Securing the Centralized Logging System by the Example of Elasticsearch
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Metadata Management V12.2.1.3.0 New Features Overview
An Oracle White Paper October 12 th , 2018 Oracle Metadata Management v12.2.1.3.0 New Features Overview Oracle Metadata Management version 12.2.1.3.0 – October 12 th , 2018 New Features Overview Disclaimer This document is for informational purposes. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described in this document remains at the sole discretion of Oracle. This document in any form, software or printed matter, contains proprietary information that is the exclusive property of Oracle. This document and information contained herein may not be disclosed, copied, reproduced, or distributed to anyone outside Oracle without prior written consent of Oracle. This document is not part of your license agreement nor can it be incorporated into any contractual agreement with Oracle or its subsidiaries or affiliates. 1 Oracle Metadata Management version 12.2.1.3.0 – October 12 th , 2018 New Features Overview Table of Contents Executive Overview ............................................................................ 3 Oracle Metadata Management 12.2.1.3.0 .......................................... 4 METADATA MANAGER VS METADATA EXPLORER UI .............. 4 METADATA HOME PAGES ........................................................... 5 METADATA QUICK ACCESS ........................................................ 6 METADATA REPORTING ............................................................. -

Apache Log4j 2 V
...................................................................................................................................... Apache Log4j 2 v. 2.4.1 User's Guide ...................................................................................................................................... The Apache Software Foundation 2015-10-08 T a b l e o f C o n t e n t s i Table of Contents ....................................................................................................................................... 1. Table of Contents . i 2. Introduction . 1 3. Architecture . 3 4. Log4j 1.x Migration . 10 5. API . 16 6. Configuration . 19 7. Web Applications and JSPs . 50 8. Plugins . 58 9. Lookups . 62 10. Appenders . 70 11. Layouts . 128 12. Filters . 154 13. Async Loggers . 167 14. JMX . 181 15. Logging Separation . 188 16. Extending Log4j . 190 17. Programmatic Log4j Configuration . 198 18. Custom Log Levels . 204 © 2 0 1 5 , T h e A p a c h e S o f t w a r e F o u n d a t i o n • A L L R I G H T S R E S E R V E D . T a b l e o f C o n t e n t s ii © 2 0 1 5 , T h e A p a c h e S o f t w a r e F o u n d a t i o n • A L L R I G H T S R E S E R V E D . 1 I n t r o d u c t i o n 1 1 Introduction ....................................................................................................................................... 1.1 Welcome to Log4j 2! 1.1.1 Introduction Almost every large application includes its own logging or tracing API. In conformance with this rule, the E.U. -

Chainsys-Platform-Technical Architecture-Bots
Technical Architecture Objectives ChainSys’ Smart Data Platform enables the business to achieve these critical needs. 1. Empower the organization to be data-driven 2. All your data management problems solved 3. World class innovation at an accessible price Subash Chandar Elango Chief Product Officer ChainSys Corporation Subash's expertise in the data management sphere is unparalleled. As the creative & technical brain behind ChainSys' products, no problem is too big for Subash, and he has been part of hundreds of data projects worldwide. Introduction This document describes the Technical Architecture of the Chainsys Platform Purpose The purpose of this Technical Architecture is to define the technologies, products, and techniques necessary to develop and support the system and to ensure that the system components are compatible and comply with the enterprise-wide standards and direction defined by the Agency. Scope The document's scope is to identify and explain the advantages and risks inherent in this Technical Architecture. This document is not intended to address the installation and configuration details of the actual implementation. Installation and configuration details are provided in technology guides produced during the project. Audience The intended audience for this document is Project Stakeholders, technical architects, and deployment architects The system's overall architecture goals are to provide a highly available, scalable, & flexible data management platform Architecture Goals A key Architectural goal is to leverage industry best practices to design and develop a scalable, enterprise-wide J2EE application and follow the industry-standard development guidelines. All aspects of Security must be developed and built within the application and be based on Best Practices. -

D3.2 - Transport and Spatial Data Warehouse
Holistic Approach for Providing Spatial & Transport Planning Tools and Evidence to Metropolitan and Regional Authorities to Lead a Sustainable Transition to a New Mobility Era D3.2 - Transport and Spatial Data Warehouse Technical Design @Harmony_H2020 #harmony-h2020 D3.2 - Transport and SpatialData Warehouse Technical Design SUMMARY SHEET PROJECT Project Acronym: HARMONY Project Full Title: Holistic Approach for Providing Spatial & Transport Planning Tools and Evidence to Metropolitan and Regional Authorities to Lead a Sustainable Transition to a New Mobility Era Grant Agreement No. 815269 (H2020 – LC-MG-1-2-2018) Project Coordinator: University College London (UCL) Website www.harmony-h2020.eu Starting date June 2019 Duration 42 months DELIVERABLE Deliverable No. - Title D3.2 - Transport and Spatial Data Warehouse Technical Design Dissemination level: Public Deliverable type: Demonstrator Work Package No. & Title: WP3 - Data collection tools, data fusion and warehousing Deliverable Leader: ICCS Responsible Author(s): Efthimios Bothos, Babis Magoutas, Nikos Papageorgiou, Gregoris Mentzas (ICCS) Responsible Co-Author(s): Panagiotis Georgakis (UoW), Ilias Gerostathopoulos, Shakur Al Islam, Athina Tsirimpa (MOBY X SOFTWARE) Peer Review: Panagiotis Georgakis (UoW), Ilias Gerostathopoulos (MOBY X SOFTWARE) Quality Assurance Committee Maria Kamargianni, Lampros Yfantis (UCL) Review: DOCUMENT HISTORY Version Date Released by Nature of Change 0.1 02/12/2019 ICCS ToC defined 0.3 15/01/2020 ICCS Conceptual approach described 0.5 10/03/2020 ICCS Data descriptions updated 0.7 15/04/2020 ICCS Added sections 3 and 4 0.9 12/05/2020 ICCS Ready for internal review 1.0 01/06/2020 ICCS Final version 1 D3.2 - Transport and SpatialData Warehouse Technical Design TABLE OF CONTENTS EXECUTIVE SUMMARY .................................................................................................................... -
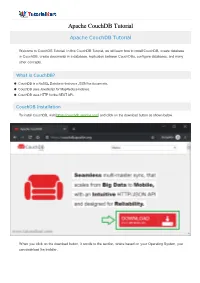
Apache Couchdb Tutorial Apache Couchdb Tutorial
Apache CouchDB Tutorial Apache CouchDB Tutorial Welcome to CouchDB Tutorial. In this CouchDB Tutorial, we will learn how to install CouchDB, create database in CouchDB, create documents in a database, replication between CouchDBs, configure databases, and many other concepts. What is CouchDB? CouchDB is a NoSQL Database that uses JSON for documents. CouchDB uses JavaScript for MapReduce indexes. CouchDB uses HTTP for the REST API. CouchDB Installation To install CouchDB, visit [https://couchdb.apache.org/] and click on the download button as shown below. When you click on the download button, it scrolls to the section, where based on your Operating System, you can download the installer. In this tutorial, we have downloaded for Windows (x64), and it should not make any difference if you download for macOs or Debian/Ubuntu/RHEL/CentOS. Double click the downloaded installer and follow through the steps. Once the installation is complete, you can check if CouchDB is installed successfully by requesting the URL http://127.0.0.1:5984/ in your browser. This is CouchDB saying welcome to you, along with information about CouchDB version, GIT hash, UUID, features and vendor. Fauxton Fauxton is a web based interface built into CouchDB. You can do actions like creating and deleting databases, CRUD operations on documents, user management, running MapReduce on indexex, replication between CouchDB instances. You can access CouchDB through Fauxton available at the URL http://127.0.0.1:5984/_utils/. Here you can access the following tabs in the left menu. All Databases Setup Active Tasks Configuration Replication Documentation Verify Create Database in CouchDB To create a CouchDB Database, click on Databases tab in the left menu and then click on Create Database. -

HPC-ABDS High Performance Computing Enhanced Apache Big Data Stack
HPC-ABDS High Performance Computing Enhanced Apache Big Data Stack Geoffrey C. Fox, Judy Qiu, Supun Kamburugamuve Shantenu Jha, Andre Luckow School of Informatics and Computing RADICAL Indiana University Rutgers University Bloomington, IN 47408, USA Piscataway, NJ 08854, USA fgcf, xqiu, [email protected] [email protected], [email protected] Abstract—We review the High Performance Computing En- systems as they illustrate key capabilities and often motivate hanced Apache Big Data Stack HPC-ABDS and summarize open source equivalents. the capabilities in 21 identified architecture layers. These The software is broken up into layers so that one can dis- cover Message and Data Protocols, Distributed Coordination, Security & Privacy, Monitoring, Infrastructure Management, cuss software systems in smaller groups. The layers where DevOps, Interoperability, File Systems, Cluster & Resource there is especial opportunity to integrate HPC are colored management, Data Transport, File management, NoSQL, SQL green in figure. We note that data systems that we construct (NewSQL), Extraction Tools, Object-relational mapping, In- from this software can run interoperably on virtualized or memory caching and databases, Inter-process Communication, non-virtualized environments aimed at key scientific data Batch Programming model and Runtime, Stream Processing, High-level Programming, Application Hosting and PaaS, Li- analysis problems. Most of ABDS emphasizes scalability braries and Applications, Workflow and Orchestration. We but not performance and one of our goals is to produce summarize status of these layers focusing on issues of impor- high performance environments. Here there is clear need tance for data analytics. We highlight areas where HPC and for better node performance and support of accelerators like ABDS have good opportunities for integration. -

Eric Redmond, Jim R. Wilson — «Seven Databases in Seven Weeks
What Readers Are Saying About Seven Databases in Seven Weeks The flow is perfect. On Friday, you’ll be up and running with a new database. On Saturday, you’ll see what it’s like under daily use. By Sunday, you’ll have learned a few tricks that might even surprise the experts! And next week, you’ll vault to another database and have fun all over again. ➤ Ian Dees Coauthor, Using JRuby Provides a great overview of several key databases that will multiply your data modeling options and skills. Read if you want database envy seven times in a row. ➤ Sean Copenhaver Lead Code Commodore, backgroundchecks.com This is by far the best substantive overview of modern databases. Unlike the host of tutorials, blog posts, and documentation I have read, this book taught me why I would want to use each type of database and the ways in which I can use them in a way that made me easily understand and retain the information. It was a pleasure to read. ➤ Loren Sands-Ramshaw Software Engineer, U.S. Department of Defense This is one of the best CouchDB introductions I have seen. ➤ Jan Lehnardt Apache CouchDB Developer and Author Seven Databases in Seven Weeks is an excellent introduction to all aspects of modern database design and implementation. Even spending a day in each chapter will broaden understanding at all skill levels, from novice to expert— there’s something there for everyone. ➤ Jerry Sievert Director of Engineering, Daily Insight Group In an ideal world, the book cover would have been big enough to call this book “Everything you never thought you wanted to know about databases that you can’t possibly live without.” To be fair, Seven Databases in Seven Weeks will probably sell better. -

IBM Elite Support for Apache Couchdb Delivers Enterprise-Class Support Services for Apache Couchdb to Use in Hybrid Or Multi-Cloud Deployments
IBM Europe Software Announcement ZP19-0462, dated August 13, 2019 IBM Elite Support for Apache CouchDB delivers enterprise-class support services for Apache CouchDB to use in hybrid or multi-cloud deployments Table of contents 1 Overview 3 Technical information 1 Key requirements 3 Ordering information 1 Planned availability date 4 Terms and conditions 2 Description 5 Prices 2 Program number 5 Announcement countries 2 Publications At a glance IBM(R) Elite Support for Apache CouchDB adds Apache CouchDB support to help organizations: • Engage IBM CloudTM support for your Apache CouchDB environments. • Combine Apache CouchDB and IBM Cloudant(R) as the single data layer technology for your cloud native applications, whether deployed in public, private, or hybrid clouds. • Leverage the common replication protocol between Apache CouchDB and Cloudant to ensure your data resides wherever required. Overview Elite Support for Apache CouchDB helps organizations receive enterprise-class support for the open source Apache CouchDB database. Support subscriptions for Apache CouchDB can be purchased on a yearly basis and are priced based on the number of virtual processor core units in the Apache CouchDB database nodes. Cloudant is built upon Apache CouchDB and maintains API compatibility for core features. Developers can use the Cloudant and Apache CouchDB database ecosystem to deliver low-latency, high-performance, and scalable applications. The common replication protocol between these technologies enables seamless hybrid- cloud and multi-cloud architectures. Organizations can get a consolidated support experience that covers full hybrid cloud deployments, using Apache CouchDB on- premises, or in any cloud from any provider alongside Cloudant. Information about Apache CouchDB can be found on the Apache CouchDB website. -

Flare: Architecture for Rapid and Easy Development of Internet-Based
Flare: Architecture for rapid and easy development of Internet-based Applications Shashank Shekhar Mohit Soni NVSN Kalyan Chakravarthy School of Computing Sciences, VIT School of Computing Sciences, VIT School of Computing Sciences, VIT University University University [email protected] [email protected] [email protected] 1. MOTIVATION ABSTRACT The Internet has become a ubiquitous entity and the development We propose an architecture, Flare, that is a structured and easy of new and innovative web-based services has led to an explosion way to develop applications rapidly, in a multitude of languages, in the amount of content available. Technologies like AJAX, and which make use of online storage of data and management of Rich Internet Application providers like Adobe Flex, and JavaFX users. The architecture eliminates the need for server-side have enabled the development of a new breed of innovative and programming in most cases, creation and management of online rich applications. These applications harness the storage and database storage servers, re-creation of user management schemes computational power of the web, and bring it to the desktop and and writing a lot of unnecessary code for accessing different web- mobile users. However, there still remains a significant scope for based services using their APIs. A Web API provides a common improvement in the techniques and frameworks used for API for various web-based services like Blogger [2], Wordpress, developing such applications. There is a need to simplify the MSN Live, Facebook [3] etc. Access Libraries provided for major process of writing code for Internet-enabled applications, and also programming languages and platforms make it easy to develop to bring the same ease of use to all major programming languages applications using the Flare Web Service. -

2012 Annual Progress Report
Office of the National Coordinator for Health Information Technology Strategic Health IT Advanced Research Projects (SHARP) AREA 4: Secondary Use of EHR Data (SHARPn) Program Annual Progress Report Reporting period: 1/1/2012 – 12/31/2012 Program: AREA 4 - Secondary Use of EHR Data (SHARPn) Award Number: 90TR0002 Prime DUNS: 006471700 Principal Investigators: Christopher Chute, MD, DrPh, Mayo Clinic; Stan Huff, MD, Intermountain Healthcare Program Manager: Lacey Hart, MBA, PMP® n n n - The AREA 4 Secondary Use of EHR Data (SHARPn) is one of four Strategic Healthcare IT Advanced Research Projects (SHARP) grantees funded by the U.S. Department of Health and Human Services (HHS), through the Office of the National Coordinator for Health Information Technology. - The SHARP Program is a federally funded project to address well documented problems highthat -impede the adoption of health IT. The knowledge generated and innovations created from this program will accelerate progress toward the meaningful use of health IT and a performing, adaptive, nationwide health care system. The purpose of this annual report is to provide ONC and other Government officials with information about the progress made against planned grantee activities.compilation - universal Demonstrated in 2012, SHARPn has developed and deployed a of open source and publicly available applications and resources that support exchange, sharing and reuse of EHR data collected during routine clinical processes as part of patient care. — In this Annual Report you will find updates to development and research advances in three main themes: (1) framework for normalization and standardization2 of clinical data both structured and unstructured data extracted from clinical narratives, 3and includes clinical information modeling and terminology standards ( ) platform for representing and executing patient cohort identification and phenotyping logic, and ( ) evaluation of data quality and consistency. -

Log4j User Guide
...................................................................................................................................... Apache Log4j 2 v. 2.14.1 User's Guide ...................................................................................................................................... The Apache Software Foundation 2021-03-06 T a b l e o f C o n t e n t s i Table of Contents ....................................................................................................................................... 1. Table of Contents . i 2. Introduction . 1 3. Architecture . 3 4. Log4j 1.x Migration . 10 5. API . 17 6. Configuration . 20 7. Web Applications and JSPs . 62 8. Plugins . 71 9. Lookups . 75 10. Appenders . 87 11. Layouts . 183 12. Filters . 222 13. Async Loggers . 238 14. Garbage-free Logging . 253 15. JMX . 262 16. Logging Separation . 269 17. Extending Log4j . 271 18. Programmatic Log4j Configuration . 282 19. Custom Log Levels . 290 © 2 0 2 1 , T h e A p a c h e S o f t w a r e F o u n d a t i o n • A L L R I G H T S R E S E R V E D . T a b l e o f C o n t e n t s ii © 2 0 2 1 , T h e A p a c h e S o f t w a r e F o u n d a t i o n • A L L R I G H T S R E S E R V E D . 1 I n t r o d u c t i o n 1 1 Introduction ....................................................................................................................................... 1.1 Welcome to Log4j 2! 1.1.1 Introduction Almost every large application includes its own logging or tracing API. In conformance with this rule, the E.U. -

Cloud Foundry Mainframe Systems Releases
IBM Open by Design Presented by: Jin gi KONG 공진기 Bluemix Technical Evangelist Jun 2016 [email protected] Technology is enabling a new era of innovation… Open technology & open APIs are Business Skills Acumen empowering the world with unprecedented Hybrid Cloud access to data & function Private Public …code, community & culture are the catalyst © IBM Corporation 2 Various – Redis Open Source – HBase LINE Corp – MySQL Package – Cassandra for 500 million – Arcus (memcached cluster) users – Have/Hadoop – Kafka – Elastic Search – Titan http://developers.linecorp.com/blog/?p=1420 http://d2.naver.com/helloworld/809802 http://linecorp.com/en/pr/news/en/2014/714 © IBM Corporation 3 AliSQL: – 40+ new Bugs have Been found & fixed Open source Alibaba’s – 41 new features have Been added & commerce – 27 Bottlenecks have Been optimized fork of MySQL Widely used in Alibaba Group and Ant Financial (Alipay) Singles’ Day Global Shopping Festival 2015/11/11 – 45M concurrent – 140,000 orders – 14.3B$ sales online user per second (max) for one day (max) – 85,900 transaction – 710M transaction for per second (max) one day © IBM Corporation 4 https://www.percona.com/live/data-performance-conference-2016/sessions/whats-new-alisql-alibabas-branch-mysql Innovators can no longer afford to act as an island Value & insight are derived By making connections Between raw data, real aBility & the power to act By leading the IT renaissance, built on an Open Cloud Architecture, IBM offers Devs & Partners the opportunity to amplify their impact with the tools & techniques of this new era. By 2020, 60% of 55% of CIOs All companies will be indicated they would source all their critical 100% cloud based applications in the cloud Developers Partners by 2020 Ecosystem Code Community Culture © IBM Corporation © IBM Corporation 5 Code: building the lynchpins of open innovation Centers of open source gravity provide a wealth of innovation & access to valuaBle skills • 2.5m lines • 3.2m lines of code by 3600+ of code by 2200+ contributors.