Stochastic Models in Telecommunications for Optimal Design, Control and Performance Evaluation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designing Traffic Profiles for Bursty Internet Traffic
Designing Traffic Profiles for Bursty Internet Traffic Xiaowei Yang MIT Laboratory for Computer Science Cambridge, MA 02139 [email protected] Abstract An example of a non-conforming stream is one that has a This paper proposes a new class of traffic profiles that is much higher expected transmission rate than that allowed better suited for metering bursty Internet traffic streams by a traffic profile. than the traditional token bucket profile. A good traffic It is desirable to have a range of traffic profiles for differ- profile should satisfy two criteria: first, it should consider ent classes of traffic, and for differentiation within a class. packets from a conforming traffic stream as in-profile with For example, traffic streams generated by constant bit rate high probability to ensure a strong QoS guarantee; second, video applications have quite different statistics than those it should limit the network resources consumed by a non- generated by web browsing sessions, thus require different conforming traffic stream to no more than that consumed profiles to meet their QoS requirements. It is worth noting by a conforming stream. We model a bursty Internet traffic that the type of traffic we consider in this paper is most of- stream as an ON/OFF stream, where both the ON-period ten generated by document transfers, such as web browsing. and the OFF-period have a heavy-tailed distribution. Our Traditionally, the QoS requirement for such traffic (a.k.a. study shows that the heavy-tailed distribution leads to an elastic traffic) is less obvious than that for the real-time excessive randomness in the long-term session rate distribu- traffic. -

Performance Analysis I
CS 6323 Complex Networks and Systems: Modeling and Inference Lecture 5: Performance Analysis I Prof. Gregory Provan Department of Computer Science University College Cork Slides: Based on M. Yin (Performability Analysis) Overview •Queuing Models •Birth-Death Process •Poisson Process •Task Graphs Complex Networks and Systems 2 Network Modelling • We model the transmission of packets through a network using Queueing Theory • Enables us to determine several QoS metrics • Throughput times, delays, etc. • Predictive Model • Properties of queueing network depends on • Network topology • Performance for each “path” in network • Network interactions Complex Networks and Systems 3 Queuing Networks • A queuing network consists of service centers and customers (often called jobs) • A service center consists of one or more servers and one or more queues to hold customers waiting for service. : customers arrival rate : service rate 1/24/2014 Complex Networks and Systems 4 Interarrival • Interarrival time: the time between successive customer arrivals • Arrival process: the process that determines the interarrival times • It is common to assume that interarrival times are exponentially distributed random variables. In this case, the arrival process is a Poisson process : customers arrival rate : service rate 0 1 2 n 1/24/2014 Complex Networks and Systems 5 Service Time • The service time depends on how much work the customer needs and how fast the server is able to perform the work • Service times are commonly assumed to be independent, identically distributed (iid) random variables. 1/24/2014 Complex Networks and Systems 6 A Queuing Model Example Server Center 1 Server Center 2 cpu1 Disk1 cpu2 queue Disk2 Arriving customers cpu3 servers Server Center 3 Queuing delay Service time Response time 1/24/2014 Complex Networks and Systems 7 Terminology Term Explanations Buffer size The total number of customers allowed at a service center. -

Poisson Processes Stochastic Processes
Poisson Processes Stochastic Processes UC3M Feb. 2012 Exponential random variables A random variable T has exponential distribution with rate λ > 0 if its probability density function can been written as −λt f (t) = λe 1(0;+1)(t) We summarize the above by T ∼ exp(λ): The cumulative distribution function of a exponential random variable is −λt F (t) = P(T ≤ t) = 1 − e 1(0;+1)(t) And the tail, expectation and variance are P(T > t) = e−λt ; E[T ] = λ−1; and Var(T ) = E[T ] = λ−2 The exponential random variable has the lack of memory property P(T > t + sjT > t) = P(T > s) Exponencial races In what follows, T1;:::; Tn are independent r.v., with Ti ∼ exp(λi ). P1: min(T1;:::; Tn) ∼ exp(λ1 + ··· + λn) . P2 λ1 P(T1 < T2) = λ1 + λ2 P3: λi P(Ti = min(T1;:::; Tn)) = λ1 + ··· + λn P4: If λi = λ and Sn = T1 + ··· + Tn ∼ Γ(n; λ). That is, Sn has probability density function (λs)n−1 f (s) = λe−λs 1 (s) Sn (n − 1)! (0;+1) The Poisson Process as a renewal process Let T1; T2;::: be a sequence of i.i.d. nonnegative r.v. (interarrival times). Define the arrival times Sn = T1 + ··· + Tn if n ≥ 1 and S0 = 0: The process N(t) = maxfn : Sn ≤ tg; is called Renewal Process. If the common distribution of the times is the exponential distribution with rate λ then process is called Poisson Process of with rate λ. Lemma. N(t) ∼ Poisson(λt) and N(t + s) − N(s); t ≥ 0; is a Poisson process independent of N(s); t ≥ 0 The Poisson Process as a L´evy Process A stochastic process fX (t); t ≥ 0g is a L´evyProcess if it verifies the following properties: 1. -

A Stochastic Processes and Martingales
A Stochastic Processes and Martingales A.1 Stochastic Processes Let I be either IINorIR+.Astochastic process on I with state space E is a family of E-valued random variables X = {Xt : t ∈ I}. We only consider examples where E is a Polish space. Suppose for the moment that I =IR+. A stochastic process is called cadlag if its paths t → Xt are right-continuous (a.s.) and its left limits exist at all points. In this book we assume that every stochastic process is cadlag. We say a process is continuous if its paths are continuous. The above conditions are meant to hold with probability 1 and not to hold pathwise. A.2 Filtration and Stopping Times The information available at time t is expressed by a σ-subalgebra Ft ⊂F.An {F ∈ } increasing family of σ-algebras t : t I is called a filtration.IfI =IR+, F F F we call a filtration right-continuous if t+ := s>t s = t. If not stated otherwise, we assume that all filtrations in this book are right-continuous. In many books it is also assumed that the filtration is complete, i.e., F0 contains all IIP-null sets. We do not assume this here because we want to be able to change the measure in Chapter 4. Because the changed measure and IIP will be singular, it would not be possible to extend the new measure to the whole σ-algebra F. A stochastic process X is called Ft-adapted if Xt is Ft-measurable for all t. If it is clear which filtration is used, we just call the process adapted.The {F X } natural filtration t is the smallest right-continuous filtration such that X is adapted. -

Introduction to Stochastic Processes - Lecture Notes (With 33 Illustrations)
Introduction to Stochastic Processes - Lecture Notes (with 33 illustrations) Gordan Žitković Department of Mathematics The University of Texas at Austin Contents 1 Probability review 4 1.1 Random variables . 4 1.2 Countable sets . 5 1.3 Discrete random variables . 5 1.4 Expectation . 7 1.5 Events and probability . 8 1.6 Dependence and independence . 9 1.7 Conditional probability . 10 1.8 Examples . 12 2 Mathematica in 15 min 15 2.1 Basic Syntax . 15 2.2 Numerical Approximation . 16 2.3 Expression Manipulation . 16 2.4 Lists and Functions . 17 2.5 Linear Algebra . 19 2.6 Predefined Constants . 20 2.7 Calculus . 20 2.8 Solving Equations . 22 2.9 Graphics . 22 2.10 Probability Distributions and Simulation . 23 2.11 Help Commands . 24 2.12 Common Mistakes . 25 3 Stochastic Processes 26 3.1 The canonical probability space . 27 3.2 Constructing the Random Walk . 28 3.3 Simulation . 29 3.3.1 Random number generation . 29 3.3.2 Simulation of Random Variables . 30 3.4 Monte Carlo Integration . 33 4 The Simple Random Walk 35 4.1 Construction . 35 4.2 The maximum . 36 1 CONTENTS 5 Generating functions 40 5.1 Definition and first properties . 40 5.2 Convolution and moments . 42 5.3 Random sums and Wald’s identity . 44 6 Random walks - advanced methods 48 6.1 Stopping times . 48 6.2 Wald’s identity II . 50 6.3 The distribution of the first hitting time T1 .......................... 52 6.3.1 A recursive formula . 52 6.3.2 Generating-function approach . -

A Novel Simulation Based Methodology for the Congestion Control in ATM Networks
A Novel Simulation Based Methodology for the Congestion Control in ATM Networks Heven Patel, Hardik Patel, Aditya Jagannath, Syed Rizvi, Khaled Elleithy Computer Science and Engineering Department University of Bridgeport, Bridgeport, CT Abstract- In this project, we use the OPNET simulation tool client server and source destination networks with various for modeling and analysis of packet data networks. Our project protocol parameters and service categories. We also is mainly focused on the performance analysis of simulate a policing mechanism for ATM networks .In this Asynchronous transfer mode (ATM) networks. Specifically, in section we simulate the performance of the FDDI this project, we simulate two types of high-performance protocol. We consider network throughput, link networks namely, Fiber Distributed Data Interface (FDDI) utilizations, and end-to-end delay by varying network and Asynchronous Transfer Mode (ATM). In the first type of network, we examine the performance of the FDDI protocol by parameters in two network configurations. The leaky varying network parameters in two network configurations. In bucket mechanism limits the difference between the the second type, we build a simple ATM network model and negotiated mean cell rate (MCR) parameter and the actual measure its performance under various ATM service cell rate of a traffic source. It can be viewed as a bucket, categories. Finally, we develop an OPNET process model for placed immediately after each source. Each cell generated leaky bucket congestion control algorithm and examine its by the traffic source carries token and attempts to place it performance and its relative effect on the traffic patterns (loss in the bucket. -
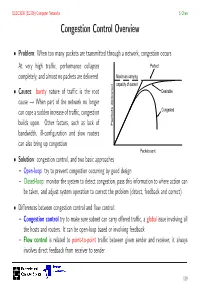
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

Non-Local Branching Superprocesses and Some Related Models
Published in: Acta Applicandae Mathematicae 74 (2002), 93–112. Non-local Branching Superprocesses and Some Related Models Donald A. Dawson1 School of Mathematics and Statistics, Carleton University, 1125 Colonel By Drive, Ottawa, Canada K1S 5B6 E-mail: [email protected] Luis G. Gorostiza2 Departamento de Matem´aticas, Centro de Investigaci´ony de Estudios Avanzados, A.P. 14-740, 07000 M´exicoD. F., M´exico E-mail: [email protected] Zenghu Li3 Department of Mathematics, Beijing Normal University, Beijing 100875, P.R. China E-mail: [email protected] Abstract A new formulation of non-local branching superprocesses is given from which we derive as special cases the rebirth, the multitype, the mass- structured, the multilevel and the age-reproduction-structured superpro- cesses and the superprocess-controlled immigration process. This unified treatment simplifies considerably the proof of existence of the old classes of superprocesses and also gives rise to some new ones. AMS Subject Classifications: 60G57, 60J80 Key words and phrases: superprocess, non-local branching, rebirth, mul- titype, mass-structured, multilevel, age-reproduction-structured, superprocess- controlled immigration. 1Supported by an NSERC Research Grant and a Max Planck Award. 2Supported by the CONACYT (Mexico, Grant No. 37130-E). 3Supported by the NNSF (China, Grant No. 10131040). 1 1 Introduction Measure-valued branching processes or superprocesses constitute a rich class of infinite dimensional processes currently under rapid development. Such processes arose in appli- cations as high density limits of branching particle systems; see e.g. Dawson (1992, 1993), Dynkin (1993, 1994), Watanabe (1968). The development of this subject has been stimu- lated from different subjects including branching processes, interacting particle systems, stochastic partial differential equations and non-linear partial differential equations. -

Simulation of Markov Chains
Copyright c 2007 by Karl Sigman 1 Simulating Markov chains Many stochastic processes used for the modeling of financial assets and other systems in engi- neering are Markovian, and this makes it relatively easy to simulate from them. Here we present a brief introduction to the simulation of Markov chains. Our emphasis is on discrete-state chains both in discrete and continuous time, but some examples with a general state space will be discussed too. 1.1 Definition of a Markov chain We shall assume that the state space S of our Markov chain is S = ZZ= f:::; −2; −1; 0; 1; 2;:::g, the integers, or a proper subset of the integers. Typical examples are S = IN = f0; 1; 2 :::g, the non-negative integers, or S = f0; 1; 2 : : : ; ag, or S = {−b; : : : ; 0; 1; 2 : : : ; ag for some integers a; b > 0, in which case the state space is finite. Definition 1.1 A stochastic process fXn : n ≥ 0g is called a Markov chain if for all times n ≥ 0 and all states i0; : : : ; i; j 2 S, P (Xn+1 = jjXn = i; Xn−1 = in−1;:::;X0 = i0) = P (Xn+1 = jjXn = i) (1) = Pij: Pij denotes the probability that the chain, whenever in state i, moves next (one unit of time later) into state j, and is referred to as a one-step transition probability. The square matrix P = (Pij); i; j 2 S; is called the one-step transition matrix, and since when leaving state i the chain must move to one of the states j 2 S, each row sums to one (e.g., forms a probability distribution): For each i X Pij = 1: j2S We are assuming that the transition probabilities do not depend on the time n, and so, in particular, using n = 0 in (1) yields Pij = P (X1 = jjX0 = i): (Formally we are considering only time homogenous MC's meaning that their transition prob- abilities are time-homogenous (time stationary).) The defining property (1) can be described in words as the future is independent of the past given the present state. -

A Representation for Functionals of Superprocesses Via Particle Picture Raisa E
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector stochastic processes and their applications ELSEVIER Stochastic Processes and their Applications 64 (1996) 173-186 A representation for functionals of superprocesses via particle picture Raisa E. Feldman *,‘, Srikanth K. Iyer ‘,* Department of Statistics and Applied Probability, University oj’ Cull~ornia at Santa Barbara, CA 93/06-31/O, USA, and Department of Industrial Enyineeriny and Management. Technion - Israel Institute of’ Technology, Israel Received October 1995; revised May 1996 Abstract A superprocess is a measure valued process arising as the limiting density of an infinite col- lection of particles undergoing branching and diffusion. It can also be defined as a measure valued Markov process with a specified semigroup. Using the latter definition and explicit mo- ment calculations, Dynkin (1988) built multiple integrals for the superprocess. We show that the multiple integrals of the superprocess defined by Dynkin arise as weak limits of linear additive functionals built on the particle system. Keywords: Superprocesses; Additive functionals; Particle system; Multiple integrals; Intersection local time AMS c.lassijication: primary 60555; 60H05; 60580; secondary 60F05; 6OG57; 60Fl7 1. Introduction We study a class of functionals of a superprocess that can be identified as the multiple Wiener-It6 integrals of this measure valued process. More precisely, our objective is to study these via the underlying branching particle system, thus providing means of thinking about the functionals in terms of more simple, intuitive and visualizable objects. This way of looking at multiple integrals of a stochastic process has its roots in the previous work of Adler and Epstein (=Feldman) (1987), Epstein (1989), Adler ( 1989) Feldman and Rachev (1993), Feldman and Krishnakumar ( 1994). -

Immigration Structures Associated with Dawson-Watanabe Superprocesses
View metadata, citation and similar papers at core.ac.uk brought to you COREby provided by Elsevier - Publisher Connector stochastic processes and their applications ELSEVIER StochasticProcesses and their Applications 62 (1996) 73 86 Immigration structures associated with Dawson-Watanabe superprocesses Zeng-Hu Li Department of Mathematics, Beijing Normal University, Be!ring 100875, Peoples Republic of China Received March 1995: revised November 1995 Abstract The immigration structure associated with a measure-valued branching process may be described by a skew convolution semigroup. For the special type of measure-valued branching process, the Dawson Watanabe superprocess, we show that a skew convolution semigroup corresponds uniquely to an infinitely divisible probability measure on the space of entrance laws for the underlying process. An immigration process associated with a Borel right superpro- cess does not always have a right continuous realization, but it can always be obtained by transformation from a Borel right one in an enlarged state space. Keywords: Dawson-Watanabe superprocess; Skew convolution semigroup; Entrance law; Immigration process; Borel right process AMS classifications: Primary 60J80; Secondary 60G57, 60J50, 60J40 I. Introduction Let E be a Lusin topological space, i.e., a homeomorphism of a Borel subset of a compact metric space, with the Borel a-algebra .N(E). Let B(E) denote the set of all bounded ~(E)-measurable functions on E and B(E) + the subspace of B(E) compris- ing non-negative elements. Denote by M(E) the space of finite measures on (E, ~(E)) equipped with the topology of weak convergence. Forf e B(E) and # e M(E), write ~l(f) for ~Efd/~. -

LECTURES 3 and 4: MARTINGALES 1. Introduction in an Arbitrage–Free
LECTURES 3 AND 4: MARTINGALES 1. Introduction In an arbitrage–free market, the share price of any traded asset at time t = 0 is the expected value, under an equilibrium measure, of its discounted price at market termination t = T . We shall see that the discounted share price at any time t ≤ T may also be computed by an expectation; however, this expectation is a conditional expectation, given the information about the market scenario that is revealed up to time t. Thus, the discounted share price process, as a (random) function of time, has the property that its value at any time t is the conditional expectation of the value at a future time given information available at t.A stochastic process with this property is called a martingale. The theory of martingales (initiated by Joseph Doob, following earlier work of Paul Levy´ ) is one of the central themes of modern probability. In discrete-time finance, the importance of martingales stems largely from the Optional Stopping Formula, which (a) places fundamental constraints on (discounted) share price processes, and (b) provides a computational tool of considerable utility. 2. Filtrations of Probability Spaces Filtrations. In a multiperiod market, information about the market scenario is revealed in stages. Some events may be completely determined by the end of the first trading period, others by the end of the second, and others not until the termination of all trading. This suggests the following classification of events: for each t ≤ T , (1) Ft = {all events determined in the first t trading periods}. The finite sequence (Ft)0≤t≤T is a filtration of the space Ω of market scenarios.