploit code and potentially vulnerable targets.These are not strictly “dark side” exercises, since security professionals often use public exploit code during a vulnerability assessment. However, only black hats use those tools against systems without prior consent. Locating Exploit Code Untold hundreds and thousands of Web sites are dedicated to providing exploits to the gen- eral public. Black hats generally provide exploits to aid fellow black hats in the hacking community.White hats provide exploits as a way of eliminating false positives from auto- mated tools during an assessment. Simple searches such as remote exploit and vulnerable exploit locate exploit sites by focusing on common lingo used by the security community. -

Sox Examples
Signal Analysis Young Won Lim 2/17/18 Copyright (c) 2016 – 2018 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". Please send corrections (or suggestions) to [email protected]. This document was produced by using LibreOffice. Young Won Lim 2/17/18 Based on Signal Processing with Free Software : Practical Experiments F. Auger Audio Signal Young Won Lim Analysis (1A) 3 2/17/18 Sox Examples Audio Signal Young Won Lim Analysis (1A) 4 2/17/18 soxi soxi s1.mp3 soxi s1.mp3 > s1_info.txt Input File Channels Sample Rate Precision Duration File Siz Bit Rate Sample Encoding Audio Signal Young Won Lim Analysis (1A) 5 2/17/18 Generating signals using sox sox -n s1.mp3 synth 3.5 sine 440 sox -n s2.wav synth 90000s sine 660:1000 sox -n s3.mp3 synth 1:20 triangle 440 sox -n s4.mp3 synth 1:20 trapezium 440 sox -V4 -n s5.mp3 synth 6 square 440 0 0 40 sox -n s6.mp3 synth 5 noise Audio Signal Young Won Lim Analysis (1A) 6 2/17/18 stat Sox s1.mp3 -n stat Sox s1.mp3 -n stat > s1_info_stat.txt Samples read Length (seconds) Scaled by Maximum amplitude Minimum amplitude Midline amplitude Mean norm Mean amplitude RMS amplitude Maximum delta Minimum delta Mean delta RMS delta Rough frequency Volume adjustment Audio Signal Young Won -

Name Synopsis Description Options
SoXI(1) Sound eXchange SoXI(1) NAME SoXI − Sound eXchange Information, display sound file metadata SYNOPSIS soxi [−V[level]] [−T][−t|−r|−c|−s|−d|−D|−b|−B|−p|−e|−a] infile1 ... DESCRIPTION Displays information from the header of a givenaudio file or files. Supported audio file types are listed and described in soxformat(7). Note however, that soxi is intended for use only with audio files with a self- describing header. By default, as much information as is available is shown. An option may be giventoselect just a single piece of information (perhaps for use in a script or batch-file). OPTIONS −V Set verbosity.See sox(1) for details. −T Used with multiple files; changes the behaviour of −s, −d and −D to display the total across all givenfiles. Note that when used with −s with files with different sampling rates, this is of ques- tionable value. −t Showdetected file-type. −r Showsample-rate. −c Shownumber of channels. −s Shownumber of samples (0 if unavailable). −d Showduration in hours, minutes and seconds (0 if unavailable). Equivalent to number of samples divided by the sample-rate. −D Showduration in seconds (0 if unavailable). −b Shownumber of bits per sample (0 if not applicable). −B Showthe bitrate averaged overthe whole file (0 if unavailable). −p Showestimated sample precision in bits. −e Showthe name of the audio encoding. −a Showfile comments (annotations) if available. BUGS Please report anybugs found in this version of SoX to the mailing list ([email protected]). SEE ALSO sox(1), soxformat(7), libsox(3) The SoX web site at http://sox.sourceforge.net LICENSE Copyright 2008−2013 by Chris Bagwell and SoX Contributors. -
Software Übersicht
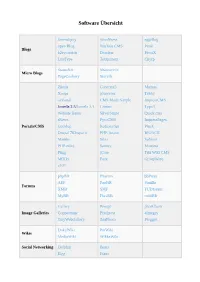
Software Übersicht Serendipity WordPress eggBlog open Blog Nucleus CMS Pixie Blogs b2evolution Dotclear PivotX LifeType Textpattern Chyrp StatusNet Sharetronix Micro Blogs PageCookery Storytlr Zikula Concrete5 Mahara Xoops phpwcms Tribiq ocPortal CMS Made Simple ImpressCMS Joomla 2.5/Joomla 3.1 Contao Typo3 Website Baker SilverStripe Quick.cms sNews PyroCMS ImpressPages Portals/CMS Geeklog Redaxscript Pluck Drupal 7/Drupal 8 PHP-fusion BIGACE Mambo Silex Subrion PHP-nuke Saurus Monstra Pligg jCore Tiki Wiki CMS MODx Fork GroupWare e107 phpBB Phorum bbPress AEF PunBB Vanilla Forums XMB SMF FUDforum MyBB FluxBB miniBB Gallery Piwigo phpAlbum Image Galleries Coppermine Pixelpost 4images TinyWebGallery ZenPhoto Plogger DokuWiki PmWiki Wikis MediaWiki WikkaWiki Social Networking Dolphin Beatz Elgg Etano Jcow PeoplePods Oxwall Noahs Classifieds GPixPixel Ad Management OpenX OSClass OpenClassifieds WebCalendar phpScheduleIt Calenders phpicalendar ExtCalendar BlackNova Traders Word Search Puzzle Gaming Shadows Rising MultiPlayer Checkers phplist Webmail Lite Websinsta maillist OpenNewsletter Mails SquirrelMail ccMail RoundCube LimeSurvey LittlePoll Matomo Analytics phpESP Simple PHP Poll Open Web Analytics Polls and Surveys CJ Dynamic Poll Aardvark Topsites Logaholic EasyPoll Advanced Poll dotProject Feng Office Traq phpCollab eyeOSh Collabtive Project PHProjekt The Bug Genie Eventum Management ProjectPier TaskFreak FlySpray Mantis Bug tracker Mound Zen Cart WHMCS Quick.cart Magento Open Source Point of Axis osCommerce Sale TheHostingTool Zuescart -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

In Support of DITA)
Collaborative Focus Areas project (in support of DITA) In addition to the requirements already defined which are specific to this project, I have compiled a list of standard measures for evaluating any Free and Open Source Software (FOSS) technology. FOSS Technology Requirements 1. Community How viable is the community supporting the product? Are there independent contributors? How active are mailing lists, web sites? Is the community healthy, friendly and welcoming to newcomers? 2. Low Entry Barrier How easy is it to get started? Is the product a turn-key solution with immediate value after download? How consistent is the documentation, how hard is it to familiarize oneself with the codebase? 3. Product Maturity How robust is the underlying code? Are sound software engineering practices in use? Is the architecture clean and consistent? Are changes to the code regression-tested? 4. Industrial Strength How much does the product scale? How flexible and stable is the product, how well does it perform? Is it secure? 5. Off The Shelf Components How much does the product make use of standard components? Is the architecture modular to accomodate external code? 6. Feature Set Does the product have a conservative feature set, or does it have many bells and whistles? 7. Standards Compliance How much does the product use and interoperate with standards? 8. Usability Is the user interface understandable for non-technical persons? Is it consistent? Does it follow usability best practice? 9. Platform How well does the application fit into our infrastructure? 10. Security What is the profile and track record of the community vis-a-vis security best-practices? How often is the project listed in security vulnerability alerts, and what is the response time? 11.