Wireless Communications PURPOSE the Purpose of This Policy Is to Define Connection to the District’S Network Through Wireless Networking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Life Cycle of Municipal Wi-Fi
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Tseng, Chien-Kai; Huang, Kuang-Chiu Conference Paper Life Cycle of Municipal Wi-Fi 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017 Provided in Cooperation with: International Telecommunications Society (ITS) Suggested Citation: Tseng, Chien-Kai; Huang, Kuang-Chiu (2017) : Life Cycle of Municipal Wi- Fi, 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017, International Telecommunications Society (ITS), Calgary This Version is available at: http://hdl.handle.net/10419/168493 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. -

Long Term Evolution (LTE)
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-ISSN: 2278-2834,p- ISSN: 2278-8735. Volume 7, Issue 3 (Sep. - Oct. 2013), PP 36-42 www.iosrjournals.org Long Term Evolution (LTE) 1 2 3 4 Emad Kazi , Rajan Pillai , Uzair Qureshi , Awab Fakih 1,2,3,4 (Electronics and Telecommunication, Anjuman-I-Islam’s Kalsekar technical campus (AIKTC), Mumbai University, India) Abstract:The number of people using mobile phone in the world has exceeded 4.5 billion and this figure is continuing to grow. For the past several years, mobile data traffic such as internet access, the downloading of music and video communication has been nearly tripling every year. With the popularity of smartphones, mobile data traffic will increase 200 times in the 7 to 8 years upto 2020.There are high expectations that Long Term Evolution (LTE) which is known as 3.9G wireless system will be a new service platform that can support a huge amount of mobile data traffic. This paper describes the features, technology and network architecture of LTE & also provides an overview of next generation telecommunication network LTE, which is started commercially in December 2010 in Japan (started by DOCOMO), realizing high speed wireless access. It also outlines the further trends towards a further speed increase. Keywords-Circuit Switching, GSM, HSPA, LTE, Packet Switching, WiMAX I. Introduction In times when mobile devices are getting more popular the mobile network are becoming more and more important too. Websites are not same they used to be 10 years ago. They consist of with quality pictures, animation, flash application and more. -
Wireless Networking Summary 11-4 Bluetooth, Wimax, and RFID Questions and Problems
11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 412 Wireless 11 Networking CHAPTER 11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 413 CHAPTER OUTLINE 11-1 Introduction 11-5 Securing Wireless LANs 11-2 The IEEE 802.11 Wireless LAN 11-6 Configuring a Point-to-Multipoint Standard Wireless LAN: A Case Study 11-3 802.11 Wireless Networking Summary 11-4 Bluetooth, WiMAX, and RFID Questions and Problems OBJECTIVES ● Define the features of the 802.11 wireless ● Examine how site surveys are done for wire- LAN standard less LANs ● Understand the components of the wireless ● Investigate the issues of securing a wireless LAN LAN ● Explore how wireless LANs are configured ● Explore how to configure a point-to-multi- point wireless LAN KEY TERMS WLAN pseudorandom WiMAX Basic Service Set (BSS) hopping sequence BWA ad hoc OFDM NLOS access point U-NII last mile transceiver MIMO Radio Frequency Extended Service Set Wi-Fi Identification (RFID) (ESS) SSID backscatter hand-off site survey Slotted Aloha roaming inquiry procedure beacon CSMA/CA paging procedure WPA DSSS piconet EAP ISM pairing RADIUS FHSS Passkey 413 11_0131358383_ch11s.qxd 8/1/08 1:04 PM Page 414 11-1 INTRODUCTION WLAN This chapter examines the features and technologies used in the wireless local area Wireless local area network network (WLAN). Wireless networking is an extension of computer networks into the RF (radio frequency) world. The WLAN provides increased flexibility and mo- bility for connecting to a network. A properly designed WLAN for a building pro- vides mobile access for a user from virtually any location in the building. -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

Wireless LAN/MAN Modem Product Directory
Wireless LAN/MAN Modem Product Directory Compiled by Barry McLarnon, VE3JF. Please send comments, corrections and additions to [email protected]. Introduction After a long hiatus, I've started working on updating these pages again. Currently I'm concentrating on checking the vendor info and URLs, and then I'll get more into the product data and other stuff. I've dropped the color coding to highlight changes, as it was too much of a headache to maintain. Instead, I'm keeping a in which I'll record the changes as I make them. This is a survey of currently available wireless RF modem products suitable for wireless LAN and MAN applications. At the moment, this survey includes only those products which are suitable for unlicenced operation in the ISM bands: 900 MHz (902-928 MHz), 2.4 GHz (2400-2483.5 MHz) and 5.8 GHz (5725-5850 MHz). Some of these products are intended for very short range wireless applications, while others are designed to be used as longer-haul point-to-point wireless bridges, and some can be used in either role. No attempt has been made to differentiate between these usages in this survey. Also, I don't necessarily list every product in each vendor's wireless product line. Some product lines have many different variants, and the tables would get too unwieldy if I tried to list them all, but I try to include some representative products from each manufacturer. I tend to omit the "access point" products, and products in which the WLAN modem is integrated into something else, such as a portable computer. -
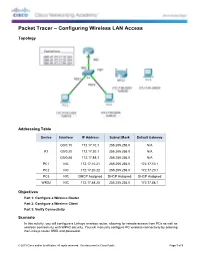
Packet Tracer – Configuring Wireless LAN Access
Packet Tracer – Configuring Wireless LAN Access Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0.10 172.17.10.1 255.255.255.0 N/A R1 G0/0.20 172.17.20.1 255.255.255.0 N/A G0/0.88 172.17.88.1 255.255.255.0 N/A PC1 NIC 172.17.10.21 255.255.255.0 172.17.10.1 PC2 NIC 172.17.20.22 255.255.255.0 172.17.20.1 PC3 NIC DHCP Assigned DHCP Assigned DHCP Assigned WRS2 NIC 172.17.88.25 255.255.255.0 172.17.88.1 Objectives Part 1: Configure a Wireless Router Part 2: Configure a Wireless Client Part 3: Verify Connectivity Scenario In this activity, you will configure a Linksys wireless router, allowing for remote access from PCs as well as wireless connectivity with WPA2 security. You will manually configure PC wireless connectivity by entering the Linksys router SSID and password. © 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 3 Packet Tracer – Configuring Wireless LAN Access Part 1: Configure a Wireless Router Step 1: Connect the Internet interface of WRS2 to S1. Connect the WRS2 Internet interface to the S1 F0/7 interface. Step 2: Configure the Internet connection type. a. Click WRS2 > GUI tab. b. Set the Internet Connection type to Static IP. c. Configure the IP addressing according to the Addressing Table. Step 3: Configure the network setup. a. Scroll down to Network Setup. For the Router IP option, set the IP address to 172.17.40.1 and the subnet mask to 255.255.255.0. -

87.35 Wireless Local Area Network (LAN)
BUSINESS POLICIES AND PROCEDURES MANUAL INFORMATION SECURITY 87.35.1 New 7-20 Information Technology Services 509-335-4357 Wireless Local Area Network (LAN) Management OVERVIEW Wireless networks allow for accelerated delivery of network connectivity at a lower cost than traditional wired networks. Because of this, wireless networks have overtaken wired networks in terms of total data transmitted and have become a cornerstone of digital service delivery. Wireless networks present unique challenges in their administration, including the following: • Shared Spectrum – Wireless data networks using the IEEE 802.11 specification operate in the 2.4 GHz or 5 GHz radio spectrums. Both frequencies must be shared by all applications utilizing them in the same coverage area. This can be a problem if adjacent departments in the same building or area independently operate wireless local area networks (LANs). Problems may also be caused in the 2.4 GHz spectrum by other competing applications, such as microwave ovens or some cordless telephones. • Nonoverlapping Channels – Both frequencies are limited by the number of nonoverlapping channels that are available with the 2.4 GHz frequency limited to only three nonoverlapping channels and the 5 GHz frequency limited to 23 nonoverlapping channels. • Security – Wireless networks have unique security requirements to prevent rogue devices from connecting to, or interfering with, the WSU network. For the above reasons the following requirements are necessary. See BPPM 87.01 for definitions related to this section. Purpose The wireless LAN policy (BPPM 87.35) provides assurance of the security and operability of the wireless LAN segments thought out the University. Scope This policy applies to all institutional business units, workforce members, and institutional information systems that collect, store, process, share, or transmit institutional data. -

Wireless LAN Networking White Paper
Wireless LAN Networking White Paper Introduction • Roaming capability is desired; e.g., maintaining connectivity from almost anywhere inside a Wireless technology has helped to simplify home or business networking by enabling multiple computer • Network access is desired outdoors; e.g., users to simultaneously share resources outside a home or office building in a home or business without additional or intrusive wiring. These resources might include a broadband Internet connection, network Wireless LANs in the Office printers, data files, and even streaming audio and video. This kind of resource sharing has An 802.11 network is the ideal solution for a become more prevalent as computer users network administrator in many respects. No have changed their habits from using single, longer is it a requirement that every workstation stand-alone computers to working on networks and conference room be wired up to hubs and with multiple computers, each with potentially switches with cables in hard-to-reach areas. different operating systems and varying Wireless networking allows for impromptu peripheral hardware. U.S. Robotics wireless meetings in cafeterias, hallways, courtyards, networking products offer a variety of solutions or wherever inspiration strikes while providing to seamlessly integrate computers, peripherals, real-time LAN connectivity for business and data. applications such as sending e-mail, working on spreadsheets on shared drives, and Wireless networking enables the same capabilities conducting market research. and comparable speeds of a wired 10BASE-T network without the difficulties associated with laying wire, drilling into walls, or stringing Wireless LANs in the Home Ethernet cables throughout an office building Wireless networking has become commonplace, or home. -

User Guide Model Number RAC2V1A 802.11Ac Wave 2 Router
User Guide Model Number RAC2V1A 802.11ac Wave 2 Router C2V1A Router User Guide 1 Table of Contents 1. Overview ............................................................... 5 1.1. Introduction .................................................................................................. 5 2. Product Overview ............................................... 6 2.1. About The Router ....................................................................................... 6 2.2. What's in the Box? ..................................................................................... 6 2.3. Items You Need ........................................................................................... 6 2.4. About This Manual ...................................................................................... 7 3. System Requirements ........................................ 8 3.1. Recommended Hardware ........................................................................ 8 3.2. Windows ........................................................................................................ 8 3.3. Mac OS ........................................................................................................... 8 3.4. Linux/Unix ..................................................................................................... 8 3.5. Mobile Devices ............................................................................................. 8 4. Installing the Router ........................................... 9 4.1. Front Panel ................................................................................................... -

Bluetooth and Wi-Fi Wireless Protocols: a Survey and a Comparison Erina Ferro and Francesco Potorti`, Institute of the National Research Council (Isti—Cnr)
ACCEPTED FROM OPEN CALL BLUETOOTH AND WI-FI WIRELESS PROTOCOLS: A SURVEY AND A COMPARISON ERINA FERRO AND FRANCESCO POTORTI`, INSTITUTE OF THE NATIONAL RESEARCH COUNCIL (ISTI—CNR) ABSTRACT ging. Another advantage lies in the way new wireless users can dynamically join or leave the Bluetooth and IEEE 802.11 (Wi-Fi) are two network, move among different environments, communication protocol standards that define a create ad hoc networks for a limited time, and physical layer and a MAC layer for wireless then leave. Wireless networks are simple to communications within a short range (from a deploy, and in some cases cost less than wired few meters up to 100 m) with low power con- LANs. Nevertheless, the technological chal- sumption (from less than 1 mW up to 100 mW). lenges involved in wireless networks are not triv- Bluetooth is oriented to connecting close devices, ial, leading to disadvantages with respect to serving as a substitute for cables, while Wi-Fi is cabled networks, such as lower reliability due to oriented toward computer-to-computer connec- interference, higher power consumption, data tions, as an extension of or substitution for security threats due to the inherent broadcast cabled LANs. In this article we offer an overview properties of the radio medium, worries about of these popular wireless communication stan- user safety due to continued exposition to radio Bluetooth and IEEE dards, comparing their main features and behav- frequency, and lower data rates. iors in terms of various metrics, including Currently the wireless scene is held by two 802.11 (Wi-Fi) are capacity, network topology, security, quality of standards: the Bluetooth and IEEE 802.11 pro- service support, and power consumption. -

Ts 124 244 V12.2.0 (2015-04)
ETSI TS 1124 244 V12.2.0 (201515-04) TECHNICAL SPECIFICATION Universal Mobile Telelecommunications System ((UMTS); LTE; Wireless LALAN control plane protocol for trusteted WLAN access to EPC; Stage 3 (3GPP TS 24.2.244 version 12.2.0 Release 12) 3GPP TS 24.244 version 12.2.0 Release 12 1 ETSI TS 124 244 V12.2.0 (2015-04) Reference RTS/TSGC-0124244vc20 Keywords LTE,UMTS ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -

Wireless LAN/Bluetooth Precautions for Use GN-4030
MULTIFUNCTIONAL DIGITAL COLOR SYSTEMS / MULTIFUNCTIONAL DIGITAL SYSTEMS Wireless LAN/Bluetooth Precautions for Use GN-4030 © 2020 Toshiba Tec Corporation All rights reserved Under the copyright laws, this manual cannot be reproduced in any form without prior written permission of Toshiba Tec Corporation. Preface Thank you for purchasing our product. This manual explains the precautions for Wireless LAN/Bluetooth Module GN-4030. Read this manual before using the functions. How to read this manual Symbols in this manual In this manual, some important items are described with the symbols shown below. Be sure to read these items before using this equipment. Indicates a potentially hazardous situation which, if not avoided, could result in death, serious injury, or serious damage, or fire in the equipment or surrounding objects. Indicates a potentially hazardous situation which, if not avoided, may result in minor or moderate injury, partial damage to the equipment or surrounding objects, or loss of data. Indicates information to which you should pay attention when operating the equipment. Describes handy information that is useful to know when operating the equipment. Pages describing items related to what you are currently doing. See these pages as required. Target audience for this manual This is a manual that is aimed at general users and administrators. Model and series names in this manual In this manual, each model name is replaced with the series name as shown below. Model name Series name e-STUDIO330AC/400AC e-STUDIO400AC Series Options For the available options, refer to the Quick Start Guide for this equipment. Trademarks For trademarks, refer to the Safety Information.