A First Look at Mobile Hand-Held Device Traffic
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bedienungsanleitung HTC Touch 3G
Handbuch www.htc.com Bitte zuerst lesen WENN SIE DEN AKKU AUS DEM KARTON ENTNEHMEN, IST ER NICHT GELADEN. ENTFERNEN SIE NICHT DEN AKKU, WÄHREND DAS GERÄT GELADEN WIRD. DIE GARANTIE ERLISCHT, WENN SIE DAS AUSSENGEHÄUSE DES GERÄTES ÖFFNEN ODER SONSTWIE BESCHÄDIGEN. DATENSCHUTZBESCHRÄNKUNGEN Einige Länder erfordern die volle Offenlegung von aufgezeichneten Telefongesprächen und schreiben vor, dass Sie Ihren Gesprächspartner darüber informieren müssen, wenn ein Gespräch aufgezeichnet wird. Befolgen Sie immer die entsprechenden Gesetze und Bestimmungen Ihres Landes, wenn Sie die Aufnahmefunktion des PDA-Telefons einsetzen. INFORMATIONEN ZU RECHTEN ÜBER GEISTIGES EIGENTUM Copyright © 008 HTC Corporation. Alle Rechte vorbehalten. HTC, das HTC-Logo, HTC Innovation, ExtUSB, TouchFLO, HTC Touch und HTC Care sind Warenzeichen und/oder Dienstleistungszeichen der HTC Corporation. Microsoft, MS-DOS, Windows, Windows NT, Windows Server, Windows Mobile, Windows XP, Windows Vista, ActiveSync, Windows Mobile-Gerätecenter, Internet Explorer, MSN, Hotmail, Windows Live, Outlook, Excel, PowerPoint, Word, OneNote und Windows Media sind entweder eingetragene oder nicht eingetragene Warenzeichen von Microsoft Corporation in den USA und/oder anderen Ländern. Bluetooth und das Bluetooth-Logo sind Warenzeichen im Besitz von Bluetooth SIG, Inc. Java, JME und alle anderen Java-basierten Zeichen sind Warenzeichen oder eingetragene Warenzeichen von Sun Microsystems, Inc. in den USA und anderen Ländern. Copyright © 008, Adobe Systems Incorporated. Alle Rechte vorbehalten. microSD ist ein Warenzeichen von SD Card Association. Opera® Mobile von Opera Software ASA. Copyright 1995-008 Opera Software ASA. Alle Rechte vorbehalten. Google ist ein eingetragenes Warenzeichen und Google Maps ist ein Warenzeichen von Google, Inc. in den USA und anderen Ländern. YouTube ist ein Warenzeichen von Google, Inc. -
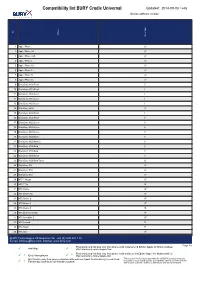
BURY Compatibility List Generator
Compatibility list BURY Cradle Universal Updated: 2014-09-03 / v48 Device software version: No Phone Set of tips 1 Apple iPhone A' 2 Apple iPhone 3G A' 3 Apple iPhone 3GS A' 4 Apple iPhone 4 A' 5 Apple iPhone 4S A' 6 Apple iPhone 5 A' 7 Apple iPhone 5c A' 8 Apple iPhone 5s A' 9 BlackBerry 8100 Pearl F 10 BlackBerry 8110 Pearl F 11 BlackBerry 8300 Curve F 12 BlackBerry 8310 Curve F 13 BlackBerry 8520 Curve F 14 BlackBerry 8800 A' 15 BlackBerry 9100 Pearl E 16 BlackBerry 9105 Pearl E 17 BlackBerry 9320 Curve E 18 BlackBerry 9360 Curve E 19 BlackBerry 9380 Curve E 20 BlackBerry 9500 Storm F 21 BlackBerry 9520 Storm2 F 22 BlackBerry 9700 Bold F 23 BlackBerry 9780 Bold F 24 BlackBerry 9800 Torch F 25 BlackBerry 9900 Bold Touch E 26 BlackBerry Q5 A' 27 BlackBerry Q10 A' 28 BlackBerry Z10 A' 29 HTC 7 Mozart A' 30 HTC 7 Pro B 31 HTC Desire A' 32 HTC Desire HD A' 33 HTC Desire S A' 34 HTC Desire X A' 35 HTC Desire Z B 36 HTC EVO 3D X515m A' 37 HTC Incredible S A' 38 HTC Legend F 39 HTC Magic F 40 HTC One A' BURY Technologies UK Enquiries Tel. +44 (0)1489 881 118 E-mail: [email protected], Internet: www.bury.com Page 1/5 Phonebook and call lists only from phone (with installed 2nd Edition Applet for Nokia mobiles) ✓ working ✓ * http://www.bury.com/en/applet2nd Phonebook and call lists only from phone (with installed 3rd Edition Applet for Nokia mobiles) ✓ 1 Only from phone ✓ ** http://www.bury.com/en/applet3rd Mail function only from phone available with installed Applet for BlackBerry (Email Read The scope of the functions described for all BURY products may vary ✓ 2 according to your mobile phone, your network service provider and the The use of some mobile phones keys could be restricted due to cradle holding mechanism. -

MARATHON WILD ENDURANCE M-PESA Changing Lives
SeptemberSeptember - NovemberNovember 20092009 WIN a beach holiday for two SAFARICOM MARATHON WILD ENDURANCE M-PESA changing lives THIS MONTH SeptemberSeptembetbr --N Novemberovember 2009 WIN a beach holiday for two SAFARICOM MARATHON WILD ENDURANCE Inside 2 Message from Michael M-PESA changing lives 4 What’s news? 6 Matchless marathon WIN a MANAGING EDITOR: Chris Muthama 12 Passion for youth holiday 23 EDITOR: Maryann Michuki CONTRIBUTORS: Craig Bishop, John Kabubu, for two! Kimani Kamakiru, Chebet Karago, 14 Uplifting Kenyans Candice Miranda PHOTOGRAPHY: Craig Bishop, 17 High value trees Gina Din Corporate Communications, Charlie Grieves-Cook, Alex Kamweru, 18 Camphone seduction Chebet Karago, Candice Miranda, Neil Thomas, Duncan Willetts 20 Lions of Lewa PUBLISHERS: East African Magazines Ltd, Nairobi PRINTING: Colourprint, Nairobi 23 Feeling lucky? ALL CORRESPONDENCE TO: The Option Magazine 24 Techno teasers Safaricom Limited P.O. Box 46350- 00100 Nairobi, Kenya 26 Are cellphones risky? [email protected] www.safaricom.co.ke 28 Mobile manners To advertise in The Option Magazine, contact: Helen Kiarie Tel: 020 605991/2 29 Meet Torome Tirike [email protected] 30 Dial 24/7 Techno 34 Going global The editorial content and individual opinions expressed bytes herein are solely those of the authors and do not necessarily represent those of Safaricom Ltd. Neither 35 Always in touch Safaricom nor the Publishers accept any responsibility for the content. All rights reserved. No part of this work 36 What’s hot! may be reproduced or transmitted in any form or by 24 any means, electronic or mechanical, without prior permission in writing from Safaricom. 40 Safaricom shops Ed’s letter It’s amazing how time flies: it is 10 years since the first Safaricom Marathon in Lewa. -

Master Thesis
MASTER THESIS TITLE: Software support for video streaming from smartphone on small airship MASTER DEGREE: Master in Science in Telecommunication Engineering & Management AUTHOR: Miguel Carretero Rodríguez SUPERVISOR: Zbynek Soban DIRECTOR: Lukas Kencl DATE: February, 9th 2009 Overview This project has been created to study and to solve two goals. The main goal has been streaming real video from a smartphone to a laptop and the second goal has been to control the airship electronics from the smartphone. To achieve the main goal of the project, firstly has been necessary realize a technologies study to select the better choice. The chosen technology has been to use of wi-fi, mainly due to the high transmission speed. Once the technology has been chosen, an ad-hoc wi-fi network has been created to be able to transmit wirelessly. After that, it has been necessary to study how to do the sending of the information. The first idea was using the User Datagram Protocol or Transport Control Protocol, at the beginning it seemed a good choice, because of was possible to achieve a communication between the smartphone and the laptop and a camera in record mode application was created. However, when the real video was to be sent to the laptop, it was not possible because it was not way to open the file while it was been created and there was not any temporal file. Then, another possibility had to be studied and it was the use of streamers. The Live555 Streaming Media is a set of C++ libraries which allows to stream real time from a device to a computer. -

Acer Airis Alcatel Alltel Amoi Amoisonic Anextek Apple Arima
Acer 1 n10 1 1 n311 1 1 S100 Liquid 1 1 X960 1 Airis 1 T480 1 Alcatel 1 ELLE No 1 1 1 ELLE No 3 1 1 One Touch 355 1 1 One Touch 556 1 1 One Touch 557 1 1 One Touch 565 1 1 One Touch 708 1 1 One Touch 735i 1 1 One Touch 756 1 1 One Touch 757 1 1 One Touch 800 1 1 One Touch C551 1 1 One Touch C552 1 1 One Touch C635 1 1 One Touch C651 1 1 One Touch C652 1 1 One Touch C750 1 1 One Touch S853 1 1 One Touch V670 1 Alltel 1 PPC-6800 1 Amoi 1 A310 1 1 D85 1 1 D89 1 1 E72 1 1 F8 1 1 F90 1 1 H9 1 1 M636 1 1 N810 1 1 WP-S1 Skypephone 1 Amoisonic 1 9201 1 AnexTek 1 SP230 1 Apple 1 iPad 1 1 iPhone 1 1 iPod Touch 1 Arima 1 2850 1 Asus 1 1210 1 1 Galaxy II 1 1 Galaxy Mini 1 1 J100 1 1 J101 1 1 J102 1 1 M303 1 1 M530w 1 1 M930 1 1 P320 1 1 P505 1 1 P525 1 1 P526 1 1 P527 1 1 P550 1 1 P552 1 1 P735 1 1 P750 1 1 V80 1 AT&T 1 8900 Tilt 1 1 8925 Tilt 1 Audiovox 1 CDM-8450 1 1 CDM-8450SP 1 1 CDM-8455 1 1 CDM-8615 1 1 CDM-8900 1 1 CDM-8910 1 1 CDM-8912 1 1 CDM-8915 1 1 CDM-8920 1 1 CDM-8930 1 1 PM-8912 1 1 PM-8920 1 1 PPC-6600 / PPC-6601 1 1 PPC-6700 1 1 SMT-5600 1 1 VI600 1 BenQ 1 A500 1 1 A5001 1 1 A520 1 1 CL71 1 1 E72 1 1 E81 1 1 M315 1 1 M350 1 1 M580A 1 1 Morpheus 1 1 P30 1 1 P50 1 1 S660C 1 1 S668C 1 1 S670C 1 1 S680C 1 1 S700 1 1 S7001 1 1 S82 1 1 S830C 1 1 U700 1 1 Z2 1 BenQ-Siemens 1 C81 1 1 C81F 1 1 E71 1 1 EF51 1 1 EF81 1 1 EF91 1 1 EL71 1 1 M81 1 1 P51 1 1 S68 1 1 S80 1 1 S81 1 Bird 1 D660 1 1 E810 1 1 S689 1 1 SC01 1 1 SC24 1 1 V007 1 BlackBerry 1 7100g 1 1 7100i 1 1 7100r 1 1 7100t 1 1 7100v 1 1 7100x 1 1 7105t 1 1 7130c 1 1 7130e 1 1 7130g -

NCK Dongle with Activation (ACT1)
GSM-Support ul. Bitschana 2/38, 31-420 Kraków, Poland mobile +48 608107455, NIP PL9451852164 REGON: 120203925 www.gsm-support.net NCK Dongle with activation (ACT1) NCK Dongle with activation (ACT1) unlimited phone flashing, mobile unlocking and code calculation (Standalone! No server required!) tool for MTK cell phones. NCK Dongle Outstanding Features: - Unlimited Unlock operations - Read BlackBerry Unlock Codes - Calculate BlackBerry 5 Level Codes via IMEI & MEP - Calculate BlackBerry 5 Level Codes via IMEI & PRD - Read Codes for HTC (Omap & Qualcomm) - Read/Write MTK Flash - Write MTK Factory Flash (flash files can be found in support area only) - Format MTK phones - Reset factory defaults (ZTE phones with counter) - Read info and provider ID - Display Codes on PC - Supports latest PIDs - Reads LG Correct Code for Connected phone with RJ45 Cable + FTDI and USB - Unlock Code Calculations for Alcatel cell phones, Calculates 5 levels of Unlock Codes + All - - Existing PIDs Supported - Unlock Code Calculations for ZTE cell phones - Unlock Code Calculations for Motorola WX-series cell phones - Unlock Code Calculations for Vodafone cell phones - Unlock Code Calculations for SFR cell phones - Unlock Code Calculations for ZTE Android B03/B04 cell phones - Read Unlock Codes for LG Infineon cell phones - Factory Reset for LG Infenion based cell phones - Windows 7, Vista & XP compatible - USB Dongle protected Supported models: Alcatel cell phones: AMOI1, B331, C700, C701, C707, C717, C820, C825, EL03, EL05, EL09, F115, F121, F122, F331, MD01, -
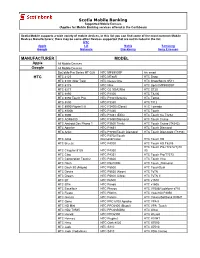
Supported Devices
Scotia Mobile Banking Supported Mobile Devices (Applies for Mobile Banking services offered in the Caribbean) Scotia Mobile supports a wide variety of mobile devices, in this list you can find some of the most common Mobile Devices Manufacturers; there may be some other Devices supported that are not included in the list. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson MANUFACTURER MODEL Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MP6950SP htc smart HTC HTC 2125 HTC MTeoR HTC Snap HTC 3100 (Star Trek) HTC Nexus One HTC Snap/Sprint S511 HTC 6175 HTC Nike HTC Sprint MP6900SP HTC 6277 HTC O2 XDA2Mini HTC ST20 HTC 6850 HTC P3300 HTC T8290 HTC 6850 Touch Pro HTC P3301/Artemis HTC Tattoo HTC 8500 HTC P3350 HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3400i (Gene) HTC Tornado HTC 8900b HTC P3450 HTC Touch HTC 9090 HTC P3451 (Elfin) HTC Touch 3G T3232 HTC ADR6300 HTC P3490/Diamond HTC Touch Cruise HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise (T4242) HTC Apache HTC P3651 HTC Touch Diamond HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond2 (T5353) HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch HD HTC Breeze HTC P4000 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cingular 8125 HTC P4350 III) HTC Cleo HTC P4351 HTC Touch Pro/T7373 HTC Corporation Touch2 HTC P4600 HTC Touch Viva HTC Dash HTC P5310BM HTC Touch_Diamond HTC Dash 3G (Maple) HTC P5500 HTC TouchDual HTC Desire HTC P5530 (Neon) HTC TyTN HTC Dream HTC P5800 (Libra) HTC TyTN II HTC Elf HTC P6500 HTC v1510 HTC Elfin HTC -

Analysis of New Trends in the Web from a Network Perspective
Technische Universitat¨ Berlin Fakultat¨ fur¨ Elektrotechnik und Informatik Lehrstuhl fur¨ Intelligente Netze und Management Verteilter Systeme Analysis of New Trends in the Web from a Network Perspective vorgelegt von Fabian Schneider (Dipl. Inf.) von der Fakult¨at IV – Elektrotechnik und Informatik der Technischen Universit¨at Berlin zur Erlangung der akademischen Grades Doktor der Naturwissenschaften (Dr. rer. nat.) genehmigte Dissertation Promotionsausschuss: Vorsitzende: Prof. Dr. Ina Schieferdecker, TU Berlin Berichtende: Prof. Anja Feldmann, Ph. D., TU Berlin Berichtender: Prof. Dr. habil. Odej Kao, TU Berlin Berichtender: Walter Willinger, Ph. D., AT&T Labs–Research Tag der wissenschaftlichen Aussprache: 30. M¨arz 2010 Berlin 2010 D83 Ich versichere von Eides statt, dass ich diese Dissertation selbst¨andig verfasst und nur die angegebenen Quellen und Hilfsmittel verwendet habe. Datum Fabian Schneider i/ix Abstract Over the last five years, several trends have changed the landscape of the World Wide Web, forming the new “Web 2.0”. The advent of user generated content (blogs and wikis), the popularity of multimedia (e. g., YouTube and MySpace), and the penetration of Google’s services (maps, mail, etc.) are commonly noticeable. In particular, the recent popularity of Online Social Networks (OSNs, e. g., Facebook and LinkedIn) has caused a fundamental change in how the Internet is used. For example, certain OSN users are only using the OSN internal messaging instead of email. This motivates us to examine the usage of these new Web trends and determine their impact on the network. First, we present a traffic study of several Web 2.0 applications including Google Maps, modern Web-based email, and social networking Websites, and compare their traffic characteristics with the ambient HTTP traffic. -

IZAR MOBILE Manual EN.Pdf
Online help Contents 1 IZAR@Mobile.................................................................................................................................1 2 Introduction...................................................................................................................................3 2.1 What is IZAR@Mobile?...................................................................................................3 2.1.1 Reading.................................................................................................................3 2.1.2 Configuration.........................................................................................................3 2.2 System requirements......................................................................................................3 2.2.1 Preconditions PDA installation..............................................................................3 2.2.2 Preconditions notebook installation.......................................................................4 2.3 Installation.......................................................................................................................4 2.3.1 PDA installation.....................................................................................................5 2.3.2 Notebook installation.............................................................................................5 2.3.3 Software update....................................................................................................5 2.4 User -

HXC Dongle - HTC Dongle
GSM-Support ul. Bitschana 2/38, 31-420 Kraków, Poland mobile +48 608107455, NIP PL9451852164 REGON: 120203925 www.gsm-support.net HXC Dongle - HTC Dongle HXC Dongle (GPG Powered) - old HTC Dongle is world first standalone tool for HTC phones and smartphones with simply unlock without loosing any data. HTC Dongle support over 200 phones of the following brands: T-Mobile, Dopod, O2, Orange, Qtek, SFR, Swisscom, Vodafone, EMobile, SoftBank and others. This tool support over 95% of HTC phones. Supported Features: - unlock HTC - read codes in HTC - GoldCard HTC generation - write recovery in HTC HTC Dongle supported list: BRANDMODELOSRead Codes Unlock Gold Card Write Recovery HTC A6366 AndroidYesYesYesYesHTC Aria AndroidYesYesYesYesHTC AT&T Aria AndroidYesYesYesYesHTC BAHAMAS AndroidYesYesYesYesHTC BRAVO AndroidYesYesYesYesHTC BUZZ AndroidYesYesYesYesHTC CLIC1000 AndroidYesYesYesYesHTC Desire AndroidYesYesYesYesHTC Espresso AndroidYesYesYesYesHTC Gratia AndroidYesYesYesYesHTC Hero AndroidYesYesYesYesHTC HERO100 AndroidYesYesYesYesHTC HERO10000 AndroidYesYesYesYesHTC Intruder AndroidYesYesYesYesHTC Legend AndroidYesYesYesYesHTC Liberty AndroidYesYesYesYesHTC Magic AndroidYesYesYesYesHTC My Touch 3G AndroidYesYesYesYesHTC MyTouch 3G Slide AndroidYesYesYesYesHTC MyTouch2 AndroidYesYesYesYesHTC PB6510000 AndroidYesYesYesYesHTC PB7610000 AndroidYesYesYesYesHTC PB9920000 AndroidYesYesYesYesHTC PC4910000 AndroidYesYesYesYesHTC Saphire AndroidYesYesYesYesHTC SAPP100 AndroidYesYesYesYesHTC SAPP10000 AndroidYesYesYesYesHTC Tattoo AndroidYesYesYesYesHTC -
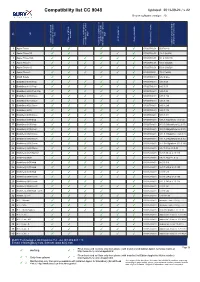
BURY Compatibility List Generator
Compatibility list CC 9048 Updated: 2013-09-24 / v.22 Device software version: 20 No key keys Type tags) activation A2DP supported Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device used to test/ Comments Access to mobile phone voice-dial function (voice Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ 07-0257-0c.01 3.0(7a341) 2 Apple iPhone 3G ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 4.2.1 (8a306) 3 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.1.2 (10b146) 4 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0.1 (10a523) 5 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0.1 (10a523) 6 Apple iPhone 5 ✓ ✓ ✓ ✓ ✓ ✓ 04-29-0020-0 7.0 (11a465) 7 ASUS Solaris ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.2.2 wwe 8 BlackBerry 8100 Pearl ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.69 9 BlackBerry 8110 Pearl ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.55 10 BlackBerry 8220 Pearl Flip ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.94 11 BlackBerry 8300 Curve ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.182 12 BlackBerry 8310 Curve ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.180 13 BlackBerry 8520 Curve ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.1.286 14 BlackBerry 8800 ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.174 15 BlackBerry 8900 Curve ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v5.0.0.411 16 BlackBerry 9000 Bold ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.40(platform 4.0.0.82) 17 BlackBerry 9100 Pearl ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v5.0.0.696(platform 6.2.0.57) 18 BlackBerry 9105 Pearl ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v5.0.0.696(platform 6.2.0.57) 19 BlackBerry 9320 Curve ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 -
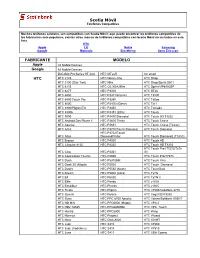
Scotia Móvil FABRICANTE MODELO
Scotia Móvil Teléfonos Compatibles Muchos teléfonos celulares son compatibles con Scotia Móvil; aquí puede encontrar los teléfonos compatibles de los fabricantes más populares, existen otras marcas de teléfonos compatibles con Scotia Móvil no incluidos en esta lista. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson FABRICANTE MODELO Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MTeoR htc smart HTC HTC 2125 HTC Nexus One HTC Snap HTC 3100 (Star Trek) HTC Nike HTC Snap/Sprint S511 HTC 6175 HTC O2 XDA2Mini HTC Sprint MP6900SP HTC 6277 HTC P3300 HTC ST20 HTC 6850 HTC P3301/Artemis HTC T8290 HTC 6850 Touch Pro HTC P3350 HTC Tattoo HTC 8500 HTC P3400i (Gene) HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3450 HTC Tornado HTC 8900b HTC P3451 (Elfin) HTC Touch HTC 9090 HTC P3490/Diamond HTC Touch 3G T3232 HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise HTC Apache HTC P3651 HTC Touch Cruise (T4242) HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch Diamond2 (T5353) HTC Breeze HTC P4000 HTC Touch HD HTC Cingular 8125 HTC P4350 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cleo HTC P4351 III) HTC Corporation Touch2 HTC P4600 HTC Touch Pro/T7373 HTC Dash HTC P5310BM HTC Touch Viva HTC Dash 3G (Maple) HTC P5500 HTC Touch_Diamond HTC Desire HTC P5530 (Neon) HTC TouchDual HTC Dream HTC P5800 (Libra) HTC TyTN HTC Elf HTC P6500 HTC TyTN II HTC Elfin HTC Panda HTC v1510 HTC Excalibur HTC Pharos HTC v1605 HTC Fiesta HTC Pilgrim HTC V7505/Vodafone