Gpg4win-Compendium-En.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation of Proactive Spam Fighting Te Niques
Implementation of Proactive Spam Fighting Teniques Masterarbeit von Martin Gräßlin Rupret-Karls-Universität Heidelberg Betreuer: Prof. Dr. Gerhard Reinelt Prof. Dr. Felix Freiling 03. März 2010 Ehrenwörtlie Erklärung I versiere, dass i diese Masterarbeit selbstständig verfasst, nur die angegebenen ellen und Hilfsmiel verwendet und die Grundsätze und Empfehlungen „Verantwortung in der Wissensa“ der Universität Heidelberg beatet habe. Ort, Datum Martin Gräßlin Abstract One of the biggest allenges in global communication is to overcome the problem of unwanted emails, commonly referred to as spam. In the last years many approaes to reduce the number of spam emails have been proposed. Most of them have in common that the end-user is still required to verify the filtering results. ese approaes are reactive: before mails can be classified as spam in a reliable way, a set of similar mails have to be received. Spam fighting has to become proactive. Unwanted mails have to be bloed before they are delivered to the end-user’s mailbox. In this thesis the implementation of two proactive spam fighting teniques is discussed. e first concept, called Mail-Shake, introduces an authentication step before a sender is allowed to send emails to a new contact. Computers are unable to authenticate themselves and so all spam messages are automatically bloed. e development of this concept is discussed in this thesis. e second concept, called Spam Templates, is motivated by the fact that spam messages are generated from a common template. If we gain access to the template we are able to identify spam messages by mating the message against the template. -

Downloads." the Open Information Security Foundation
Performance Testing Suricata The Effect of Configuration Variables On Offline Suricata Performance A Project Completed for CS 6266 Under Jonathon T. Giffin, Assistant Professor, Georgia Institute of Technology by Winston H Messer Project Advisor: Matt Jonkman, President, Open Information Security Foundation December 2011 Messer ii Abstract The Suricata IDS/IPS engine, a viable alternative to Snort, has a multitude of potential configurations. A simplified automated testing system was devised for the purpose of performance testing Suricata in an offline environment. Of the available configuration variables, seventeen were analyzed independently by testing in fifty-six configurations. Of these, three variables were found to have a statistically significant effect on performance: Detect Engine Profile, Multi Pattern Algorithm, and CPU affinity. Acknowledgements In writing the final report on this endeavor, I would like to start by thanking four people who made this project possible: Matt Jonkman, President, Open Information Security Foundation: For allowing me the opportunity to carry out this project under his supervision. Victor Julien, Lead Programmer, Open Information Security Foundation and Anne-Fleur Koolstra, Documentation Specialist, Open Information Security Foundation: For their willingness to share their wisdom and experience of Suricata via email for the past four months. John M. Weathersby, Jr., Executive Director, Open Source Software Institute: For allowing me the use of Institute equipment for the creation of a suitable testing -

GNU Wget 1.10 the Non-Interactive Download Utility Updated for Wget 1.10, Apr 2005
GNU Wget 1.10 The non-interactive download utility Updated for Wget 1.10, Apr 2005 by Hrvoje Nikˇsi´cand the developers Copyright c 1996–2005, Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with the Invariant Sections being “GNU General Public License” and “GNU Free Documentation License”, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”. Chapter 1: Overview 1 1 Overview GNU Wget is a free utility for non-interactive download of files from the Web. It supports http, https, and ftp protocols, as well as retrieval through http proxies. This chapter is a partial overview of Wget’s features. • Wget is non-interactive, meaning that it can work in the background, while the user is not logged on. This allows you to start a retrieval and disconnect from the system, letting Wget finish the work. By contrast, most of the Web browsers require constant user’s presence, which can be a great hindrance when transferring a lot of data. • Wget can follow links in html and xhtml pages and create local versions of remote web sites, fully recreating the directory structure of the original site. This is sometimes referred to as “recursive downloading.” While doing that, Wget respects the Robot Exclusion Standard (‘/robots.txt’). Wget can be instructed to convert the links in downloaded html files to the local files for offline viewing. -
Metadata Track Akonadi the Independent Solution for PIM Data
Akonadi – The independent solution for PIM GCDS 2009 data Metadata track Akonadi the independent solution for PIM data Will Stephenson Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Akonadi Topics Akona-what? Design Overview What we give you What you give us Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Akonadi The story so far Monolithic apps Own data storage Limited if any external interfaces E-D-S Data storage service Limited range of types supported Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Limitations of KDE3 KResource framework limitations: Data is not shared Designed for synchronous access Hard to extend to other data types Basically no shared common code KMail limitations: Only limited backend abstraction Designed for small amounts of local data Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Scalability with KDE 3 |Data| = small Contact applet KAddressBook l l KMail Kopete Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Scalability in KDE 3 |Data| = large Contact applet KAddressBook l l KMail Kopete Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Goals As much as possible shared, type independent functionality Easy to extend to new data types Unified API to access PIM data, independent of the actual data source Scalability Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Goals One synchronization point for mobile devices Reliable, -

How to Use Encryption and Privacy Tools to Evade Corporate Espionage
How to use Encryption and Privacy Tools to Evade Corporate Espionage An ICIT White Paper Institute for Critical Infrastructure Technology August 2015 NOTICE: The recommendations contained in this white paper are not intended as standards for federal agencies or the legislative community, nor as replacements for enterprise-wide security strategies, frameworks and technologies. This white paper is written primarily for individuals (i.e. lawyers, CEOs, investment bankers, etc.) who are high risk targets of corporate espionage attacks. The information contained within this briefing is to be used for legal purposes only. ICIT does not condone the application of these strategies for illegal activity. Before using any of these strategies the reader is advised to consult an encryption professional. ICIT shall not be liable for the outcomes of any of the applications used by the reader that are mentioned in this brief. This document is for information purposes only. It is imperative that the reader hires skilled professionals for their cybersecurity needs. The Institute is available to provide encryption and privacy training to protect your organization’s sensitive data. To learn more about this offering, contact information can be found on page 41 of this brief. Not long ago it was speculated that the leading world economic and political powers were engaged in a cyber arms race; that the world is witnessing a cyber resource buildup of Cold War proportions. The implied threat in that assessment is close, but it misses the mark by at least half. The threat is much greater than you can imagine. We have passed the escalation phase and have engaged directly into full confrontation in the cyberwar. -

Name Synopsis Description Options
GPGTAR(1) GNU Privacy Guard 2.2 GPGTAR(1) NAME gpgtar −Encrypt or sign files into an archive SYNOPSIS gpgtar [options] filename1 [ filename2, ... ] directory1 [ directory2, ... ] DESCRIPTION gpgtar encrypts or signs files into an archive.Itisangpg-ized tar using the same format as used by PGP’s PGP Zip. OPTIONS gpgtar understands these options: --create Put givenfiles and directories into a vanilla ‘‘ustar’’archive. --extract Extract all files from a vanilla ‘‘ustar’’archive. --encrypt -e Encrypt givenfiles and directories into an archive.This option may be combined with option --symmetric for an archive that may be decrypted via a secret key orapassphrase. --decrypt -d Extract all files from an encrypted archive. --sign -s Makeasigned archive from the givenfiles and directories. This can be combined with option --encrypt to create a signed and then encrypted archive. --list-archive -t List the contents of the specified archive. --symmetric -c Encrypt with a symmetric cipher using a passphrase. The default symmetric cipher used is AES-128, but may be chosen with the --cipher-algo option to gpg. --recipient user -r user Encrypt for user id user.For details see gpg. --local-user user -u user Use user as the key tosign with. Fordetails see gpg. --output file -o file Write the archive tothe specified file file. --verbose -v Enable extra informational output. GnuPG 2.2.12 2018-12-11 1 GPGTAR(1) GNU Privacy Guard 2.2 GPGTAR(1) --quiet -q Trytobeasquiet as possible. --skip-crypto Skip all crypto operations and create or extract vanilla ‘‘ustar’’archives. --dry-run Do not actually output the extracted files. -

With Yocto/Openembedded
PORTING NEW CODE TO RISC-V WITH YOCTO/OPENEMBEDDED Martin Maas ([email protected]) 1st RISC-V Workshop, January 15, 2015 Monterey, CA WHY WE NEED A LINUX DISTRIBUTION • To build an application for RISC-V, you need to: – Download and build the RISC-V toolchain + Linux – Download, patch and build application + dependencies – Create an image and run it in QEMU or on hardware • Problems with this approach: – Error-prone: Easy to corrupt FS or get a step wrong – Reproducibility: Others can’t easily reuse your work – Rigidity: If a dependency changes, need to do it all over • We need a Linux distribution! – Automatic build process with dependency tracking – Ability to distribute binary packages and SDKs 2 RISCV-POKY: A PORT OF THE YOCTO PROJECT • We ported the Yocto Project – Official Linux Foundation Workgroup, supported by a large number of industry partners – Part I: Collection of hundreds of recipes (scripts that describe how to build packages for different platforms), shared with OpenEmbedded project – Part II: Bitbake, a parallel build system that takes recipes and fetches, patches, cross-compiles and produces packages (RPM/DEB), images, SDKs, etc. • Focus on build process and customizability 3 GETTING STARTED WITH RISCV-POKY • Let’s build a full Linux system including the GCC toolchain, Linux, QEMU + a large set of packages (including bash, ssh, python, perl, apt, wget,…) • Step I: Clone riscv-poky: git clone [email protected]:ucb-bar/riscv-poky.git • Step II: Set up the build system: source oe-init-build-env • Step III: Build an image (may -

Replacing PGP 2.X with Gnupg
Replacing PGP 2.x with GnuPG This article is based on an earlier PGP 2.x/GnuPG compatability guide (http://www.toehold.com/~kyle/pgp- compat.html) written by Kyle Hasselbacher (<[email protected]>). Mike Ashley (<[email protected]>) edited and expanded it. Michael Fischer v. Mollard (<[email protected]>) transformed the HTML source to Doc- Book SGML and also expanded it further. Some of the details described here came from the gnupg-devel and gnupg-user mailing lists. The workaround for both signing with and encrypting to an RSA key were taken from Gero Treuner’s compatability script (http://muppet.faveve.uni-stuttgart.de/~gero/gpg-2comp/changes.html). Please direct questions, bug reports, or suggesstions to the maintainer, Mike Ashley. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". Introduction This document describes how to communicate with people still using old versions of PGP 2.x GnuPG can be used as a nearly complete replacement for PGP 2.x. You may encrypt and decrypt PGP 2.x messages using imported old keys, but you cannot generate PGP 2.x keys. This document demonstrates how to extend the standard distribution of GnuPG to support PGP 2.x keys as well as what options must be used to ensure inter- operation with PGP 2.x users. -

GNU Texinfo Font Subsystem I
GNU Texinfo font subsystem i Table of Contents 1 Font management::::::::::::::::::::::::::::::: 1 1.1 Introduction ::::::::::::::::::::::::::::::::::::::::::::::::::: 1 1.1.1 Font features and attributes ::::::::::::::::::::::::::::::: 1 1.1.2 Current font attribute set ::::::::::::::::::::::::::::::::: 1 1.1.3 Font substitution :::::::::::::::::::::::::::::::::::::::::: 2 1.1.4 Other ::::::::::::::::::::::::::::::::::::::::::::::::::::: 2 1.2 Font definition macros:::::::::::::::::::::::::::::::::::::::::: 3 1.3 Font selection macros :::::::::::::::::::::::::::::::::::::::::: 4 1.3.1 Relative font scaling ::::::::::::::::::::::::::::::::::::::: 4 1.4 Font substitution macros ::::::::::::::::::::::::::::::::::::::: 5 1.5 Font collections :::::::::::::::::::::::::::::::::::::::::::::::: 5 1.5.1 Font styles :::::::::::::::::::::::::::::::::::::::::::::::: 5 1.5.2 Font style selection :::::::::::::::::::::::::::::::::::::::: 5 1.5.3 Font styles for document elements ::::::::::::::::::::::::: 5 1.6 Input encodings :::::::::::::::::::::::::::::::::::::::::::::::: 8 1.7 Font encodings ::::::::::::::::::::::::::::::::::::::::::::::::: 8 Index :::::::::::::::::::::::::::::::::::::::::::::::: 9 Chapter 1: Font management 1 1 Font management Texinfo's font management macros allow customization of fonts used in the printed docu- ment. 1.1 Introduction In this chapter we introduce the basic concepts of font management in Texinfo. 1.1.1 Font features and attributes Each font can be characterized by a number of features. For example, a font can be char- -

Brave Gnu World
LINUXCOVERCOMMUNITY USERSTORY SchlagwortSchlagwortBrave GNU sollte Worldsollte hier hier stehen stehen Schlagwort sollte hier stehen COVER STORY The Monthly GNU Column BRAVE GNU WORLD This column looks into projects and current affairs in the world of free software from the perspective of the GNU Project and the FSF. In this issue, I’ll focus on Comspari and the EU decision on software patents. BY GEORG C.F. GREVE n the past, the German government the Kroupware project in 2002. The pub- principles back to front. For example, has often caused a (positive) stir due lic tender by the BSI was aimed to pro- many other solutions are based on the Ito its activities with free software. duce a groupware solution that would principle that the server is the king of The Federal Ministry of the Economy support strong cryptography and inte- the hill and the users have to bow down (BMWi) sponsored Gnupg [1], for exam- grate seamlessly into a heterogeneous and worship it. The Kolab server does ple. Add to this a number of accompany- environment. things differently. The program makes ing activities, such as a report by the The government office gave a consor- the user king, and gives the user power Bavarian Accounts Office, the KBST let- tium comprising Erfrakon, Klarälvdalens to do things. The software simply helps ter, and the highly acclaimed migration Datakonsult [2], and Intevation [3] the coordinate things as a central intermedi- guide by the Federal Ministry of the Inte- task of developing the software. Inter- ary. rior (BMI). nally, the design and the software was Kolab 1 combined so-called partial referred to as Kolab 1. -

Nextcloud User Manual Release Latest
Nextcloud User Manual Release latest The Nextcloud developers Oct 06, 2021 CONTENTS 1 Nextcloud latest user manual introduction1 2 What’s new for users in Nextcloud latest3 3 The Nextcloud Web interface7 3.1 Web browser requirements........................................7 3.2 Navigating the main user interface....................................8 4 Files & synchronization 11 4.1 Accessing your files using the Nextcloud Web interface......................... 11 4.2 Accessing Nextcloud files using WebDAV................................ 17 4.3 Managing deleted files.......................................... 28 4.4 Desktop and mobile synchronization.................................. 29 4.5 Encrypting your Nextcloud files on the server.............................. 30 4.6 File Sharing............................................... 33 4.7 Federated Shares............................................. 37 4.8 Making anonymous uploads....................................... 39 4.9 Large file uploads............................................ 41 4.10 Storage quota............................................... 42 4.11 Version control.............................................. 42 4.12 Projects.................................................. 43 4.13 Transfer Ownership........................................... 47 5 Groupware 49 5.1 Using the Contacts app.......................................... 49 5.2 Using the Calendar app......................................... 52 5.3 Synchronizing with Android....................................... 60 5.4 -
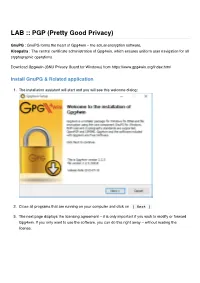
LAB :: PGP (Pretty Good Privacy)
LAB :: PGP (Pretty Good Privacy) GnuPG : GnuPG forms the heart of Gpg4win – the actual encryption software. Kleopatra : The central certificate administration of Gpg4win, which ensures uniform user navigation for all cryptographic operations. Download Gpg4win (GNU Privacy Guard for Windows) from https://www.gpg4win.org/index.html Install GnuPG & Related application 1. The installation assistant will start and you will see this welcome dialog: 2. Close all programs that are running on your computer and click on [ Next ] 3. The next page displays the licensing agreement – it is only important if you wish to modify or forward Gpg4win. If you only want to use the software, you can do this right away – without reading the license. Click on [ Next ] 4. On the page that contains the selection of components you can decide which programs you want to install. A default selection has already been made for you. You can also install individual components at a later time. Moving your mouse cursor over a component will display a brief description. Another useful feature is the display of required hard drive space for all selected components. Bellow are the application and there fucntion: a. GnuPG: Gnu Privacy Guard b. Kleopatra: Keymanager for OpenPGP c. GPA: GNU Privacy Assistant d. GpgOL: GnuPG for Outlook e. GpgEX: GnuPG Shell Extension f. Claws-Mail: Claws Mail user client g. Gpg4win Compedium: The Gpg4Win documentation Click on [ Next ] 5. The system will suggest a folder for the installation, e.g.: C:\Programme Files (x86)\GNU\GnuPG You can accept the suggestion or select a different folder for installing Gpg4win.