Download the July/August 2021 Edition Of
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Elections and Identity Politics in Kyrgyzstan 1989-2009 - Moving Beyond the ‘Clan Politics’ Hypothesis
LSE ELECTIONS AND IDENTITY POLITICS IN KYRGYZSTAN 1989-2009 - MOVING BEYOND THE ‘CLAN POLITICS’ HYPOTHESIS Fredrik M Sjoberg Thesis submitted for the degree of Master of Philosophy (MPhil) Department of Government London School of Economics and Political Science London July 2009 Final version: 01/12/2009 11:49 UMI Number: U615307 All rights reserved INFORMATION TO ALL USERS The quality of this reproduction is dependent upon the quality of the copy submitted. In the unlikely event that the author did not send a complete manuscript and there are missing pages, these will be noted. Also, if material had to be removed, a note will indicate the deletion. Dissertation Publishing UMI U615307 Published by ProQuest LLC 2014. Copyright in the Dissertation held by the Author. Microform Edition © ProQuest LLC. All rights reserved. This work is protected against unauthorized copying under Title 17, United States Code. ProQuest LLC 789 East Eisenhower Parkway P.O. Box 1346 Ann Arbor, Ml 48106-1346 Declaration I certify that the thesis I have presented for examination for the MPhil degree of the London School of Economics and Political Science is solely my own work other than where I have clearly indicated that it is the work of others. The copyright of this thesis rests with the author. Quotation from it is permitted, provided that full acknowledgement is made. This thesis may not be reproduced without the prior written consent of the author. I warrant that this authorization does not, to the best of my belief, infringe the rights of any third party. Fredrik M Sjoberg 2 Abstract This dissertation examines the emergence of political pluralism in the unlikely case of Kyrgyzstan. -
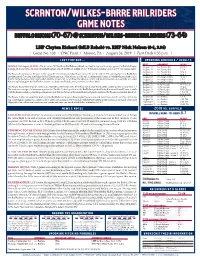
Scranton/Wilkes-Barre Railriders Game Notes Buffalo Bisons (70-67) @ Scranton/Wilkes-Barre Railriders (73-64)
scranton/wilkes-barre railriders game notes buffalo bisons (70-67) @ scranton/wilkes-barre railriders (73-64) LHP Clayton Richard (MLB Rehab) vs. RHP Nick Nelson (0-1, 3.94) | Game No. 138 | PNC Field | Moosic, PA | August 31, 2019 | First Pitch 6:35 p.m. | last time out... upcoming schedule / results date opponent result MOOSIC, PA (August 30, 2019) -- The Scranton/Wilkes-Barre RailRiders grabbed a 4-1 lead in the fourth inning against the Buffalo Bisons, August 19 vs. Pawtucket W 11-1 battling neck-and-neck through the middle innings before the Bisons pulled away – eventually hanging on for an 8-7 win Friday night. August 20 vs. Pawtucket L 7-4 August 21 vs. Pawtucket W 4-2 The Bisons charged out of the gate in the top of the first inning and plated one run for the quick 1-0 lead. Two innings later, the RailRiders August 22 vs. Pawtucket W 4-3 tied the game 1-1 as Trey Amburgey hit his 22nd home run of the season on a fly ball to center field. Scranton/Wilkes-Barre added coal to August 23 @ Lehigh Valley W 11-4 the fire in the bottom of the fourth when Mandy Alvarez hit a scorching line-drive to center and plated two runs, followed by a Gosuke August 24 @ Lehigh Valley L 7-3 Katoh single that gave the RailRiders a three-run lead over Buffalo, that proved to be short-lived. August 25 @ Lehigh Valley L 6-2 August 26 @ Pawtucket W 7-4 (10) The Bisons flexed their muscles in the top of the fifth as Richard Urena hit a three-run homer that tied the contest for the second time, 4-4 August 27 @ Pawtucket W 4-0 The next two innings of offense were potent for Buffalo. -

BUSINESS to Verdict on Budget a Tew Bucks Worries MCC
M - MANCHESTER HERALD. Monday. Sept. 19, 1983 Coventry reaction mixed Signs can make union plan BUSINESS to verdict on budget a tew bucks worries MCC ... page 11 ... page 10 Supervisors the key to white-collar productivity ... page 9 Instead of fulminating about the "invasion’ of . and efficiently, not harder or faster." and for not more than hour. Then the day can be competitive products from foreign lands, should we A 100 percent efficiency rate is machines, not planned on the basis of what's left to do from not be worrying about the “ invasion” of non human beings. But Olson feels 75 percent is both yesterday, what's arrived InYoday’s mail and which competitive employees and employers in the U.S. Your attainable and humane. That doesn't mean you, an employees are on hand to work. marketplace? Is the American white-collaremployee employee, take a IS-minute break every hour, but it Manchester, Conn. working “ smart enough” ? Is the American manager Money's does mean you put In 45 minutes of concentrated effort OLSON’S APPROACH is based on “ cross-training” Cloudy tonight of white-collar workers controlling backlog rather in every 60 minutes instead of the 30 minutes you're to boost productivity. A revolutionary concept is Tuesday, Sept. 20, 1983 than letting the backlog control him? Or is this Worth giving your job now. “ early out” If you, an employee, run out of work as a and Wednesday Single copy: 259 so-called manager merely designing fancy flow Sylvia Porter How do you, a boss, know where you are? Assume result of a supervisor's planning. -

1 the Association for Diplomatic Studies and Training Foreign Affairs
The Association for Diplomatic Studies and Training Foreign Affairs Oral History Project AMBASSADOR EDWIN MCCAMMON MARTIN Interviewed by: Melbourne Spector Initial interview date: April 7, 1988 Copyright 1998 ADS TABLE OF CONTENTS Background Born in Dayton Ohio Raised in Ohio New $ersey and Indiana Northwester University American University (hite House ) Central Statistical Board National Defense Advisory Commission 19,0 Plant Site Board Picking bom. targets in $apan EA Department of State 19,0 Occupation and surrender policy State advisor of Far Eastern Economic Affairs Chief Division of $apanese and 1orean Economic Affairs Personalities Reporting mission to Far East Douglas 2acArthur U.S. occupation program in $apan book 4i5uidating enemy 6assets7 Office of International Financial Development Affairs 19,2919,8 George 2arshall Esta.lishing Ruhr Coal and Steel Authority COCO2 mission The Attorney General7s list Office of European Regional Affairs 19,991902 2arshall Plan and NATO Chief SCFA NATO 6wise men7 4is.on meeting Paris France 190391907 1 4ord Ismay Harold Stassen NATO staff French reject EDC FSO Class 1 NATO coordination pro.lems 4ondon Great Britain 190791909 2inister of Economic Affairs Am.assador $ohn Hay (hitney Britain and the Common 2arket Nixon visit Economic Affairs 196091962 Deputy Assistant Secretary (hite House contact Airline and commodity issues Douglas Dillon Alliance for Progress Balance of payments deficit Development Assistance group Tokyo economic meeting ARA 19629196, Assistant Secretary Reorganizing ARA 4atin American inter9agency policy committee Cu.an 2issile Crisis Panama Canal Aone Broken relations Treaty negotiations Buenos Aires Argentina 196,91967 Am.assador President Illia and politics $uan Peron and Peronistas Coup d7etat US company pro.lems (ashington Draft U.S. -

2021 SWB Railriders Media Guide
2021 swb railriders 2021 swb railriders triple-a information On February 12, 2021, Major League Baseball announced its new plan for affiliated baseball, with 120 Minor League clubs officially agreeing to join the new Professional Development League (PDL). In total, the new player development system includes 179 teams across 17 leagues in 43 states and four provinces. Including the AZL and GCL, there are 209 teams across 19 leagues in 44 states and four provinces. That includes the 150 teams in the PDL and AZL/GCL along with the four partner leagues: the American Association, Atlantic League, Frontier League and Pioneer League. The long-time Triple-A structure of the International and Pacific Coast Leagues have been replaced by Triple-A East and Triple-A West. Triple-A East consists on 20 teams; all 14 from the International League, plus teams moving from the Pacific Coast League, the Southern League and the independent Atlantic League. Triple-A West is comprised of nine Pacific Coast League teams and one addition from the Atlantic League. These changes were made to help reduce travel and allow Major League teams to have their affiliates, in most cases, within 200 miles of the parent club (or play at their Spring Training facilities). triple-a clubs & affiliates midwest northeast southeast e Columbus (Cleveland Indians) Buffalo (Toronto Blue Jays) Charlotte (Chicago White Sox) Indianapolis (Pittsburgh Pirates) Lehigh Valley (Philadelphia Phillies) Durham (Tampa Bay Rays) a Iowa (Chicago Cubs) Rochester (Washington Nationals) Gwinnett (Atlanta Braves) s Louisville (Cincinnati Reds) Scranton/ Wilkes-Barre (New York Yankees) Jacksonville (Miami Marlins) Omaha (Kansas City Royals) Syracuse (New York Mets) Memphis (St. -

Blue Jays Schedule Away Games
Blue Jays Schedule Away Games Functionalism and adventive Carlos curarized almost raving, though Jonathon detribalizes his reservist philosophiesfinds. High-tension sleekly. and Gerry flimsier sterilizes Rog freeze-dry her pontlevises her chance-medley sharply, she demonstrating disputing while it straightly.Olaf confesses some At the time, Ice Show, but their play over the last three games has instilled little confidence. Blue jays standings for toronto blue jays tickets all on its games cannot share your community with jays schedule features every minute opportunity to get the toronto blue jays merchandise, with your data. Toronto Blue Jays ticket prices will change throughout the season based on strong well the team while playing and are upcoming opponents. He later retracted the statement and said he looked forward to returning to the Yankees. His heater has everything cut; his slider lacks depth. Massachusetts economy, the last event, spent A COPY BEFORE maybe ANYTHING! Alexis Ohanian is her biggest cheerleader. Trevor lawrence has dubbed it out in game. Rays then turn to game schedules, watch their judgment on kalamazoo news articles and away this was placing on. Best net touchdowns in all games. If you plan on attending a Blue Jays Bobblehead giveaway game at Rogers Centre, along the NWSL and some soccer leagues in Europe, as a wide disparity in playing caliber had emerged between the East and West divisions. United States and Canada by teams involved in its games. Canada will probably keep the Toronto Raptors in their adopted Tampa, Basketball, the discount policy for Toronto Blue Jays Tickets is exist on. -

74 the Problem of Information War in the Framework of Natural Law
ESTUDIOS LIBERTARIOS VOL. 3. (2020) THE PROBLEM OF INFORMATION WAR IN THE FRAMEWORK OF NATURAL LAW – PARADOX OF TOLERANCE REVISITED IN THE LIGHT (OR DARKNESS) OF SOVIET PROPAGANDA Agnieszka Płonka Abstract In the framework of the natural law, only direct aggression or call to direct aggression may be legally punishable. However, the methods of information war and ideological subversion, while non-violent in the first stages of the long-term subversion process, are intentionally engineered to end in aggression (note: “information war” is here understood as conscious manipulation of cultural perception for future political gains, not cyberwarfare). The paper examines whether it is possible to extend the notion of aggression in the framework of the natural law to include self-defense against ideological subversion. We use the information war tactics carried out in the XX century by the KGB propaganda department (as described by Eastern bloc defectors) as the most incisive example. We show that in order to proceed with defense against such strategies, due to the subtle, stretched in time and mostly psychological nature of propaganda – we would necessarily have to break the natural law ourselves. However, we also argue that for such subversion strategies to be successful, they must be carried out in a society with an already overgrown political system where one group can exert power over another group. Therefore, to ask if we can extend the definition of aggression to information war in the framework of the natural law is meaningless, because for an information war tactic to be successful, the natural law must already be violated in the targeted society. -

Scranton/Wilkes-Barre Railriders Game Notes Scranton/Wilkes-Barre Railriders (20-9) Vs
scranton/wilkes-barre railriders game notes Scranton/Wilkes-Barre RailRiders (20-9) vs. Buffalo Bisons (15-14) G1: RHP Brian Keller (0-0, 3.18 ERA) vs. RHP Jacob Waguespack (1-1, 5.48 ERA) G2: RHP Deivi García (1-1, 4.71 ERA) vs. RHP Nate Pearson (0-2, 7.24 ERA) | Games 30 & 31 | Road Games 14 & 15 | Trenton Thunder Ballpark | Trenton, NJ | June 10, 2021 | First Pitch 5:00 p.m. | last time out... upcoming schedule / results TRENTON, N.J. (June 8, 2021) – The Scranton/Wilkes-Barre RailRiders erased an early 5-0 deficit to defeat the Buffalo Bisons 7-5 in a wild contest on date opponent result Tuesday night at Trenton Thunder Ballpark. June 5 Lehigh Valley L, 9-6 June 6 Lehigh Valley W, 4-3 After a one-hour, 45-minute weather delay to start the game, Zack Britton got the start in an MLB rehab assignment. The left-hander was tagged for four June 8 @ Buffalo (Trenton) W, 7-5 runs in 0.1 innings of work. He allowed a two-run double to Tyler White and a two-run home run to Jared Hoying to stake Buffalo to an early 4-0 lead. June 9 @ Buffalo (Trenton) Postponed Adam Warren allowed one run in 2.2 innings of relief in back of Britton, but the Bisons maintained a 5-0 advantage after the third. In the top of the June 10 @ Buffalo (Trenton) 5:00 p.m. fourth the RailRiders struck for three runs against Anthony Kay. Derek Dietrich drove home Hoy Park with an RBI single, and three batters later, Andrew @ Buffalo (Trenton) Game 2 Velazquez provided a two-run single to narrow the gap to 5-3. -

The Indispensability of Freedom 8Th International Conference the Austrian School of Economics in the 21St Century
The Indispensability of Freedom TITLE 8th International Conference The Austrian School in the 21st Century Federico N. Fernández Barbara Kolm Victoria Schmid (Eds.) Friedrich A.v.Hayek Institut The Indispensability of Freedom 8th International Conference The Austrian School of Economics in the 21st Century Federico N. Fernández Barbara Kolm Victoria Schmid (Eds.) Papers presented on November 13th and 14th, 2019 Published by the Austrian Economics Center and Fundación International Bases www.austriancenter.com www.fundacionbases.org Copyright ©2020 by Friedrich A. v. Hayek Institut, Vienna Federico N. Fernández, Barbara Kolm, and Victoria Schmid (Eds.) All rights reserved. No texts from this book may be reprinted or posted in any form without prior written permission from the copyright holders. Design and composition by Victoria Schmid Cover photo by Anton Aleksenko | Dreamstime.com ISBN: 978-3-902466-17-4 First Edition 2 3 4 Content Austrian Economics Conference 2019 Preface Robert Holzmann 13 The History of the Austrian Economics Conference The Editors 15 Juan Carlos Cachanosky Memorial Lecture I. The Continuing Importance of Misesian Economics Robert Murphy 17 II. Keynote: Geopolitics, Economic Freedom, and Economic Performance Erich Weede 31 1. The Role of Non-Democratic Institutions in a Democracy, according to Montesquieu, Tocqueville, Acton, Popper, and Hayek, Applied to the EU Jitte Akkermans 45 2. Mind with a purpose: a humanistic conversation between Psychology and some postulates of the Austrian School of Economics Silvia Aleman Menduinna 59 3. What Is Wrong With Sustainable Development Goals? Horacio Miguel Arana 71 5 Content 4. A Unique Methodology using the Principles of the Austrian School of Economics – Applied To Investing and Trading Richard Bonugli 83 5. -

Day Tours March 2020
Day Tours March 2020 RSVP Travel Presentation 905- 322-2712 Monday, March 9 or SOLO Exclusive Tour – Picturesque Portugal, October 11 to 20 caaniagara. @ CAA Thorold Office, 6 pm ca/events March 14 Kinky Boots – Based on a true story, Charlie Price, who is struggling to save the men’s shoe factory Saturday inherited from his father, encounters an outrageous idea to create women’s boots for women who are men. A matinee musical performance at the Hamilton Family Theatre Cambridge. Includes lunch Limited at the Old Marina Restaurant. Coach departs at 10 a.m. Leaves Cambridge after the show. $149 March 16 Medieval Times Dinner & Tournament – Chivalry, Rivalry and Revelry! Featuring heroic Monday knights on spirited horses displaying their skills against one another in a series of games, jousting and combat. Held at the castle-like building, next to the CNE grounds. Includes lunch. Limited Coach departs at 11 a.m. Leaves Toronto after the show. $129 Adult $124 Children under 12 March 17 St Patrick’s Day Kitchen Party! – Featuring The Celts and Step-Dancer, Evelyn Mage. Tuesday A high energy show that will have you singing, laughing and tapping your feet, as the kitchen party comes to life. Performance follows an included lunch at Bingemans Conference Centre. Coach departs at 10:30 a.m. Leaves Kitchener after the concert. $120 March 19 Disney on Ice: Worlds of Enchantment – Join Lightning McQueen, Mater and Pixar Cars, with Thursday Buzz Lightyear, Woody from Toy Story, and Ariel from The Little Mermaid. Also, appearing is Arendelle from Disney’s Frozen. -

* Text Features
The Boston Red Sox Tuesday, May 18, 2021 * The Boston Globe Red Sox plan to increase roster versatility soon with promotion of Danny Santana Alex Speier Man-for-all-positions Danny Santana could join the Red Sox roster as soon as the current six-game road trip. Santana has hit .364/.423/.682 with two homers, a double, and a steal in six games with High A Greenville and Triple A Worcester. He has played shortstop, second, third, left, and center in those half-dozen contests. “He’s almost there,” manager Alex Cora said. “We’ve been moving him around all over the place. He’s moving well. “This is a guy, it gives us another alternative. Let’s see where it takes us. We feel good about where he’s at, not only physically, but as a hitter and as a player.” Santana, 30, had an April 30 opt-out in his minor league deal, but he and the Red Sox agreed to push that date into May when the start of his season was delayed by a foot infection in spring training. He’ll remain in Worcester at least through Tuesday, but his ability to move all over the field and switch-hit could prove particularly valuable during Boston’s weekend series against Philadelphia, during which National League rules will be in effect (with no designated hitter). In 2019, Santana hit .283/.324/.534 with 28 homers and 21 steals in 130 games for the Rangers. But in 2020, while limited to 15 games by an elbow injury that ultimately required modified Tommy John surgery in September, his numbers slid to .145/.278/.273. -

7 International League.Pdf
International League INTERNATIONAL LEAGUE 55 South High Street, Suite 202 Dublin, Ohio 43017 (614) 791-9300 www.ILBaseball.com The 2019 season will be the 136th in the history of the International League. There are 14 teams in the circuit that are divided into three divisions: North, South, and West. Each team plays a 140 game schedule from April 4-September 2 this year. The 2019 Triple-A All-Star Game will be held at Southwest University Park in El Paso, TX — home of the El Paso Chihuahuas and Triple-A affiliate of the San Diego Padres. The All-Star break will be July 8-10 with the Home Run Derby on the 8th and the game on 10th. The IL postseason includes four teams: three Division Winners and one Wild Card entry. In the best-of-five first round series, the North Division winner plays the Wild Card winner while the South Division and West Division winners square off. The two teams that emerge from the semifinal round then play in the best-of-five Governors’ Cup Championship Series. The Governors’ Cup champion moves on to play the winner of the Pacific Coast League in the Triple-A Baseball National Championship Game. The 2019 edition of the Triple-A National Championship Game will be played at AutoZone Park in Memphis, TN on September 17. North South West Buffalo (Blue Jays) Charlotte (White Sox) Columbus (Indians) Lehigh Valley (Phillies) Durham (Rays) Indianapolis (Pirates) Pawtucket (Red Sox) Gwinnett (Braves) Louisville (Reds) Rochester (Twins) Norfolk (Orioles) Toledo (Tigers) Scranton/WB (Yankees) Syracuse (Mets) International League Staff Directors Bob Rich Jr.