Name Synopsis Description
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SCIS Boardman Labs User Manual Version5
SCIS Common Use Labs in Boardman Hall USER MANUAL Note: The instructions in this manual assume students walking into the labs are first-time users of the labs and are complete novices in using the machines. Table of Contents Page I. Access to Boardman Hall SCIS Labs for Computer Science and New Media Students A. Services Provided 2 B. Gaining Access to Lab Rooms and Computers 3 II. SCIS Common Use Lab (Room 138 Boardman) A. Services Provided 3 B. Use of iMacs on Tables 4 C. Use of Large Table Monitor for Sharing Among Table Group 4 D. Use of Overhead Projector 5 E. Use of Laser Printer (8 ½ by 11” Prints) 6 F. Use of Large Format Plotter 7 G. Software Available on Computers in Room 138 7 H. Equipment Available for Checkout from Room 138 Lab Monitors 8 III. Combined Focus Ring and Stillwater Labs (Rooms 127 and 129 Boardman) A. Services Provided 8 B. Use of iMacs on Tables 9 C. Use of Cybertron PC for AI and VR D. Use of … E. Software Available on Computers in Rooms 127 and 129 F. Equipment Checkout Procedure G. Equipment Available for Checkout from Rooms 127 and 129 Lab Monitors IV. SCIS Student Lounge and Project Work Room (Room 137 Boardman) A. Services Provided B. Use of Large Screen by Students APPENDICES Appendix A. Laptop Computer Recommendations for Computer Science Students Appendix B. Laptop Computer Recommendations for New Media Students Appendix C. Convenient Web Resources for Development of Computer Code Note: On SCIS web site all of the above topics will link to anchors at the same topics below. -

Tworzenie Dokumentów, Prawo Autorskie
Zajęcia 7 - tworzenie dokumentów JANUSZ WRÓBEL Typy plików Tekstowe txt – najprostszy plik tekstowy np. z Notatnika doc, docx - dokumenty z WORDA lub WORDPADA odt – dokumenty z programu OPENOFFICE rtf – format tekstowy zawierający podstawowe formatowanie tekstu kompatybilny z wieloma edytorami tekstu Graficzne jpg – najpopularniejszy format plików graficznych png – format głównie wykorzystywany przez Internet gif – format graficzny umożliwiający przechowanie wielu obrazów tworzących np. animację Tiff – format kompresji bezstratnej Dźwiękowe Mp3 – najpopularniejszy, stratny zapis dźwięku Midi - standard dla przechowywania zapisu dźwięku zbliżonego do nutowego Wav – popularny standard dla Windowsa i internetu Wma – gównie pliki w Windowsie Wideo MPEG4 – najpopularniejszy standard kodowania umożliwiający rejestrowanie i przesyłanie na bieżąco wizji i fonii. MOV- kodowanie firmy Apple wymaga specjalnego odtwarzacza QuickTime Player Avi – format zapisu filmów zwykle przeznaczonych do dalszej obróbki WMV – format kompresji filmów firmy Microsoft FLV – format filmów wykorzystywany na stronach www Uruchamialne EXE – popularny dla Windowsa plik programu mogący zawierać różne zasoby np. okna, ikony, dźwięki BAT – program wykonywany przez komputer bez wpływu użytkownika na jego przebieg (tryb wsadowy) COM – dawniej popularny typ programów wykonywalnych w systemie DOS Skompresowane ZIP – format kompresji bezstratnej i archiwizacji na PC (Personal Computer) RAR – format kompresji bezstratnej i archiwizacji JPG, MPEG, MP3 – to -
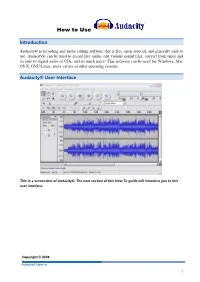
Audacity® Is Recording and Audio Editing Software That Is Free, Open Sourced, and Generally Easy to Use
How to Use Introduction Audacity® is recording and audio editing software that is free, open sourced, and generally easy to use. Audacity® can be used to record live audio, edit various sound files, convert from tapes and records to digital audio or CDs, and so much more! This software can be used for Windows, Mac OS X, GNU/Linux, and a variety of other operating systems. Audacity® User Interface This is a screenshot of Audacity®. The next section of this How-To guide will introduce you to this user interface. Copyright © 2008 Audacity® How- to 1 Audacity® User Interface: Toolbars The Audacity® Control Toolbar Envelope Tool Skip to Start Stop Button Button Select D r a w Record Tool Tool Button Zoom Multi- Tool Tool Pause Skip to End Timeshift Play Button Button Tool Button The Audacity® Edit Toolbar Zoom Zoom To Copy Cut Paste Undo Redo Out Selection Zoom Zoom To Trim Silence In Entire Project The Audacity® Meter & Mixer Toolbars Input Output Level Level Meter Meter Output Input Volume Volume Input Control Control Source Selector Copyright © 2008 Audacity® How- to 2 Importing Audio with Audacity® 1. Create a New Project This is an important step. Give your project a name & saving location prior to working in Audacity®. Select and choose a file name and location to save your project. *Note when you initially begin Audacity® only the “Save As” function will be available. 2. Check Preferences Click File > Preferences (Ctrl + P) Check to be sure the correct Playback & Recording Devices have been selected. Copyright © 2008 Audacity® How- to 3 Set the sample rate of your choice. -
Qualys Policy Compliance Getting Started Guide
Policy Compliance Getting Started Guide July 28, 2021 Verity Confidential Copyright 2011-2021 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks are the property of their respective owners. Qualys, Inc. 919 E Hillsdale Blvd Foster City, CA 94404 1 (650) 801 6100 Table of Contents Get Started ........................................................................................................ 5 Set Up Assets............................................................................................................................ 6 Start Collecting Compliance Data ............................................................... 8 Configure Authentication....................................................................................................... 8 Launch Compliance Scans ................................................................................................... 10 We recommend you schedule scans to run automatically .............................................. 12 How to configure scan settings............................................................................................ 12 Install Cloud Agents.............................................................................................................. 17 Evaluate Middleware Assets by Using Cloud Agent .......................................................... 17 Define Policies ................................................................................................. 21 -

Command-Line Sound Editing Wednesday, December 7, 2016
21m.380 Music and Technology Recording Techniques & Audio Production Workshop: Command-line sound editing Wednesday, December 7, 2016 1 Student presentation (pa1) • 2 Subject evaluation 3 Group picture 4 Why edit sound on the command line? Figure 1. Graphical representation of sound • We are used to editing sound graphically. • But for many operations, we do not actually need to see the waveform! 4.1 Potential applications • • • • • • • • • • • • • • • • 1 of 11 21m.380 · Workshop: Command-line sound editing · Wed, 12/7/2016 4.2 Advantages • No visual belief system (what you hear is what you hear) • Faster (no need to load guis or waveforms) • Efficient batch-processing (applying editing sequence to multiple files) • Self-documenting (simply save an editing sequence to a script) • Imaginative (might give you different ideas of what’s possible) • Way cooler (let’s face it) © 4.3 Software packages On Debian-based gnu/Linux systems (e.g., Ubuntu), install any of the below packages via apt, e.g., sudo apt-get install mplayer. Program .deb package Function mplayer mplayer Play any media file Table 1. Command-line programs for sndfile-info sndfile-programs playing, converting, and editing me- Metadata retrieval dia files sndfile-convert sndfile-programs Bit depth conversion sndfile-resample samplerate-programs Resampling lame lame Mp3 encoder flac flac Flac encoder oggenc vorbis-tools Ogg Vorbis encoder ffmpeg ffmpeg Media conversion tool mencoder mencoder Media conversion tool sox sox Sound editor ecasound ecasound Sound editor 4.4 Real-world -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Oracle Optimized Solution for Oracle E-Business Suite a High-Performance, Flexible Architecture on SPARC T5-2 Servers and Oracle Exadata
Oracle Optimized Solution for Oracle E-Business Suite A High-Performance, Flexible Architecture on SPARC T5-2 Servers and Oracle Exadata ORACLE WHITE P A P E R | OCTOBER 2015 Table of Contents Introduction 1 Solution Overview 2 Oracle Technologies—Everything Needed for Oracle E-Business Suite Deployment 2 Platform Infrastructure 3 Network Infrastructure and Remote Management 4 Built-in Virtualization for Simplified Oracle E-Business Suite Application Consolidation 4 High Availability Features to Keep Oracle E-Business Suite Running 6 Backup, Restore, and Disaster Recovery Solutions 6 Built-in Security Technology and Comprehensive Tools for Secure Deployment 7 Cryptographic Acceleration for Oracle E-Business Suite 7 Secure Isolation 9 Secure Access Control 9 Data Protection 9 Compliance 10 Security Best Practices for Oracle E-Business Suite Deployments 10 Security Technical Implementation Guides 11 My Oracle Support Documents 11 Component-Level Security Recommendations 12 Mapping an Oracle E-Business Suite Deployment to SPARC T5 Servers and Oracle Exadata 13 Consolidating to Oracle Systems 14 ORACLE OPTIMIZED SOLUTION FOR ORACLE E-BUSINESS SUITE A Basic Production System 15 Test Systems, Disaster Recovery Systems, and Other Systems 17 Solution Scalability 18 Consolidation of Quality Assurance, Disaster Recovery, and Other Systems 18 Consolidating onto a Single Oracle System 18 Cloud-Based Deployments 19 Additional Oracle Optimized Solutions for Oracle E-Business Suite Deployments 20 Oracle Optimized Solution for Secure Backup and Recovery -

Sound-HOWTO.Pdf
The Linux Sound HOWTO Jeff Tranter [email protected] v1.22, 16 July 2001 Revision History Revision 1.22 2001−07−16 Revised by: jjt Relicensed under the GFDL. Revision 1.21 2001−05−11 Revised by: jjt This document describes sound support for Linux. It lists the supported sound hardware, describes how to configure the kernel drivers, and answers frequently asked questions. The intent is to bring new users up to speed more quickly and reduce the amount of traffic in the Usenet news groups and mailing lists. The Linux Sound HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 1.1. Acknowledgments.............................................................................................................................1 1.2. New versions of this document.........................................................................................................1 1.3. Feedback...........................................................................................................................................2 1.4. Distribution Policy............................................................................................................................2 2. Sound Card Technology.................................................................................................................................3 3. Supported Hardware......................................................................................................................................4 -

EMEP/MSC-W Model Unofficial User's Guide
EMEP/MSC-W Model Unofficial User’s Guide Release rv4_36 https://github.com/metno/emep-ctm Sep 09, 2021 Contents: 1 Welcome to EMEP 1 1.1 Licenses and Caveats...........................................1 1.2 Computer Information..........................................2 1.3 Getting Started..............................................2 1.4 Model code................................................3 2 Input files 5 2.1 NetCDF files...............................................7 2.2 ASCII files................................................ 12 3 Output files 17 3.1 Output parameters NetCDF files..................................... 18 3.2 Emission outputs............................................. 20 3.3 Add your own fields........................................... 20 3.4 ASCII outputs: sites and sondes..................................... 21 4 Setting the input parameters 23 4.1 config_emep.nml .......................................... 23 4.2 Base run................................................. 24 4.3 Source Receptor (SR) Runs....................................... 25 4.4 Separate hourly outputs......................................... 26 4.5 Using and combining gridded emissions................................. 26 4.6 Nesting.................................................. 27 4.7 config: Europe or Global?........................................ 31 4.8 New emission format........................................... 32 4.9 Masks................................................... 34 4.10 Other less used options......................................... -

RFP Response to Region 10 ESC
An NEC Solution for Region 10 ESC Building and School Security Products and Services RFP #EQ-111519-04 January 17, 2020 Submitted By: Submitted To: Lainey Gordon Ms. Sue Hayes Vertical Practice – State and Local Chief Financial Officer Government Region 10 ESC Enterprise Technology Services (ETS) 400 East Spring Valley Rd. NEC Corporation of America Richardson, TX 75081 Cell: 469-315-3258 Office: 214-262-3711 Email: [email protected] www.necam.com 1 DISCLAIMER NEC Corporation of America (“NEC”) appreciates the opportunity to provide our response to Education Service Center, Region 10 (“Region 10 ESC”) for Building and School Security Products and Services. While NEC realizes that, under certain circumstances, the information contained within our response may be subject to disclosure, NEC respectfully requests that all customer contact information and sales numbers provided herein be considered proprietary and confidential, and as such, not be released for public review. Please notify Lainey Gordon at 214-262-3711 promptly upon your organization’s intent to do otherwise. NEC requests the opportunity to negotiate the final terms and conditions of sale should NEC be selected as a vendor for this engagement. NEC Corporation of America 3929 W John Carpenter Freeway Irving, TX 75063 http://www.necam.com Copyright 2020 NEC is a registered trademark of NEC Corporation of America, Inc. 2 Table of Contents EXECUTIVE SUMMARY ................................................................................................................................... -

Sox Examples
Signal Analysis Young Won Lim 2/17/18 Copyright (c) 2016 – 2018 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". Please send corrections (or suggestions) to [email protected]. This document was produced by using LibreOffice. Young Won Lim 2/17/18 Based on Signal Processing with Free Software : Practical Experiments F. Auger Audio Signal Young Won Lim Analysis (1A) 3 2/17/18 Sox Examples Audio Signal Young Won Lim Analysis (1A) 4 2/17/18 soxi soxi s1.mp3 soxi s1.mp3 > s1_info.txt Input File Channels Sample Rate Precision Duration File Siz Bit Rate Sample Encoding Audio Signal Young Won Lim Analysis (1A) 5 2/17/18 Generating signals using sox sox -n s1.mp3 synth 3.5 sine 440 sox -n s2.wav synth 90000s sine 660:1000 sox -n s3.mp3 synth 1:20 triangle 440 sox -n s4.mp3 synth 1:20 trapezium 440 sox -V4 -n s5.mp3 synth 6 square 440 0 0 40 sox -n s6.mp3 synth 5 noise Audio Signal Young Won Lim Analysis (1A) 6 2/17/18 stat Sox s1.mp3 -n stat Sox s1.mp3 -n stat > s1_info_stat.txt Samples read Length (seconds) Scaled by Maximum amplitude Minimum amplitude Midline amplitude Mean norm Mean amplitude RMS amplitude Maximum delta Minimum delta Mean delta RMS delta Rough frequency Volume adjustment Audio Signal Young Won -

Trustworthy Whole-System Provenance for the Linux Kernel
Trustworthy Whole-System Provenance for the Linux Kernel Adam Bates, Dave (Jing) Tian, Thomas Moyer Kevin R.B. Butler University of Florida MIT Lincoln Laboratory {adammbates,daveti,butler}@ufl.edu [email protected] Abstract is presently of enormous interest in a variety of dis- In a provenance-aware system, mechanisms gather parate communities including scientific data processing, and report metadata that describes the history of each ob- databases, software development, and storage [43, 53]. ject being processed on the system, allowing users to un- Provenance has also been demonstrated to be of great derstand how data objects came to exist in their present value to security by identifying malicious activity in data state. However, while past work has demonstrated the centers [5, 27, 56, 65, 66], improving Mandatory Access usefulness of provenance, less attention has been given Control (MAC) labels [45, 46, 47], and assuring regula- to securing provenance-aware systems. Provenance it- tory compliance [3]. self is a ripe attack vector, and its authenticity and in- Unfortunately, most provenance collection mecha- tegrity must be guaranteed before it can be put to use. nisms in the literature exist as fully-trusted user space We present Linux Provenance Modules (LPM), applications [28, 27, 41, 56]. Even kernel-based prove- the first general framework for the development of nance mechanisms [43, 48] and sketches for trusted provenance-aware systems. We demonstrate that LPM provenance architectures [40, 42] fall short of providing creates a trusted provenance-aware execution environ- a provenance-aware system for malicious environments. ment, collecting complete whole-system provenance The problem of whether or not to trust provenance is fur- while imposing as little as 2.7% performance overhead ther exacerbated in distributed environments, or in lay- on normal system operation.