Cyber, Intelligence, and Security Volume 3 | No
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IDC Herzliya's President and Founder, the Israeli Marketing Association Expresses Its Appreciation for His Initiative and Leadership As the Prof
Herzliyan The IDC WINTER 2017 Leading Innovation IDC Herzliya Inaugurates the Dr. Miriam and Sheldon G. Adelson School of Entrepreneurship Contact IDC Herzliya: Israel Friends of IDC Tel: +972-9-952-7212 • [email protected] International Friends of IDC Tel: +972-9-952-7321 • [email protected] American Friends of IDC Tel: +1-212-213-5962 • [email protected] UK & Francophone Europe Friends of IDC Tel: +44 (0)778 384 6852 • [email protected] IDC Alumni Association Tel: +972-9-960-2756 • [email protected] Raphael Recanati International School Tel: +972-9-960-2806 • [email protected] THE RAPHAEL RECANATI INTERNATIONAL SCHOOL THANKS ALEXANDER MUSS HIGH SCHOOL IN ISRAEL THE ISRAELI AMERICAN COUNCIL (IAC) GARIN TZABAR HESEG HILLEL ISRAEL AT HEART ISRAEL MINISTRY OF EDUCATION ISRAEL MINISTRY OF IMMIGRANT ABSORPTION THE JEWISH AGENCY FOR ISRAEL & WZO THE JEWISH FEDERATIONS MASA NEFESH B’NEFESH OLIM ORGANIZATIONS STAND WITH US STUDENT AUTHORITY TAGLIT BIRTHRIGHT THE ZIONIST YOUTH MOVEMENTS BA Business Administration | Business & Economics (double major) | Communications | Government for helping us bring 1,800 students Government & Sustainability (double major) | Psychology from 86 countries to study for full academic degrees taught in English. BSc Computer Science MA Counter-Terrorism & Homeland Security Studies Diplomacy & Conflict Studies | Financial Economics (MAFE) Organizational Behavior & Development (OBD) Social Psychology GLOBAL MBA Innovation & Entrepreneurship Strategy & Business Development MBA One-Year Program LIVE IN ISRAEL Study in English ISRAEL +972 9 960 2841 [email protected] www.rris.idc.ac.il NORTH AMERICA +1 866 999 RRIS [email protected] UK & FRANCOPHONE EUROPE +44 (0) 778 384 6852 [email protected] IDC HERZLIYAN WINTER 2017 Inside Prof. -

JW Apostate Reply Supporting Motion to Quash April 6Th
Case 7:20-mc-00119-CS Document 13 Filed 04/06/20 Page 1 of 21 1 JANE / JOHN DOE 2 Email: [email protected] 3 4 Pro se 5 IN THE UNITED STATES DISTRICT COURT FOR THE 6 SOUTHERN DISTRICT OF NEW YORK 7 8 IN RE: DMCA SUBPOENA TO GOOGLE, LLC Case No.: 7:20-mc-00119 9 10 JANE / JOHN DOE’S REPLY IN SUPPORT OF THE OBJECTION AND MOTION TO 11 QUASH DMCA SUBPOENA 12 13 A. INTRODUCTION 14 15 While it is true that Jehovah’s Witnesses are well known for their distribution of 16 Bible based books and publications, they are also a notorious group of criminal 17 pedophiles running a scam “religion” who are guilty of abuse of process and emotional 18 19 extortion through sham litigation in their pathetic efforts at discovering leaks and 20 moles and whistleblowers. Unfortunately for them, this is the year 2020 and things 21 22 like VPNs, anonymous proxies, and TOR exit nodes frustrate them at every turn. 23 Whether one is known as Darkspilver or John Redwood or JW Apostate, or any 24 number of other pseudonyms, it does not really matter as we are all Spartacus in this 25 26 fight! Reporting on and exposing to public comment and ridicule the doctrinal 27 inconsistencies and reversals, failed predictions, mistranslation of the Bible, harsh 28 JANE / JOHN DOE’S REPLY IN SUPPORT OF OBJECTION AND MOTION TO QUASH DMCA SUBPOENA- 1 Case 7:20-mc-00119-CS Document 13 Filed 04/06/20 Page 2 of 21 1 treatment of former members and autocratic and coercive leadership (not to mention 2 the child raping!) is a public duty that Jane / John Doe takes extremely seriously at 3 1 great personal risk. -

Introduction Points
Introduction Points Ahmia.fi - Clearnet search engine for Tor Hidden Services (allows you to add new sites to its database) TORLINKS Directory for .onion sites, moderated. Core.onion - Simple onion bootstrapping Deepsearch - Another search engine. DuckDuckGo - A Hidden Service that searches the clearnet. TORCH - Tor Search Engine. Claims to index around 1.1 Million pages. Welcome, We've been expecting you! - Links to basic encryption guides. Onion Mail - SMTP/IMAP/POP3. ***@onionmail.in address. URSSMail - Anonymous and, most important, SECURE! Located in 3 different servers from across the globe. Hidden Wiki Mirror - Good mirror of the Hidden Wiki, in the case of downtime. Where's pedophilia? I WANT IT! Keep calm and see this. Enter at your own risk. Site with gore content is well below. Discover it! Financial Services Currencies, banks, money markets, clearing houses, exchangers. The Green Machine Forum type marketplace for CCs, Paypals, etc.... Some very good vendors here!!!! Paypal-Coins - Buy a paypal account and receive the balance in your bitcoin wallet. Acrimonious2 - Oldest escrowprovider in onionland. BitBond - 5% return per week on Bitcoin Bonds. OnionBC Anonymous Bitcoin eWallet, mixing service and Escrow system. Nice site with many features. The PaypalDome Live Paypal accounts with good balances - buy some, and fix your financial situation for awhile. EasyCoin - Bitcoin Wallet with free Bitcoin Mixer. WeBuyBitcoins - Sell your Bitcoins for Cash (USD), ACH, WU/MG, LR, PayPal and more. Cheap Euros - 20€ Counterfeit bills. Unbeatable prices!! OnionWallet - Anonymous Bitcoin Wallet and Bitcoin Laundry. BestPal BestPal is your Best Pal, if you need money fast. Sells stolen PP accounts. -

Longitudinal Analysis of Misuse of Bitcoin⋆
Longitudinal Analysis of Misuse of Bitcoin? Karim Eldefrawy1, Ashish Gehani1, and Alexandre Matton2?? 1 SRI International, USA 2 Stanford University, USA Abstract. We conducted a longitudinal study to analyze the misuse of Bitcoin. We first investigated usage characteristics of Bitcoin by analyz- ing how many addresses each address transacts with (from January 2009 to May 2018). To obtain a quantitative estimate of the malicious activity that Bitcoin is associated with, we collected over 2.3 million candidate Bitcoin addresses, harvested from the dark web between June 2016 and December 2017. The Bitcoin addresses found on the dark web were la- beled with tags that classified the activities associated with the onions that these addresses were collected from. The tags covered a wide range of activities, from suspicious to outright malicious or illegal. Of these addresses, only 47,697 have tags we consider indicative of suspicious or malicious activities. We saw a clear decline in the monthly number of Bitcoin addresses seen on the dark web in the periods coinciding with takedowns of known dark web markets. We also found interesting behavior that distinguishes the Bitcoin addresses collected from the dark web when compared to activity of a random address on the Bitcoin blockchain. For example, we found that Bitcoin addresses used on the dark web are more likely to be involved in mixing transactions. To identify mixing transactions, we developed a new heuristic that extends previously known ones. We found that Bitcoin addresses found on the dark web are significantly more ac- tive, they engage in transactions with 20 times the neighbors and 4 times the Bitcoin amounts when compared to random addresses. -

Cyber Influence Campaigns in the Dark Web
Cyber Influence Campaigns in the Dark Web Lev Topor and Pnina Shuker In recent years there has been a significant rise in the scope and intensity of information wars between the great powers and other forces in the international arena, and influence campaigns have become a legitimate tool in the hands of politicians, propagandists, and global powers. In this context, the professional literature has focused most on campaigns on social networks while it has almost ignored similar campaigns in the Dark Web where the current research tends to focus on criminal activity. The Dark Web was developed by the American Navy for intelligence purposes and was then promoted by the West as a public tool to protect privacy and anonymity. Today it provides fertile ground for deliberate leaks by countries that do not wish to publish certain information in the traditional media. These leaks are perceived as authentic, leading the media and other intelligence organizations to swallow the bait and investigate, and in some cases they even change their operations accordingly. The purpose of this article is to present the way in which the Dark Web is used in influence campaigns, particularly through deliberately leaking information. Keywords: Dark Web, influence campaigns, propaganda, information wars, disinformation Dr. Lev Topor is a senior strategic advisor and researcher on racism and cyber. Pnina Shuker is a Neubauer Research Fellow at the Institute of National Security Studies. Cyber, Intelligence, and Security | Volume 3 | No. 2 | October 2019 63 LEV TOPOR AND PNINA SHUKER | CYBER Influence Campaigns IN THE DARK WEB 64 Introduction In January 2019, tens of thousands of documents and emails from senior Russian government officials, leaders of the Russian Orthodox Church, and Russian oligarchs were leaked to the Dark Web. -

Full 8Chan Leak Dump As of April-15-2015 This Is a Quick Overview of Quick Leak
Full 8chan Leak Dump As Of April-15-2015 This is a quick overview of Quick Leak http://8ch.net/leaked/index.html Anonymous Post Makes News Headline! KILLCEN 04/15/15 (Wed) 15:09:40 No.235[Repl y][Watch Thread] LoL! Hey Anonymous! You made news coverage! http://www.cbsnews.com/news/top-law-officials-personal-information-posted-online -right-wing-group-blamed/ DHS-CIA-FBI TRAITORS HOME ADDRESSES: http://quickleak.ir/xiUw8SIv Infowars also covers dox KILLCEN 04/15/15 (Wed) 15:19:3 2 No.236 Holly Molly! Infowars posts report about this too! (I'd l ay low if I were you, for a while) http://www.infowars.com/leaking-of-government-officials-ad dresses-accompanied-by-note-warning-of-fema-crackdown-by-nwo-satanists/ PREPARATION FOR MARTIAL LAW DOWNLOAD LINKS Anonymous 04/15/15 (Wed) 14:51:11 No .234[Reply][Watch Thread] CONCENTRATION CAMPS FOR AMERICANS FREE PDF DOWNLOAD Concentration Camps for Americans How would you like to enter one the over 600 American concentration camps acros s the USA? The barbed wired, shackle embedded camps have been built and are awaiti ng to enslave huge numbers of the population. Should a fitting event take place, current laws allow FEMA to legally incarcerate civilians into these camps. The Federal Government admits plans to detain millions of people Rex 84, short for Readiness Exercise 1984, was a plan by the United States fede ral government to test their ability to detain large numbers of American citizens in case of massive civil unrest or national emergency. -

Says a Friend of Benthall's
54 I At 3:15 P.M. on October 1, 2013, Ross Ulbricht’s career as a drug kingpin came to an end in the science- fiction section of San Francisco’s Glen Park Library. The 29-year- old had walked up the steps just inside the modern stone building, passed the librarian working at the circula- tion desk and taken a seat at a far corner table near a window. It was a sunny day, but the small community library was filled with people. Ulbricht, with his easy smile and thick mop of brown hair, was dressed in blue jeans web of lies_ AN UNDERGROUND, ANONYMOUS INTERNET— THE DEEP WEB—IS THE LAST LAWLESS FRONTIER ON EARTH. BUT NOTHING COULD SAVE ITS KINGPINS FROM THE PAINFUL CONSEQUENCES OF HUMAN ERROR BY JOSHUA HUNT and a T-shirt. The hand- ful of people reading and wandering among rows of novels nearby weren’t dressed much differently, but beneath their shirts and jackets they wore vests that identified them as FBI agents. Until the moment they rushed Ulbricht, pushing him up against a window to handcuff him as other agents seized his laptop before he could lock it down, nobody suspected anything out of place. The cuffs went on and a small crowd gathered, but Ulbricht just looked out at the afternoon sun. Ulbricht was an educated person, with a master’s degree in 55 materials science and engi- neering from Penn State. He was a good son from a good Texas family, an un- likely addition to the list of men who had changed the shape and scale of drug distribution in Amer- ica. -

Technical and Legal Overview of the Tor Anonymity Network
Emin Çalışkan, Tomáš Minárik, Anna-Maria Osula Technical and Legal Overview of the Tor Anonymity Network Tallinn 2015 This publication is a product of the NATO Cooperative Cyber Defence Centre of Excellence (the Centre). It does not necessarily reflect the policy or the opinion of the Centre or NATO. The Centre may not be held responsible for any loss or harm arising from the use of information contained in this publication and is not responsible for the content of the external sources, including external websites referenced in this publication. Digital or hard copies of this publication may be produced for internal use within NATO and for personal or educational use when for non- profit and non-commercial purpose, provided that copies bear a full citation. www.ccdcoe.org [email protected] 1 Technical and Legal Overview of the Tor Anonymity Network 1. Introduction .................................................................................................................................... 3 2. Tor and Internet Filtering Circumvention ....................................................................................... 4 2.1. Technical Methods .................................................................................................................. 4 2.1.1. Proxy ................................................................................................................................ 4 2.1.2. Tunnelling/Virtual Private Networks ............................................................................... 5 -

'Strategy and Iran Directorate' Under General Staff
MIDDLE EAST, NORTH AFRICA Israel Establishes New ‘Strategy and Iran Directorate’ Under General Staff OE Watch Commentary: On 18 February, the Israeli Defense Forces (IDF) announced the creation of a new directorate within the General Staff, called the “Strategy and Iran Directorate” to address growing Iranian threats and coordinate actions against Iran under one roof. The accompanying passages from local sources discuss this new directorate and subsequent changes to the structure of the IDF. The first article from The Times of Israel describes the design of the new Iran Directorate. Currently, the IDF has Major General Amir Baram leading the Northern Command in overseeing operations and threats stemming from Hezbollah while Major General Herzi Halevi and the Southern Command oversee the fight against Hamas in the Gaza Strip. Similarly, the IDF will now have a major general overseeing operations and threats coming directly from Iran. This means that the responsibility for overseeing threats from and actions towards Israel Defense Forces - Nahal’s Brigade Wide Drill. Iran is split between multiple different sections of the Israeli Military such as Source: Flickr via Wikimedia, https://commons.wikimedia.org/wiki/File:Flickr_-_Israel_Defense_Forces_-_Nahal%27s_ Brigade_Wide_Drill_(1).jpg, CC BY 3.0 the Air Force, the Operations Directorate, the Planning Directorate, and Military Intelligence. The second article from The Times of Israel states the Strategy and Iran Directorate will not be responsible for overseeing threats from Iranian proxy forces but only Iran itself, even though Iran has ties to multiple organizations across the region. It reports that the directorate “will be responsible for countering Iran only, not its proxies, like the Hezbollah terror group, which will remain the purview of the IDF Northern Command.” Brigadier General Tal Kalman, currently in charge of the IDF’s Strategic Division, will be promoted to major general and will lead the Strategy and Iran Directorate. -

Troll Hunting
For my father, Brian, who taught me to love wor ds. Hell is empty, and all the devils are here. William Shakespeare, The Tempest, Act 1, Scene 2 THIS IS A work of nonfiction, researched and documented to the best of my ability. There were significant security risks in writing this book. I sought expert advice and wrote according to it. Therefore, some of the trolling syndicates mentioned within these pages have been given pseudonyms or go unnamed. Likewise, some of the trolls themselves are discussed only with a pseudonym. A few of the trolls who spoke to me behind the scenes are not named at all and others are composites or have been segmented. Some readers may be critical of the decision to provide anonymity for people who are hurting others so much. However, sometimes access to information comes at a cost – and, all things being equal, the trolls gave me great access. By the same token, some predator-troll victims are in physical danger. This is especially true where domestic violence is involved. In those cases, names and other identifying details may have been altered but the facts of the stories are unchanged. I have worked hard to quote all interviewees verbatim, but for the sake of readability have corrected some spelling errors and syntax. When I’m messaging with trolls in the United States, I use Australian spelling and they use American spelling. For authenticity, I’ve left this as is. This is a book about the internet and how it bleeds into real life. When quoting links and screenshots, I’ve aimed for accuracy. -

Quase 700 Sites Onion, a MAIORIA ESTÁ ONLINE
Quase 700 sites onion, A MAIORIA ESTÁ ONLINE (ALGUNS NÃO SÃO 24HRS ONLINE) APROVEITE, TENHA CAUTELA A VISITAR SITES SEM LEGENDA, NÃO SABEMOS O QUE É OU O QUE V AI ENCONTRAR EU NÃO TESTEI TODOS OS SITES, OBVIAMENTE. http://2222243pi3jvhgnt.onion/ The Nowhere Server (restored from FH) http://222224h72gngmbr4.onion/ The Nowhere Server (restored from FH) http://2222266ahj25j5j2.onion/ The Nowhere Server (restored from FH) http://2223t4sermipwasm.onion/ The Nowhere Server (restored from FH) http://23tjl3xpt5btiqms.onion/ W38M411 - Login http://25ffhnaechrbzwf3.onion/ NL Growers - Coffee Shop grade Cannabis from the Netherlands - Weed, Hash, Marijuana, Cannabis for Bitcoins http://2atptz66l5aepcbj.onion/ Hacktivisme libre http://2bicbge75gy5xjso.onion/ Sam's Drug Store http://2cmg43zpfbelgwlw.onion/ http://2fqgjzbb2h7yevom.onion/ http://2gxxzwnj52jutais.onion/ The Nowhere Server (restored from FH) http://2jv5r7k66ralyk3g.onion/ http://2kcreatydoneqybu.onion/ Einloggen http://2kka4f23pcxgqkpv.onion/ Euro Guns - Number one guns dealer in onionland - Buy guns and ammo for Bitcoin. http://2ogmrlfzdthnwkez.onion/ Rent-A-Hacker - Hire a hacker for every job you c an imagine, from DDOS to completely ruining people or destroy reputation of a co mpany or individual http://2oztyiaxrr3vijwe.onion/ Index of / http://2pdkdy3eo552mpiz.onion/ http://2q4ryi45p6har5w2.onion/ I2P Downloads from kytv http://2qhtfzoxe24d5gxe.onion/ System Setup Required http://2qtnwm3zdbn52nxt.onion/ Hidden Service #6 http://2r2tz6wzqh7gaji7.onion/ KAVKAZ CENTER http://2xtsq3ekkxjpfm4l.onion/ -
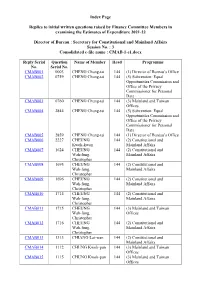
Administration's Replies to Members Initial Written Questions
Index Page Replies to initial written questions raised by Finance Committee Members in examining the Estimates of Expenditure 2021-22 Director of Bureau : Secretary for Constitutional and Mainland Affairs Session No. : 3 Consolidated e-file name : CMAB-1-e1.docx Reply Serial Question Name of Member Head Programme No. Serial No. CMAB001 0003 CHENG Chung-tai 144 (1) Director of Bureau’s Office CMAB002 0759 CHENG Chung-tai 144 (5) Subvention: Equal Opportunities Commission and Office of the Privacy Commissioner for Personal Data CMAB003 0760 CHENG Chung-tai 144 (3) Mainland and Taiwan Offices CMAB004 2844 CHENG Chung-tai 144 (5) Subvention: Equal Opportunities Commission and Office of the Privacy Commissioner for Personal Data CMAB005 2859 CHENG Chung-tai 144 (1) Director of Bureau’s Office CMAB006 2227 CHEUNG 144 (2) Constitutional and Kwok-kwan Mainland Affairs CMAB007 1624 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB008 1695 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB009 1696 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB010 1714 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB011 1715 CHEUNG 144 (3) Mainland and Taiwan Wah-fung, Offices Christopher CMAB012 1716 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB013 1313 CHIANG Lai-wan 144 (2) Constitutional and Mainland Affairs CMAB014 1112 CHUNG Kwok-pan 144 (3) Mainland and Taiwan Offices CMAB015 1115 CHUNG Kwok-pan 144 (3) Mainland