Forensic Acquisition and Analysis of Volatile Data in Memory
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ENDPOINT MANAGEMENT 1 Information Systems Managers
STAFF SYMPOSIUM SERIES INFORMATION TECHNOLOGY TRACK FACILITATORS Carl Brooks System Manager ‐ Detroit, MI Chapter 13 Standing Trustee – Tammy L. Terry Debbie Smith System Manager – Robinsonville, NJ Chapter 13 Standing Trustee – Al Russo Scot Turner System Manager –Las Vegas, NV Chapter 13 Standing Trustee – Rick Yarnall Tom O’Hern Program Manager, ICF International, Baltimore, MD STACS ‐ Standing Trustee Alliance for Computer Security STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 1 Information Systems Managers Windows 10 Debbie Smith System Manager Regional Staff Symposium ‐ IT Track May 11 and 12, 2017 Las Vegas, NV STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 2 Windows lifecycle fact sheet End of support refers to the date when Microsoft no longer provides automatic fixes, updates, or online technical assistance. This is the time to make sure you have the latest available update or service pack installed. Without Microsoft support, you will no longer receive security updates that can help protect your PC from harmful viruses, spyware, and other malicious software that can steal your personal information. Client operating systems Latest update End of mainstream End of extended or service pack support support Windows XP Service Pack 3April 14, 2009 April 8, 2014 Windows Vista Service Pack 2April 10, 2012 April 11, 2017 Windows 7* Service Pack 1 January 13, 2015 January 14, 2020 Windows 8 Windows 8.1 January 9, 2018 January 10, 2023 Windows 10, July 2015 N/A October 13, 2020 October 14, 2025 * Support for Windows 7 RTM without service packs ended on April 9, 2013. -

Security Now! #664 - 05-22-18 Spectreng Revealed
Security Now! #664 - 05-22-18 SpectreNG Revealed This week on Security Now! This week we examine the recent flaws discovered in the secure Signal messaging app for desktops, the rise in DNS router hijacking, another seriously flawed consumer router family, Microsoft Spectre patches for Win10's April 2018 feature update, the threat of voice assistant spoofing attacks, the evolving security of HTTP, still more new trouble with GPON routers, Facebook's Android app mistake, BMW's 14 security flaws and some fun miscellany. Then we examine the news of the next-generation of Spectre processor speculation flaws and what they mean for us. Our Picture of the Week Security News Update your Signal Desktop Apps for Windows & Linux A few weeks ago, Argentinian security researchers discovered a severe vulnerability in the Signal messaging app for Windows and Linux desktops that allows remote attackers to execute malicious code on recipient systems simply by sending a message—without requiring any user interaction. The vulnerability was accidentally discovered while researchers–amond them Juliano Rizzo–were chatting on Signal messenger and one of them shared a link of a vulnerable site with an XSS payload in its URL. However, the XSS payload unexpectedly got executed on the Signal desktop app!! (Juliano Rizzo was on the beach when the BEAST and CRIME attacks occurred to him.) After analyzing the scope of this issue by testing multiple XSS payloads, they found that the vulnerability resides in the function responsible for handling shared links, allowing attackers to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags. -

Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research
applied sciences Systematic Review Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research Majda Wazzan 1,*, Daniyal Algazzawi 2 , Omaima Bamasaq 1, Aiiad Albeshri 1 and Li Cheng 3 1 Computer Science Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] (O.B.); [email protected] (A.A.) 2 Information Systems Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] 3 Xinjiang Technical Institute of Physics & Chemistry Chinese Academy of Sciences, Urumqi 830011, China; [email protected] * Correspondence: [email protected] Abstract: Internet of Things (IoT) is promising technology that brings tremendous benefits if used optimally. At the same time, it has resulted in an increase in cybersecurity risks due to the lack of security for IoT devices. IoT botnets, for instance, have become a critical threat; however, systematic and comprehensive studies analyzing the importance of botnet detection methods are limited in the IoT environment. Thus, this study aimed to identify, assess and provide a thoroughly review of experimental works on the research relevant to the detection of IoT botnets. To accomplish this goal, a systematic literature review (SLR), an effective method, was applied for gathering and critically reviewing research papers. This work employed three research questions on the detection methods used to detect IoT botnets, the botnet phases and the different malicious activity scenarios. The authors analyzed the nominated research and the key methods related to them. The detection Citation: Wazzan, M.; Algazzawi, D.; methods have been classified based on the techniques used, and the authors investigated the botnet Bamasaq, O.; Albeshri, A.; Cheng, L. -

Technical Brief P2P Iot Botnets Clean AC Font
Uncleanable and Unkillable: The Evolution of IoT Botnets Through P2P Networking Technical Brief By Stephen Hilt, Robert McArdle, Fernando Merces, Mayra Rosario, and David Sancho Introduction Peer-to-peer (P2P) networking is a way for computers to connect to one another without the need for a central server. It was originally invented for file sharing, with BitTorrent being the most famous P2P implementation. Decentralized file-sharing systems built on P2P networking have stood the test of time. Even though they have been used to share illegal pirated content for over 20 years, authorities have not been able to put a stop to these systems. Of course, malicious actors have used it for malware for quite a long time as well. Being able to create and manage botnets without the need for a central server is a powerful capability, mostly because law enforcement and security companies typically take down criminal servers. And since a P2P botnet does not need a central command-and-control (C&C) server, it is much more difficult to take down. From the point of view of defenders, this is the scariest problem presented by P2P botnets: If they cannot be taken down centrally, the only option available would be to disinfect each of the bot clients separately. Since computers communicate only with their own peers, the good guys would need to clean all the members one by one for a botnet to disappear. Originally, P2P botnets were implemented in Windows, but developers of internet-of-things (IoT) botnets do have a tendency to start incorporating this feature into their creations. -

Three Plead Guilty in US to Developing Mirai Botnet
Source: https://internetofbusiness.com/three-plead-guilty-developing-mirai-botnet/ Three plead guilty in US to developing Mirai botnet By Rene Millman - December 18, 2017 Hackers go up before US federal court charged with creating Mirai botnet used in massive DDoS attacks. Three men have pleaded guilty to creating the Mirai IoT botnet, used in distributed denial of service (DDoS) attacks since 2016. A statement released last week by the US Department of Justice, it outlines plea deals and details of the three defendants: Paras Jha, 21, of Fanwood, New Jersey; Josiah White, 20, of Washington, Pennsylvania; and Dalton Norman, 21, of Metairie, Louisiana. The three admitted conspiracy to violate the Computer Fraud & Abuse Act. Jha and Norman also pleaded guilty to building an IoT botnet of 100,000 devices to carry out ‘clickfraud’, an Internet-based scheme that makes it appear that a real user has clicked’ on an advertisement for the purpose of articially generating revenue. In addition, Jha pleaded guilty to a third charge, related to a series of DDoS attacks on the networks of Rutgers University in New Jersey. Read more: Malwar! Hajime IoT botnet ghts back against Mirai Adopted by others The DoJ said the Mirai botnet was created during the summer and autumn of 2016, and went on to compromise 300,000 IoT devices, such as wireless cameras, routers, and digital video recorders. It added that the defendants’ involvement with the original Mirai variant ended in the fall of 2016, when Jha posted its source code on a criminal forum. Since then, other criminal actors have adopted Mirai and used variants in other attacks. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Installing, Using and Testing Microsoft Windows Driver Kit (WDK)
www.installsetupconfig.com Installing, Using and Testing Microsoft Windows Driver Kit (WDK) What do we have in this session? Introduction Installing the WDK The Windows Debuggers Installing Symbols Package The WinDbg Starting WinDbg Verifying WDK Installation Steps on Using WDK and Building Windows Driver from Code Sample Building a Windows Driver Sample Drivers and Services Installing/Registering a Driver Starting a Driver Viewing Driver Output Unloading a Driver Print Devices: Generic Text-Only Driver Sample Useful WDK references: Introduction The Windows machine specification used in this session are: 1. Operating System : Windows XP Pro SP2 2. RAM : 2 GB DDR2 3. HDD : 160++GB 4. Display : 128 MB ATI PCI Express 5. Processor : Intel Core 2 Duo 4400 2.00 GHz The DDK has been superseded by the Windows Driver Kit (WDK). While the DDK can be downloaded openly, you may need to register for free and participate in the respective Microsoft community to download WDK. Microsoft said that the WDK should be used for the following reasons: 1. Use the Windows Vista build environments in the WDK to build drivers that use new features or functionality available only in Windows Vista. 2. Use the Windows Server 2003 build environments in the WDK to build drivers that use new features or functionality available only in Windows Server 2003. 3. Use the Windows XP build environments in the WDK to build drivers that do not use new functionality available only in Windows Vista or only in Windows Server 2003 and that are targeted for either Windows XP or Windows Server 1 www.installsetupconfig.com 2003 and Windows XP. -

Comparing the Utility of User-Level and Kernel-Level Data for Dynamic Malware Analysis
Comparing the utility of User-level and Kernel-level data for Dynamic Malware Analysis A thesis submitted in partial fulfilment of the requirement for the degree of Doctor of Philosophy Matthew Nunes October 2019 Cardiff University School of Computer Science & Informatics i Copyright c 2019 Nunes, Matthew. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”. A copy of this document in various transparent and opaque machine-readable formats and related software is available at http://orca.cf.ac.uk. Dedication ii To my family (blood or otherwise) for their love and support. iii Abstract Dynamic malware analysis is fast gaining popularity over static analysis since it is not easily defeated by evasion tactics such as obfuscation and polymorphism. During dynamic analysis, it is common practice to capture the system calls that are made to better understand the behaviour of malware. System calls are captured by hooking certain structures in the Operating System. There are several hooking techniques that broadly fall into two categories, those that run at user-level and those that run at kernel- level. User-level hooks are currently more popular despite there being no evidence that they are better suited to detecting malware. The focus in much of the literature surrounding dynamic malware analysis is on the data analysis method over the data capturing method. -

Support for Microsoft Office 2007
GE Healthcare Invasive Cardiology Security Website Interventional - Invasive Cardiology Product Group: Interventional Invasive Products Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, Products: SpecialsLab and ComboLab IT/XT/XTi Recording Systems Versions: 6.8.1, 6.8, 6.5.6, 6.5.4, 6.5.3 Subject: Security Information Date: 16-August-2019 Summary The following information is provided to GE Healthcare Technologies customers in regards to known technical security vulnerabilities associated with Mac-Lab® Hemodynamic, CardioLab® Electrophysiology, SpecialsLab and ComboLab IT Recording Systems for Cath Lab, EP Lab and other interventional labs as well as the Centricity® Cardiology Data Management Systems. Security Patch Base Configuration The security patch base configuration of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi product at release is listed within the MLCL Base Configuration under the Hemodynamic, Electrophysiology and Cardiovascular Information Technologies section of the http://www3.gehealthcare.com/en/Support/Invasive_Cardiology_Product_Security website. Process The following actions are taken whenever Microsoft/OEMs releases new security patches: • The Invasive Cardiology Engineering Team performs a security analysis process for supported Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, GE Client Review and INW Server hardware/software. • If a vulnerability meets Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi validation criteria, the vulnerability is communicated through the GEHC Product Security Database and Invasive Cardiology Security Website within Three weeks of the patch release. Page 1 of 88 GE Healthcare/16-August-2019 GE Healthcare • Upon validation of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi vulnerability, the GEHC Product Security Database and Invasive Cardiology Security Website and affected Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi Security Patch Installation Instructions are updated. -
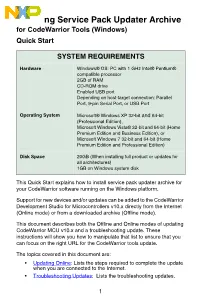
CW MCU V10.X Service Pack Updater
Installing Service Pack Updater Archive for CodeWarrior Tools (Windows) Quick Start SYSTEM REQUIREMENTS Hardware Windows® OS: PC with 1 GHz Intel® Pentium® compatible processor 2GB of RAM CD-ROM drive Enabled USB port Depending on host-target connection: Parallel Port, 9-pin Serial Port, or USB Port Operating System Microsoft® Windows XP 32-bit and 64-bit (Professional Edition), Microsoft Windows Vista® 32-bit and 64-bit (Home Premium Edition and Business Edition), or Microsoft Windows 7 32-bit and 64-bit (Home Premium Edition and Professional Edition) Disk Space 20GB (When installing full product or updates for all architectures) 1GB on Windows system disk This Quick Start explains how to install service pack updater archive for your CodeWarrior software running on the Windows platform. Support for new devices and/or updates can be added to the CodeWarrior Development Studio for Microcontrollers v10.x directly from the Internet (Online mode) or from a downloaded archive (Offline mode). This document describes both the Offline and Online modes of updating CodeWarrior MCU v10.x and a troubleshooting update. These instructions will show you how to manipulate that list to ensure that you can focus on the right URL for the CodeWarrior tools update. The topics covered in this document are: • Updating Online: Lists the steps required to complete the update when you are connected to the Internet. • Troubleshooting Updates: Lists the troubleshooting updates. 1 • Updating Offline: Lists the steps required to complete the update when you are not connected to the Internet. NOTE To ensure successful installation of service packs, updates, and patches select Restart in the File menu to perform a CodeWarrior restart. -

Early Detection of Mirai-Like Iot Bots in Large-Scale Networks Through Sub-Sampled Packet Traffic Analysis
Early Detection Of Mirai-Like IoT Bots In Large-Scale Networks Through Sub-Sampled Packet Traffic Analysis Ayush Kumar and Teng Joon Lim Department of Electrical and Computer Engineering, National University of Singapore, Singapore 119077 [email protected], [email protected] Abstract. The widespread adoption of Internet of Things has led to many secu- rity issues. Recently, there have been malware attacks on IoT devices, the most prominent one being that of Mirai. IoT devices such as IP cameras, DVRs and routers were compromised by the Mirai malware and later large-scale DDoS at- tacks were propagated using those infected devices (bots) in October 2016. In this research, we develop a network-based algorithm which can be used to detect IoT bots infected by Mirai or similar malware in large-scale networks (e.g. ISP network). The algorithm particularly targets bots scanning the network for vul- nerable devices since the typical scanning phase for botnets lasts for months and the bots can be detected much before they are involved in an actual attack. We analyze the unique signatures of the Mirai malware to identify its presence in an IoT device. The prospective deployment of our bot detection solution is discussed next along with the countermeasures which can be taken post detection. Further, to optimize the usage of computational resources, we use a two-dimensional (2D) packet sampling approach, wherein we sample the packets transmitted by IoT devices both across time and across the devices. Leveraging the Mirai signatures identified and the 2D packet sampling approach, a bot detection algorithm is pro- posed. -

Why Choose Wisetrustboot?
Connected devices require protection against the ever increasing threat of cyber-attacks. WISeTrustBoot will do just that. Embedding WISeTrustBoot in conjunction with WISeKey’s tamper resistant Secure Element VaultIC in a device will protect it against modification of its function, against botnets such as Mirai, Brickerbot or Hajime, ensures the data exchange with the device is not compromised and protects your business against device cloning. WISeTrustBoot does this by building a chain of trust, cryptographically validating every step of the chain, from boot until transmission of data. Additionally, it provides a mechanism to securely download and install updated versions of the firmware. WISeTrustBoot combines the strength of a tamper resistant chip, Chain of Trust state-of-the-art crypto libraries Why choose and strong digital signatures WISeTrustBoot? based on WISeKey’s recognized Authentic Integrity Trusted Authentic Authentic experience in Public Key Device Protected Boot Device Data Firmware Data Infrastructure Services and secure chip technology Examples of malware that can be avoided WISeTrustBoot provides Internet of Things: when using WISeTrustBoot full protection against Mirai Brickerbot Spectre and Meltdown malware on embedded Industry 4.0 Mirai was a malicious piece Brickerbot was a malware Discovered in early 2018, Utilities, smart grid connected devices: of software code, or Bot that that, once infecting a device, these two exploits use Building security, video targeted low cost consumer started to destroy it by vulnerabilities in widely Trusted Boot surveillance cameras… devices such as video deleting the data in storage implemented microprocessors and disconnecting it from the of for example personal Firmware signature validation cameras. A large number Smart Cities (street lighting, of these Bots where used network.