Digital Technical Journal, Volume 6, Number 4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

VAX 4000 V96-2.3—10 Feb 1997
TM VAX 4000 V96-2.3—10 Feb 1997 DIGITAL Systems and Options Catalog Product Description VAX 4000 systems provide commercial systems performance, high availability, and a compact footprint. They support a wide range of applications and options, including FDDI networks and Q-bus peripherals. System enclosure supports internal storage and Q-bus expansion through a B400X expansion cabinet. VAX 4000 systems come in three packages: Desktop Model 106A, Desktop/Deskside Model 108, and Pedestal/Deskside Model 505A/705A DSSI and Ethernet adapter chips—each driven by a 10-MIP on-chip RISC processor—are tightly integrated on the CPU module with direct access to memory. Digital's DSSI to SCSI HSD10 storage solutions replace DSSI RF36 disk technology in all VAX 4000 systems. Digital’s HSD10 DSSI-to-SCSI controller. mounted internally in system cabinet, supports standard RZxx SCSI storage on VAX 4000 systems while still supporting DSSI clustering. External StorageWorks HSD10 controllers are supported. VAX 4000 Model 106A offers performance of 10-ns NVAX chip. Systems achieve 215 transactions per second (TPS). With internal support for the HSD10, DSSI-to-SCSI controller, VAX 4000 customers can take advantage of low-cost, more flexible and open StorageWorks solutions. VAX 4000 Model 108 offers identical performance, is compatible with Model 106A, but is housed in a new Desktop/Deskside minitower enclosure. In addition, these systems offer enchancements in the memory and storage capacity, supporting up to 512 MB of standard SIMM memory and six storage devices in the system enclosure. VAX 4000 Model 505A and 705A offer 12 ns and 9 ns performance, respectively in a Q-bus Pedestal package. -

I Txso C~T Dc~ 5 SPD / LETTER FC~R
i DIGITAL Digital Equipm~t3t Corporation SOFTW~►,RE Digital Drive SILL OF MATERIALS Westminster, Massachusetts 01473-0471 Option Number Option Title Date Page ~ QA-10 OAA-W55.6 ~rAX FORTF~? V5.6 UPD TK5 0 28-Feb-91 1 of 1 ~TY PICK LOCATION PART NLJL~ER PART DESCRIPTION .~_ -.. 1 *FS* 36-28231-07 TRE~I~ZA~L S~~RCODE LABEL 1 *FS* 99-08545-02 BOOKT~IRAP 1 t UR) AQ-FP 8 6N-BN ~irAX FORTP~AN V5.6 BIN TK5 0 1 ~ DP ~ AV-PF4FA-TK SUP REPLACEMENT LETTER 1 EN-01044-07 SFT'WR PERFOF~!~ANCE REPORT FORM 1 ***** NS ~~~ QA-10 OAA-WZ 5.6 ~irAX FORTF~AN V5.6 UPD DOC 1 *FS* 36-28231-0? THEF~!zA,L P.~ARCODE LABEL 1 *FS* 99-08545-02 BOOKT~IRAP 1 (UR} AE-JF8?L-TE ~irAX FORTP►AN V5.6 SPD 2 5.16.3 6 1 - t~~ AE-LT36H-TE ~irAX FORTP;AN SSA 2 5.16.3 6 -A 1 SDP ) AE -1~tA,5 OA- TK SOFTWARE W TY ADDENDUM 1 tUR~ AV-N672V-TE V'AX FORTP►AN V5.6 PAD FIRS T 1 EN-02512-05 C~3LANGE OF ADDRESS CARD ilk.~ r~~i~li~ilpirfi~~ra~~reis~-~-~~~------~----~~~~ t~ii~~l~+~r~~~-~~~--~--~.r~.~ i Txso c~t Dc~ 5 SPD / LETTER FC~R : AV-PF4FA- TK October, 1990 d 9 Dear Service Customer, Enclosed is a software product update/maintenance release supplied as part of your software maintenance agreement. As part of its planned License Management Zbols program, Digital has initiated replacement of all Service Update PAKs (SUPs) for licensed software product with License Product Authorization Keys (PAKs). -

Validated Processor List
NISTIR 4557 Programming Languages and Database Language SQL VALIDATED PROCESSOR UST Including GOSIP Conformance Testing Registers Judy B. Kailey Editor U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology National Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 April 1991 (Supersedes January 1991 Issue) U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director NIST > NISTIR 4557 Programming Languages and Database Language SQL VALIDATED PROCESSOR LIST Including GOSIP Conformance Testing Registers Judy B. Kailey Editor U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology National Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 April 1991 (Supersedes January 1991 Issue) U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director lib t TABLE OF CONTENTS 1. INTRODUCTION 1 1.1 Purpose 1 1.2 Document Organization 1 1.2.1 Language Processors 1 1.2.2 Contributors to the VPL 2 1.2.3 Other FIPS Conformance Testing Products 2 1.2.4 GOSIP Registers 2 1.3 FIPS Programming and Database Language Standards 3 1.4 Validation of Processors 3 1.4.1 Validation Requirements 3 1.4.2 Placement in the List 4 1.4.3 Removal from the List 4 1.4.4 Validation Procedures 4 1.5 Certificate of Validation 4 1.6 Registered Report 4 1.7 Processor Validation Suites 5 2. COBOL PROCESSORS 7 3. FORTRAN PROCESSORS 13 4. Ada PROCESSORS 21 5. Pascal PROCESSORS 35 6. SQL PROCESSORS 37 APPENDIX A CONTRIBUTORS TO THE LIST A-1 APPENDIX B OTHER FIPS CONFORMANCE TESTING B-1 APPENDIX C REGISTER OF GOSIP ABSTRACT TEST SUITES C-1 APPENDIX D REGISTER OF GOSIP MEANS OF TESTING D-1 APPENDIX E REGISTER OF GOSIP CONFORMANCE TESTING LABORATORIES E-1 . -

Alpha and VAX Comparison Based on Industry-Standard Benchmark
Alpha and VAX Comparison based on Industry-standard Benchmark Results Digital Equipment Corporation December 1994 EC-N3909-10 Version 3.0 December 1994 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. Digital conducts its business in a manner that conserves the environment and protects the safety and health of its employees, customers, and the community. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c) (1 )(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227 7013. Copyright© 1994 Digital Equipment Corporation All rights reserved. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: AlphaServer, AlphaStation, AlphaGeneration, DEC, OpenVMS, VMS, ULTRIX, and the DIGITAL logo. The following are third-party trademarks: MIPS is a trademark of MIPS Computer Systems, Inc. TPC-A is a trademark of the Transaction Processing Performance Council. INFORMIX is a registered trademark of lnformix Software, Inc. OSF/1 is a registered trademark of the Open Software Foundation, Inc. ORACLE is a registered trademark of Oracle Corporation. SPEC, SPECfp92, and SPECratio are trademarks of Standard Performance Evaluation Corporation. MIPS is a trademark of MIPS Computer Systems, Inc. All other trademarks and registered -

Digital Technical Journal, Volume 6, Number 4: RAID Array Controllers
RAID Away Controllers Workflvw Models PC LAN and System Management Tools Digital Technical Journal Digital Equipment Corporation Editorial Advisory Board Jane C. Blake, Managing Editor Samuel H. Fuller, Chairman Kathleen M. Stetson, Editor Richard W Beane Helen L. Patterson, Editor Donald 2. Harbert Circulation William R. Hawe Catherine M. Phillips, Administrator RichardJ. Hollingsworth Dorothea B. Cassady, Secretary Richard E Lary Alan G. Nemeth Production Jean A. Proulx Terri Autieri, Production Editor Robert M. Supnik Anne S. Katzeff, Typographer Gayn B. Winters Peter R. Woodbury, Illustrator The Digital TechnicalJournal is a refereed journal published quarterly by Digital Equipment Corporation, 30 Porter Road LJ02/D10, Littleton, Massachusetts 01460. Subscriptionsto the Journal are $40.00 (non-U.S. $60) for four issues and $75.00 (non-U.S. $115) for eight issues and must be prepaid in U.S. funds. University and college professors and Ph.D. students in the electrical engineering and computer science fields receive complimentary subscriptions upon request. Orders, inquiries, and address changes should be sent to the Digital TechnicalJournal at the published- by address. Inquiries can also be sent electronically to [email protected] copies and back issues are available for $16.00 each by calling DECdirect at 1-800-DIGITAL (1-800-344-4825). Recent back issues of the Journal are also available on the Internet at http://www.digital.com/info/DTJ/home.html. Complete Digital Internet listings can be obtained by sending an electronic mail message to [email protected]. Digital employees may order subscriptions through Readers Choice by entering VTX PROFILE at the system prompt. -

Vaxstation 4000 Model 90 Owner's and System Installation Guide
VAXstation 4000 Model 90 Series Owner’s and System Installation Guide Order Number: EK–VAXOG–IN. B01 Digital Equipment Corporation Maynard, Massachusetts First Printing, August 1992 Second Printing, March 1994 Digital Equipment Corporation makes no representations that the use of its products in the manner described in this publication will not infringe on existing or future patent rights, nor do the descriptions contained in this publication imply the granting of licenses to make, use, or sell equipment or software in accordance with the description. © Digital Equipment Corporation March 1994. All Rights Reserved. The postpaid Reader’s Comments form at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: DEC, DECconnect, DECwindows, ThinWire, RX, VAX, VAXstation, OpenVMS, and the DIGITAL logo. S2530 This document is available on CDROM. This document was prepared using VAX DOCUMENT Version 2.1. Contents Preface ..................................................... xi 1 Your VAXstation 4000 Model 90 System Introduction . ................................... 1–1 Chapter Topics . ................................... 1–1 System Capabilities ................................... 1–1 Overview of Features ............................... 1–1 The VAXstation 4000 Model 90 System ................. 1–2 System Components ................................... 1–3 Components Shipped ............................... 1–3 System Components ............................... -

SOFTWARE PRODUCT DESCRIPTION Charon-VAX/XM and /XM PLUS for Linux
SOFTWARE PRODUCT DESCRIPTION Charon-VAX/XM and /XM PLUS for Linux Product version 4.9 Document version 1 DESCRIPTION Stromasys Charon-VAX/XM and Charon-VAX/XM PLUS are members of the Charon-VAX cross-platform hardware virtualization product family. They are designed to replace MicroVAX II; VAXserver, VAXstation, and MicroVAX models 3600 and 3900; VAX 3100-96; VAX 4000-106; and VAXstation 4000-90 systems by their virtual equivalents running on an x86-64 compatible standard LICENSE PROTECTION computer system. Charon-VAX creates a virtual replica of the original A valid license should be permanently available to Charon in the form DEC VAX hardware, allowing the VAX/VMS operating system and all of a local or network attached USB HASP license dongle, or a software running in that environment to continue to work as before in Software License. The license contains customer specific parameters their existing, binary form. No or only minimal configuration changes and allows remote electronic updates. USB dongles enable a rapid to the original software (operating system, layered products, and switch-over to another host system as the Charon executable itself applications), operational procedures, and management are required. can be installed on multiple systems for disaster recovery purposes. Flexible licensing options allow combining multiple instances of NETWORK different Charon products on a single host system. Charon-VAX virtualizes the Ethernet controllers present in the original VAX hardware. Any protocol supported on these controllers DISTRIBUTION (DECnet, TCP/IP, LAT) will work on the virtualized network link. Charon Release notes, User manuals and Software Product Descriptions are available for download from the Stromasys Product STORAGE Documentation and Knowledge Base web pages. -
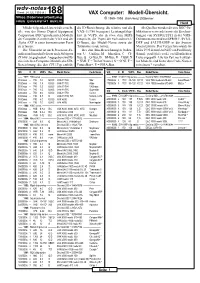
VAX-Computer
wdv-notes Stand: 24.JUL.1993 (4.) 188 VAX Computer: Modell-Übersicht. Wiss.Datenverarbeitung © 1980–1993 Karl-Heinz Dittberner FREIE UNIVERSITÄT BERLIN Hard Mit der folgenden Liste wird versucht, die ID-Bezeichnung, die relative (auf die Als Quellen wurden diverse DEC-Pu- alle von der Firma Digital Equipment VAX-11/780 bezogene) Leistungsfähig- blikationen verwendet sowie die Beschrei- Corporation (DEC) produzierten Modelle keit in VUPS, die in etwa dem MIPS bungen von SYS$GETSYI in der VMS- der Computer-Familien der VAX und der entspricht, die Typen der vorhandenen I/ Dokumentation und von $PRDEF, $VAX- Alpha AXP in einer konzentrierten Form O-Busse, der Modell-Name sowie der DEF und $ALPHADEF in der System zu erfassen. Tarnname (code name). Macro Library. Das Verzeichnis wurde im Die Übersicht ist nach Prozessor-Fa- Bei den Bus-Bezeichnungen bedeu- März 1993 der im UseNET von Paul Hardy milien und innerhalb dieser nach Subtypen ten: U = UniBus, M = MassBus, C = CI- (Email: [email protected]) veröffentlichten (X bzw. S) gegliedert. Angegeben sind für Bus, Q = Q-Bus, B = BI-Bus, D = DSSI, X Liste angepaßt. Alle zur Zeit noch aktuel- die einzelnen Computer-Modelle die SID- = XMI, T = TurboChannel, S = SCSI, F = len Modelle sind hinter dem Code-Namen Bezeichnung, die den CPU-Typ enthält, FutureBus+, E = EISA-Bus. mit einem * versehen. SID X ID VUPS Bus Model Name Code Name SID X ID VUPS Bus Model Name Code Name —— 1977: 700 series ———————————————————————————— —— 1991: NVAX+ chip series ———– Decimal SID = 385875968 ———————— 0100xxxx – 780 1.0 -

VAX VMS at 20
1977–1997... and beyond Nothing Stops It! Of all the winning attributes of the OpenVMS operating system, perhaps its key success factor is its evolutionary spirit. Some would say OpenVMS was revolutionary. But I would prefer to call it evolutionary because its transition has been peaceful and constructive. Over a 20-year period, OpenVMS has experienced evolution in five arenas. First, it evolved from a system running on some 20 printed circuit boards to a single chip. Second, it evolved from being proprietary to open. Third, it evolved from running on CISC-based VAX to RISC-based Alpha systems. Fourth, VMS evolved from being primarily a technical oper- ating system, to a commercial operat- ing system, to a high availability mission-critical commercial operating system. And fifth, VMS evolved from time-sharing to a workstation environment, to a client/server computing style environment. The hardware has experienced a similar evolution. Just as the 16-bit PDP systems laid the groundwork for the VAX platform, VAX laid the groundwork for Alpha—the industry’s leading 64-bit systems. While the platforms have grown and changed, the success continues. Today, OpenVMS is the most flexible and adaptable operating system on the planet. What start- ed out as the concept of ‘Starlet’ in 1975 is moving into ‘Galaxy’ for the 21st century. And like the universe, there is no end in sight. —Jesse Lipcon Vice President of UNIX and OpenVMS Systems Business Unit TABLE OF CONTENTS CHAPTER I Changing the Face of Computing 4 CHAPTER II Setting the Stage 6 CHAPTER -

Mini-Computers • Mini-Skirt • DEC Europe Sales Person Yaniv Frishman
Origin of the Name • Mini-minor Mini-Computers • Mini-skirt • DEC Europe sales person Yaniv Frishman Seminar in computer History CS236801 1 Seminar in computer History CS236801 2 Comparison with Main-Frames Defining Facets Mainframes: 1. Architecture • Leased (rented) 2. Packaging • HW modifications not allowed • HW & SW sold together 3. Role of third-party in apps development Minicomputers: 4. Price • Sold, not rented 5. Financing • Much cheaper • Open spec, modifications encouraged • OEM model Seminar in computer History CS236801 3 Seminar in computer History CS236801 4 Word Length Short Word Workarounds • Typical 1960s IBM Mainframes used 36- • More complex instructions bits – Address stored in a different register – 10 decimal digits • Using double precision math (add with • Manufacturers assumed less would not be carry) enough • Shorter instructions reduce addressing abilities Seminar in computer History CS236801 5 Seminar in computer History CS236801 6 1 DEC PDP-1 PDP-1 I/O - DMA • I/O flows directly from the device to memory • Included many of the TX-0 features • Multiple interrupts • Designed from the ground using • HW support for correct handling (priority) transistors • Cheap: a single IBM I/O channel cost more • Capable of 100,000 additions per second than a complete PDP-1 ($120K) • Core memory of 4K words • About 50 machines sold Seminar in computer History CS236801 7 Seminar in computer History CS236801 8 PDP-1 Space Invaders PDP-1 Space Invaders • Developed by MIT students Applet demo – see • Using 1024x1204 CRT http://spacewar.oversigma.com/ -

Decstation/Decsystem 5000 Model 200 Series Maintenance Guide
EK-PM38C-MG-002 DECstation/DECsystem 5000 Model 200 Series Maintenance Guide digital equipment corporation maynard, massachusetts First printing, January 1992 Second printing, April 1993 © Digital Equipment Corporation 1993. USA This equipment generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference. Operation of this equipment in a residential area may cause interference in which case the user at his own expense will be required to take whatever measures may be required to correct the interference. The following are trademarks of Digital Equipment Corporation: DEC PDP VAXBI DECnet ThinWire VAXcluster DECstation TURBOchannel VAXstation DECsystem ULTRIX VMS DECUS ULTRIX-32 VT MicroVAX UNIBUS MicroVMS VAX dt Contents About This Guide .......................................... xix Part I Hardware 1 System Overview System Hardware Configurations . .................... 1–2 System Unit ......................................... 1–4 Controls and Indicators ............................ 1–6 External System Unit Connectors ................... 1–8 Internal Base System Module Connectors . ........... 1–10 Hardware Options and Peripherals . .................... 1–12 CPU Module Description ........................... 1–13 System Boot ROM ................................. 1–13 Memory Modules ................................. -

The Computer History Simulation Project
The Computer History Simulation Project The Computer History Simulation Project The Computer History Simulation Project is a loose Internet-based collective of people interested in restoring historically significant computer hardware and software systems by simulation. The goal of the project is to create highly portable system simulators and to publish them as freeware on the Internet, with freely available copies of significant or representative software. Simulators SIMH is a highly portable, multi-system simulator. ● Download the latest sources for SIMH (V3.5-1 updated 15-Oct-2005 - see change log). ● Download a zip file containing Windows executables for all the SIMH simulators. The VAX and PDP-11 are compiled without Ethernet support. Versions with Ethernet support are available here. If you download the executables, you should download the source archive as well, as it contains the documentation and other supporting files. ● If your host system is Alpha/VMS, and you want Ethernet support, you need to download the VMS Pcap library and execlet here. SIMH implements simulators for: ● Data General Nova, Eclipse ● Digital Equipment Corporation PDP-1, PDP-4, PDP-7, PDP-8, PDP-9, PDP-10, PDP-11, PDP- 15, VAX ● GRI Corporation GRI-909 ● IBM 1401, 1620, 1130, System 3 ● Interdata (Perkin-Elmer) 16b and 32b systems ● Hewlett-Packard 2116, 2100, 21MX ● Honeywell H316/H516 ● MITS Altair 8800, with both 8080 and Z80 ● Royal-Mcbee LGP-30, LGP-21 ● Scientific Data Systems SDS 940 Also available is a collection of tools for manipulating simulator file formats and for cross- assembling code for the PDP-1, PDP-7, PDP-8, and PDP-11.