IYIR for HTML
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shaping Choices in the Digital World
IP REPORTS INNOVATION AND FORESIGHT N°06 Shaping Choices in the Digital World January 2019 Commission Nationale de l’Informatique et des Libertés From dark patterns to data protection: 3 place de Fontenoy TSA 80715 the influence of ux/ui design on user empowerment 75334 PARIS CEDEX 07 Tél. +33 (0)1 53 73 22 22 [email protected] www.cnil.fr linc.cnil.fr SHAPING CHOICES IN THE DIGITAL WORLD EDITORIAL 1 People live with all kinds of digital objects. These range from social networks to cutting-edge connected objects. They are now a fully-fledged part of our aesthetic relationship with the world, on a par with architecture or decorative art. A certain widely distributed and highly standardised aesthetic of digital media has been created, producing strong brands in users’ minds. Users are barely aware of this aesthetic, which is well thought out. Conditioning through design pre-empts everything that the individual handles or sees in the digital world. In the wake of Bauhaus, where design is based on the search for functional aesthetics, digital technology has become a relevant field of application in EDITORIAL problem-solving. For, beyond the desire to avoid ugliness that “does not sell”, to quote Raymond Loewy, the digital promise is so broad that the functions provided by design seem endless, giving the key players that own them the expectation of a substantial return on investment. Web giants have understood this by competing to attract users, customising their experience, influencing – as subtly and as substantially as possible – their behaviour, in all fields, from leisure to politics. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Analisi Del Progetto Mozilla
Università degli studi di Padova Facoltà di Scienze Matematiche, Fisiche e Naturali Corso di Laurea in Informatica Relazione per il corso di Tecnologie Open Source Analisi del progetto Mozilla Autore: Marco Teoli A.A 2008/09 Consegnato: 30/06/2009 “ Open source does work, but it is most definitely not a panacea. If there's a cautionary tale here, it is that you can't take a dying project, sprinkle it with the magic pixie dust of "open source", and have everything magically work out. Software is hard. The issues aren't that simple. ” Jamie Zawinski Indice Introduzione................................................................................................................................3 Vision .........................................................................................................................................4 Mozilla Labs...........................................................................................................................5 Storia...........................................................................................................................................6 Mozilla Labs e i progetti di R&D...........................................................................................8 Mercato.......................................................................................................................................9 Tipologia di mercato e di utenti..............................................................................................9 Quote di mercato (Firefox).....................................................................................................9 -

Manual De Firefox Instalación Y Uso
Manual de Firefox Instalación y uso Servicio de Información Mesoamericano de Agricultura Sostenible ÍNDICE ¿Qué es Firefox? ....................................... 3 ¿Cómo lo descargo a mi computadora?............................... 4 Instalación ....................................... 5 Comenzar a utilizar Mozilla Firefox ....................................... 8 Elementos para Navegar ....................................... 9 Pestañas de Navegación ....................................... 11 Uso de Marcadores ....................................... 12 Guardar y extraer información ....................................... 15 Historial ....................................... 15 Establecer Preferencias ....................................... 16 Temas y Extenxiones para Mozilla Firefox............................. 18 Unidad de Informática 2 ¿Qué es Firefox? Firefox es una de las aplicaciones gratuitas que se pueden utilizar para navegar en Internet. Seguramente el lector utilice Internet Explorer que es el navegador más conocido y utilizado, pero no el mejor. Basado en Mozilla, el proyecto Firefox nació, a finales de 2002, orientado a usuarios no técnicos. Fue pasando por diversos nombres (Phoenix, Firebird) hasta tomar la denominación actual. Cabe destacar que se trata de un proyecto ‘Open Source’ (Código Abierto), lo que supone que cualquier desarrollador puede modificar el código para mejorarlo. Este pequeño manual le enseñará a instalar y utilizar Firefox en una computadora con sistema operativo Windows. ¿Por qué debo usar Firefox? Hay -

John Athayde and Bruce Williams — «The Rails View
What readers are saying about The Rails View This is a must-read for Rails developers looking to juice up their skills for a world of web apps that increasingly includes mobile browsers and a lot more JavaScript. ➤ Yehuda Katz Driving force behind Rails 3.0 and Co-founder, Tilde In the past several years, I’ve been privileged to work with some of the world’s leading Rails developers. If asked to name the best view-layer Rails developer I’ve met, I’d have a hard time picking between two names: Bruce Williams and John Athayde. This book is a rare opportunity to look into the minds of two of the leading experts on an area that receives far too little attention. Read, apply, and reread. ➤ Chad Fowler VP Engineering, LivingSocial Finally! An authoritative and up-to-date guide to everything view-related in Rails 3. If you’re stabbing in the dark when putting together your Rails apps’ views, The Rails View provides a big confidence boost and shows how to get things done the right way. ➤ Peter Cooper Editor, Ruby Inside and Ruby Weekly The Rails view layer has always been a morass, but this book reins it in with details of how to build views as software, not just as markup. This book represents the wisdom gained from years’ worth of building maintainable interfaces by two of the best and brightest minds in our business. I have been writing Ruby code for over a decade and Rails code since its inception, and out of all the Ruby books I’ve read, I value this one the most. -

Mozilla Source Tree Docs Release 50.0A1
Mozilla Source Tree Docs Release 50.0a1 August 02, 2016 Contents 1 SSL Error Reporting 1 2 Firefox 3 3 Telemetry Experiments 11 4 Build System 17 5 WebIDL 83 6 Graphics 85 7 Firefox for Android 87 8 Indices and tables 99 9 Localization 101 10 mach 105 11 CloudSync 113 12 TaskCluster Task-Graph Generation 119 13 Crash Manager 133 14 Telemetry 137 15 Crash Reporter 207 16 Supbrocess Module 211 17 Toolkit modules 215 18 Add-on Manager 221 19 Linting 227 20 Indices and tables 233 21 Mozilla ESLint Plugin 235 i 22 Python Packages 239 23 Managing Documentation 375 24 Indices and tables 377 Python Module Index 379 ii CHAPTER 1 SSL Error Reporting With the introduction of HPKP, it becomes useful to be able to capture data on pin violations. SSL Error Reporting is an opt-in mechanism to allow users to send data on such violations to mozilla. 1.1 Payload Format An example report: { "hostname":"example.com", "port":443, "timestamp":1413490449, "errorCode":-16384, "failedCertChain":[ ], "userAgent":"Mozilla/5.0 (X11; Linux x86_64; rv:36.0) Gecko/20100101 Firefox/36.0", "version":1, "build":"20141022164419", "product":"Firefox", "channel":"default" } Where the data represents the following: “hostname” The name of the host the connection was being made to. “port” The TCP port the connection was being made to. “timestamp” The (local) time at which the report was generated. Seconds since 1 Jan 1970, UTC. “errorCode” The error code. This is the error code from certificate veri- fication. Here’s a small list of the most commonly-encountered errors: https://wiki.mozilla.org/SecurityEngineering/x509Certs#Error_Codes_in_Firefox In theory many of the errors from sslerr.h, secerr.h, and pkixnss.h could be encountered. -

Click Fraud,' Personal, Non-Commercial Use Only
April 6, 2005 PAGE ONE Traffic Jam DOW JONES REPRINTS This copy is for your In 'Click Fraud,' personal, non-commercial use only. To order presentation-ready copies Web Outfits Have for distribution to your colleagues, clients or customers, use the Order A Costly Problem Reprints tool at the bottom of any article or visit: www.djreprints.com. Marketers Worry About Bills Inflated by People Gaming • See a sample reprint in PDF format . The Search-Ad System • Order a reprint of this article now. Mr. McKelvey Turns Detective RELATED ARTICLE By KEVIN J. DELANEY • Internet Firms Face Legal Test on Staff Reporter of THE WALL STREET JOURNAL Advertising Fees3 April 6, 2005; Page A1 Nathan McKelvey began to worry about foul play when Yahoo Inc. refunded him $69.28 early last year. He grew more suspicious when a $16.91 refund arrived from Google Inc. The refunds were for "unusual clicks" and "invalid click activity" and they suggested someone was sabotaging Mr. McKelvey's advertising strategy. He pitches his charter-jet brokerage the way companies increasingly do: contracting with Yahoo and Google to serve up small text ads to anyone searching the Web using certain words, such as "private jet" or "air charter." He pays the search companies a fee every time someone clicks on his ads. But Yahoo and Google determined someone was clicking on CharterAuction.com Inc.'s ads with no intention of doing business, thus unfairly driving up the company's advertising costs. Mr. McKelvey, turning detective, combed through lists of "IP" addresses, the identifying codes supplied by computers when they access Web sites. -

Mozilla, the European Perspective
Mozilla, the European perspective Pascal Chevrel Mozilla Europe October 09 TheThe MozillaMozilla structurestructure Project led by a non-profit: Mozilla Foundation 2 direct subsidiaries: Mozilla Corporation (Web and labs) Mozilla Messaging (Thunderbird) 3 regional affiliates Mozilla Europe Mozilla Japan Mozilla China AA fewfew factsfacts aboutabout MozillaMozilla inin EuropeEurope 45% of Firefox users are in Europe (~150 million) ~32% market share in Europe (vs 23% world) Regional affiliate to Mozilla (Mozilla Europe) Firefox in 41 European languages Dynamic professional market based on the Mozilla platform or using pieces of it (Mozdev Group, Zoomorama, Briks, Glaxstar, Disruptive Innovations, TomTom, 3Liz, Nokia...) France:France: aa fertilefertile fieldfield forfor MozillaMozilla Strong and organized community of developers building applications with the Mozilla platform Organized community with several not for profit organizations (frenchmozilla, geckozone, xulfr) Mozilla Europe is based in Paris Professional market for Xul outside of Firefox add- ons (intranet applications, large scale deployments of Firefox/Thunderbird, industry applications...) TheThe EuropeanEuropean MozillaMozilla CommunityCommunity EuropeanEuropean eventsevents onon MozillaMozilla TechnologiesTechnologies Two annual European-wide meetings for Mozilla 1. FOSDEM, in Université Libre de Bruxelles 2. MozCamp Europe + Direct education outreach with Mozilla Add-ons Workshops across Europe WhyWhy MozillaMozilla EducationEducation inin Europe?Europe? The Mozilla project values are based on sharing of knowledge and meritocracy, values shared with Education Open Source is quickly gaining acceptance both in the industry and the public sector in Europe, making Mozilla technologies an asset on the job market The Web was invented in Europe in CERN ! MMTCMMTC coursecourse inin Madrid,Madrid, 20092009 CollaborationCollaboration withwith URJCURJC A 3 months course online, started with a one week live session of teaching in Madrid. -

Clickjacking: Attacks and Defenses
Clickjacking: Attacks and Defenses Lin-Shung Huang Alex Moshchuk Helen J. Wang Carnegie Mellon University Microsoft Research Microsoft Research [email protected] [email protected] [email protected] Stuart Schechter Collin Jackson Microsoft Research Carnegie Mellon University [email protected] [email protected] Abstract such as a “claim your free iPad” button. Hence, when Clickjacking attacks are an emerging threat on the web. the user “claims” a free iPad, a story appears in the user’s In this paper, we design new clickjacking attack variants Facebook friends’ news feed stating that she “likes” the using existing techniques and demonstrate that existing attacker web site. For ease of exposition, our description clickjacking defenses are insufficient. Our attacks show will be in the context of web browsers. Nevertheless, the that clickjacking can cause severe damages, including concepts and techniques described are generally applica- compromising a user’s private webcam, email or other ble to all client operating systems where display is shared private data, and web surfing anonymity. by mutually distrusting principals. We observe the root cause of clickjacking is that an Several clickjacking defenses have been proposed and attacker application presents a sensitive UI element of a deployed for web browsers, but all have shortcomings. target application out of context to a user (such as hiding Today’s most widely deployed defenses rely on frame- the sensitive UI by making it transparent), and hence the busting [21, 37], which disallows a sensitive page from user is tricked to act out of context. To address this root being framed (i.e., embedded within another web page). -

Online Advertising Security: Issues, Taxonomy, and Future Directions
IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. XX, NO. NN, XX 2021 1 Online Advertising Security: Issues, Taxonomy, and Future Directions Zahra Pooranian, Senior Member, IEEE, Mauro Conti, Senior Member, IEEE, Hamed Haddadi, Member, IEEE and Rahim Tafazolli, Senior Member, IEEE Abstract—Online advertising has become the backbone of over time. Also, mobile advertising has become one of the the Internet economy by revolutionizing business marketing. It fastest-growing industries with the advent of smartphones [6]. provides a simple and efficient way for advertisers to display Millions of mobile applications are registered in various ap- their advertisements to specific individual users, and over the last couple of years has contributed to an explosion in the plication platforms such as Google Play Store, Apps Store, income stream for several web-based businesses. For example, etc., which contain at least one advertising library that allows Google’s income from advertising grew 51.6% between 2016 and mobile advertising [7]. According to [8], in 2019, total mobile 2018, to $136.8 billion. This exponential growth in advertising advertising spending worldwide has reached $189 billion and revenue has motivated fraudsters to exploit the weaknesses of will surpass $240 billion by 2022. the online advertising model to make money, and researchers to discover new security vulnerabilities in the model, to propose Online advertising uses the same mechanisms that are countermeasures and to forecast future trends in research. applied to manage other “traditional” advertising channels, Motivated by these considerations, this paper presents a such as newspapers, radio or TV, but is much more creative in comprehensive review of the security threats to online advertising providing targeted and personalized advertisements [9], [10]. -

UI Redressing and Clickjacking: About Click Fraud and Data Theft
Introduction Attack vectors Counteractive measures Conclusion and outlook UI Redressing and Clickjacking: About click fraud and data theft Marcus Niemietz [email protected] Ruhr-University Bochum Chair for Network and Data Security 25th of November 2011 Marcus Niemietz, RUB @Zeronights UI Redressing and Clickjacking Introduction Attack vectors Counteractive measures Conclusion and outlook Short and crisp details about me Studying \IT-Security/Information Technology", RUB \Computer Science", Distance University Hagen B.Sc. in \IT-Security/Information Technology" Books Authentication Web Pages with Selenium ≥Feb. 2012: Clickjacking und UI-Redressing International speaker Work: RUB, Pixelboxx, ISP and IT-Security, Freelancer (trainings, penetration tests) Twitter: @mniemietz Marcus Niemietz, RUB @Zeronights UI Redressing and Clickjacking Introduction Attack vectors Counteractive measures Conclusion and outlook Contents 1 Introduction UI redressing Clickjacking 2 Attack vectors UI redressing Round up Clickjacking Tool 3 Counteractive measures Frame busting Busting frame busting Clickjacking statistics 4 Conclusion and outlook Marcus Niemietz, RUB @Zeronights UI Redressing and Clickjacking Introduction Attack vectors UI redressing Counteractive measures Clickjacking Conclusion and outlook Introduction Google Inc. can generate a profit of over $8.5 billion in 2010 Interesting for commercial companies to offer web applications shopping banking share status messages New attacks available that can bypass existing protection mechanisms CSRF -
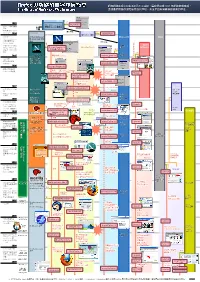
Firefox 與網路瀏覽器發展簡史 網際網路在現今的生活中已不可或缺,讓我們回溯 1993 年網路黎明時期, the History of Firefox and Web Browsers 透過最常接觸的瀏覽器其進化歷程,來逐步回顧網際網路發展的歷史。
Firefox 與網路瀏覽器發展簡史 網際網路在現今的生活中已不可或缺,讓我們回溯 1993 年網路黎明時期, The History of Firefox and Web Browsers 透過最常接觸的瀏覽器其進化歷程,來逐步回顧網際網路發展的歷史。 NCSA 發行 Marc Andreessen 等人 NCSA Mosaic 離開 ‧Mosaic 席捲瀏覽器 開發出 Mosaic 瀏覽器 市場 ‧台灣 最 初 的 WWW Server 出現 提供授權 發行 Mosaic Spyglass Spyglass Mosaic Communications 取得 Mosaic 授權 .W3C 成立 由 Marc Andreessen Microsoft Apple .Netscape Navigator 及 James Clark 共同 席捲瀏覽器市場 設立 發行 提供授權 分頁瀏覽功能的原型 .Yahoo! JP上線 .台灣首家 ISP 新絲 取得 Mosaic Opera 路成立、Hinet 成立 Netscape Navigator 1.0 Mozilla Classic 授權 Software .教育部 TWNIC 計畫 開發代號「Mozilla」 發行 開始 發行 Windows 95 開始支援 JavaScript Internet Explorer 1.0 發行 ‧Java 登場 因 NCSA 抗議 發展 ‧網路使用者遽增 而變更公司名稱 MultiTorg Opera 1.0 ‧蕃薯藤成立 日本分公司成立 Internet Explorer 2.0 Netscape Navigator 2.0 ‧瀏覽器大戰白熱化 發展 整合 Mail、Composer ‧公佈 CSS1 建議書 郵件及網頁編輯功能 部份支援 JScript、VBScript Opera 2.0 Netscape Navigator 3.0 Netscape Navigator 3.0 及 CSS 草案 Standard Edition Gold Edition 支援 CSS、DHTML Internet Explorer 3.0 加強國際化支援 KDE Netscape Communicator 4.0 CSS、DHTML Project ‧公佈 HTML4.0 建議 精誠公司代理 KDE HTML 書 Netscape Trident 發展 widget ‧精誠公司成立 Kimo 進入台灣市場 開始開發 Internet Explorer 4.0 Windows 98 奇摩站 發行 免費散佈 NC4.x 整合 IE 4.0 開發中的 NC5.0 Netscape Communicator 5.0 ‧IE 獲得壓倒性優勢 開放原始碼化 ‧CSS2、XML1.0、 繼承部份程式碼 Opera 3.0 發行 和設計概念 支援 Ruby Text DOM 1 建議書公佈 放棄 文字顯示 KHTML ‧SEEDNet、蕃薯藤公 加入 Mail 功能 公開 司化 Mozilla Application Suite Gecko Internet Explorer 5.0 Google [Milestone 3~18] 高度支援網頁 ‧台灣上網人口突 破 開發代號「Seamonkey」 標準的成像技術 四百萬 支援文字直排 由 Netscape 的 全 發展 Windows 職員工和 Netscape 2000 發行 ‧瀏覽器大戰結束 開始中文化專案台灣志願者Communications Mozilla Application Suite 0.6 Internet Explorer 5.5 Opera