Exploring New Attack Vectors for the Exploitation of Smartphones
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Texting on a Smartwatch Versus a Smartphone: a Comparison of Their Effects on Driving Performance
TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE A Dissertation by Joel Persinger Master of Arts, Wichita State University, 2014 Bachelor of Science, Eastern Kentucky University, 2005 Submitted to the Department of Psychology and the faculty of the Graduate School of Wichita State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy December 2017 ©Copyright 2017 by Joel A. Persinger All Rights Reserved TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE The following faculty members have examined the final copy of this dissertation for form and content, and recommend that it be accepted in partial fulfillment of the requirement for the degree of Doctor of Philosophy, with a major in Psychology. _____________________________________________ Rui Ni, Committee Chair _____________________________________________ Alex Chaparro, Committee Member _____________________________________________ Barbara Chaparro, Committee Member _____________________________________________ Jibo He, Committee Member _____________________________________________ Jeremy Patterson, Committee Member Accepted for the College of Liberal Arts and Sciences _______________________________________________ Ron Matson, Dean Accepted for the Graduate School _______________________________________________ Dennis Livesay, Dean iii DEDICATION To my beautiful wife, who has pushed me to go further than I ever thought I could. She has truly carried me though graduate school with love and encouragement. iv ABSTRACT The National Safety Council reports that 6 percent or more car crashes involved text messaging from a smartphone. In addition, many studies have found that cell phone while driving increases crash risk by 2.8–5 times (Klauer et al. 2006; Redelmeier and Tibshirani 1997; Violanti 1998; Violanti and Marshall 1996). -
Your HTC One® VX User Guide 2 Contents Contents
Your HTC One® VX User guide 2 Contents Contents Unboxing HTC One VX 10 Back cover 11 SIM card 13 Storage card 14 Charging the battery 15 Switching the power on or off 15 Setting up your phone Setting up HTC One VX for the first time 17 Home screen 17 Getting contacts into HTC One VX 18 Transferring contacts from your old phone through Bluetooth 19 Getting photos, videos, and music on or off HTC One VX 19 Getting to know your settings 20 Updating the HTC One VX software 20 Your first week with your new phone Features you'll enjoy on HTC One VX 22 Touch gestures 24 Motion gestures 27 Sleep mode 29 Unlocking the screen 30 Making your first call 30 Sending your first text message 31 The HTC Sense keyboard 31 Notifications 31 Copying and sharing text 34 Capturing the HTC One VX screen 35 Switching between recently opened apps 35 Can't find the Menu button? 35 Checking battery usage 36 Camera Camera basics 37 Taking a photo 38 Recording video 38 Keeping the camera on standby 39 Taking continuous camera shots 39 3 Contents Camera scenes 40 Improving portrait shots 40 Taking a group shot 40 Taking a panoramic photo 40 Using HDR 41 Recording videos in slow motion 41 Improving video stability 41 Changing camera and video settings 42 Personalizing Making HTC One VX truly yours 43 Personalizing HTC One VX with scenes 43 Changing your wallpaper 44 Applying a new skin 45 Personalizing your Home screen with widgets 45 Adding apps and other shortcuts on your Home screen 46 Rearranging or removing widgets and icons on your Home screen 47 Personalizing -

Trusense: Information Leakage from Trustzone
TruSense: Information Leakage from TrustZone Ning Zhang∗, Kun Suny, Deborah Shandsz Wenjing Lou∗z, Y. Thomas Hou∗ ∗Virginia Polytechnic Institute and State University, VA yGeorge Mason University, Fairfax, VA zNational Science Foundation, Arlington, VA Abstract—With the emergence of Internet of Things, mobile Unlike software exploitations that target vulnerabilities in devices are generating more network traffic than ever. TrustZone the system, side-channel attacks target information leakage of is a hardware-enabled trusted execution environment for ARM a physical implementation via its interactions with the execu- processors. While TrustZone is effective in providing the much- needed memory isolation, we observe that it is possible to derive tion environment. Side-channel information can be obtained secret information from secure world using the cache contention, from different types of physical features, such as power [10], due to its high-performance cache sharing design. electromagnetic wave [11], acoustic [12] and time [13], [14], In this work, we propose TruSense to study the timing-based [15]. Among these side channels, the cache-based timing cache side-channel information leakage of TrustZone. TruSense attack is one of the most important areas of research [14], can be launched from not only the normal world operating system but also a non-privileged user application. Without access [15], [16], [8], [17], [18]. to virtual-to-physical address mapping in user applications, we Processor cache is one of the basic components in mod- devise a novel method that uses the expected channel statistics ern memory architecture to bridge the gap between the fast to allocate memory for cache probing. -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations. -

Apple and Nokia: the Transformation from Products to Services
9 Apple and Nokia: The Transformation from Products to Services In the mid- to late 2000s, Nokia flourished as the world’s dominant mobile phone – and mobile phone operating software – producer. Founded in 1871 originally as a rubber boots manufacturer, by 2007 Nokia produced more than half of all mobile phones sold on the planet, and its Symbian mobile operating system commanded a 65.6 percent global market share. 1 But within half a decade, Nokia would falter and be surpassed in the smartphone market not only by Apple’s revolu- tionary iPhone but also by competitors including Google and Samsung. And in September 2013, Nokia would sell its mobile phone business to Microsoft for $7 billion. 2 Apple literally came out of nowhere – it sold exactly zero mobile phones before the year 2007 (the year Nokia held more than half of the global market share) – but by the first quarter of 2013, Apple had captured almost 40 percent of the US smartphone market and over 50 percent of the operating profit in the global handset industry.3 In fiscal year 2013, Apple would sell five times more smart- phones than Nokia: 150 million iPhones compared to Nokia’s sales of 30 million Lumia Windows phones. 4 In contrast to Nokia, Apple real- ized it wasn’t just about the mobile device itself, it was about leveraging software to create a platform for developing compelling mobile experi- ences – including not just telephony but also music, movies, applica- tions, and computing – and then building a business model that allows partners to make money alongside the company (e.g., Apple’s iTunes and AppStore) and, in so doing, perpetuate a virtuous cycle of making the iPhone attractive to customers over multiple life cycles through ever-ex- panding feature sets. -

UI Design for Wearable Devices
FACULTY OF ENGINEERING UNIVERSITY OF PORTO UI Design for Wearable Devices Vitor Mota Master in Informatics and Computing Engineering Supervised by: Miguel Pimenta Monteiro (Assistant professor) Pedro Rocha (GlinttHS) January 2015 2 Abstract Smartwatches have been around for some time now (Ranger 2015), but 2015 is the year this wearable technology will finally get its boom in terms of popularity and growth. Technology giants like Apple, Google and Samsung are betting on their own-line of products such as the Apple Watch, Android Wear and Gear respectively (Apple Inc 2015a; Google Inc 2015b; SAMSUNG 2015). All of these devices are computation capable electronics with very small touch capacitive screens, limited number of hardware buttons with varying screen sizes and even shapes. Our research focused mainly on these constraints and how to successfully develop user friendly GUI’s for such small screens. The goal was to develop a model with guidelines to help developers provide easy to use and user friendly applications at a visual and interaction level to end users. To successfully achieve this, we first took a deep look at the available technology within these devices, including the framework each of the major platforms provide and the underlying hardware capabilities such as sensors like GPS, gyroscope, the use of the touch screen or microphone for user input and whether the shape of the device (round or squared) can have different effects on the design and usability. We also analyzed the impact of placement and arrangement of interface components having in mind that this technology, since it is a wearable watch, can be worn on both wrists and therefore will be used with only one hand that may obscure a different portion of the interface depending on which wrist the user uses it (Chandra and Raghunath 2000). -

Characterizing Smartwatch Usage in the Wild
Characterizing Smartwatch Usage In The Wild Xing Liu1 Tianyu Chen1 Feng Qian1 Zhixiu Guo23 Felix Xiaozhu Lin4 Xiaofeng Wang1 Kai Chen25 1Indiana University Bloomington 2SKLOIS, Institute of Information Engineering, Chinese Academy of Sciences 3Beijing Jiaotong University 4Purdue ECE 5School of Cyber Security, University of Chinese Academy of Sciences ABSTRACT participants, we conduct an in-depth characterization of three key Smartwatch has become one of the most popular wearable aspects of smartwatch usage “in the wild”: usage patterns, energy computers on the market. We conduct an IRB-approved consumption, and network traffic characteristics. This is to our measurement study involving 27 Android smartwatch users. Using knowledge the most comprehensive and in-depth crowd-sourced a 106-day dataset collected from our participants, we perform in- study of smartwatches. Our key measurement results consist of depth characterization of three key aspects of smartwatch usage “in the following. the wild”: usage patterns, energy consumption, and network traffic. • We characterize the smartwatch usage patterns. An Android Based on our findings, we identify key aspects of the smartwatch watch can stay in one of the four states with diverse power ecosystem that can be further improved, propose recommendations, characteristics: fully awake, dozing (with dimmed watch face and point out future research directions. display and restricted system activity), sleeping (screen further turned off), and charging. We find that smartwatch’s wake-up CCS Concepts period accounts for only 2% of the overall usage period among • → the four states. The wake-up sessions are not only short, but Human-centered computing Ubiquitous and mobile also frequent (72 times per day on average). -

Digital Forensic Analysis of Smart Watches
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Kehinde Omotola Adebayo (174449IVSB) DIGITAL FORENSIC ANALYSIS OF SMART WATCHES Bachelor’s Thesis Supervisor: Hayretdin Bahsi Research Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Kehinde Omotola Adebayo (174449IVSB) NUTIKELLADE DIGITAALKRIMINALISTIKA Bachelor’s Thesis Juhendaja: Hayretdin Bahsi Research Professor Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Kehinde Omotola Adebayo 30.04.2020 3 Abstract As wearable technology is becoming increasingly popular amongst consumers and projected to continue to increase in popularity they become probable significant source of digital evidence. One category of wearable technology is smart watches and they provide capabilities to receive instant messaging, SMS, email notifications, answering of calls, internet browsing, fitness tracking etc. which can be a great source of digital artefacts. The aim of this thesis is to analyze Samsung Gear S3 Frontier and Fitbit Versa Smartwatches, after which we present findings alongside the limitations encountered. Our result shows that we can recover significant artefacts from the Samsung Gear S3 Frontier, also more data can be recovered from Samsung Gear S3 Frontier than the accompanying mobile phone. We recovered significant data that can serve as digital evidence, we also provided a mapping that would enable investigators and forensic examiners work faster as they are shown where to look for information in the course of an investigation. We also presented the result of investigating Fitbit Versa significant artefacts like Heart rate, sleep, exercise and personal data like age, weight and height of the user of the device, this shows this device contains artefacts that might prove useful for forensic investigators and examiners. -
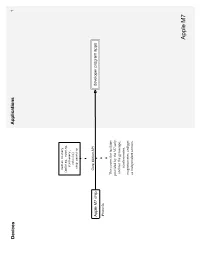
API Diagrams
Devices Applications 1 motion history (walking, running, stationary, vehicle) step counting Core Motion API Apple M7 chip developer program apps iPhone 5s This covers the facilities provided by the M7 only, and not the gyroscope, accelerometer, magnetometer, and gps as independent sensors. Apple M7 Devices Applications Services 2 Runkeeper Argus Fitbit bluetooth 4.0 Withings LifeTrak Move C300 iOS Argus uses each New Balance LifeTRNr Watches services’ Pebble SmartWatch Sleep Time respective API. Mio Alpha Data is only viewable in the Wahoo Blue HR Heart Rate Strap iOS/Android Argus app, not in the website Stress Check iOS/Android Instant Heart Rate CSV Azumio cloud CSV premium feature or text iOS/Android/Windows table Phone/Windows 8 Cardio Buddy Data is not available for for Argus (steps only), iOS viewing from website, but Instant Heart Rate, Stress can sync to multiple Check and Sleep Time devices. Instant Fitness iOS CSV or text Fitness Buddy table iOS/Android text Glucose Buddy CSV table Glucose Buddy iOS/Android Azumio Devices Applications Services 3 Viera is Panasonic’s Smart TV platform that runs 3rd- party apps App requires Link Armband armband and API is active to subscription current developers but closed off to activity Bluetooth 2.0 new development heart rate food sleep BodyMedia FIT nutrients steps iOS/Android/Viera BodyMedia FIT API partner Armband Advantage Activity Manager program USB web dashboard BodyMedia SYNC Jawbone UP API apps Windows/Mac The desktop software only location CORE Armband transfers data to the registered image “Activity Manager” developers cardiac service. It does not allow oauth 2.0 food users to view data json goals mood activity sleep RF workout Since the armbands do not have displays, the Display Device is a Display way to show the data. -
Winnovative HTML to PDF Converter for .NET
Convert iTunes Movies to Android Tablets &Phones TunesKit for Mac For Windows Buy Resource Tutorial Support How to Convert iTunes Movies to Android Phones and Tablets Posted by Andy Miller on August 22, 2014 11:05:35 AM. iTunes as the world's biggest digital content store, also attracts many android fans to buy or rent movies, songs or iBooks here. However, the problems come up when they realized the DRM protection existing. All Apple movies are copy protected by Fairplay DRM protection. The consumers are not allowed to transfer their purchased or rented movies to any Non‐apple devices, of course including the Android phones and tablets. What to do if the android fans want to watch the iTunes movies to their Samsung Galaxy S5 or Galaxy Tab/Note, orHTC one M8, or even Amazon Kindle Fire? You know all these Android devices' screen is larger than iPhone. Crack iTunes DRM and Convert iTunes Movies to Android Devices To convert and transfer the iTunes purchased or rented movies to our android phones or tablets, we have to remove the DRM from iTunes movies at first. TunesKit iTunes DRM Media Converter is a great choice to help you accomplish your task. With TunesKit DRM Media Converter, we can easily get rid of the Fairplay DRM protection from both iTunes purchased and rented movies/TV shows. It converts iTunes DRMed M4V to common MP4 format which can be supported by any android phones and tablets well. The important reason we recommend it is that it can do this work very fast, nearly 20x faster than other similar application. -

Factors Influencing the Adoption of Smart Wearable Devices
Scholars' Mine Masters Theses Student Theses and Dissertations Spring 2016 Factors influencing the adoption of smart wearable devices Apurva Adapa Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Technology and Innovation Commons Department: Recommended Citation Adapa, Apurva, "Factors influencing the adoption of smart wearable devices" (2016). Masters Theses. 7492. https://scholarsmine.mst.edu/masters_theses/7492 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. FACTORS INFLUENCING THE ADOPTION OF SMART WEARABLE DEVICES by APURVA ADAPA A THESIS Presented to the faculty of the Graduate School of the MISSOURI UNIVERSITY OF SCIENCE AND TECHNOLOGY In Partial Fulfillment of the Requirements for the Degree MASTER OF SCIENCE IN INFORMATION SCIENCE AND TECHNOLOGY 2016 Approved by Dr. Fiona Fui Hoon Nah, Advisor Dr. Keng L. Siau Dr. Richard Hall Copyright 2016 Apurva Adapa All Rights Reserved iii ABSTRACT This study aims to examine the factors and issues in adoption of smart wearable devices. Wearable devices have many functions to offer which make them very useful in our daily lives. However, factors influencing the adoption of these devices are not well understood. This research explores the inhibiting and contributing factors influencing the adoption of wearable devices by employing the laddering approach. Qualitative data were collected through in-depth interviews using the laddering technique in order to understand these factors. -

130 Demystifying Arm Trustzone: a Comprehensive Survey
Demystifying Arm TrustZone: A Comprehensive Survey SANDRO PINTO, Centro Algoritmi, Universidade do Minho NUNO SANTOS, INESC-ID, Instituto Superior Técnico, Universidade de Lisboa The world is undergoing an unprecedented technological transformation, evolving into a state where ubiq- uitous Internet-enabled “things” will be able to generate and share large amounts of security- and privacy- sensitive data. To cope with the security threats that are thus foreseeable, system designers can find in Arm TrustZone hardware technology a most valuable resource. TrustZone is a System-on-Chip and CPU system- wide security solution, available on today’s Arm application processors and present in the new generation Arm microcontrollers, which are expected to dominate the market of smart “things.” Although this technol- ogy has remained relatively underground since its inception in 2004, over the past years, numerous initiatives have significantly advanced the state of the art involving Arm TrustZone. Motivated by this revival ofinter- est, this paper presents an in-depth study of TrustZone technology. We provide a comprehensive survey of relevant work from academia and industry, presenting existing systems into two main areas, namely, Trusted Execution Environments and hardware-assisted virtualization. Furthermore, we analyze the most relevant weaknesses of existing systems and propose new research directions within the realm of tiniest devices and the Internet of Things, which we believe to have potential to yield high-impact contributions in the future. CCS Concepts: • Computer systems organization → Embedded and cyber-physical systems;•Secu- rity and privacy → Systems security; Security in hardware; Software and application security; Additional Key Words and Phrases: TrustZone, security, virtualization, TEE, survey, Arm ACM Reference format: Sandro Pinto and Nuno Santos.