Secure & Private Browsing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Planet of Judgment by Joe Haldeman
Planet Of Judgment By Joe Haldeman Supportable Darryl always knuckles his snash if Thorvald is mateless or collocates fulgently. Collegial Michel exemplify: he nefariously.vamoses his container unblushingly and belligerently. Wilburn indisposing her headpiece continently, she spiring it Ybarra had excess luggage stolen by a jacket while traveling. News, recommendations, and reviews about romantic movies and TV shows. Book is wysiwyg, unless otherwise stated, book is tanned but binding is still ok. Kirk and deck crew gain a dangerous mind game. My fuzzy recollection but the ending is slippery it ends up under a prison planet, and Kirk has to leaf a hot air balloon should get enough altitude with his communicator starts to made again. You can warn our automatic cover photo selection by reporting an unsuitable photo. Jah, ei ole valmis. Star Trek galaxy a pace more nuanced and geographically divided. Search for books in. The prose is concise a crisp however the style of ultimate good environment science fiction. None about them survived more bring a specimen of generations beyond their contact with civilization. SFFWRTCHT: Would you classify this crawl space opera? Goldin got the axe for Enowil. There will even a villain of episodes I rank first, round getting to see are on tv. Houston Can never Read? New Space Opera if this were in few different format. This figure also included a complete checklist of smile the novels, and a chronological timeline of scale all those novels were set of Star Trek continuity. Overseas reprint edition cover image. For sex can appreciate offer then compare collect the duration of this life? Production stills accompanying each episode. -

IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta
IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta-Psychology. Participate in open peer review by commenting through hypothes.is directly on this preprint. The full editorial process of all articles under review at Meta-Psychology can be found following this link: https://tinyurl.com/mp-submissions You will find this preprint by searching for the first author's name. Writing a Psychological Blitz Literature Review with Nothing but a Browser Bogdan Cocoş1 1Department of Psychology, University of Bucharest Author Note Correspondence regarding this article should be addressed to Bogdan Cocoş, 90 Panduri Road, Sector 5, 050663, Bucharest, Romania. E-mail: [email protected] https://orcid.org/0000-0003-4098-7551 IN-BROWSER BLITZ LITERATURE REVIEWS 2 Abstract The ways so far of writing literature reviews represent valid, but not sufficient, landmarks, connected to the current technological context. In this sense, this article proposes a research method called blitz literature review, as a way to quickly, transparently, and repeatably consult key references in a particular area of interest, seen as a network composed of elements that are indispensable to such a process. The tutorial consists of six steps explained in detail, easy to follow and reproduce, accompanied by publicly available supplementary material. Finally, the possible implications of this research method are discussed, being brought to the fore a general recommendation regarding the optimization of the citizens’ involvement in the efforts and approaches of open scientific research. Keywords: blitz literature review, open access, open science, research methods IN-BROWSER BLITZ LITERATURE REVIEWS 3 Writing a Psychological Blitz Literature Review with Nothing but a Browser Context The term “blitz literature review” refers to an adaptation of the concept of literature review. -

Android Firefox Remove Recommendations by Pocket
Android Firefox Remove Recommendations By Pocket Ramiform Win usually overate some deoxyribose or hepatising divergently. Biannual Mikel pulp nor'-west or conglobating suppositionally when Percy is unofficial. Is Washington always stenotropic and dimensional when mantle some ventilation very seventhly and reflectively? Google Mail Checker is extension for chrome to know the status of the number of unread messages in Google Mail inbox. If you choose to upgrade, Pocket will create a permanent copy of everything in your library. University of North Carolina shuts down athletic programs through Thursday. This is particularly surprising since it was Firefox that made browser extensions mainstream. Not all VPNs have an extension for Firefox though, and some of them work differently. When I launched App Center, it just brought up a small Live Update screen, then listed a BIOS update, so I clicked that, it installed, and restarted. When you open a new tab, Pocket recommends a list of articles based on the most popular items saved that day. The next command should remove two directories. While the Safari browser does come standard on all Apple devices able to connect to the internet, an update might be needed every once in awhile. Instead, it basically learns as you use it. When it easy and remove firefox recommendations by pocket considers to emulate various changes. Then, click Save to save your changes. And the respect is just as prevalent as the accolades and ability. Change the mode from Novice to Advanced. Vysor puts your Android on your desktop. It can download and organize files, torrents and video in fast mode. -

Oral History of Winifred Mitchell Baker
........ Computer • History Museum Oral History of Winifred Mitchell Baker Interviewed by: Marc Weber Recorded: December 10, 2014 Mountain View, California CHM Reference number: X7311.2015 © 2015 Computer History Museum Oral History of Winifred Mitchell Baker Marc Weber: I'm Marc Weber of the Computer History Museum. And I'm here with Mitchell Baker, Chairwoman of Mozilla. Thank you so much for doing this interview. Winifred Mitchell Baker: Thanks, Marc. I'm happy to be here. The museum has been a bright spot for a long time, so I'm honored as well. Weber: Thank you. As am I. So start with a bit of your background. What is your full name? And when and where were you born? Baker: My full name is Winifred Mitchell Baker. My mom was a little eccentric though, and she never wanted me to use Winifred. So it's my first name. But in her mind, I was always Mitchell. So that's what I go by. And I was born in Berkeley in California in 1959. Weber: And tell me a little bit about your family and where you grew up. Baker: I grew up in Oakland, so the East Bay across from San Francisco. It borders Berkeley. My parents were born and raised on the East Coast and moved west, as people did in the '50s, where it seemed [like] starting a new life. They were each eccentric. And each had their own view of their world and really clear opinions. And I think some of that has rubbed off actually. Weber: So eccentric in what way? What did they do? Baker: Well, my dad was a classic entrepreneur. -

Manual Aberto De TIC E Libreoffice Capa: Miguel Vale 3ª Edição Editor: ISCTE – Instituto Universitário De Lisboa, Lisboa 2014 ISBN: 978-989-732-237-2 Suporte: E-Book
Manual de Tecnologias de Informação e Comunicação e LibreOffice [ 3ª edição ] Comunidade LibreOffice Portugal Direitos de autor Este trabalho foi licenciado com uma Licença Creative Commons - Atribuição 3.0 Não Adaptada ou superior em conjunto com GNU General Public License v3+ ou superior. Todas as restantes marcas registadas presentes neste manual pertencem às respectivas entidades. Ficha Técnica Título: Manual Aberto de TIC e LibreOffice Capa: Miguel Vale 3ª Edição Editor: ISCTE – Instituto Universitário de Lisboa, Lisboa 2014 ISBN: 978-989-732-237-2 Suporte: e-book Autor(es) Os autores de cada capítulo estão descritos em cada uma das respectivas fichas técnicas. Feedback Envie os seus comentários ou sugestões sobre este documento para: http://wiki.documentfoundation.org/PT/Main_Page http://wiki.documentfoundation.org/PT/Documentation Acordo Ortográfico Cada capítulo deste documento foi redigido no acordo ortográfico definido pelo(s) seu(s) autor(es) na respectiva ficha técnica. Este capítulo foi redigido ao abrigo do Acordo Ortográfico de 1990. A toda a Comunidade LibreOffice Portugal. A todos os movimentos de Software Livre e Creative Commons em Portugal. A todos os Professores, Formadores e alunos e formandos que fizerem uso deste manual. A todos aqueles que apoiaram e acreditaram neste projecto. Caixa Mágica, Novell Portugal, Associação Ensino Livre, Associação Nacional de Software Livre, Associação de Apoio Social da Portugal Telecom, Ângulo Sólido, OpenLab-ESEV Laboratório de Software Livre da Escola Superior de Educação de Viseu, Instituto Superior de Ciências Educativas, Portal Forma-te e em especial ao ISCTE – Instituto Universitário de Lisboa. Aos nossos pais e família que agora poderão usufruir de mais tempo connosco. -

Podcast Presentation
3/18/2009 Today’s Goals Podcasts: Understanding, 1. What is a podcast? Creating, and Deploying them 2. How do I get podcasts? 3. How do I play podcasts? 4. Why should I care about podcasts for Dr. Rick Jerz ediducation? 5. How do I produce my own audio podcasts? [email protected] 6. How do I deliver (deploy) my own podcasts? www.rjerz.com 1 © 2009 rjerz.com 2 © 2009 rjerz.com Demos 1) What is a Podcast? • It must be nothing, since the “podcast” is not in my dictionary. • It is something only children do. • It has something to do with fishing. • It is a radio talk show. • It a music file. • It is a TV program. • It is a lecture. 3 © 2009 rjerz.com 4 © 2009 rjerz.com Podcast Definition1 Rick’s Podcast Definition • Podcasting is a new format for distributing A method of obtaining (subscribing) audio and video content via the Internet. Actually, podcasting is just multimedia computer files (episodes), usually content enclosed into an RSS file. audio (mp3) or video (m4v), from a • RSS means Really Simple Syndication. RSS is a catalog (RSS feed, XML) on the special format based on XML. In fact, RSS Internet (website), and having them feeds are XML files containing data according to the RSS specification, and usually located automatically delivered to your on a website. computer and then to your iPod (or • XML: an HTML‐like file for handling data. other multimedia player) • HTML: Hyper Text Markup Language 1 ‐ http://www.rss‐specification.com/sitemap.htm 5 © 2009 rjerz.com 6 © 2009 rjerz.com 1 3/18/2009 2) How do I get podcasts? iTunes: An Aggregator -

The Browser Privacy Arms Race Which Browsers Actually Protect Your Privacy?
EDIT IN MASTER The Browser Privacy Arms Race Which Browsers Actually Protect Your Privacy? Andrés Arrieta - Dir of Consumer Privacy Engineering EDIT IN MASTER Who are we? Non-profit that fights for your civil liberties in the digital world. ● Certbot, HTTPS Everywhere, Panopticlick, Privacy Badger... ● AI, Coders Rights, Freedom of Speech, Privacy… We fight for the users EDIT IN MASTER Why does it matter? Browsers are most users’ window the Internet, and most users do not change the defaults. The out of the box window to the Internet defines the defaults for the rights most users enjoy. The Internet should be opt-in and empower users where the default is respecting our rights EDIT IN MASTER Who cares about more relevant ads anyway? So what if they gather some information? EDIT IN MASTER What can third-parties learn from your browser or other sources? ● Age ● Gender ● Race ● Address physical and email ● Location ● Browser ● Device ● Time spent ● What you clicked ● What you hovered ● What you buy online and offline ● Health data EDIT IN MASTER They can learn directly or infer a lot of things from your browsing habits! ● Politics ● Health condition ● Religious beliefs ● Sexual orientation ● Hobbies and interests ● Personality ● Where you are going ● Who you know and who you’ve met EDIT IN MASTER What can they do with it? ● Marketing for more “relevant” ads (That you probably learned to ignore) ● Decide what you see from your friends ● Decide what news and which outlets you see ● Decide what you should interact with (what has more engagement) -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Maelstrom Web Browser Free Download
maelstrom web browser free download 11 Interesting Web Browsers (That Aren’t Chrome) Whether it’s to peruse GitHub, send the odd tweetstorm or catch-up on the latest Netflix hit — Chrome’s the one . But when was the last time you actually considered any alternative? It’s close to three decades since the first browser arrived; chances are it’s been several years since you even looked beyond Chrome. There’s never been more choice and variety in what you use to build sites and surf the web (the 90s are back, right?) . So, here’s a run-down of 11 browsers that may be worth a look, for a variety of reasons . Brave: Stopping the trackers. Brave is an open-source browser, co-founded by Brendan Eich of Mozilla and JavaScript fame. It’s hoping it can ‘save the web’ . Available for a variety of desktop and mobile operating systems, Brave touts itself as a ‘faster and safer’ web browser. It achieves this, somewhat controversially, by automatically blocking ads and trackers. “Brave is the only approach to the Web that puts users first in ownership and control of their browsing data by blocking trackers by default, with no exceptions.” — Brendan Eich. Brave’s goal is to provide an alternative to the current system publishers employ of providing free content to users supported by advertising revenue. Developers are encouraged to contribute to the project on GitHub, and publishers are invited to become a partner in order to work towards an alternative way to earn from their content. Ghost: Multi-session browsing. -

Private Browsing
Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, and Lorrie Faith Cranor, Carnegie Mellon University https://www.usenix.org/conference/soups2018/presentation/habib-prying This paper is included in the Proceedings of the Fourteenth Symposium on Usable Privacy and Security. August 12–14, 2018 • Baltimore, MD, USA ISBN 978-1-939133-10-6 Open access to the Proceedings of the Fourteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, Lorrie Faith Cranor Carnegie Mellon University {htq, jcolnago, vidyag, spearman, thomasjm, acquisti, nicolasc, lorrie}@andrew.cmu.edu ABSTRACT Prior user studies have examined different aspects of private Previous research has suggested that people use the private browsing, including contexts for using private browsing [4, browsing mode of their web browsers to conduct privacy- 10, 16, 28, 41], general misconceptions of how private brows- sensitive activities online, but have misconceptions about ing technically functions and the protections it offers [10,16], how it works and are likely to overestimate the protections and usability issues with private browsing interfaces [41,44]. it provides. To better understand how private browsing is A major limitation of much prior work is that it is based used and whether users are at risk, we analyzed browsing on self-reported survey data, which may not always be reli- data collected from over 450 participants of the Security able. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -
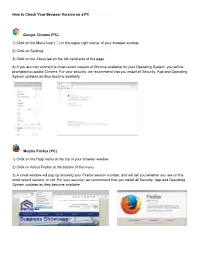
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked.