The Extended Efficiency Improvement Advisor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Riverside Quarterly V2N4 Sapiro 1967-03
Riverside XZ ‘ RIVERS lue. QUARTERLY March 1967 Vol. u, 4 Editor: Leland Sapiro Associate Editor: Jim Harmon Poetry Editor: Jim Sallis Assistant Editors: Redd Boggs Edward Teach Jon White Send business correspondence and prose manuscripts to: This issue is dedicated to John W. Campbell, Jr., who is Box 82 University Station, Saskatoon, Canada the main subject in two articles. If Orlin Tremaine changed science fiction "from a didactic exercise into a form of art," Send poetry to: R.D. 3, Iowa City, Iowa 52240 then Campbell changed it from romance to novel, i.e., into an art form with social content. I do not prefer the type of story emphasised by Mr. Campbell's present magazine, but this in no way reduces indebtedness to him for any science fiction reader. table of contents "NOW HEAR THIS'." Everyone is urged to register at once for the 1967 science RQ Miscellany .................... 231 fiction convention to be held in New York city, September 1—4. Superman and the System ..... A S3 registration fee paid now entitles you to the usual con (first of two parts) ........... W.H.G. Armytage .... 232 vention privileges (e.g., reduced room rates) plus progress reports and a program book mailed in advance. Send cash or in Consubstantial ............ ....... Padraig 0 Broin .... 243 quiries to Nycon 3, Box 367, Gracie Square Sta., New York 10028. Creide's Lament for Cael ............ 244 Parapsychology: Fact or Fraud? .... Raymond Birge ..... 247 "RADIOHERO" The Bombardier .................... Thomas Disch ....... 265 Old Time Radio fans can anticipate Jim Harmon's book, The Great Radio Heroes, scheduled for publication by Doubleday On Being Forbidden Entrance to a Castle ... -

Tesis Doctorals En Xarxa
Coprocessor integration for real-time event processing in particle physics detectors Alexey Pavlovich Badalov http://hdl.handle.net/10803/396128 ADVERTIMENT. L'accés als continguts d'aquesta tesi queda condicionat a l'acceptació de les condicions d'ús establertes per la següent llicència Creative Commons: http://creativecommons.org/licenses/by/4.0/ ADVERTENCIA. El acceso a los contenidos de esta tesis queda condicionado a la aceptación de las condiciones de uso establecidas por la siguiente licencia Creative Commons: http://creativecommons.org/licenses/by/4.0/ The access to the contents of this doctoral thesis it is limited to the acceptance of the use WARNING. conditions set by the following Creative Commons license: http://creativecommons.org/licenses/by/4.0/ 90) - 02 - TESIS DOCTORAL Título Coprocessor integration for real-time event processing in particle physics detectors Realizada por Alexey Badalov en el Centro La Salle – Ramon Llull University y en el Departamento GR-SETAD C.I.F. G: 59069740 Universitat Ramon Llull Fundació Rgtre. Fund. Generalitat de Catalunya núm. 472 (28 472 núm. de Catalunya Generalitat Rgtre. Fund. Fundació Llull Ramon Universitat 59069740 G: C.I.F. Dirigida por Dr. Xavier Vilasis i Cardona Dr. Niko Neufeld C. Claravall, 1-3 | 08022 Barcelona | Tel. 93 602 22 00 | Fax 93 602 22 49 | [email protected] | www.url.edu Coprocessor integration for real-time event processing in particle physics detectors Alexey Badalov 2 Abstract High-energy physics experiments today have higher energies, more accurate sensors, and more flexible means of data collection than ever before. Their rapid progress requires ever more computational power; and massively parallel hardware, such as graphics cards, holds the promise to provide this power at a much lower cost than traditional CPUs. -

"What Raw Statistics Have the Greatest Effect on Wrc+ in Major League Baseball in 2017?" Gavin D
1 "What raw statistics have the greatest effect on wRC+ in Major League Baseball in 2017?" Gavin D. Sanford University of Minnesota Duluth Honors Capstone Project 2 Abstract Major League Baseball has different statistics for hitters, fielders, and pitchers. The game has followed the same rules for over a century and this has allowed for statistical comparison. As technology grows, so does the game of baseball as there is more areas of the game that people can monitor and track including pitch speed, spin rates, launch angle, exit velocity and directional break. The website QOPBaseball.com is a newer website that attempts to correctly track every pitches horizontal and vertical break and grade it based on these factors (Wilson, 2016). Fangraphs has statistics on the direction players hit the ball and what percentage of the time. The game of baseball is all about quantifying players and being able give a value to their contributions. Sabermetrics have given us the ability to do this in far more depth. Weighted Runs Created Plus (wRC+) is an offensive stat which is attempted to quantify a player’s total offensive value (wRC and wRC+, Fangraphs). It is Era and park adjusted, meaning that the park and year can be compared without altering the statistic further. In this paper, we look at what 2018 statistics have the greatest effect on an individual player’s wRC+. Keywords: Sabermetrics, Econometrics, Spin Rates, Baseball, Introduction Major League Baseball has been around for over a century has given awards out for almost 100 years. The way that these awards are given out is based on statistics accumulated over the season. -

Combining Radar and Optical Sensor Data to Measure Player Value in Baseball
sensors Article Combining Radar and Optical Sensor Data to Measure Player Value in Baseball Glenn Healey Department of Electrical Engineering and Computer Science, University of California, Irvine, CA 92617, USA; [email protected] Abstract: Evaluating a player’s talent level based on batted balls is one of the most important and difficult tasks facing baseball analysts. An array of sensors has been installed in Major League Baseball stadiums that capture seven terabytes of data during each game. These data increase interest among spectators, but also can be used to quantify the performances of players on the field. The weighted on base average cube model has been used to generate reliable estimates of batter performance using measured batted-ball parameters, but research has shown that running speed is also a determinant of batted-ball performance. In this work, we used machine learning methods to combine a three-dimensional batted-ball vector measured by Doppler radar with running speed measurements generated by stereoscopic optical sensors. We show that this process leads to an improved model for the batted-ball performances of players. Keywords: Bayesian; baseball analytics; machine learning; radar; intrinsic values; forecasting; sensors; batted ball; statistics; wOBA cube 1. Introduction The expanded presence of sensor systems at sporting events has enhanced the enjoy- ment of fans and supported a number of new applications [1–4]. Measuring skill on batted balls is of fundamental importance in quantifying player value in baseball. Traditional measures for batted-ball skill have been based on outcomes, but these measures have a low Citation: Healey, G. Combining repeatability due to the dependence of outcomes on variables such as the defense, the ball- Radar and Optical Sensor Data to park dimensions, and the atmospheric conditions [5,6]. -

2017 Killersports.Com Journal of MLB Research
2017 KillerSports.com Journal of MLB Research Featuring the SDQL MLB Studies from Handicapping and Data Experts 580 Perfect Team and Starter Trends and Much, Much More The 2017 KillerSports.com Journal of MLB Research Introduction ........................................................................................................................................... 4 SDQL Overview ...................................................................................................................................... 5 Team Records vs Player Hits, By Dr Edwin F Meyer, KillerSports.com ................................................6-7 9th Inning Momentum Study, By Vince Akins, SportsBook Breakers .................................................8-9 Shutout MLB System, By Mr East. .......................................................................................................10 Series Openers, By MTi Sports Forecasting. ...................................................................................12-15 MLB Scatter Plots, By Joe Meyer, SportsDataBase.com. .....................................................................16 After a Complete Game Shutout, By John Currey, SDQL Master ....................................................18-19 Featured Starter Trend: Cole Hamels, Sports Data Query Group ........................................................21 40 Starter Trends, By Vince Akins, SportsBook Breakers ................................................................22-24 More MLB Scatter Plots, By Joe Meyer, SportsDataBase.com. -

ESP Your Sixth Sense by Brad Steiger
ESP Your Sixth Sense By Brad Steiger Contents: Book Cover (Front) (Back) Scan / Edit Notes Inside Cover Blurb 1 - Exploring Inner Space 2 - ESP, Psychiatry, and the Analyst's Couch 3 - Foreseeing the Future 4 - Telepathy, Twins, and Tuning Mental Radios 5 - Clairvoyance, Cops, and Dowsing Rod 6 - Poltergeists, Psychokinesis, and the Telegraph Key in the Soap Bubble 7 - People Who See Without Eyes 8 - Astral Projection and Human Doubles 9 - From the Edge of the Grave 10 - Mediumship and the Survival Question 11 - "PSI" and Psychedelics, and Mind-Expanding Drugs 12 - ESP in the Space Age 13 - "PSI" Research Behind the Iron Curtain 14 - Latest Experiments in ESP 15 - ESP - Test It Yourself ~~~~~~~ Scan / Edit Notes Versions available and duly posted: Format: v1.0 (Text) Format: v1.0 (PDB - open format) Format: v1.5 (HTML) Format: v1.5 (PDF - no security) Genera: ESP / Paranormal / Psychic Extra's: Pictures Included (for all versions) Copyright: 1966 / 1967 First Scanned: August - 11 - 2002 Posted to: alt.binaries.e-book Note: 1. The Html, Text and Pdb versions are bundled together in one zip file. 2. The Pdf files are sent as a single zip (and naturally does not have the file structure below) ~~~~ Structure: (Folder and Sub Folders) Main Folder - HTML Files | |- {Nav} - Navigation Files | |- {PDB} | |- {Pic} - Graphic files | |- {Text} - Text File -Salmun ~~~~~~~ Inside Cover Blurb Have you ever played a "lucky" hunch? Ever had a dream come true? Received a call or letter from someone you "just happened" to think of? Felt that "I've been here before" sensation known as Deja vu? Sensed what was "about to happen" even an instant before it occurred? Known what someone was about to say - or perhaps even spoken the exact words along with him? Then You May Be Using Your Sixth Sense Your Esp Without Even Realizing It! Recent research indicates that almost everyone possesses latent ESP powers. -

BY D~O W. CHANCE 25 Exciting Computer Games in BASIC for All Ages
BY D~O W. CHANCE 25 Exciting Computer Games in BASIC for All Ages by David W. Chance Entertaining and educational games and puzzles for the TRS-80™, Apple®, or PET®! Improve your computing skills .. turn your computer into a teaching machine that makes learning fun ... explore the real capabilities of your TRS-80, Apple, or PET ... discover ex citing and challenging new games for every skill level, every age group from four to 60-plus! It's all here in this out standing new collection of ready-to-run programs: puzzles, memory games, ac tion games, educational games, and games designed pu rely for entertai n ment. Here's a book that gives you 25 ex citing programs written in BASICforthe TRS-80. Easy-to-follow conversion in structions (including specific command changes and program line modifica tions) let you easily adapt the programs for use on an Apple or PET. Each pro gram is thoroughly explained with complete program listings, flowcharts, sample runs, and notation of memory required (some programs take as little as 4K of memory) . The author has even included suggestions for modifying programs to make them more chal lenging or for the use of additional graphics. Includes listings of REM statements to help new computerists gain a better understanding of BASIC and several " program shorts" that pro vide big computing excitment with only a little typing. You ' ll find teaching and learning games that feature graphic rewards for (continued on back flap) 25 EXCITING COMPUTER GAMES IN BASIC FOR All AGES Other TAB books by the author: No. -

What Determines WAR in Baseball Sam Eichel Mentor
What determines WAR in Baseball Sam Eichel Mentor: Jebessa Mijena Department of Mathematics Georgia College & State University 2020 1 Content Acknowledgement……………… 3 Abstract………………………..... 4 Introduction…………………….. 5 Data Analysis………………….... 6 Original Fit…………… 7 Variable Selection……. 9 All Variables Transform 10 Inverse Response……… 14 Conclusion……………………….. 18 References……………………….. 19 2 Acknowledgements I would like to thank Jebessa Mijena for mentoring me these last two semesters. I would also like to thank my family for their constant support. 3 Abstract 2020 has been a very weird year. The 2020 Baseball season was no different. Instead of the normal 162 game season, it was a very short season of 60 games. In this research, we used variable selection to determine what predictors have the highest effect on War(Wins Above Replacement). We also used several other techniques from multiple regression analysis to find the best fit for War. 4 Introduction 2020 was a very weird baseball Season. The motivation behind this project is to see what kind of effect 2020 had on a player’s WAR and how WAR differs from a normal length season. For this project I used several statistics: WAR(Wins Above Replacement), OBP(On Base Percentage), Slugging(Slugging Percentage), HRs (Home runs), RBI(Runs Batted In), wRAA(Weighted Runs Above Average), wOBA(Weighted On base Percentage), Hits, Walks, Avg(Batting Average), and Handedness. In general, WAR assesses how valuable a player is. For example, one player could hit a lot of HRs, but his WAR isn't very high because he struggles in other areas like wRAA, or wOBA. OBP measures how often a player reaches base via hit(this includes HRs) or walk. -

Cranfield University
CRANFIELD UNIVERSITY FAYE ANDREWS DESIGN OF A COTS MST DISTRIBUTED SENSOR SUITE SYSTEM FOR PLANETARY SURFACE EXPLORATION. SCHOOL OF ENGINEERING EngD. THESIS CRANFIELD UNIVERSITY SCHOOL OF ENGINEERING EngD. THESIS Academic Year 2005 FAYE ANDREWS Design of a COTS MST distributed Sensor Suite System for planetary surface exploration. Supervisors: Dr. Stephen Hobbs Dr. Ian Honstvet Dr. Robin Lane This thesis is submitted in partial fulfilment of the requirements for the degree of Engineering Doctorate. © Cranfield University 2005. All rights reserved. No part of this publication may be reproduced without the written permission of the copyright owner. ABSTRACT The aim of this project is To bring together current commercially available technology and relevant Microsystems Technology (MST) into a small, standardised spacecraft primary systems architecture, multiple units of which can demonstrate collaboration… Distributed “lab-on-a-chip” sensor networks are a possible option for the surface exploration of both Earth and Mars, and as such have been chosen as a model small spacecraft architecture. This project presents a systems approach to the design of a collection of collaborative MST sensor suites for use in a variety of environments. Based on a set of derived objectives, the main features of the study are: What are the fundamental limits to miniaturisation? What are the hardware issues raised using both standard and MST components? What is the optimum deployment pattern of the network to locate various shaped targets? What are the strategic and economic challenges of MST and the development of a sensor suite network? In general, there are few fundamental physical laws that limit the size of the sensor system. -
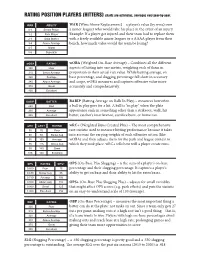
WAR (Wins Above Replacement) – a Player's Value (By Wins) Over A
RATING POSITION PLAYERS (HITTERS) charts are estimates, averages vary year-by-year. WAR ABILITY WAR (Wins Above Replacement) – a player’s value (by wins) over 0-1 Bench Player a minor leaguer who would take his place in the event of an injury. 1-2 Role Player Example: If a player got injured and their team had to replace them 2-3 Solid Starter with a freely available minor leaguer or a AAAA player from their 3-4 Above Average bench, how much value would the team be losing? 4-5 Allstar 5-6 Superstar wOBA RATING wOBA (Weighted On-Base Average) – Combines all the different .300 Poor aspects of hitting into one metric, weighting each of them in .310 Below Average proportion to their actual run value. While batting average, on- .320 Average base percentage, and slugging percentage fall short in accuracy .340 Above Average and scope, wOBA measures and captures offensive value more .370 Great accurately and comprehensively. .400 Excellent BABIP BATTER BABIP (Batting Average on Balls In Play) – measures how often .260 Bad a ball in play goes for a hit. A ball is “in play” when the plate .300 Average appearance ends in something other than a strikeout, walk, hit .350 Excellent batter, catcher’s interference, sacrifice bunt, or home run. wRC wRC+ RATING wRC+ (Weighted Runs Created Plus) – The most comprehensive 50 75 Poor rate statistic used to measure hitting performance because it takes 60 80 Below Avg into account the varying weights of each offensive action (like 65 100 Average wOBA) and then adjusts them for the park and league context in 75 115 Above Avg which they took place. -

2018 Killersports.Com MLB Annual
2018 KillerSports.com MLB Annual Featuring the SDQL MLB Studies from Handicapping and Data Experts 400+ Perfect MLB Trends and Much, Much More Contributors and Acknowledgements The 2018 MLB Annual was designed by Ed Meyer at KillerSports and Kyle Akins at SportsBookBreakers. Joe Meyer at SportsDatabase.com executed the design using Open Source tools including Ubuntu-Linux and Python-ReportLabs. The Sports Data Query Lanaguge (SDQL) was used for stats and trends. The typeface is Helvetica. The data are provided by the the peer-maintainers at the SportsDatabase-Data Google Group. Call the Gamblers Book Club at 800-522-1777 for a paper copy of this MLB Annual. Table of Contents Net Profit for each Team Page 2 Walk off Winners with Momentum Page 5 The 2017 MLB Season with the SDQL Page 6 SDQL Tables at KillerSports.com Page 15 Bankroll Growth vs Fraction Bet Page 19 Starting a Series with Rest Page 21 SDQL Research for Baseball Page 23 SDQL Trends and Stats Page 24 Common Abbreviations SDQL Sports Data Query Language SU Straight Up ATS Against the Spread O/U Over Under BL Biggest Lead BPRA Bull Pen Runs Allowed HR Home Runs HPR Hits Per Run HPU Home Plate Umpire IL Innings Led IT Innings Tied MRI Multiple Run Innings PU Pitchers Used SHA Starter's Hits Allowed SHF Starter's Hitters Faced SHRA Starter's Home Runs Allowed SIP Starter's Innings Pitched WOW Walk Off Win 1 MLB Net Profit by Team 2010 - 2017 By MTi Sports Forecasting The table below gives the net profit or loss when betting on a particular MLB team for an entire regular season. -

Effects of Immediate Feedback on ESP Performance: a Second Study
Effects of Immediate Feedback on ESP Performance: A Second Study ABSTRACT: An experiment was undertaken to replicate the successful ESP train- ing study reported earlier by Tart. The experiment again commenced with a two- stage screening process. Percipients who successfully passed the screening then completed the Training Study, 20 runs (500 trials) with immediate feedback on either the four-choice trainer (Aquarius) or a more fully automated version of the original ten-choice trainer (ADEPT), which was introduced midway through the screening phase. The screening was significantly less successful in providing talented percip- ients on the ten-choice trainers in this experiment than in the first experiment. Nevertheless, seven percipients completed the Training Study on ADEPT, but their scores as a group were close to chance. The screening was somewhat more suc- cessful with Aquarius, but only three subjects completed training on this machine. However, these percipients continued to score significantly above chance as a group. Too few sufficiently talented percipients were selected by the screening process to allow a meaningful confirmatory test of the learning hypothesis in this experi- ment, and it is concluded that the status of this hypothesis is the same as it was at the completion of the first experiment. This experiment was designed to replicate, with a minimum of procedural variation, the successful ESP learning experiment con- ducted two years earlier and reported elsewhere (Tart, 1975, 1976). Data from the first experiment provided support for several hy- potheses derived from the learning theory proposed by the first author more than 10 years ago (Tart, 1966).