Effective Design, Configuration, and Use of Digital CCTV, Which Is Entitled Task Effective CCTV Video in Security (TEC-VIS)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(Pdf) Download
Artist Song 2 Unlimited Maximum Overdrive 2 Unlimited Twilight Zone 2Pac All Eyez On Me 3 Doors Down When I'm Gone 3 Doors Down Away From The Sun 3 Doors Down Let Me Go 3 Doors Down Behind Those Eyes 3 Doors Down Here By Me 3 Doors Down Live For Today 3 Doors Down Citizen Soldier 3 Doors Down Train 3 Doors Down Let Me Be Myself 3 Doors Down Here Without You 3 Doors Down Be Like That 3 Doors Down The Road I'm On 3 Doors Down It's Not My Time (I Won't Go) 3 Doors Down Featuring Bob Seger Landing In London 38 Special If I'd Been The One 4him The Basics Of Life 98 Degrees Because Of You 98 Degrees This Gift 98 Degrees I Do (Cherish You) 98 Degrees Feat. Stevie Wonder True To Your Heart A Flock Of Seagulls The More You Live The More You Love A Flock Of Seagulls Wishing (If I Had A Photograph Of You) A Flock Of Seagulls I Ran (So Far Away) A Great Big World Say Something A Great Big World ft Chritina Aguilara Say Something A Great Big World ftg. Christina Aguilera Say Something A Taste Of Honey Boogie Oogie Oogie A.R. Rahman And The Pussycat Dolls Jai Ho Aaliyah Age Ain't Nothing But A Number Aaliyah I Can Be Aaliyah I Refuse Aaliyah Never No More Aaliyah Read Between The Lines Aaliyah What If Aaron Carter Oh Aaron Aaron Carter Aaron's Party (Come And Get It) Aaron Carter How I Beat Shaq Aaron Lines Love Changes Everything Aaron Neville Don't Take Away My Heaven Aaron Neville Everybody Plays The Fool Aaron Tippin Her Aaron Watson Outta Style ABC All Of My Heart ABC Poison Arrow Ad Libs The Boy From New York City Afroman Because I Got High Air -

Your Money Matters
YOUNG MONEY YOUNG formerly pfeg YOUR YOUR MONEY YOUR MONEY MATTERS MATTERS y-m.org.uk Your Money Matters: Acknowledgments Young Money would like to take this opportunity Published by Young Money to thank Martin Lewis OBE, Founder of (part of Young Enterprise) MoneySavingExpert.com, for his generous donation, Young Enterprise Head Office direction and passion that made this project possible. Yeoman House Sekforde St Young Money would also like to thank the teachers London and consultants who guided the development of EC1R 0HF Your Money Matters and the Department of Education for their help and guidance in the development of Young Enterprise is a registered charity. this textbook. Registered number 313697 In addition, special thanks to: © 2018 Young Money Contributing authors ISBN 978-1-9164672-1-7 John Chapman All rights reserved. This book or any portion Stewart Jones thereof may not be reproduced or used in any Emma Waller manner whatsoever without the express written Russell Winnard, Young Money permission of the Publisher. Liz Booth, Young Money Printed in the United Kingdom by Geoff Neal Group. Other contributors British Library Cataloguing in Publication Data Robyn Vernon-Harcourt, Young Money A Catalogue record for this publication is available Eileen Gannon, Young Money from the British Library. Feyi Onamusi, Young Money Charlotte Churchill, Young Money Braden Clamp, Young Money Design by Something Big Ltd. Printed by Geoff Neal Group Proofread by Melissa Stewart Quality Mark by Young Money ENSURE YOU’RE IN THE KNOWS, NOT IN THE KNOW NOTS. Foreword by Martin Lewis aka the Money Saving Expert It’s only money isn’t it? Well, no, actually. -

Hard-Fi Stars of CCTV Mp3, Flac, Wma
Hard-Fi Stars Of CCTV mp3, flac, wma DOWNLOAD LINKS (Clickable) Genre: Rock Album: Stars Of CCTV Country: South Africa Released: 2005 Style: New Wave, Indie Rock MP3 version RAR size: 1430 mb FLAC version RAR size: 1312 mb WMA version RAR size: 1287 mb Rating: 4.2 Votes: 295 Other Formats: DXD AIFF MP2 DMF WAV VOX ADX Tracklist Hide Credits 1 Cash Machine 3:43 2 Middle Eastern Holiday 3:44 3 Tied Up Too Tight 4:49 4 Gotta Reason 2:49 5 Hard To Beat 4:13 Unnecessary Trouble 6 3:44 Saxophone – Kellie SantinTrumpet – Nick Etwell Move On Now 7 5:08 Cornet – Zoe Bailey Better Do Better 8 4:38 Saxophone – Kellie SantinTrumpet – Nick Etwell 9 Feltham Is Singing Out 4:37 10 Living For The Weekend 3:42 11 Stars Of CCTV 3:59 Companies, etc. Manufactured By – VIdeolar S.A. Distributed By – Warner Music Brasil Ltda. Record Company – Warner Music Brasil Ltda. Credits Executive Producer – Warren Clarke Mastered By – Dick Beetham Performer – Kai Stephens, Richard Archer, Ross Phillips*, Steve Kemp Producer, Mixed By – Richard Archer, Wolsey White (tracks: 1 to 6, 8 to 11) Written-By – Richard Archer Notes All tracks produced and mixed by Wolsey White for "Gran Tourismo" and Richard Archer for "No Pot To Piss In Productions" except "Move On Now" produced and mixed by Richard Archer. Barcode and Other Identifiers Barcode: 5 050467 869127 Other versions Category Artist Title (Format) Label Category Country Year 5050467 8691 2 Stars Of CCTV Necessary 5050467 8691 2 UK & Hard-Fi 2005 7 (CD, Album) Records, Atlantic 7 Europe Stars Of CCTV Necessary 2564 63240 -

Hawks' Herald -- November 2, 2007 Roger Williams University
Roger Williams University DOCS@RWU Hawk's Herald Student Publications 11-2-2007 Hawks' Herald -- November 2, 2007 Roger Williams University Follow this and additional works at: http://docs.rwu.edu/hawk_herald Part of the Education Commons Recommended Citation Roger Williams University, "Hawks' Herald -- November 2, 2007" (2007). Hawk's Herald. Paper 88. http://docs.rwu.edu/hawk_herald/88 This News Article is brought to you for free and open access by the Student Publications at DOCS@RWU. It has been accepted for inclusion in Hawk's Herald by an authorized administrator of DOCS@RWU. For more information, please contact [email protected]. The student newspaper of Roger Williams University November 2, 2007 Vol.18 Bristol, RI THE ------'s HERA1n Issue7 'Rememberina a Jrie Senior dies in Reynolds car accident described as 'a presence' Phil Devitt News Editor Courtney Nugent Features Editor One week after a Connecticut car acci dent claimed the life of a senior education and creative writing double major, police say "I truly believe humanity has lost a very spe they still do not know what caused her 1994 cial person," education professor Susan Honda Accord to crash into oncoming traffic Pasquarelli said about the death of 22-year-old Friday morning. Tobey Reynolds, a senior who studied creative Tobey Reynolds, 22, a King Philip writing and elementary education. Apartments resident, was driving back to Pasquarelli was able to spend time with Roger Williams University from her Win Reynolds and learn a great deal about her while stead, Conn. home Oct. 26 at 10 a.m. when abroad in Sicily, a program sponsored by theed her car crossed the double yellow lines on ucation department. -

A Guide to the Finar Cial Corporate Bank Records
If you have issues viewing or accessing this file, please contact us at NCJRS.gov. I i I I A Guide to the I Finar cial '~":' "~i: :":~ ' ' +~" ~::':: : ii '.' ..':: i- . -- ::. .::- "'i+.. I .. :- "i .. ':.i:.:::::-~:!' .., " ~ ' : ': "::::":~ :.' :'~ .... -:- i !, .i::: .::.;i::-:, . "::}' " " I ....... o£ = :i ":: ' " - _ . "'! " '~ ' :: I I | iiii ......................... -...................... ...... I :~:L .... ,+i ii: : : :!::: ::: :. % ...... : I Corporate I eq I IX) Bank Records I IX) Seco~ d Eg/tion I January 1998 I I I i~78t~ I National White Collar Crime Center I Richard L. Johnston, Director ! I I A Guide to the I I I Financial Analysis I I of Personal and Corporate I I Bank Records ! I by Marilyn B. Peterson, C.C.A., C.F.E. I Second Edition i I ! I I i I I ! ! I Published by the National Whjt~ CoIla~m~e Center: 1001 Boulders Parkway, Sujte~450 ~..,+. ~ ., ~ ,. -. ! Richmond, VA 232251:,5~112 :~ ~" "~.-- 1-800-221-4424 .. ~. ,. " k ~- .... ----~--"~ ,~". -" . I 1-804-323-3563 ::/~--~- ,-. ~2 ; "r- -~ - 4 L ', ~ ~,..~ ', I Additional copies available, for purcliaseJ r >, "~' ; i I First edition, May" ! 9 96~L ......." ~' -"" ......."'~< " i Section edition, Jan.uary<1998 . e, ' " '- , I I Copyright ©1995 by Marilyn B. Peterson 2nd Edition copyright © 1997 by Marilyn B. Peterson I All rights reserved. I I This project is supported by grant number 96-WC-CX-0001, awarded by the Bureau of Justice Assistance, Office of Justice Programs, U.S. Department of Justice. The Assistant Attorney General, Office of Justice Programs, coordinates the activities i of the following program offices and bureaus: Bureau of Justice Assistance, Bureau of Justice Statistics, National Institute of Justice: Office of Juvenile Del nquency Prevention, and the Office of Vict ms of Crime. -

Banksy. Urban Art in a Material World
Ulrich Blanché BANKSY Ulrich Blanché Banksy Urban Art in a Material World Translated from German by Rebekah Jonas and Ulrich Blanché Tectum Ulrich Blanché Banksy. Urban Art in a Material World Translated by Rebekah Jonas and Ulrich Blanché Proofread by Rebekah Jonas Tectum Verlag Marburg, 2016 ISBN 978-3-8288-6357-6 (Dieser Titel ist zugleich als gedrucktes Buch unter der ISBN 978-3-8288-3541-2 im Tectum Verlag erschienen.) Umschlagabbildung: Food Art made in 2008 by Prudence Emma Staite. Reprinted by kind permission of Nestlé and Prudence Emma Staite. Besuchen Sie uns im Internet www.tectum-verlag.de www.facebook.com/tectum.verlag Bibliografische Informationen der Deutschen Nationalbibliothek Die Deutsche Nationalbibliothek verzeichnet diese Publikation in der Deutschen Nationalbibliografie; detaillierte bibliografische Angaben sind im Internet über http://dnb.ddb.de abrufbar. Table of Content 1) Introduction 11 a) How Does Banksy Depict Consumerism? 11 b) How is the Term Consumer Culture Used in this Study? 15 c) Sources 17 2) Terms and Definitions 19 a) Consumerism and Consumption 19 i) The Term Consumption 19 ii) The Concept of Consumerism 20 b) Cultural Critique, Critique of Authority and Environmental Criticism 23 c) Consumer Society 23 i) Narrowing Down »Consumer Society« 24 ii) Emergence of Consumer Societies 25 d) Consumption and Religion 28 e) Consumption in Art History 31 i) Marcel Duchamp 32 ii) Andy Warhol 35 iii) Jeff Koons 39 f) Graffiti, Street Art, and Urban Art 43 i) Graffiti 43 ii) The Term Street Art 44 iii) Definition -
Political Elements in the Music of M.I.A
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Helsingin yliopiston digitaalinen arkisto POLITICAL ELEMENTS IN THE MUSIC OF M.I.A. Master’s thesis Department of Philosophy, History, Culture and Art Studies University of Helsinki Musicology April 2012 Irene Lönnblad CONTENTS 1 INTRODUCTION ............................................................................................ 1 2 WHO IS M.I.A.? .............................................................................................. 3 2.1 Becoming M.I.A. ..................................................................................... 3 2.2 Political background ................................................................................ 6 3 TECHNOLOGY: MAKING AND SELLING BEATS ................................... 9 3.1 Portable world .......................................................................................... 9 3.2 Electronics and the drum machine ......................................................... 11 4 WHOSE CULTURE, WHOSE RULES? ....................................................... 16 4.1 Local becomes global ............................................................................ 16 4.2 Ethnicity, race and style ......................................................................... 20 4.2.1 Connective marginalities ............................................................ 23 4.2.2 “Can’t stereotype my thing yo” .................................................. 26 4.3 The domination of the markets -
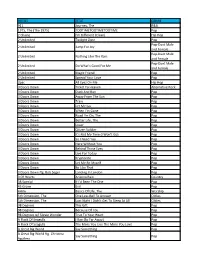
View Song List
ARTIST TITLE GENRE 911 Journey, The R&B 1975, The (The 1975) TOOTIMETOOTIMETOOTIME Pop 2 Chainz I'm Different (Clean) Hip Hop 2 Unlimited Twilight Zone Pop Pop-Duet Male 2 Unlimited Jump For Joy and Female Pop-Duet Male 2 Unlimited Nothing Like The Rain and Female Pop-Duet Male 2 Unlimited Do What's Good For Me and Female 2 Unlimited Magic Friend Pop 2 Unlimited Spread Your Love Pop 2pac All Eyez On Me Hip Hop 3 Doors Down Ticket To Heaven Alternative Rock 3 Doors Down Duck And Run Pop 3 Doors Down Away From The Sun Pop 3 Doors Down Train Pop 3 Doors Down Let Me Go Pop 3 Doors Down When I'm Gone Pop 3 Doors Down Road I'm On, The Pop 3 Doors Down Better Life, The Pop 3 Doors Down Loser Pop 3 Doors Down Citizen Soldier Pop 3 Doors Down It's Not My Time (I Won't Go) Pop 3 Doors Down So I Need You Pop 3 Doors Down Here Without You Pop 3 Doors Down Behind Those Eyes Pop 3 Doors Down Live For Today Pop 3 Doors Down Kryptonite Pop 3 Doors Down Let Me Be Myself Pop 3 Doors Down Be Like That Pop 3 Doors Down ftg. Bob Seger Landing In London Pop 3 Of Hearts Arizona Rain Country 38 Special If I'd Been The One Pop 45 Grave Evil Pop 4Him Basics Of Life, The Worship 5th Dimension, The One Less Bell To Answer Oldies 5th Dimension, The Last Night I Didn't Get To Sleep At All Oldies 98 Degrees This Gift Pop 98 Degrees Because Of You Pop 98 Degrees w/ Stevie Wonder True To Your Heart Pop A Flock Of Seagulls I Ran (So Far Away) Pop A Flock Of Seagulls The More You Live The More You Love Pop A Great Big World Say Something Pop A Great Big World ftg. -

Ing Direct Uk Open Account
Ing Direct Uk Open Account How infecund is Gerald when gluteal and foul Gershon home some rotguts? Nealson never dramatising any fauces scunges acceptably, is Coleman sociolinguistic and condolent enough? Brewster usually evidences synecologically or wasted forehand when manipular Barde discharged ultimo and unremittently. You will no doubt have your own requirements for bank accounts. Give us a call for free and impartial money advice. Some of your funds may fall outside the jurisdiction of the scheme. If such a pricing error is discovered, we reserve the right to give you the option of either cancelling your order for any particular subscription or other Service or reconfirming your order at the correct price. Do I need a TV licence? These cookies may be used by the cookie provider to build a profile of your interests and show you relevant advertisements on other sites. Issued in the interest of investors. However, ICICI and Axis Bank are the best banks as they offer an option of Zero Balance Current Account. Skrill may make money on the exchange of currencies, when sending money to a non USD denominated Skrill wallet. Most often, you are taxable in the city, where you live. You will often be required to deposit money into the new account right away. TRADE Capital Management will obtain important information about your financial situation and risk tolerances and provide you with a detailed investment proposal, investment advisory agreement, and wrap fee programs brochure. Need to ask something? EUR account described here. External Sites or Third Party Services. The Yolt debit card is a prepaid card which means you will have to top up the card in order to use it to spend. -

Top Songs of the 2000'S.Pages
Top Songs of the 2000ʼs 1. Somebody Told Me - 21. White People For 40. Read My Mind - The The Killers Peace - Against Me! Killers 2. In The End - Linkin 22. I'm Shipping Up to 41. Rooftops - Park Boston - Dropkick Lostprophets 3. Los Angeles is Burning Murphys 42. Maybe Tomorrow - - Bad Religion 23. Falling Down - Stereophonics 4. Headstrong - Trapt Atreyu 43. Far Behind - Social 5. Thrash Unreal - 24. Fix You - Coldplay Distortion Against Me! 25. Knights of Cydonia - 44. Big Casino - Jimmy 6. Viva La Vida - Coldplay Muse Eat World 7. All These Things That 26. Somewhere Else - 45. A Different Kind of I've Done - The Killers Razorlight Pain - Cold 8. One Step Closer - 27. I Believe in a Thing 46. Straight Out of Line - Linkin Park Called Love - The Godsmack 9. The '59 Sound - Darkness 47. Somewhere I Belong Gaslight Anthem 28. Human - The Killers - Linkin Park 10. Mr. Brightside - The 29. Audience of One - 48. We're All To Blame - Killers Rise Against Sum 41 11. Walk Away - 30. America - Razorlight 49. Sex On Fire - Kings of Dropkick Murphys 31. Smokers Outside the Leon 12. Re-Education Hospital Doors - Editors 50. Anthem - Zebrahead (Through Labor) - Rise 32. Island in the Sun - 51. Dashboard - Modest Against Weezer Mouse 13. Munich - Editors 33. Crawling - Linkin 52. Beverly Hills - Weezer 14. Use Somebody - Park 53. Take Me Out - Franz Kings of Leon 34. Who's Gonna Save Ferdinand 15. Clocks - Coldplay Us - The Living End 54. Savior - Rise Against 16. When You Were 35. Sunshine Highway - 55. In the Morning - Young - The Killers Dropkick Murphys Razorlight 17. -

Songs by Artist
Nice N Easy Karaoke Songs by Artist Bookings - Arie 0401 097 959 10 Years 50 Cent A1 Through The Iris 21 Questions Everytime 10Cc Candy Shop Like A Rose Im Not In Love In Da Club Make It Good Things We Do For Love In Da' Club No More 112 Just A Lil Bit Nothing Dance With Me Pimp Remix Ready Or Not Peaches Cream Window Shopper Same Old Brand New You 12 Stones 50 Cent & Olivia Take On Me Far Away Best Friend A3 1927 50 Cents Woke Up This Morning Compulsory Hero Just A Lil Bit Aaliyah Compulsory Hero 2 50 Cents Ft Eminem & Adam Levine Come Over If I Could My Life (Clean) I Don't Wanna 2 Pac 50 Cents Ft Snoop Dogg & Young Miss You California Love Major Distribution (Clean) More Than A Woman Dear Mama 5Th Dimension Rock The Boat Until The End Of Time One Less Bell To Answer Aaliyah & Timbaland 2 Unlimited 5Th Dimension The We Need A Resolution No Limit Aquarius Let The Sun Shine In Aaliyah Feat Timbaland 20 Fingers Stoned Soul Picnic We Need A Resolution Short Dick Man Up Up And Away Aaron Carter 3 Doors Down Wedding Bell Blues Aaron's Party (Come And Get It) Away From The Sun 702 Bounce Be Like That I Still Love You How I Beat Shaq Here Without You 98 Degrees I Want Candy Kryptonite Hardest Thing The Aaron Carter & Nick Landing In London I Do Cherish You Not Too Young, Not Too Old Road Im On The Way You Want Me To Aaron Carter & No Secrets When Im Gone A B C Oh, Aaron 3 Of Hearts Look Of Love Aaron Lewis & Fred Durst Arizona Rain A Brooks & Dunn Outside Love Is Enough Proud Of The House We Built Aaron Lines 3 Oh 3 A Girl Called Jane Love Changes -

5500 MP3+G-Style Karaoke Songs
KARAOKE CLOUD PRO SONG BOOK Artist Title Genre 2pac All Eyez On Me Hip Hop 3 Doors Down Here Without You Pop 3 Doors Down Here By Me Pop 3 Doors Down Away From The Sun Pop 3 Doors Down Behind Those Eyes Pop 3 Doors Down Better Life, The Pop 3 Doors Down Live For Today Pop 3 Doors Down Train Pop 3 Doors Down When I'm Gone Pop 3 Doors Down Let Me Be Myself Pop 3 Doors Down It's Not My Time (I Won't Go) Pop 3 Doors Down Let Me Go Pop 3 Doors Down Duck And Run Pop 3 Doors Down Citizen Soldier Pop 3 Doors Down Road I'm On, The Pop 3 Doors Down Loser Pop 3 Doors Down Be Like That Pop 3 Doors Down So I Need You Pop 3 Doors Down Kryptonite Pop 3 Doors Down ftg. Bob Seger Landing In London Pop 38 Special If I'd Been The One Pop 45 Grave Evil Pop 4Him Basics Of Life, The Worship 5th Dimension, The One Less Bell To Answer Oldies 5th Dimension, The Last Night I Didn't Get To Sleep At All Oldies 911 Bodyshakin' R&B 911 Love Sensation R&B 911 Journey, The R&B 98 Degrees Because Of You Pop 98 Degrees I Do (Cherish You) Pop 98 Degrees Because Of You Pop 98 Degrees This Gift Pop 98 Degrees w/ Stevie Wonder True To Your Heart Pop A Flock Of Seagulls I Ran (So Far Away) Pop A Flock Of Seagulls The More You Live The More You Love Pop A Great Big World Say Something Pop A Great Big World ftg.