The Secure Encryption and Transfer Tool Release 3.3.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How to Use Encryption and Privacy Tools to Evade Corporate Espionage
How to use Encryption and Privacy Tools to Evade Corporate Espionage An ICIT White Paper Institute for Critical Infrastructure Technology August 2015 NOTICE: The recommendations contained in this white paper are not intended as standards for federal agencies or the legislative community, nor as replacements for enterprise-wide security strategies, frameworks and technologies. This white paper is written primarily for individuals (i.e. lawyers, CEOs, investment bankers, etc.) who are high risk targets of corporate espionage attacks. The information contained within this briefing is to be used for legal purposes only. ICIT does not condone the application of these strategies for illegal activity. Before using any of these strategies the reader is advised to consult an encryption professional. ICIT shall not be liable for the outcomes of any of the applications used by the reader that are mentioned in this brief. This document is for information purposes only. It is imperative that the reader hires skilled professionals for their cybersecurity needs. The Institute is available to provide encryption and privacy training to protect your organization’s sensitive data. To learn more about this offering, contact information can be found on page 41 of this brief. Not long ago it was speculated that the leading world economic and political powers were engaged in a cyber arms race; that the world is witnessing a cyber resource buildup of Cold War proportions. The implied threat in that assessment is close, but it misses the mark by at least half. The threat is much greater than you can imagine. We have passed the escalation phase and have engaged directly into full confrontation in the cyberwar. -
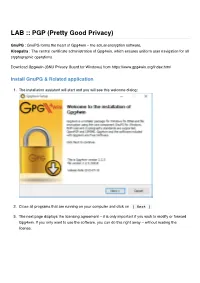
LAB :: PGP (Pretty Good Privacy)
LAB :: PGP (Pretty Good Privacy) GnuPG : GnuPG forms the heart of Gpg4win – the actual encryption software. Kleopatra : The central certificate administration of Gpg4win, which ensures uniform user navigation for all cryptographic operations. Download Gpg4win (GNU Privacy Guard for Windows) from https://www.gpg4win.org/index.html Install GnuPG & Related application 1. The installation assistant will start and you will see this welcome dialog: 2. Close all programs that are running on your computer and click on [ Next ] 3. The next page displays the licensing agreement – it is only important if you wish to modify or forward Gpg4win. If you only want to use the software, you can do this right away – without reading the license. Click on [ Next ] 4. On the page that contains the selection of components you can decide which programs you want to install. A default selection has already been made for you. You can also install individual components at a later time. Moving your mouse cursor over a component will display a brief description. Another useful feature is the display of required hard drive space for all selected components. Bellow are the application and there fucntion: a. GnuPG: Gnu Privacy Guard b. Kleopatra: Keymanager for OpenPGP c. GPA: GNU Privacy Assistant d. GpgOL: GnuPG for Outlook e. GpgEX: GnuPG Shell Extension f. Claws-Mail: Claws Mail user client g. Gpg4win Compedium: The Gpg4Win documentation Click on [ Next ] 5. The system will suggest a folder for the installation, e.g.: C:\Programme Files (x86)\GNU\GnuPG You can accept the suggestion or select a different folder for installing Gpg4win. -

Obstacles to the Adoption of Secure Communication Tools
Obstacles to the Adoption of Secure Communication Tools Ruba Abu-Salma M. Angela Sasse Joseph Bonneau University College London, UK University College London, UK Stanford University & EFF, USA Anastasia Danilova Alena Naiakshina Matthew Smith University of Bonn, Germany University of Bonn, Germany University of Bonn, Germany Abstract—The computer security community has advocated Recent mobile phone-based secure communication tools widespread adoption of secure communication tools to counter have often been designed to hide security from the user com- mass surveillance. Several popular personal communication tools pletely (albeit at some security cost [1]). WhatsApp famously (e.g., WhatsApp, iMessage) have adopted end-to-end encryption, and many new tools (e.g., Signal, Telegram) have been launched deployed E2E encryption to approximately a billion users with security as a key selling point. However it remains unclear through a code update to its application for messages, voice if users understand what protection these tools offer, and if they calls and video communications [18], with only negligible value that protection. In this study, we interviewed 60 partici- changes to the user experience. Some other communication pants about their experience with different communication tools tools (e.g., Signal, Threema) have launched with security and their perceptions of the tools’ security properties. We found that the adoption of secure communication tools is hindered by as an explicit selling point, but they also hide nearly all fragmented user bases and incompatible tools. Furthermore, the cryptographic details. vast majority of participants did not understand the essential There are key differences in the security model of dif- concept of end-to-end encryption, limiting their motivation to ferent E2E-encrypted tools, in addition to a large gap in adopt secure tools. -

The Crypto Cat Is out of the Bag: an Illustrative Inventory of Widely-Available Encryption Applications
December 8, 2015 The Crypto Cat is Out of the Bag: An Illustrative Inventory of Widely-Available Encryption Applications When it comes to encryption, the genie is out of the bottle. But encryption isn’t magic. It’s math, and very well-known math at that. The basic principles behind modern end-to-end encryption of digital messages, where only the recipient of the message can decode it, are nearly four decades old.1 U.S. companies like Apple and Facebook, providers of the encrypted messaging services iMessage and WhatsApp, don’t have a monopoly on strong end-to-end encryption tools. Strong encryption tools are everywhere, and over a billion ordinary people around the world rely on them every day. There are countless applications that are freely available online, across the globe, with unbreakable end-to-end encryption. The vast majority of those applications are either “open source” software that anyone is free to use, review, copy or build on,2 and/or are offered by companies, organizations or developers outside of the United States. In fact, it’s so easy to create new end-to-end encryption apps, jihadists have been coding their very own secure messaging tools since at least 2007, tools with names like Mujahadeen Secrets and Security of the Mujahid.3 Another app that terrorists are claimed to have used, Telegram, is based in Berlin.4 1 The foundational work in this area began with Whitfield Diffie and Martin Hellman’s New Directions in Cryptography, IEEE Transactions in Information Theory (Nov. 6, 1976), available at http://www- ee.stanford.edu/~hellman/publications/24.pdf. -

SFTP Bulk Upload Guide Electronic Taxpayer Service Center
SFTP Bulk Upload Guide Electronic Taxpayer Service Center Revised January 2021 Indiana Department of Revenue Table of Contents Overview of Bulk Upload 2 ACH Debit Payments — Debit Block Option 3 Taxpayer Registration 4 Registration 4 Certification to File 4 Encryption for SFTP Submission 5 PGP or GPG Software 5 Secure File Transfer 5 Acknowledgements 6 File Naming Conventions 8 Quick Reference 9 Registration Steps 9 Steps to File 9 GPG Kleopatra Install and Key Generation 10 Kleopatra Usage 15 APPENDIX A – PGP setup and use 19 APPENDIX B - SFTP Client Installation and Setup Instructions (WinSCP) 20 APPENDIX C – Using WinSCP to Send a File 21 APPENDIX D – Common Troubleshooting 24 APPENDIX E – Common Acronyms 25 APPENDIX F – Supported Form Types 26 APPENDIX G – SFTP Bulk Upload Business Rules 27 1 Overview of Bulk Upload The bulk upload facility provides taxpayers submitting files with large numbers of transactions the ability to electronically submit these records to the Indiana Department of Revenue (DOR). Bulk upload files are created by the customer and then submitted to DOR for processing. The files are processed sequentially within a couple of hours. During high-volume processing, there can be an increased turnaround time. When the process is complete, an acknowledgment email is sent to the authorized representative with the results of the submission. The Indiana Department of Revenue is transitioning to a new modernized tax system, INTIME. Due to this transition we now have a new expanded file size limit of 10MB for many of the files submitted. DOR recommends INTIME as the preferred method for file submission. -

Gnupg, Openssl Und Co Verschlüsselung Und Elektronische Unterschrift
GnuPG, OpenSSL und Co Verschlüsselung und elektronische Unterschrift Joerg.Schulenburg-at-ovgu.de 2004-2014 TLS SSL TLS PGP hash MD5 SHA1 ngerprint RA CA PKI WoT RND private Key sym- metrisch revoke ... ??? Inhalt 3 Abschnitte I Motivation/Einführung (kurz) I Theorie (ausführlich) I Verschlüsselung, Signierung, PKI, WoT, Sperrung, Schwachstellen I Praxis (optional) I Protokolle: PGP, TLS, S/MIME, SSH, ... I Hardware: RdRand, eGK, nPA I Software: GnuPG, GnuTLS, OpenSSL, stunnel, OpenSSH, ... Basiscs Was ist Verschlüsselung? (kurz) I Umwandlung von Klartext in Geheimtext I mit dem Ziel, Klartext vor Unbefugten zu verbergen Basiscs Was ist eine elektronische Signatur? (kurz) I (elektron.) Ersatz für handgeschriebene Unterschrift (jurist.) I lt. Wikipedia verschieden von digitaler Signatur (meinte ich wohl) I digitales Anhängsel zur Prüfung von Urheberschaft und Zugehörigkeit Wozu brauchen wir Crypto? ... unübersehbare Zahl von Missbrauchsrisiken Wozu brauchen wir Crypto? theoretisch I sichern gegen mitlauschen durch Dritte I sichern gegen Verfälschung I Verlässliche (Absender-)Identizierung Wozu brauchen wir Crypto? praktisch I WLANs: neugierige Nachbarn, Vermeidung Störerhaftung I automat. Anmeldung ohne Passwort (ssh, ClientZert. GRID) I bequeme (Geld-)Geschäfte via Internet (SSL, HBCI) I (autom.) Download von signierten Programmpaketen I vertrauliche EMAILs, ext. Backups (mit Kundendaten) I signierte Rechnungen/Verträge per EMAIL I Schutz bei Verlust der Hardware und mögl. Missbrauch I Passwortersatz Userzertikate (Browser,VPN) I $(Ergänzungen?) -
![Dark Corners of the Internet a Survey of Tor Research [Archive.Org]](https://docslib.b-cdn.net/cover/0978/dark-corners-of-the-internet-a-survey-of-tor-research-archive-org-4330978.webp)
Dark Corners of the Internet a Survey of Tor Research [Archive.Org]
The Hitchhiker’s Guide to Online Anonymity (Or “How I learned to start worrying and love privacy anonymity”) Version 1.0.4, September 2021 by AnonymousPlanet. This guide is still a work in progress. While I am working constantly to correct issues, improve the content, general structure, and readability, it will probably never be “finished”. Some parts might lack information or contain inaccuracies. Your experience may vary. Remember to check regularly for an updated version of this guide. This guide is a non-profit open-source initiative, licensed under Creative Commons Attribution-NonCommercial 4.0 International (cc-by-nc-4.0 [Archive.org]). See the license at the end of the document. • For mirrors see Appendix A6: Mirrors • For help in comparing versions see Appendix A7: Comparing versions Feel free to submit issues using GitHub Issues at: https://github.com/AnonymousPlanet/thgtoa/issues Feel free to come to discuss ideas at: • GitHub Discussions: https://github.com/AnonymousPlanet/thgtoa/discussions • Matrix/Element: ```#anonymity:matrix.org``` https://matrix.to/#/#anonymity:matrix.org Follow me on: • Twitter at https://twitter.com/AnonyPla [Nitter] (cannot guarantee this account will stay up for long tho) • Mastodon at https://mastodon.social/@anonypla. To contact me, see the updated information on the website or send an e-mail to [email protected] Please consider donating if you enjoy the project and want to support the hosting fees (for the Tor hosting and the Tor Exit node). There are several ways you could read this guide: • You want to understand the current state of online privacy and anonymity not necessarily get too technical about it: Just read the Introduction, Requirements, Understanding some basics of how some information can lead back to you and how to mitigate those, and A final editorial note sections. -

BSI Magazine 2017/02 Security in Focus Information Security As the Prerequisite for Digitalisation
BSI Magazine 2017/02 Security in focus Information Security as the Prerequisite for Digitalisation CYBER SECURITY THE BSI IT SECURITY IN PRACTICE The BSI in Operation Cyber Security in Without Cooperation, on Site Digitalisation You Won’t Get Very Far Everything from a EDITORIAL Single Source The massive cyber attacks of the recent past have shown that the major digitalisation projects in Germany and the use of the Internet of Things by our citizens are only a gain for us all if an appropriate security level can be ensured. The IT Security Act, the KRITIS regulations, the regulations in the Telecommuni- cations and NIS Implementation Act create a solid framework for higher IT security. They require numerous players to ensure an adequate level of security and report incidents. The focus of the BSI goes even beyond this, however. As the national cyber security agency, it is our job to shape information security in digitalisation. That is why we also approach those who are not directly subject to the above-mentioned regulations. No company likes to admit that it has fallen victim to a cyber attack; no PC user gladly admits that ransomware irretrievably encrypted all of his data. They must trust the authority they turn to in such cases. A representative survey conducted by the BSI recently showed that 87 per cent of respondents consider security on the Internet an important aspect, but less than half say they are familiar with this topic. Two-thirds say that security tests, security guidelines and clear liability provisions contribute to more security in cyber space. -

ECE646 – Fall 2007 Lab 1: Pretty Good Privacy
ECE646 – Fall 2007 Lab 1: Pretty Good Privacy PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY: 1. PART I, must be performed before the lecture on Wednesday, September 26th. 2. A LAB REPORT must be handed in at the beginning of class on Wednesday, October 3rd. 3. You are required to address all the questions listed in this manual, in your final report. 4. All e-mails exchanged with other students as a part of this lab should be CC: to [email protected] In order to perform the following lab, you are required to have an understanding of LECTURES 1-4 and have read the following sections: Stallings, 4th ed., Chapter 15.1 and appendices 15 A, B, C, or Stallings, 3rd ed., Chapter 15.1 and appendices 15 A, B, C, or Stallings, 2nd ed., Chapter 12.1 and appendices 12 A, B, C and Additional slides posted together with this instruction. PART I 1. INSTALLATION In order to complete this lab you have to install Gnu Privacy Guard on your personal computer/notebook or you can use the GPG installation in some GMU ECE Labs. Unix or Linux Users might already have GPG installed on their systems. Otherwise, you can download and install it from: http://www.gnupg.org/ Windows users can download Gpg4win Light v1.1.1 from: http://www.gpg4win.org/. Select all components including Sylpheed-Claws. GPG should be ready to use after you reboot. You will find a GnuPG folder installed in your Start Menu. GnuPG FAQ will serve as a manual for GnuPG command line utilities. -

Well Known NYC Media Company
Well Known NYC Media Company InVision Assessment PREPARED FOR WELL KNOWN NYC MEDIA COMPANY n Version 2.0 n April 30, 2020 Confidentiality Notice This document contains confidential and proprietary information of CPP Associates and Well Known NYC Media Company, except as noted in this paragraph, may not be shared with any other party. Well Known NYC Media Company may copy or disclose the information contained herein (with the exception of any pricing) as needed for the purpose of providing this information to the end user customer identified in this Assessment Report, provided that any such disclosure of information is accompanied by a requirement to maintain the confidentiality of such information. Except as expressly authorized in the preceding sentence, Well Known NYC Media Company may not copy or disclose without the prior written permission of CPP Associates. Table of Contents Executive Summary ...................................................................................................... 4 1.1 Scope ................................................................................................................ 6 1.2 Network Infrastructure ..................................................................................... 7 1.3 Windows Infrastructure .................................................................................... 8 1.4 Overall Client Risk ........................................................................................... 11 1.5 Servers .......................................................................................................... -

Repositorio De Archivos Con Seguridad Basado En El Protocolo Ssh Y El Sistema De Seguridad Rsa
REPOSITORIO DE ARCHIVOS CON SEGURIDAD BASADO EN EL PROTOCOLO SSH Y EL SISTEMA DE SEGURIDAD RSA Mancer Andrés Barranco León 2080900 [email protected] REPOSITORIO DE ARCHIVOS CON SEGURIDAD BASADO EN EL PROTOCOLO SSH Y EL SISTEMA DE SEGURIDAD RSA Mancer Andrés Barranco León Director de Proyecto Jaime Vitola Oyaga Universidad Santo Tomás Facultad de Ingeniería Electrónica, División de Ingenierías Bogotá, D.C. 2015 Nota de aceptación: Firma del Director de Proyecto Firma del Jurado Firma del Jurado Contenido Pag. Resumen 1 Introducción 2 Capítulo I. Introducción e información preliminar 1. Descripción del problema 3 2. Antecedentes 3 3. Justificación 6 4. Objetivo General 6 4.1. Objetivos Específicos 7 5. Factibilidad 7 Capitulo II. Marco Teórico 8 6. Repositorio Digital 8 7. Criptografía 9 7.1. Criptografía simétrica 9 7.2. Criptografía asimétrica 9 8. Protocolo SSH 10 9. Sistema de Seguridad RSA 16 10. Servidores de Claves 19 11. Definición de PGP 19 11.1. Funcionamiento 19 11.2. Aplicaciones de PGP 20 11.3. PGP Desktop 20 11.4. GNUPG o GPG 20 11.5. GPGshell 20 11.6. Enigmail 21 11.7. GNUPGK 21 12. OpenPGP (Estándar RFC4880) 21 12.1. Funciones Generales 21 12.2. La confidencialidad mediante cifrado 22 12.3. Autenticación a través de la firma digital 22 12.4. Compresión 23 12.5. La conversión de Radix-64 23 13. Servidores de claves PGP 23 14. GNUPG 23 15. Triple DES 24 16. Firma Digital 26 17. Segmentación de redes 27 18. Protocolo IPv4 27 19. Protocolo IPv6 28 20. Firewall 28 21. -
The Enigmail Handbook 1.0.0
openpgp email security for mozilla applications The Handbook V 1.8 Adaptations by Ludwig Hügelschäfer Based on Version 1 by Daniele Raffo with Patrick Brunschwig and Robert J. Hansen. Enigmail Handbook Contents 1. Setup and usage.......................................................................... 5 1.1. What do you need?................................................................................... 5 1.2. How to install Thunderbird.........................................................................5 1.3. How do I install Enigmail?......................................................................... 6 2. Quick start guide......................................................................... 8 2.1. The Setup Wizard......................................................................................9 2.2. Start using Thunderbird with Enigmail.....................................................28 3. Key management....................................................................... 30 3.1. Operations on your key pair.................................................................... 31 3.2. Distributing your public key..................................................................... 35 3.3. Importing public keys...............................................................................36 3.4. Validity of public keys.............................................................................. 37 3.5. Importing an existing key pair..................................................................42 3.6. Generating