Kaspersky Anti Virus Renewal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cost of a Cyber Incident)
CO ST OF A CYBER INCIDENT: S YSTEMATIC REVIEW AND C ROSS-VALIDATION OCTOBER 26, 2020 1 Acknowledgements We are grateful to Dr. Allan Friedman, Dr. Lawrence Gordon, Jay Jacobs, Dr. Sasha Romanosky, Matthew Shabat, Kelly Shortridge, Steven Surdu, David Tobar, Brett Tucker and Sounil Yu for the review comments and helpful feedback on the earlier draft of the report. The authors would like to thank CISA staff for support and advice on this project. 2 Table of Contents 1. Objectives .................................................................................................................................................................... 7 2. Results in Brief .......................................................................................................................................................... 8 3. Analysis ...................................................................................................................................................................... 16 3.1. Per-Incident Cost and Loss Estimates .............................................................................................. 18 3.1.1. Cross-Validation: Primary Loss Data for Large and Small Incidents .................................. 20 3.1.2. Reconciliation of Per-Incident Cost Studies .................................................................................. 26 3.1.3. Per-Record Estimates ............................................................................................................................. 29 3.2. Aggregate -

Usability and Security of Personal Firewalls
Usability and Security of Personal Firewalls Almut Herzog^ and Nahid Shahmehri^ Dept. of Computer and Information Science, Linkopings universitet,Sweden {almhe, nahsh}@ida.liu.se Abstract. Effective security of a personal firewall depends on (1) the rule granularity and the implementation of the rule enforcement and (2) the correctness and granularity of user decisions at the time of an alert. A misconfigured or loosely configured firewall may be more dangerous than no firewall at all because of the user's false sense of security. This study assesses effective security of 13 personal firewalls by comparing possible granularity of rules as well as the usability of rule set-up and its influence on security. In order to evaluate usability, we have submitted each firewall to use cases that require user decisions and cause rule creation. In order to evaluate the firewalls' security, we analysed the created rules. In ad dition, we ran a port scan and replaced a legitimate, network-enabled application with another program to etssess the firewalls' behaviour in misuse cases. We have conducted a cognitive walkthrough paying special attention to user guidance and user decision support. We conclude that a stronger emphasis on user guidance, on conveying the design of the personal firewall application, on the principle of least privilege and on implications of default settings would greatly enhance both usability and security of personal firewalls. 1 Introduction In times where roaming users connect their laptops to a variety of public, pri vate and corporate wireless or wired networks and in times where more and more computers are always online, host-based firewalls implemented in soft ware, called personal firewalls, have become an important part of the security armour of a personal computer. -

EC-Council Network Security Administrator (Exam 312-38)
Product Information Sheet Exam 312-38 EC-Council Network Security Administrator (Exam 312-38) Page | 1 ENSAv4 Copyright © by EC-Council All Rights Reserved. Reproduction is Strictly Prohibited. Product Information Sheet Exam 312-38 EC-Council NSA is CNSS 4011 Certified The Committee on National Security Systems (CNSS)/National Security Agency (NSA) of the United States of America certified EC-Council’s Network Security Administrator (ENSA) course as having met 100% of the requirements as set out by the Committee on National Security Systems (CNSS) National Standards 4011. This certification is managed by the Information Assurance Courseware Evaluation (IACE) Program, National INFOSEC (Information Security) Education and Training Program and is administered by the U.S. National Security Agency (NSA). The Committee on National Security Systems (CNSS) and National Security Agency (NSA) has developed a nationally recognized certification program based on NSTISSI standards. The CNSS/NSA Certification is a government class certification that is recognized as the National Training Standard for Information Security Professionals Students who have obtained these certifications would have demonstrated a solid grasp of the principles as outlined in the 4011 standard. With this, EC-Council has joined the ranks of the organizations United States Air Force Academy, United States Military Academy, Air Force Institute of Technology and Carnegie Mellon University; all of whom have attained the National Training Standard for Information Security Professionals - the CNSS 4011. Introduction The EC-Council's Network Security Administrator certification looks at the network security in defensive view while the CEH certification program looks at the security in offensive mode. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop security policies that will protect an organization’s information. -

คู่มือ การป้องกันและกําจัด Spyware ด้วยโปรแกรม Superanti
คูมือ่ การป้องกนและกั าจัดํ Spyware ด้วยโปรแกรม SUPERAntiSpyware Free Edition โดย นายสุชล แกวประทุม้ นักเอกสารสนเทศ ระดับ งานระบบเครือขายคอมพิวเตอร์่ ฝ่ายเทคโนโลยีสารสนเทศห้องสมุด สํานักหอสมุดกลาง มหาวิทยาลัยรามคําแหง มีนาคม สารบัญ หน้า สปายแวร์ (Spyware) คืออะไร .......................................................................................................... 3 สปายแวร์ (Spyware) มาได้อยางไร่ ..................................................................................................... 3 อาการของเครืองคอมพิวเตอร์ทีติดสบายแวร์ (Spyware) ............................................................................ 4 วิธีการป้องกนสบายแวร์ั (Spyware) เบืองต้น ......................................................................................... 4 การป้องกนั และกาจัดสปายแวร์ํ (Spyware) ด้วยโปรแกรม SUPERAntiSpyware ....................................... 5 รู้จักกบโปรแกรมั SUPERAntiSpyware ........................................................................................ 5 คุณสมบัติและความสามารถของโปรแกรม SUPERAntiSpyware ........................................................ 5 ข้อจํากดของโปรแกรมั SUPERAntiSpywaer Free Editon ............................................................. 5 การติดตังโปรแกรมโปรแกรม SUPERAntiSpyware Free Editon ..................................................... 6 การใช้งานโปรแกรม SUPERAntiSpyware Free Editon .............................................................. 10 การปรับปรุง (update) ฐานข้อมูลของโปรแกรม SUPERAntiSpyware .............................................. 13 -

Automated Malware Analysis Report for SUPERANTISPYWARE
ID: 459764 Sample Name: SUPERANTISPYWARE.EXE Cookbook: default.jbs Time: 14:53:19 Date: 05/08/2021 Version: 33.0.0 White Diamond Table of Contents Table of Contents 2 Windows Analysis Report SUPERANTISPYWARE.EXE 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Process Tree 4 Malware Configuration 4 Yara Overview 4 Memory Dumps 4 Sigma Overview 5 Jbx Signature Overview 5 Malware Analysis System Evasion: 5 Lowering of HIPS / PFW / Operating System Security Settings: 5 Stealing of Sensitive Information: 5 Remote Access Functionality: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 8 URLs 8 Domains and IPs 8 Contacted Domains 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 8 Private 8 General Information 8 Simulations 9 Behavior and APIs 9 Joe Sandbox View / Context 9 IPs 9 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 27 General 28 File Icon 28 Static PE Info 28 General 28 Authenticode Signature 28 Entrypoint Preview 29 Rich Headers 29 Data Directories 29 Sections 29 Resources 29 Imports 29 Version Infos 29 Possible Origin 29 Network Behavior 29 Code Manipulations 29 Statistics 29 Behavior 29 System Behavior 29 Analysis Process: SUPERANTISPYWARE.EXE PID: 5720 Parent PID: 5776 29 General 29 File Activities 30 File Created 30 File Deleted 30 File Written 30 File Read 30 Registry Activities 30 Key Created 30 Key Value -

Mikogo & Personal Firewalls
Mikogo & Personal Firewalls - ZoneAlarm Create an Exception Rule If you use ZoneAlarm personal firewall on your PC and you are having trouble using the Mikogo software you might have to first create an Exception Rule for Mikogo. In case you receive the following message and you use ZoneAlarm, please proceed as described below. Click on the ZoneAlarm icon in your system tray next to your computer clock. The ZoneAlarm main window will appear. In the vertical navigation on the left-hand side, click on Program Control. Mikogo & Personal Firewalls – ZoneAlarm Page 2 The ZoneAlarm Program Control will open. Click on the Programs tab. Click on Add. Browse to the mikogo-starter executable file, highlight it and click Open. Mikogo & Personal Firewalls – ZoneAlarm Page 3 Mikogo will then appear in the Programs list. Click in the Access column and choose Allow. Mikogo & Personal Firewalls – ZoneAlarm Page 4 Run a Connection Test Go to the Mikogo homepage and click on Join Session. When prompted enter 000-000-000 as the session ID and your name. Then click Join Session. Alternatively you can open the software on your computer. To do so, click on Start menu > Mikogo > Mikogo > to open and run the software. The panel will appear on your screen. Click on the button and enter the 000-000-000 session ID and your name. Then click Join Session. The following message will appear confirming that you can establish a connection with Mikogo: Mikogo & Personal Firewalls – ZoneAlarm Page 5 . -

Webroot Secureanywhere User Guide Complete Edition
User Guide for the Complete Edition Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot SecureAnywhere User Guide for the Complete Edition Version 8.0.1; May, 2012 © 2011- 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is a trademark of Webroot Software, Inc. All other product and company names mentioned may be trademarks or registered trademarks of their respective owners. Contents 1: Getting Started . .1 Installing the software. .2 Using the main interface. .5 Using the system tray menu. .6 Viewing the protection status . .7 Creating a Webroot account. .8 Adding PCs to your account . .9 Adding mobile devices to your account . .10 Viewing the PC security status online . .11 2: Scans . .15 About scans . .16 Running an immediate scan. .17 Running a custom scan . .19 Changing the scan schedule . .21 Changing scan settings . .23 3: Shields . .25 About shields . .26 Changing Realtime shield settings . .27 Changing Behavior shield settings . .29 Changing Core System shield settings . .31 Changing Web Threat shield settings . .33 4: Firewall. .35 About the firewall . .36 Changing firewall alert settings . .37 Managing network applications . .38 5: Quarantine . .41 About quarantine . .42 Managing quarantined items . .43 Managing file detection . .45 Using antimalware tools . .47 Saving a threat log . .49 6: Identity Protection. .51 About the Identity shield. .52 Changing Identity shield settings . .53 Managing protected applications . .55 Managing protected websites. .57 7: Password Management . .61 About Password Management . .62 Downloading the Passwords component . .63 Capturing login credentials in a website. -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -
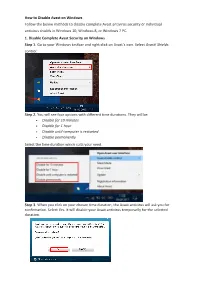
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Kaspersky Managed Service Providers Program
Kaspersky for Business MOBILE CONTROLS CLOUD ENDPOINT NETWORK SECURITY REPORTING VIRTUALIZATION SIEM SUPPORT SERVERS SERVICES CLOUD APPS Kaspersky Managed Service Providers Program Technical Reference Guide www.kaspersky.com #truecybersecurity Table of contents Program benefits 1 MSP program requirements 1 Products 2 Training and certification 5 Professional services 5 Technical designs 6 Kaspersky Endpoint Security Cloud 6 Kaspersky Endpoint Security for Business Select 6 Kaspersky Endpoint Security for Business Advanced 6 Kaspersky Hybrid Cloud Security 7 Kaspersky Security for Microsoft Office 365 8 Kaspersky Security for Mail Server 8 Kaspersky Security for Internet Gateways 9 Customer onboarding checklist 10 Appendix A 11 Appendix B 12 Appendix C 13 Appendix D 17 Program benefits • Flexible licensing allow you to choose between a monthly subscription and an annual license. Because you own the product license, there’s no need to spend time administrating contract renewals with customers — extending licenses is easy; no special action is required. • Increase sales revenues with volume-based discounts — the more customers you have, the less you pay. Pricing depends on the total number of devices of all customers. Sell more and gain bigger discounts. • Be even more efficient and grow your client base without having to hire additional engineers. With built-in best practices that drive operational efficiency, you’ll improve your tech-to-device ratio and boost your bottom line. Increase your scalability and protect more endpoints with fewer headaches. • Improved usability. Kaspersky Lab understands the importance of ease of use when it comes to security, and our design and usability specialists are closely involved in product development. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet