Finding Your MAC Address
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Life Cycle of Municipal Wi-Fi
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Tseng, Chien-Kai; Huang, Kuang-Chiu Conference Paper Life Cycle of Municipal Wi-Fi 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017 Provided in Cooperation with: International Telecommunications Society (ITS) Suggested Citation: Tseng, Chien-Kai; Huang, Kuang-Chiu (2017) : Life Cycle of Municipal Wi- Fi, 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017, International Telecommunications Society (ITS), Calgary This Version is available at: http://hdl.handle.net/10419/168493 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. -

Long Term Evolution (LTE)
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-ISSN: 2278-2834,p- ISSN: 2278-8735. Volume 7, Issue 3 (Sep. - Oct. 2013), PP 36-42 www.iosrjournals.org Long Term Evolution (LTE) 1 2 3 4 Emad Kazi , Rajan Pillai , Uzair Qureshi , Awab Fakih 1,2,3,4 (Electronics and Telecommunication, Anjuman-I-Islam’s Kalsekar technical campus (AIKTC), Mumbai University, India) Abstract:The number of people using mobile phone in the world has exceeded 4.5 billion and this figure is continuing to grow. For the past several years, mobile data traffic such as internet access, the downloading of music and video communication has been nearly tripling every year. With the popularity of smartphones, mobile data traffic will increase 200 times in the 7 to 8 years upto 2020.There are high expectations that Long Term Evolution (LTE) which is known as 3.9G wireless system will be a new service platform that can support a huge amount of mobile data traffic. This paper describes the features, technology and network architecture of LTE & also provides an overview of next generation telecommunication network LTE, which is started commercially in December 2010 in Japan (started by DOCOMO), realizing high speed wireless access. It also outlines the further trends towards a further speed increase. Keywords-Circuit Switching, GSM, HSPA, LTE, Packet Switching, WiMAX I. Introduction In times when mobile devices are getting more popular the mobile network are becoming more and more important too. Websites are not same they used to be 10 years ago. They consist of with quality pictures, animation, flash application and more. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
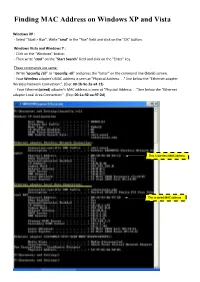
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -
Wireless Networking Summary 11-4 Bluetooth, Wimax, and RFID Questions and Problems
11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 412 Wireless 11 Networking CHAPTER 11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 413 CHAPTER OUTLINE 11-1 Introduction 11-5 Securing Wireless LANs 11-2 The IEEE 802.11 Wireless LAN 11-6 Configuring a Point-to-Multipoint Standard Wireless LAN: A Case Study 11-3 802.11 Wireless Networking Summary 11-4 Bluetooth, WiMAX, and RFID Questions and Problems OBJECTIVES ● Define the features of the 802.11 wireless ● Examine how site surveys are done for wire- LAN standard less LANs ● Understand the components of the wireless ● Investigate the issues of securing a wireless LAN LAN ● Explore how wireless LANs are configured ● Explore how to configure a point-to-multi- point wireless LAN KEY TERMS WLAN pseudorandom WiMAX Basic Service Set (BSS) hopping sequence BWA ad hoc OFDM NLOS access point U-NII last mile transceiver MIMO Radio Frequency Extended Service Set Wi-Fi Identification (RFID) (ESS) SSID backscatter hand-off site survey Slotted Aloha roaming inquiry procedure beacon CSMA/CA paging procedure WPA DSSS piconet EAP ISM pairing RADIUS FHSS Passkey 413 11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 414 11-1 INTRODUCTION WLAN This chapter examines the features and technologies used in the wireless local area Wireless local area network network (WLAN). Wireless networking is an extension of computer networks into the RF (radio frequency) world. The WLAN provides increased flexibility and mo- bility for connecting to a network. A properly designed WLAN for a building pro- vides mobile access for a user from virtually any location in the building. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Attacking the Spanning Tree Protocol
C H A P T E R 3 Attacking the Spanning Tree Protocol Radia Perlman, a distinguished engineer at Sun Microsystems, named as one of the 20 most influential people in the industry in the 25th anniversary issue of Data Communications magazine and the original inventor of the 802.1D spanning-tree specification recently had a few words to say about the protocol: “It’s time to redo (one of the Internet’s most widely used technologies) in a way that is more robust and gives more efficient paths.”1 Introducing Spanning Tree Protocol Chapter 2, “Defeating a Learning Bridge’s Forwarding Process,” explained how Ethernet switches build their forwarding tables by learning source MAC addresses from data traffic. When an Ethernet frame arrives on a switch port in VLAN X with a destination MAC address for which there is no entry in the forwarding table, the switch floods the frame. That is, it sends a copy of the frame to every single port in VLAN X (except the port that originally received the frame). Although this is perfectly fine in a single-switch environment, interesting side effects are observed in multiswitch topologies, as Figure 3-1 shows. The figure represents a simple network composed of two LAN switches interconnected by two Ethernet links. 44 Chapter 3: Attacking the Spanning Tree Protocol Figure 3-1 Basic Network Setup MAC-address 0000.0000.000A 0/1 A B All Interfaces Are Switch 1 in VLAN 5 Link Y Link X Switch 2 0/2 MAC-address 0000.0000.000B In the next steps, MAC addresses are conveniently shortened to a single-letter format for clarity. -
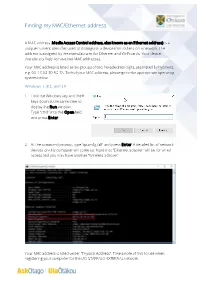
Finding My MAC/Ethernet Address
Finding my MAC/Ethernet address A MAC address (Media Access Control address, also known as an Ethernet address) is a unique numeric identifier used to distinguish a device from others on a network. The address is assigned by the manufacturer for Ethernet and Wi-Fi cards. Your device therefore is likely to have two MAC addresses. Your MAC address is listed as six groups of two hexadecimal digits, separated by hyphens, e.g. 00-13-02-80-92-7A. To find your MAC address, please go to the appropriate operating system below. Windows 7, 8.1, and 10 1. Hold the Windows key and the R keys down at the same time to display the Run window. Type "cmd" into the Open field and press Enter. 2. At the command prompt, type "ipconfig /all" and press Enter. A detailed list of network devices on this computer will come up. Note that "Ethernet adapter" will be for wired access and you may have another "Wireless adapter". Your MAC address is listed under "Physical Address". Take a note of this to use when registering your computer for the UO-STAFF/UO-EXTERNAL network. Mac OS X 1. From the Apple drop-down menu open System Preferences and click on Network. 2. If you want to register for wired access, select Ethernet from the list on the left. 3. Click the Advanced… button and select the Hardware tab to see the MAC address for your Ethernet card. 4. If you need to register for wireless access, click Cancel then select Wi-Fi from the list on the left. -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

Wireless LAN/MAN Modem Product Directory
Wireless LAN/MAN Modem Product Directory Compiled by Barry McLarnon, VE3JF. Please send comments, corrections and additions to [email protected]. Introduction After a long hiatus, I've started working on updating these pages again. Currently I'm concentrating on checking the vendor info and URLs, and then I'll get more into the product data and other stuff. I've dropped the color coding to highlight changes, as it was too much of a headache to maintain. Instead, I'm keeping a in which I'll record the changes as I make them. This is a survey of currently available wireless RF modem products suitable for wireless LAN and MAN applications. At the moment, this survey includes only those products which are suitable for unlicenced operation in the ISM bands: 900 MHz (902-928 MHz), 2.4 GHz (2400-2483.5 MHz) and 5.8 GHz (5725-5850 MHz). Some of these products are intended for very short range wireless applications, while others are designed to be used as longer-haul point-to-point wireless bridges, and some can be used in either role. No attempt has been made to differentiate between these usages in this survey. Also, I don't necessarily list every product in each vendor's wireless product line. Some product lines have many different variants, and the tables would get too unwieldy if I tried to list them all, but I try to include some representative products from each manufacturer. I tend to omit the "access point" products, and products in which the WLAN modem is integrated into something else, such as a portable computer.