Full 8Chan Leak Dump As of April-15-2015 This Is a Quick Overview of Quick Leak
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“State of Civil Society Report: 2015
the year in review State of Civil Society report 2015: THE YEAR IN REVIEW ...these stories tell us that only civil introduction society, in its broadest sense, is taking a It has been another year of hard work and high achievement for civil society. The story of the year since the stance against the 2014 State of Civil Society Report was published has partly been one of a continuing series of attacks on civil concentration of society in the many countries where, when civil society asks difficult questions about power, the powerful seek to silence it. But is has also been a story of impressive and sustained civil society response, in a world that has power in the hands of become more turbulent and contested. a tiny, global, super- rich elite, and against As we show below, civil society faces challenges - of lack of space, under-resourcing and limited access to the attempts of many decision-makers. Civil society also needs continually to prove its connection with and relevance to citizens, political leaders and and it needs to demonstrate its ability to stay ahead of trends and innovate. When civil society groups do not corporate interests do these, they fail. But so often, we see civil society leading the response to crisis, taking on difficult issues, contributing to change, and winning arguments for social justice. to undermine human rights and This year in review section of the 2015 CIVICUS State of Civil Society Report is complemented by our report’s the value of people’s special thematic section on the resourcing for civil society, and the 27 guest contributions, from civil society participation. -

Prism Vol. 9, No. 2 Prism About Vol
2 021 PRISMVOL. 9, NO. 2 | 2021 PRISM VOL. 9, NO. 2 NO. 9, VOL. THE JOURNAL OF COMPLEX OPER ATIONS PRISM ABOUT VOL. 9, NO. 2, 2021 PRISM, the quarterly journal of complex operations published at National Defense University (NDU), aims to illuminate and provoke debate on whole-of-government EDITOR IN CHIEF efforts to conduct reconstruction, stabilization, counterinsurgency, and irregular Mr. Michael Miklaucic warfare operations. Since the inaugural issue of PRISM in 2010, our readership has expanded to include more than 10,000 officials, servicemen and women, and practi- tioners from across the diplomatic, defense, and development communities in more COPYEDITOR than 80 countries. Ms. Andrea L. Connell PRISM is published with support from NDU’s Institute for National Strategic Studies (INSS). In 1984, Secretary of Defense Casper Weinberger established INSS EDITORIAL ASSISTANTS within NDU as a focal point for analysis of critical national security policy and Ms. Taylor Buck defense strategy issues. Today INSS conducts research in support of academic and Ms. Amanda Dawkins leadership programs at NDU; provides strategic support to the Secretary of Defense, Chairman of the Joint Chiefs of Staff, combatant commands, and armed services; Ms. Alexandra Fabre de la Grange and engages with the broader national and international security communities. Ms. Julia Humphrey COMMUNICATIONS INTERNET PUBLICATIONS PRISM welcomes unsolicited manuscripts from policymakers, practitioners, and EDITOR scholars, particularly those that present emerging thought, best practices, or train- Ms. Joanna E. Seich ing and education innovations. Publication threshold for articles and critiques varies but is largely determined by topical relevance, continuing education for national and DESIGN international security professionals, scholarly standards of argumentation, quality of Mr. -

JW Apostate Reply Supporting Motion to Quash April 6Th
Case 7:20-mc-00119-CS Document 13 Filed 04/06/20 Page 1 of 21 1 JANE / JOHN DOE 2 Email: [email protected] 3 4 Pro se 5 IN THE UNITED STATES DISTRICT COURT FOR THE 6 SOUTHERN DISTRICT OF NEW YORK 7 8 IN RE: DMCA SUBPOENA TO GOOGLE, LLC Case No.: 7:20-mc-00119 9 10 JANE / JOHN DOE’S REPLY IN SUPPORT OF THE OBJECTION AND MOTION TO 11 QUASH DMCA SUBPOENA 12 13 A. INTRODUCTION 14 15 While it is true that Jehovah’s Witnesses are well known for their distribution of 16 Bible based books and publications, they are also a notorious group of criminal 17 pedophiles running a scam “religion” who are guilty of abuse of process and emotional 18 19 extortion through sham litigation in their pathetic efforts at discovering leaks and 20 moles and whistleblowers. Unfortunately for them, this is the year 2020 and things 21 22 like VPNs, anonymous proxies, and TOR exit nodes frustrate them at every turn. 23 Whether one is known as Darkspilver or John Redwood or JW Apostate, or any 24 number of other pseudonyms, it does not really matter as we are all Spartacus in this 25 26 fight! Reporting on and exposing to public comment and ridicule the doctrinal 27 inconsistencies and reversals, failed predictions, mistranslation of the Bible, harsh 28 JANE / JOHN DOE’S REPLY IN SUPPORT OF OBJECTION AND MOTION TO QUASH DMCA SUBPOENA- 1 Case 7:20-mc-00119-CS Document 13 Filed 04/06/20 Page 2 of 21 1 treatment of former members and autocratic and coercive leadership (not to mention 2 the child raping!) is a public duty that Jane / John Doe takes extremely seriously at 3 1 great personal risk. -

THE CASE of SOUTH AFRICA and ISRAEL. a Thesis Submitted In
THE ROLE REGIME TYPE PLAYS WITH RESPECT TO INTELLIGENCE COOPERATION: THE CASE OF SOUTH AFRICA AND ISRAEL. A thesis submitted in fulfilment of the requirements for the degree of Magister Administration in the Department of Political Studies, University of the Western Cape. By Dean John Walbrugh Supervisor: Professor Joelien Pretorius July 2019 KEYWORDS South Africa Israel Intelligence Cooperation Regime Type South African State Security Agency (SSA) Mossad Culture Identity Realism Liberalism Constructivism i ABSTRACT This thesis explores the intelligence cooperation exhibited between South Africa and Israel during the time periods of apartheid (1948-1994) and post-apartheid (1994-2015). Regime type is explored as a factor impacting on the intelligence relationship in both periods. Pertinent to the case study is the fact that South Africa and Israel’s regime type shared commonalities during the first period, but not the second. The thesis examines how these commonalities facilitated intelligence cooperation during apartheid, then turns to the question how the change in South Africa’s regime type after 1994 (whilst Israel’s remained the same) impacted on intelligence cooperation. In order to understand the significance of South Africa’s regime change on the intelligence relationship between the two states, a comprehensive theoretical framework is proposed in order to analyse how and why the internal policies of the two states redirected their intelligence relationship. Within this thesis, the concept of regime type is not used in a conventional way, it is framed through a constructivist notion that includes a focus on identity and how this shapes the two states’ intelligence bureaucratic behaviour. This constructivist framing is in turn juxtaposed to two other International Relations (IR) theories, namely: realism and liberalism. -

Introduction Points
Introduction Points Ahmia.fi - Clearnet search engine for Tor Hidden Services (allows you to add new sites to its database) TORLINKS Directory for .onion sites, moderated. Core.onion - Simple onion bootstrapping Deepsearch - Another search engine. DuckDuckGo - A Hidden Service that searches the clearnet. TORCH - Tor Search Engine. Claims to index around 1.1 Million pages. Welcome, We've been expecting you! - Links to basic encryption guides. Onion Mail - SMTP/IMAP/POP3. ***@onionmail.in address. URSSMail - Anonymous and, most important, SECURE! Located in 3 different servers from across the globe. Hidden Wiki Mirror - Good mirror of the Hidden Wiki, in the case of downtime. Where's pedophilia? I WANT IT! Keep calm and see this. Enter at your own risk. Site with gore content is well below. Discover it! Financial Services Currencies, banks, money markets, clearing houses, exchangers. The Green Machine Forum type marketplace for CCs, Paypals, etc.... Some very good vendors here!!!! Paypal-Coins - Buy a paypal account and receive the balance in your bitcoin wallet. Acrimonious2 - Oldest escrowprovider in onionland. BitBond - 5% return per week on Bitcoin Bonds. OnionBC Anonymous Bitcoin eWallet, mixing service and Escrow system. Nice site with many features. The PaypalDome Live Paypal accounts with good balances - buy some, and fix your financial situation for awhile. EasyCoin - Bitcoin Wallet with free Bitcoin Mixer. WeBuyBitcoins - Sell your Bitcoins for Cash (USD), ACH, WU/MG, LR, PayPal and more. Cheap Euros - 20€ Counterfeit bills. Unbeatable prices!! OnionWallet - Anonymous Bitcoin Wallet and Bitcoin Laundry. BestPal BestPal is your Best Pal, if you need money fast. Sells stolen PP accounts. -

Longitudinal Analysis of Misuse of Bitcoin⋆
Longitudinal Analysis of Misuse of Bitcoin? Karim Eldefrawy1, Ashish Gehani1, and Alexandre Matton2?? 1 SRI International, USA 2 Stanford University, USA Abstract. We conducted a longitudinal study to analyze the misuse of Bitcoin. We first investigated usage characteristics of Bitcoin by analyz- ing how many addresses each address transacts with (from January 2009 to May 2018). To obtain a quantitative estimate of the malicious activity that Bitcoin is associated with, we collected over 2.3 million candidate Bitcoin addresses, harvested from the dark web between June 2016 and December 2017. The Bitcoin addresses found on the dark web were la- beled with tags that classified the activities associated with the onions that these addresses were collected from. The tags covered a wide range of activities, from suspicious to outright malicious or illegal. Of these addresses, only 47,697 have tags we consider indicative of suspicious or malicious activities. We saw a clear decline in the monthly number of Bitcoin addresses seen on the dark web in the periods coinciding with takedowns of known dark web markets. We also found interesting behavior that distinguishes the Bitcoin addresses collected from the dark web when compared to activity of a random address on the Bitcoin blockchain. For example, we found that Bitcoin addresses used on the dark web are more likely to be involved in mixing transactions. To identify mixing transactions, we developed a new heuristic that extends previously known ones. We found that Bitcoin addresses found on the dark web are significantly more ac- tive, they engage in transactions with 20 times the neighbors and 4 times the Bitcoin amounts when compared to random addresses. -

Cyber Influence Campaigns in the Dark Web
Cyber Influence Campaigns in the Dark Web Lev Topor and Pnina Shuker In recent years there has been a significant rise in the scope and intensity of information wars between the great powers and other forces in the international arena, and influence campaigns have become a legitimate tool in the hands of politicians, propagandists, and global powers. In this context, the professional literature has focused most on campaigns on social networks while it has almost ignored similar campaigns in the Dark Web where the current research tends to focus on criminal activity. The Dark Web was developed by the American Navy for intelligence purposes and was then promoted by the West as a public tool to protect privacy and anonymity. Today it provides fertile ground for deliberate leaks by countries that do not wish to publish certain information in the traditional media. These leaks are perceived as authentic, leading the media and other intelligence organizations to swallow the bait and investigate, and in some cases they even change their operations accordingly. The purpose of this article is to present the way in which the Dark Web is used in influence campaigns, particularly through deliberately leaking information. Keywords: Dark Web, influence campaigns, propaganda, information wars, disinformation Dr. Lev Topor is a senior strategic advisor and researcher on racism and cyber. Pnina Shuker is a Neubauer Research Fellow at the Institute of National Security Studies. Cyber, Intelligence, and Security | Volume 3 | No. 2 | October 2019 63 LEV TOPOR AND PNINA SHUKER | CYBER Influence Campaigns IN THE DARK WEB 64 Introduction In January 2019, tens of thousands of documents and emails from senior Russian government officials, leaders of the Russian Orthodox Church, and Russian oligarchs were leaked to the Dark Web. -

Says a Friend of Benthall's
54 I At 3:15 P.M. on October 1, 2013, Ross Ulbricht’s career as a drug kingpin came to an end in the science- fiction section of San Francisco’s Glen Park Library. The 29-year- old had walked up the steps just inside the modern stone building, passed the librarian working at the circula- tion desk and taken a seat at a far corner table near a window. It was a sunny day, but the small community library was filled with people. Ulbricht, with his easy smile and thick mop of brown hair, was dressed in blue jeans web of lies_ AN UNDERGROUND, ANONYMOUS INTERNET— THE DEEP WEB—IS THE LAST LAWLESS FRONTIER ON EARTH. BUT NOTHING COULD SAVE ITS KINGPINS FROM THE PAINFUL CONSEQUENCES OF HUMAN ERROR BY JOSHUA HUNT and a T-shirt. The hand- ful of people reading and wandering among rows of novels nearby weren’t dressed much differently, but beneath their shirts and jackets they wore vests that identified them as FBI agents. Until the moment they rushed Ulbricht, pushing him up against a window to handcuff him as other agents seized his laptop before he could lock it down, nobody suspected anything out of place. The cuffs went on and a small crowd gathered, but Ulbricht just looked out at the afternoon sun. Ulbricht was an educated person, with a master’s degree in 55 materials science and engi- neering from Penn State. He was a good son from a good Texas family, an un- likely addition to the list of men who had changed the shape and scale of drug distribution in Amer- ica. -

Technical and Legal Overview of the Tor Anonymity Network
Emin Çalışkan, Tomáš Minárik, Anna-Maria Osula Technical and Legal Overview of the Tor Anonymity Network Tallinn 2015 This publication is a product of the NATO Cooperative Cyber Defence Centre of Excellence (the Centre). It does not necessarily reflect the policy or the opinion of the Centre or NATO. The Centre may not be held responsible for any loss or harm arising from the use of information contained in this publication and is not responsible for the content of the external sources, including external websites referenced in this publication. Digital or hard copies of this publication may be produced for internal use within NATO and for personal or educational use when for non- profit and non-commercial purpose, provided that copies bear a full citation. www.ccdcoe.org [email protected] 1 Technical and Legal Overview of the Tor Anonymity Network 1. Introduction .................................................................................................................................... 3 2. Tor and Internet Filtering Circumvention ....................................................................................... 4 2.1. Technical Methods .................................................................................................................. 4 2.1.1. Proxy ................................................................................................................................ 4 2.1.2. Tunnelling/Virtual Private Networks ............................................................................... 5 -

Troll Hunting
For my father, Brian, who taught me to love wor ds. Hell is empty, and all the devils are here. William Shakespeare, The Tempest, Act 1, Scene 2 THIS IS A work of nonfiction, researched and documented to the best of my ability. There were significant security risks in writing this book. I sought expert advice and wrote according to it. Therefore, some of the trolling syndicates mentioned within these pages have been given pseudonyms or go unnamed. Likewise, some of the trolls themselves are discussed only with a pseudonym. A few of the trolls who spoke to me behind the scenes are not named at all and others are composites or have been segmented. Some readers may be critical of the decision to provide anonymity for people who are hurting others so much. However, sometimes access to information comes at a cost – and, all things being equal, the trolls gave me great access. By the same token, some predator-troll victims are in physical danger. This is especially true where domestic violence is involved. In those cases, names and other identifying details may have been altered but the facts of the stories are unchanged. I have worked hard to quote all interviewees verbatim, but for the sake of readability have corrected some spelling errors and syntax. When I’m messaging with trolls in the United States, I use Australian spelling and they use American spelling. For authenticity, I’ve left this as is. This is a book about the internet and how it bleeds into real life. When quoting links and screenshots, I’ve aimed for accuracy. -

Quase 700 Sites Onion, a MAIORIA ESTÁ ONLINE
Quase 700 sites onion, A MAIORIA ESTÁ ONLINE (ALGUNS NÃO SÃO 24HRS ONLINE) APROVEITE, TENHA CAUTELA A VISITAR SITES SEM LEGENDA, NÃO SABEMOS O QUE É OU O QUE V AI ENCONTRAR EU NÃO TESTEI TODOS OS SITES, OBVIAMENTE. http://2222243pi3jvhgnt.onion/ The Nowhere Server (restored from FH) http://222224h72gngmbr4.onion/ The Nowhere Server (restored from FH) http://2222266ahj25j5j2.onion/ The Nowhere Server (restored from FH) http://2223t4sermipwasm.onion/ The Nowhere Server (restored from FH) http://23tjl3xpt5btiqms.onion/ W38M411 - Login http://25ffhnaechrbzwf3.onion/ NL Growers - Coffee Shop grade Cannabis from the Netherlands - Weed, Hash, Marijuana, Cannabis for Bitcoins http://2atptz66l5aepcbj.onion/ Hacktivisme libre http://2bicbge75gy5xjso.onion/ Sam's Drug Store http://2cmg43zpfbelgwlw.onion/ http://2fqgjzbb2h7yevom.onion/ http://2gxxzwnj52jutais.onion/ The Nowhere Server (restored from FH) http://2jv5r7k66ralyk3g.onion/ http://2kcreatydoneqybu.onion/ Einloggen http://2kka4f23pcxgqkpv.onion/ Euro Guns - Number one guns dealer in onionland - Buy guns and ammo for Bitcoin. http://2ogmrlfzdthnwkez.onion/ Rent-A-Hacker - Hire a hacker for every job you c an imagine, from DDOS to completely ruining people or destroy reputation of a co mpany or individual http://2oztyiaxrr3vijwe.onion/ Index of / http://2pdkdy3eo552mpiz.onion/ http://2q4ryi45p6har5w2.onion/ I2P Downloads from kytv http://2qhtfzoxe24d5gxe.onion/ System Setup Required http://2qtnwm3zdbn52nxt.onion/ Hidden Service #6 http://2r2tz6wzqh7gaji7.onion/ KAVKAZ CENTER http://2xtsq3ekkxjpfm4l.onion/ -
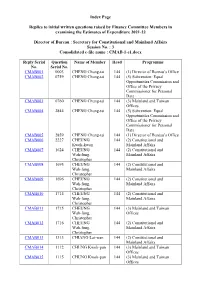
Administration's Replies to Members Initial Written Questions
Index Page Replies to initial written questions raised by Finance Committee Members in examining the Estimates of Expenditure 2021-22 Director of Bureau : Secretary for Constitutional and Mainland Affairs Session No. : 3 Consolidated e-file name : CMAB-1-e1.docx Reply Serial Question Name of Member Head Programme No. Serial No. CMAB001 0003 CHENG Chung-tai 144 (1) Director of Bureau’s Office CMAB002 0759 CHENG Chung-tai 144 (5) Subvention: Equal Opportunities Commission and Office of the Privacy Commissioner for Personal Data CMAB003 0760 CHENG Chung-tai 144 (3) Mainland and Taiwan Offices CMAB004 2844 CHENG Chung-tai 144 (5) Subvention: Equal Opportunities Commission and Office of the Privacy Commissioner for Personal Data CMAB005 2859 CHENG Chung-tai 144 (1) Director of Bureau’s Office CMAB006 2227 CHEUNG 144 (2) Constitutional and Kwok-kwan Mainland Affairs CMAB007 1624 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB008 1695 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB009 1696 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB010 1714 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB011 1715 CHEUNG 144 (3) Mainland and Taiwan Wah-fung, Offices Christopher CMAB012 1716 CHEUNG 144 (2) Constitutional and Wah-fung, Mainland Affairs Christopher CMAB013 1313 CHIANG Lai-wan 144 (2) Constitutional and Mainland Affairs CMAB014 1112 CHUNG Kwok-pan 144 (3) Mainland and Taiwan Offices CMAB015 1115 CHUNG Kwok-pan 144 (3) Mainland