Deliverable D4.1 AI-Driven Communication & Computation Co-Design: Gap Analysis and Blueprint
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Integrated Low Phase Noise Radiation-Pressure-Driven Optomechanical Oscillator Chipset
OPEN An integrated low phase noise SUBJECT AREAS: radiation-pressure-driven OPTICS AND PHOTONICS NANOSCIENCE AND optomechanical oscillator chipset TECHNOLOGY Xingsheng Luan1, Yongjun Huang1,2, Ying Li1, James F. McMillan1, Jiangjun Zheng1, Shu-Wei Huang1, Pin-Chun Hsieh1, Tingyi Gu1, Di Wang1, Archita Hati3, David A. Howe3, Guangjun Wen2, Mingbin Yu4, Received Guoqiang Lo4, Dim-Lee Kwong4 & Chee Wei Wong1 26 June 2014 Accepted 1Optical Nanostructures Laboratory, Columbia University, New York, NY 10027, USA, 2Key Laboratory of Broadband Optical 13 October 2014 Fiber Transmission & Communication Networks, School of Communication and Information Engineering, University of Electronic 3 Published Science and Technology of China, Chengdu, 611731, China, National Institute of Standards and Technology, Boulder, CO 4 30 October 2014 80303, USA, The Institute of Microelectronics, 11 Science Park Road, Singapore 117685, Singapore. High-quality frequency references are the cornerstones in position, navigation and timing applications of Correspondence and both scientific and commercial domains. Optomechanical oscillators, with direct coupling to requests for materials continuous-wave light and non-material-limited f 3 Q product, are long regarded as a potential platform for should be addressed to frequency reference in radio-frequency-photonic architectures. However, one major challenge is the compatibility with standard CMOS fabrication processes while maintaining optomechanical high quality X.L. (xl2354@ performance. Here we demonstrate the monolithic integration of photonic crystal optomechanical columbia.edu); Y.H. oscillators and on-chip high speed Ge detectors based on the silicon CMOS platform. With the generation of (yh2663@columbia. both high harmonics (up to 59th order) and subharmonics (down to 1/4), our chipset provides multiple edu) or C.W.W. -

Analysis and Design of Wideband LC Vcos
Analysis and Design of Wideband LC VCOs Axel Dominique Berny Robert G. Meyer Ali Niknejad Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2006-50 http://www.eecs.berkeley.edu/Pubs/TechRpts/2006/EECS-2006-50.html May 12, 2006 Copyright © 2006, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Analysis and Design of Wideband LC VCOs by Axel Dominique Berny B.S. (University of Michigan, Ann Arbor) 2000 M.S. (University of California, Berkeley) 2002 A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Electrical Engineering and Computer Sciences in the GRADUATE DIVISION of the UNIVERSITY OF CALIFORNIA, BERKELEY Committee in charge: Professor Robert G. Meyer, Co-chair Professor Ali M. Niknejad, Co-chair Professor Philip B. Stark Spring 2006 Analysis and Design of Wideband LC VCOs Copyright 2006 by Axel Dominique Berny 1 Abstract Analysis and Design of Wideband LC VCOs by Axel Dominique Berny Doctor of Philosophy in Electrical Engineering and Computer Sciences University of California, Berkeley Professor Robert G. Meyer, Co-chair Professor Ali M. Niknejad, Co-chair The growing demand for higher data transfer rates and lower power consumption has had a major impact on the design of RF communication systems. -
Modeling the Impact of Phase Noise on the Performance of Crystal-Free Radios Osama Khan, Brad Wheeler, Filip Maksimovic, David Burnett, Ali M
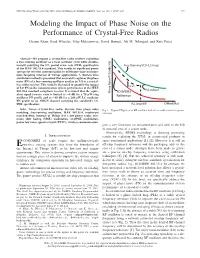
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS—II: EXPRESS BRIEFS, VOL. 64, NO. 7, JULY 2017 777 Modeling the Impact of Phase Noise on the Performance of Crystal-Free Radios Osama Khan, Brad Wheeler, Filip Maksimovic, David Burnett, Ali M. Niknejad, and Kris Pister Abstract—We propose a crystal-free radio receiver exploiting a free-running oscillator as a local oscillator (LO) while simulta- neously satisfying the 1% packet error rate (PER) specification of the IEEE 802.15.4 standard. This results in significant power savings for wireless communication in millimeter-scale microsys- tems targeting Internet of Things applications. A discrete time simulation method is presented that accurately captures the phase noise (PN) of a free-running oscillator used as an LO in a crystal- free radio receiver. This model is then used to quantify the impact of LO PN on the communication system performance of the IEEE 802.15.4 standard compliant receiver. It is found that the equiv- alent signal-to-noise ratio is limited to ∼8 dB for a 75-µW ring oscillator PN profile and to ∼10 dB for a 240-µW LC oscillator PN profile in an AWGN channel satisfying the standard’s 1% PER specification. Index Terms—Crystal-free radio, discrete time phase noise Fig. 1. Typical PN plot of an RF oscillator locked to a stable crystal frequency modeling, free-running oscillators, IEEE 802.15.4, incoherent reference. matched filter, Internet of Things (IoT), low-power radio, min- imum shift keying (MSK) modulation, O-QPSK modulation, power law noise, quartz crystal (XTAL), wireless communication. -

Understanding Phase Error and Jitter: Definitions, Implications
This article has been accepted for inclusion in a future issue of this journal. Content is final as presented, with the exception of pagination. IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS–I: REGULAR PAPERS 1 Understanding Phase Error and Jitter: Definitions, Implications, Simulations, and Measurement Ian Galton , Fellow, IEEE, and Colin Weltin-Wu, Member, IEEE (Invited Paper) Abstract— Precision oscillators are ubiquitous in modern elec- multiplication by a sinusoidal oscillator signal whereas most tronic systems, and their accuracy often limits the performance practical mixer circuits perform multiplication by squared-up of such systems. Hence, a deep understanding of how oscillator oscillator signals. Fundamental questions typically are left performance is quantified, simulated, and measured, and how unanswered such as: How does the squaring-up process change it affects the system performance is essential for designers. the oscillator error? How does multiplying by a squared-up Unfortunately, the necessary information is spread thinly across oscillator signal instead of a sinusoidal signal change a mixer’s the published literature and textbooks with widely varying notations and some critical disconnects. This paper addresses this behavior and response to oscillator error? problem by presenting a comprehensive one-stop explanation of Another obstacle to learning the material is that there are how oscillator error is quantified, simulated, and measured in three distinct oscillator error metrics in common use: phase practice, and the effects of oscillator error in typical oscillator error, jitter, and frequency stability. Each metric offers advan- applications. tages in certain applications, so it is important to understand Index Terms— Oscillator phase error, phase noise, jitter, how they relate to each other, yet with the exception of [1], frequency stability, Allan variance, frequency synthesizer, crystal, the authors are not aware of prior publications that provide phase-locked loop (PLL). -

Advanced Bridge (Interferometric) Phase and Amplitude Noise Measurements
Advanced bridge (interferometric) phase and amplitude noise measurements Enrico Rubiola∗ Vincent Giordano† Cite this article as: E. Rubiola, V. Giordano, “Advanced interferometric phase and amplitude noise measurements”, Review of Scientific Instruments vol. 73 no. 6 pp. 2445–2457, June 2002 Abstract The measurement of the close-to-the-carrier noise of two-port radiofre- quency and microwave devices is a relevant issue in time and frequency metrology and in some fields of electronics, physics and optics. While phase noise is the main concern, amplitude noise is often of interest. Presently the highest sensitivity is achieved with the interferometric method, that consists of the amplification and synchronous detection of the noise sidebands after suppressing the carrier by vector subtraction of an equal signal. A substantial progress in understanding the flicker noise mecha- nism of the interferometer results in new schemes that improve by 20–30 dB the sensitivity at low Fourier frequencies. These schemes, based on two or three nested interferometers and vector detection of noise, also feature closed-loop carrier suppression control, simplified calibration, and intrinsically high immunity to mechanical vibrations. The paper provides the complete theory and detailed design criteria, and reports on the implementation of a prototype working at the carrier frequency of 100 MHz. In real-time measurements, a background noise of −175 to −180 dB dBrad2/Hz has been obtained at f = 1 Hz off the carrier; the white noise floor is limited by the thermal energy kB T0 referred to the carrier power P0 and by the noise figure of an amplifier. Exploiting correlation and averaging in similar conditions, the sensitivity exceeds −185 dBrad2/Hz at f = 1 Hz; the white noise floor is limited by thermal uniformity rather than by the absolute temperature. -

Analysis of Oscillator Phase-Noise Effects on Self-Interference Cancellation in Full-Duplex OFDM Radio Transceivers
Revised manuscript for IEEE Transactions on Wireless Communications 1 Analysis of Oscillator Phase-Noise Effects on Self-Interference Cancellation in Full-Duplex OFDM Radio Transceivers Ville Syrjälä, Member, IEEE, Mikko Valkama, Member, IEEE, Lauri Anttila, Member, IEEE, Taneli Riihonen, Student Member, IEEE and Dani Korpi Abstract—This paper addresses the analysis of oscillator phase- recently [1], [2], [3], [4], [5]. Such full-duplex radio noise effects on the self-interference cancellation capability of full- technology has many benefits over the conventional time- duplex direct-conversion radio transceivers. Closed-form solutions division duplexing (TDD) and frequency-division duplexing are derived for the power of the residual self-interference stemming from phase noise in two alternative cases of having either (FDD) based communications. When transmission and independent oscillators or the same oscillator at the transmitter reception happen at the same time and at the same frequency, and receiver chains of the full-duplex transceiver. The results show spectral efficiency is obviously increasing, and can in theory that phase noise has a severe effect on self-interference cancellation even be doubled compared to TDD and FDD, given that the in both of the considered cases, and that by using the common oscillator in upconversion and downconversion results in clearly SI problem can be solved [1]. Furthermore, from wireless lower residual self-interference levels. The results also show that it network perspective, the frequency planning gets simpler, is in general vital to use high quality oscillators in full-duplex since only a single frequency is needed and is shared between transceivers, or have some means for phase noise estimation and uplink and downlink. -

Scheme of Instruction 2021 - 2022
Scheme of Instruction Academic Year 2021-22 Part-A (August Semester) 1 Index Department Course Prefix Page No Preface : SCC Chair 4 Division of Biological Sciences Preface 6 Biological Science DB 8 Biochemistry BC 9 Ecological Sciences EC 11 Neuroscience NS 13 Microbiology and Cell Biology MC 15 Molecular Biophysics Unit MB 18 Molecular Reproduction Development and Genetics RD 20 Division of Chemical Sciences Preface 21 Chemical Science CD 23 Inorganic and Physical Chemistry IP 26 Materials Research Centre MR 28 Organic Chemistry OC 29 Solid State and Structural Chemistry SS 31 Division of Physical and Mathematical Sciences Preface 33 High Energy Physics HE 34 Instrumentation and Applied Physics IN 38 Mathematics MA 40 Physics PH 49 Division of Electrical, Electronics and Computer Sciences (EECS) Preface 59 Computer Science and Automation E0, E1 60 Electrical Communication Engineering CN,E1,E2,E3,E8,E9,MV 68 Electrical Engineering E0,E1,E4,E5,E6,E8,E9 78 Electronic Systems Engineering E0,E2,E3,E9 86 Division of Mechanical Sciences Preface 95 Aerospace Engineering AE 96 Atmospheric and Oceanic Sciences AS 101 Civil Engineering CE 104 Chemical Engineering CH 112 Mechanical Engineering ME 116 Materials Engineering MT 122 Product Design and Manufacturing MN, PD 127 Sustainable Technologies ST 133 Earth Sciences ES 136 Division of Interdisciplinary Research Preface 139 Biosystems Science and Engineering BE 140 Scheme of Instruction 2021 - 2022 2 Energy Research ER 144 Computational and Data Sciences DS 145 Nanoscience and Engineering NE 150 Management Studies MG 155 Cyber Physical Systems CP 160 Scheme of Instruction 2020 - 2021 3 Preface The Scheme of Instruction (SoI) and Student Information Handbook (Handbook) contain the courses and rules and regulations related to student life in the Indian Institute of Science. -

Clock Jitter Effects on the Performance of ADC Devices
Clock Jitter Effects on the Performance of ADC Devices Roberto J. Vega Luis Geraldo P. Meloni Universidade Estadual de Campinas - UNICAMP Universidade Estadual de Campinas - UNICAMP P.O. Box 05 - 13083-852 P.O. Box 05 - 13083-852 Campinas - SP - Brazil Campinas - SP - Brazil [email protected] [email protected] Karlo G. Lenzi Centro de Pesquisa e Desenvolvimento em Telecomunicac¸oes˜ - CPqD P.O. Box 05 - 13083-852 Campinas - SP - Brazil [email protected] Abstract— This paper aims to demonstrate the effect of jitter power near the full scale of the ADC, the noise power is on the performance of Analog-to-digital converters and how computed by all FFT bins except the DC bin value (it is it degrades the quality of the signal being sampled. If not common to exclude up to 8 bins after the DC zero-bin to carefully controlled, jitter effects on data acquisition may severely impacted the outcome of the sampling process. This analysis avoid any spectral leakage of the DC component). is of great importance for applications that demands a very This measure includes the effect of all types of noise, the good signal to noise ratio, such as high-performance wireless distortion and harmonics introduced by the converter. The rms standards, such as DTV, WiMAX and LTE. error is given by (1), as defined by IEEE standard [5], where Index Terms— ADC Performance, Jitter, Phase Noise, SNR. J is an exact integer multiple of fs=N: I. INTRODUCTION 1 s X = jX(k)j2 (1) With the advance of the technology and the migration of the rms N signal processing from analog to digital, the use of analog-to- k6=0;J;N−J digital converters (ADC) became essential. -

Low Noise Oscillator in ADPLL Toward Direct-To-RF All-Digital Polar Transmitter
Low Noise Oscillator in ADPLL toward Direct-to-RF All-digital Polar Transmitter JIAN CHEN Doctoral Thesis in Electronic and Computer Systems Stockholm, Sweden 2012 TRITA-ICT/ECS AVH 13:03 KTH School of Information and ISSN 1653-6363 Communication Technology ISRN KTH/ICT/ECS/AVH-13/03-SE SE-164 40 Kista, Stockholm ISBN 978-91-7501-643-6 Sweden Akademisk avhandling som med tillst˚and av Kungl Tekniska h¨ogskolan framl¨agges till offentlig granskning f¨or avl¨aggande av teknologie doktorsexamen i Elektronik och Datorsystem onsdag den 13 mars 2013 klockan 9.00 i Sal D, Forum 120, Kungl Tekniska h¨ogskolan, Kista 164 40, Stockholma. c Jian Chen, September 2012 Tryck: Universitetsservice US AB iii Abstract In recent years all-digital or digitally-intensive RF transmitters (TX) have attracted great attention in both literature and industry. The motivation is to implement RF circuits in a manner suiting advanced nanometer CMOS processes. To achieve that, information is encoded in the time-domain rather than voltage amplitude. This enables RF design to also benefit from CMOS process scaling. In this thesis an improved architecture of a digitally-intensive transmitter is proposed and validated experimentally. The techniques to lower oscillator phase noise and all-digital phase-locked loop (ADPLL) quantization noise are discussed and proved by both simulation and measurements. The impact of device sizing on 1/f 2 noise is analyzed and validated by measurements. Seven oscillators in 180-nm CMOS with the same LC-tank, operation frequency and power consumption but different core device width are compared. -

Oscillator Phase Noise and Sampling Clock Jitter
OSCILLATOR PHASE NOISE AND SAMPLING CLOCK JITTER RETHNAKARAN PULIKKOONATTU ABSTRACT. This technical note presents and overview of oscillator phase noise and its characteristics, which are paramount to the understanding of digital receiver and modems. Oscillators used in practical systems deviate from ideal spectral characteristics. Due to this, there arise unpleasant performance issues. A/D and D/A converters used in digital receivers use sampling clocks (for sampling or sample and hold) which are derived from sinusoidal oscillators. Phase noise present in the source oscillator could translate to jitter in clock waveform. There is an established relationship between the mean square jitter and phase noise spectrum. The mathematical formula to compute the rms phase jitter from a given oscillator phase noise spectrum is derived and furnished with examples. The result obtained thus matches with those obtained using a web based tool [1] Date: 2007 June 12. Key words and phrases. Phase noise, Oscillator phase noise, clock jitter. ST Microelectronics, (Genesis Microchip) Bangalore, India (www.st.com). 1 2 RETHNAKARAN PULIKKOONATTU 1. PHASE NOISE Ideal sinusoidal oscillators of frequency f0 have a mathematically strict spectrum in the form of delta functions, centered at −f0 and f0. However, practical oscillators sel- dom exhibit this kind of clean spectrum. They tend to have spreading of spectral energy around the carrier frequency, as shown in Figure-1 . The spreading or spillage of energy to neighbouring points around f0 can cause unwanted behaviour at both transmitter and re- ceiver mixers. This spillage of spectral energy behave like unwanted phase modulation and is called phase noise. Besides mixers, the sampling clock used to trigger A/D and DAC are also influenced because the clocks used there are derived from non-ideal sinusoidal oscillators, with phase noise. -

Study Programme Accreditation Power, Electronic and Telecommunication UNDERGRADUATE ACADEMIC STUDIES Engineering
UNIVERSITY OF NOVI SAD FACULTY OF TECHNICAL SCIENCES 21000 NOVI SAD, TRG DOSITEJA OBRADOVIĆA 6 Study Programme Accreditation Power, Electronic and Telecommunication UNDERGRADUATE ACADEMIC STUDIES Engineering STUDY PROGRAMME ACCREDITATION MATERIAL: POWER, ELECTRONIC AND TELECOMMUNICATION ENGINEERING UNDERGRADUATE ACADEMIC STUDIES Novi Sad 2012. Prevod sa srpskog jezika: Jelisaveta Šafranj Ivana Mirović Marina Katić Vesna Bodganović Dragana Gak Ličen Branislava HIDDEN TEXT TO MARK THE BEGINNING OF THE TABEL OF CONTENTS FACULTY OF TECHNICAL SCIENCES 21000 NOVI SAD, TRG DOSITEJA OBRADOVIĆA 6 Content 00. Introduction ____________________________ 3 01. Programme Structure ____________________________ 4 02. Programme Objectives ____________________________ 5 03. Programme Goals ____________________________ 6 04. Graduates` Competencies ____________________________ 7 05. Curriculum ____________________________ 8 Table 5.2 Course specification . 8 Discrete Mathematics . 9 Fundamentals of Electrical Engineering 1 . 10 Mechanics . 11 Software Lab . 12 Sociology of Technique . 13 English Language - Elementary . 14 Mathematical Analysis 1 . 15 Fundamentals of Electrical Engineering 2 . 16 Physics . 17 Programming Languages and Data Structures . 18 English Language – Pre-Intermediate . 19 Mathematical Analysis 2 . 20 Introduction to Electronics . 21 System Control, Modeling and Simulation . 22 Signals and Systems . 23 Electrical Circuit Theory . 24 Probability, Statistics and Stochastic . 25 Processes English Language - Intermediate . 26 Power Engineering -

Design, Modeling and Noise Measurement of Oscillators Using a Large Signal Network Analyzer
DESIGN, MODELING AND NOISE MEASUREMENT OF OSCILLATORS USING A LARGE SIGNAL NETWORK ANALYZER DISSERTATION Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy in the Graduate School of The Ohio State University By Inwon Suh, M.S.E.E. Graduate Program in Electrical and Computer Engineering The Ohio State University 2011 Dissertation Committee: Prof. Patrick Roblin, Adviser Prof. Steven B. Bibyk Prof. Roberto Rojas-Teran Prof. James Peck °c Copyright by Inwon Suh 2011 ABSTRACT Oscillators play a crucial role in wireless communication systems since they are used together with mixers for frequency translation. To design discrete oscillators in a more efficient way in terms of output power, a multi-harmonic real-time open-loop active load- pull technique was developed and used to find the optimal fundamental and harmonic load impedances. Multi-harmonic loaded load circuits were then designed and implemented to approach the optimal multi-harmonic load impedances and realize a stand-alone oscillator. Then, a new behavioral modeling technique based on power dependent Volterra series was developed to model negative-resistance oscillators. The derived behavioral model pre- dicts the harmonic load-pull behaviors and the output power characteristics of oscillators and assists with the oscillator design. The noise characteristic of oscillator is also of great importance in communication cir- cuits. A new generalized 1/f Kurokawa noise analysis applicable to both low and high Q oscillators is proposed for 1/f phase and amplitude noise. A theoretical correspon- dence between the new generalized Kurokawa theory and the impulse sensitivity function and the perturbation projection vector analyses is also derived.