Digital Forensics and Born-Digital Content in Cultural Heritage Collections
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FNL Annual Report 2018
Friends of the National Libraries 1 CONTENTS Administrative Information 2 Annual Report for 2018 4 Acquisitions by Gift and Purchase 10 Grants for Digitisation and Open Access 100 Address by Lord Egremont 106 Trustees’ Report 116 Financial Statements 132 2 Friends of the National Libraries Administrative Information Friends of the National Libraries PO Box 4291, Reading, Berkshire RG8 9JA Founded 1931 | Registered Charity Number: 313020 www.friendsofnationallibraries.org.uk [email protected] Royal Patron: HRH The Prince of Wales Chairman of Trustees: to June 28th 2018: The Lord Egremont, DL, FSA, FRSL from June 28th 2018: Mr Geordie Greig Honorary Treasurer and Trustee: Mr Charles Sebag-Montefiore, FSA, FCA Honorary Secretary: Dr Frances Harris, FSA, FRHistS (to June 28th 2018) Membership Accountant: Mr Paul Celerier, FCA Secretary: Mrs Nell Hoare, MBE FSA (from June 28th 2018) Administrative Information 3 Trustees Scottish Representative Dr Iain Brown, FSA, FRSE Ex-officio Dr Jessica Gardner General Council University Librarian, University of Cambridge Mr Philip Ziegler, CVO Dr Kristian Jensen, FSA Sir Tom Stoppard, OM, CBE Head of Arts and Humanities, British Library Ms Isobel Hunter Independent Auditors Secretary, Historical Manuscripts Commission Knox Cropper, 65 Leadenhall Street, London EC3A 2AD (to 28th February 2018) Roland Keating Investment Advisers Chief Executive, British Library Cazenove Capital Management Dr Richard Ovenden London Wall Place, London EC2Y 5AU Bodley’s Librarian, Bodleian Libraries Dr John Scally Principal -

Important Freedos Operating System Information
Important FreeDOS Operating System Information This PC has the FreeDOS operating system preinstalled, The Documentation and Utilities CD supports one or more which provides only limited DOS-based functionality until languages. Because the Documentation and Utilities CD another operating system is installed. does not autorun on some operating systems, you have to explore the directory of the CD to access the Software License and Warranty documentation files. Browse the documentation folder on the CD, locate the appropriate language subfolder, then HP is not responsible for support of the FreeDOS open the product folder to the Safety & Comfort Guide. operating system, and it is important to note that some features of FreeDOS may not function on this system. NOTE: Before you can view the contents of the Some hardware options ordered and delivered with this Documentation and Utilities CD, you must install a PC may not be supported under the FreeDOS operating licensed operating system, as well as a compatible system, nor will HP be responsible for providing driver version of Adobe Acrobat Reader, available at: support for such hardware. Please refer to the standard http://www.adobe.com warranty document included with your PC to learn about software technical support. A copy of the General Public License for FreeDOS can Utilities be found on the PC in the directory The Documentation and Utilities CD also contains a PC C:\FDOS\SOURCE\FREECOM\ diagnostic program called PC Doctor. PC Doctor either runs automatically when you start your PC with this CD in and can be viewed by entering on the command line: the optical drive, or when you install it to your hard drive c:\fdos\source\freecom\license after you have installed a licensed operating system. -

Reactos-Devtutorial.Pdf
Developer Tutorials Developer Tutorials Next Developer Tutorials Table of Contents I. Newbie Developer 1. Introduction to ReactOS development 2. Where to get the latest ReactOS source, compilation tools and how to compile the source 3. Testing your compiled ReactOS code 4. Where to go from here (newbie developer) II. Centralized Source Code Repository 5. Introducing CVS 6. Downloading and configuring your CVS client 7. Checking out a new tree 8. Updating your tree with the latest code 9. Applying for write access 10. Submitting your code with CVS 11. Submitting a patch to the project III. Advanced Developer 12. CD Packaging Guide 13. ReactOS Architecture Whitepaper 14. ReactOS WINE Developer Guide IV. Bochs testing 15. Introducing Bochs 16. Downloading and Using Bochs with ReactOS 17. The compile, test and debug cycle under Bochs V. VMware Testing 18. Introducing VMware List of Tables 7.1. Modules http://reactos.com/rosdocs/tutorials/bk02.html (1 of 2) [3/18/2003 12:16:53 PM] Developer Tutorials Prev Up Next Chapter 8. Where to go from here Home Part I. Newbie Developer (newbie user) http://reactos.com/rosdocs/tutorials/bk02.html (2 of 2) [3/18/2003 12:16:53 PM] Part I. Newbie Developer Part I. Newbie Developer Prev Developer Tutorials Next Newbie Developer Table of Contents 1. Introduction to ReactOS development 2. Where to get the latest ReactOS source, compilation tools and how to compile the source 3. Testing your compiled ReactOS code 4. Where to go from here (newbie developer) Prev Up Next Developer Tutorials Home Chapter 1. Introduction to ReactOS development http://reactos.com/rosdocs/tutorials/bk02pt01.html [3/18/2003 12:16:54 PM] Chapter 1. -

Download from Anywhere in the World
Volume 11 / Number 2 FROM THE PRESIDENT CARNEGIE CONVERSATION Fall 2019 02 10 Power Houses Vartan Gregorian pays tribute to Reassessing U.S.-China Relations Competition American libraries. But do we deserve them? … confrontation … or collision course? An Asia Society Can we keep them? Andrew Carnegie’s visionary report proposes a strategy of “smart competition.” philanthropy points the way. Chief Communications and FEATURE FEATURE Digital Strategies Officer Julia Weede 18 32 Executive Director of Communications The Boundless Library Technology has brought to Saving the Bits Richard Ovenden, Bodley’s Librarian and Content Strategy much of the world a true “digital commons,” creating at the University of Oxford, warns that libraries must Robert Nolan a virtual public square. rise to the challenge of the digital era. Editor/Writer Kenneth Benson Assistant Editor CARNEGIE RESULTS CENTER POINT Anita Jain Principal Design Director 38 46 Daniel Kitae Um The Kids Are Alright At a time of heightened Librarians? What’s not to love? A colorful port- Researcher tensions between the United States and Russia, the PIR folio of portraits by artist Sean Qualls celebrates 10 of Ronald Sexton Center is “keeping the conversation going.” the most downright inspirational librarians in America — winners of the 2018 I Love My Librarian Award. Carnegie Corporation of New York is a philan- thropic foundation created by Andrew Carnegie in 1911 to promote the advancement and diffusion CARNEGIE ON THE GROUND of knowledge and understanding among the people of the United States. Subsequently, its charter was amended to permit the use of funds 54 for the same purposes in certain countries that There’s Hope Could social-emotional learning (SEL) are or have been members of the British Overseas foster the “soft skills” needed to direct students toward Commonwealth. -
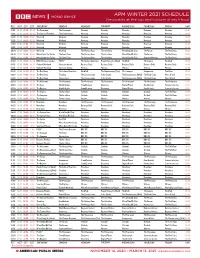
APM WINTER 2021 SCHEDULE Newscasts at the Top and Bottom of Each Hour
APM WINTER 2021 SCHEDULE Newscasts at the top and bottom of each hour PST MST CST EST SATURDAY SUNDAY MONDAY TUESDAY WEDNESDAY THURSDAY FRIDAY GMT 21:00 22:00 23:00 00:00 The Newsroom The Newsroom Newsday Newsday Newsday Newsday Newsday 05:00 21:30 22:30 23:30 00:30 The Cultural Frontline The Conversation Newsday Newsday Newsday Newsday Newsday 05:30 22:00 23:00 00:00 01:00 Weekend Weekend Newsday Newsday Newsday Newsday Newsday 06:00 22:30 23:30 00:30 01:30 Weekend Weekend Newsday Newsday Newsday Newsday Newsday 06:30 23:00 00:00 01:00 02:00 Weekend Weekend Newsday Newsday Newsday Newsday Newsday 07:00 23:30 00:30 01:30 02:30 Weekend Weekend Newsday Newsday Newsday Newsday Newsday 07:30 00:00 01:00 02:00 03:00 Weekend Weekend The History Hour The Arts Hour W’end Doc/Bk Club The Forum The Real Story 08:00 00:30 01:30 02:30 03:30 When Katty Met Carlos The Food Chain The History Hour The Arts Hour W’end Doc/Bk Club The Forum The Real Story 08:30 00:50 01:50 02:50 03:50 When Katty Met Carlos The Food Chain The History Hour The Arts Hour W’end Doc/Bk Club Sporting Witness The Real Story 08:50 01:00 02:00 03:00 04:00 BBC OS Conversations FOOC* The Climate Question People Fixing the World HardTalk The Inquiry HardTalk 09:00 01:30 02:30 03:30 04:30 Outlook Weekend Science in Action Business Daily Business Daily Business Daily Business Daily Business Daily 09:30 01:50 02:50 03:50 04:50 Outlook Weekend Science in Action Witness Witness Witness Witness Witness 09:50 02:00 03:00 04:00 05:00 The Real Story The Cultural Frontline HardTalk The Documentary -

Virtualization
Print Date: 21.06.2013 Transfer Files to FreeDOS Guest OS with ISO Image Oracle VM VirtualBox Brainboxes Limited, 18 Hurricane Drive, Liverpool International Business Park, Speke, Liverpool, L24 8RL, UK Tel: +44 (0)151 220 2500 Fax: +44 (0)151 252 0446 Web: www.brainboxes.com Email: [email protected] Contents 1. Version History ............................................................................................................................................ 10 © Copyright Brainboxes Limited 2013 Page 2 of 10 This document will demonstrate how to transfer files from the ISO disc image to FreeDOS Guest Operating System using Oracle VM VirtualBox application. 1. Start FreeDOS guest operating system by clicking “ Start ” as shown below: 2. Once the Guest Operating System is booted successfully, click “ Devices -> CD/DVD Devices -> Choose a virtual CD/DVD disk file… ” as shown below: © Copyright Brainboxes Limited 2013 Page 3 of 10 3. Browse to “Desktop” where the ISO image file is located, select the “PDS.iso” image file, and then click “Open ” when you are presented with the following: 4. Type “ md PDS ” at the DOS prompt, and then press “ Enter ” in order to create a PDS directory under C: drive as shown below: © Copyright Brainboxes Limited 2013 Page 4 of 10 5. Type “ D: ” at the DOS prompt, and then press “ Enter ” when you are presented with the following: 6. Type “ dir ” at the DOS prompt, and you will be shown that the folder “ PDS ” in the CD/DVD drive of the Guest Operating System which has the same contents as the ISO disc image file we have create previously as shown in the following: © Copyright Brainboxes Limited 2013 Page 5 of 10 7. -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -

Conference Programme
@LIBERconference #LIBER2019 48th LIBER Annual Conference Research Libraries Trinityfor College Society Dublin, Ireland 26-28 June 2019 consortium of national & university libraries While the world benefits from what’s new, IEEE can focus you on what’s next. IEEE Xplore can power your research and help develop Esploro new ideas faster with access to trusted content: • Journals and Magazines • eLearning The Library at the • Conference Proceedings • Analytics Solutions • Standards • Plus content from Heart of Research • eBooks select partners LEVERAGE LIBRARY EXPERTISE FOR MANAGING IEEE Xplore® Digital Library Information Driving Innovation AND EXPOSING INSTITUTIONAL RESEARCH See how IEEE Xplore can add value to your institution’s research collection. Learn More innovate.ieee.org Connect with IEEE Xplore One place for all Intelligent capture of research output data from internal & and data, across all external sources disciplines Improve visitor experience by providing real-time occupancy data Metadata Automated Analysis & and booking services. enrichment for update of measurement improved researcher profiles of research discoverability performance 2 N°1 mobile services for libraries Learn More: http://bit.ly/EXLEsploro www.affluences.com 48th LIBER Annual Conference Research Libraries for Society Trinity College Dublin, the University of Dublin 26-28 June 2019 @LIBERconference #LIBER2019 5 Table of Contents 4 LIBER 2019 Main Programme at a Glance 6 Welcome from the President of LIBER 8 Welcome to Trinity College Dublin 10 Welcome to Ireland 11 Venue Information 14 Conference Essentials 15 Social Programme 22 Pre-Conference Programme 25 Annual Conference Programme 39 Exhibition and Posters 41 Workshops 59 Abstracts and Presenter Profiles 153 Invitation to LIBER 2020 154 LIBER Annual Conference Fund 155 LIBER Award for Library Innovation 160 Exhibition Floor Plan 162 LIBER Organisation 166 Acknowledgements & Thanks All contents (text and images), except where otherwise noted, are licenced under a Creative Commons Attribution (CC BY) licence. -

Transfer Files to Freedos Guest OS with ISO Image 1
Print Date: 21.06.2013 Transfer Files to FreeDOS Guest OS with ISO Image Creating Disc Image Brainboxes Limited, 18 Hurricane Drive, Liverpool International Business Park, Speke, Liverpool, L24 8RL, UK Tel: +44 (0)151 220 2500 Fax: +44 (0)151 252 0446 Web: www.brainboxes.com Email: [email protected] Contents 1. Version History .............................................................................................................................................. 9 © Copyright Brainboxes Limited 2013 Page 2 of 9 The following document will help you transfer files from your Windows 7 32-bit Host Operating System to FreeDOS Guest Operating System. The following demonstration will show you how to add the files you need to transfer to “FreeDOS” Guest Operating System as a disc image ( ISO image ) using a free CD / DVD burning software called “InfraRecorder ”. You could then load this disc image as a CD / DVD drive of the FreeDOS Guest Operating System and transfer the files. For this demonstration we will be adding the folder “ PDS ” to the disc image. This folder is located under “C:\” root folder as shown below: © Copyright Brainboxes Limited 2013 Page 3 of 9 1. Please browse to the following link from your web browser: http://infrarecorder.org/?page_id=5 2. Please find and download the link as emphasized inside the red rectangle from the webpage as shown below: We will be using portable version of the application so we have the convenience of putting it in USB flash drives so that we could carry it around with us. You can also download and install the software by clicking “ Installer ” link. For this demonstration, we will be using portable version which does not require installation. -

11 Gamero Cyber Conflicts
Explorations in Cyberspace and International Relations Challenges, Investigations, Analysis, Results Editors: Nazli Choucri, David D. Clark, and Stuart Madnick This work is funded by the Office of Naval Research under award number N00014-09-1-0597. Any opinions, findings, and conclusions or recommendations expressed in this publication are those of the author(s) and do not necessarily reflect the views of the Office of Naval Research. DECEMBER 2015 Chapter 11 Cyber Conflicts in International Relations: Framework and Case Studies ECIR Working Paper, March 2014. Alexander Gamero-Garrido This work is funded by the Office of Naval Research under award number N00014-09-1-0597. Any opinions, findings, and conclusions or recommendations expressed in this publication are those of the author(s) and do not necessarily reflect the views of the Office of Naval Research. 11.0 Overview Executive Summary Although cyber conflict is no longer considered particularly unusual, significant uncertainties remain about the nature, scale, scope and other critical features of it. This study addresses a subset of these issues by developing an internally consistent framework and applying it to a series of 17 case studies. We present each case in terms of (a) its socio-political context, (b) technical features, (c) the outcome and inferences drawn in the sources examined. The profile of each case includes the actors, their actions, tools they used and power relationships, and the outcomes with inferences or observations. Our findings include: • Cyberspace has brought in a number of new players – activists, shady government contractors – to international conflict, and traditional actors (notably states) have increasingly recognized the importance of the domain. -

Digital Planet 2017 How Competitiveness and Trust in Digital Economies Vary Across the World
DIGITAL PLANET 2017 HOW COMPETITIVENESS AND TRUST IN DIGITAL ECONOMIES VARY ACROSS THE WORLD Bhaskar Chakravorti and Ravi Shankar Chaturvedi The Fletcher School, Tufts University July 2017 WELCOME SPONSOR DATA PARTNERS OTHER DATA SOURCES CIGI-IPSOS GSMA Wikimedia Edelman ILO World Bank Euromonitor ITU World Economic Forum Freedom House Numbeo World Values Survey Google Web Index DIGITAL PLANET 2017 HOW COMPETITIVENESS AND TRUST IN DIGITAL ECONOMIES VARY ACROSS THE WORLD 2 WELCOME AUTHORS DR. BHASKAR CHAKRAVORTI Principal Investigator The Senior Associate Dean of International Business and Finance at The Fletcher School, Dr. Bhaskar Chakravorti is also the founding Executive Director of Fletcher’s Institute for Business in the Global Context (IBGC) and a Professor of Practice in International Business. Dean Chakravorti has extensive experience in academia, strategy consulting, and high-tech R&D. Prior to Fletcher, Dean Chakravorti was a Partner at McKinsey & Company and a Distinguished Scholar at MIT’s Legatum Center for Development and Entrepreneurship. He has also served on the faculty of the Harvard Business School and the Harvard University Center for the Environment. He serves on the World Economic Forum’s Global Future Council on Innovation and Entrepreneurship and the Advisory Board for the UNDP’s International Center for the Private Sector in Development, is a Non-Resident Senior Fellow at the Brookings Institution India and the Senior Advisor for Digital Inclusion at The Mastercard Center for Inclusive Growth. Chakravorti’s book, The Slow Pace of Fast Change: Bringing Innovations to Market in a Connected World, Harvard Business School Press; 2003, was rated one of the best business books of the year by multiple publications and was an Amazon.com best seller on innovation. -

Morrie Gelman Papers, Ca
http://oac.cdlib.org/findaid/ark:/13030/c8959p15 No online items Morrie Gelman papers, ca. 1970s-ca. 1996 Finding aid prepared by Jennie Myers, Sarah Sherman, and Norma Vega with assistance from Julie Graham, 2005-2006; machine-readable finding aid created by Caroline Cubé. UCLA Library Special Collections Room A1713, Charles E. Young Research Library Box 951575 Los Angeles, CA, 90095-1575 (310) 825-4988 [email protected] ©2016 The Regents of the University of California. All rights reserved. Morrie Gelman papers, ca. PASC 292 1 1970s-ca. 1996 Title: Morrie Gelman papers Collection number: PASC 292 Contributing Institution: UCLA Library Special Collections Language of Material: English Physical Description: 80.0 linear ft.(173 boxes and 2 flat boxes ) Date (inclusive): ca. 1970s-ca. 1996 Abstract: Morrie Gelman worked as a reporter and editor for over 40 years for companies including the Brooklyn Eagle, New York Post, Newsday, Broadcasting (now Broadcasting & Cable) magazine, Madison Avenue, Advertising Age, Electronic Media (now TV Week), and Daily Variety. The collection consists of writings, research files, and promotional and publicity material related to Gelman's career. Physical location: Stored off-site at SRLF. Advance notice is required for access to the collection. Please contact UCLA Library Special Collections for paging information. Creator: Gelman, Morrie Restrictions on Access Open for research. STORED OFF-SITE AT SRLF. Advance notice is required for access to the collection. Please contact UCLA Library Special Collections for paging information. Restrictions on Use and Reproduction Property rights to the physical object belong to the UC Regents. Literary rights, including copyright, are retained by the creators and their heirs.