Quantum Pin Codes Christophe Vuillot, Nikolas P
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uniform Panoploid Tetracombs
Uniform Panoploid Tetracombs George Olshevsky TETRACOMB is a four-dimensional tessellation. In any tessellation, the honeycells, which are the n-dimensional polytopes that tessellate the space, Amust by definition adjoin precisely along their facets, that is, their ( n!1)- dimensional elements, so that each facet belongs to exactly two honeycells. In the case of tetracombs, the honeycells are four-dimensional polytopes, or polychora, and their facets are polyhedra. For a tessellation to be uniform, the honeycells must all be uniform polytopes, and the vertices must be transitive on the symmetry group of the tessellation. Loosely speaking, therefore, the vertices must be “surrounded all alike” by the honeycells that meet there. If a tessellation is such that every point of its space not on a boundary between honeycells lies in the interior of exactly one honeycell, then it is panoploid. If one or more points of the space not on a boundary between honeycells lie inside more than one honeycell, the tessellation is polyploid. Tessellations may also be constructed that have “holes,” that is, regions that lie inside none of the honeycells; such tessellations are called holeycombs. It is possible for a polyploid tessellation to also be a holeycomb, but not for a panoploid tessellation, which must fill the entire space exactly once. Polyploid tessellations are also called starcombs or star-tessellations. Holeycombs usually arise when (n!1)-dimensional tessellations are themselves permitted to be honeycells; these take up the otherwise free facets that bound the “holes,” so that all the facets continue to belong to two honeycells. In this essay, as per its title, we are concerned with just the uniform panoploid tetracombs. -

Convex Polytopes and Tilings with Few Flag Orbits
Convex Polytopes and Tilings with Few Flag Orbits by Nicholas Matteo B.A. in Mathematics, Miami University M.A. in Mathematics, Miami University A dissertation submitted to The Faculty of the College of Science of Northeastern University in partial fulfillment of the requirements for the degree of Doctor of Philosophy April 14, 2015 Dissertation directed by Egon Schulte Professor of Mathematics Abstract of Dissertation The amount of symmetry possessed by a convex polytope, or a tiling by convex polytopes, is reflected by the number of orbits of its flags under the action of the Euclidean isometries preserving the polytope. The convex polytopes with only one flag orbit have been classified since the work of Schläfli in the 19th century. In this dissertation, convex polytopes with up to three flag orbits are classified. Two-orbit convex polytopes exist only in two or three dimensions, and the only ones whose combinatorial automorphism group is also two-orbit are the cuboctahedron, the icosidodecahedron, the rhombic dodecahedron, and the rhombic triacontahedron. Two-orbit face-to-face tilings by convex polytopes exist on E1, E2, and E3; the only ones which are also combinatorially two-orbit are the trihexagonal plane tiling, the rhombille plane tiling, the tetrahedral-octahedral honeycomb, and the rhombic dodecahedral honeycomb. Moreover, any combinatorially two-orbit convex polytope or tiling is isomorphic to one on the above list. Three-orbit convex polytopes exist in two through eight dimensions. There are infinitely many in three dimensions, including prisms over regular polygons, truncated Platonic solids, and their dual bipyramids and Kleetopes. There are infinitely many in four dimensions, comprising the rectified regular 4-polytopes, the p; p-duoprisms, the bitruncated 4-simplex, the bitruncated 24-cell, and their duals. -

Coloring Uniform Honeycombs
Bridges 2009: Mathematics, Music, Art, Architecture, Culture Coloring Uniform Honeycombs Glenn R. Laigo, [email protected] Ma. Louise Antonette N. De las Peñas, [email protected] Mathematics Department, Ateneo de Manila University Loyola Heights, Quezon City, Philippines René P. Felix, [email protected] Institute of Mathematics, University of the Philippines Diliman, Quezon City, Philippines Abstract In this paper, we discuss a method of arriving at colored three-dimensional uniform honeycombs. In particular, we present the construction of perfect and semi-perfect colorings of the truncated and bitruncated cubic honeycombs. If G is the symmetry group of an uncolored honeycomb, a coloring of the honeycomb is perfect if the group H consisting of elements that permute the colors of the given coloring is G. If H is such that [ G : H] = 2, we say that the coloring of the honeycomb is semi-perfect . Background In [7, 9, 12], a general framework has been presented for coloring planar patterns. Focus was given to the construction of perfect colorings of semi-regular tilings on the hyperbolic plane. In this work, we will extend the method of coloring two dimensional patterns to obtain colorings of three dimensional uniform honeycombs. There is limited literature on colorings of three-dimensional honeycombs. We see studies on colorings of polyhedra; for instance, in [17], a method of coloring shown is by cutting the polyhedra and laying it flat to produce a pattern on a two-dimensional plane. In this case, only the faces of the polyhedra are colored. In [6], enumeration problems on colored patterns on polyhedra are discussed and solutions are obtained by applying Burnside's counting theorem. -

Local Symmetry Preserving Operations on Polyhedra
Local Symmetry Preserving Operations on Polyhedra Pieter Goetschalckx Submitted to the Faculty of Sciences of Ghent University in fulfilment of the requirements for the degree of Doctor of Science: Mathematics. Supervisors prof. dr. dr. Kris Coolsaet dr. Nico Van Cleemput Chair prof. dr. Marnix Van Daele Examination Board prof. dr. Tomaž Pisanski prof. dr. Jan De Beule prof. dr. Tom De Medts dr. Carol T. Zamfirescu dr. Jan Goedgebeur © 2020 Pieter Goetschalckx Department of Applied Mathematics, Computer Science and Statistics Faculty of Sciences, Ghent University This work is licensed under a “CC BY 4.0” licence. https://creativecommons.org/licenses/by/4.0/deed.en In memory of John Horton Conway (1937–2020) Contents Acknowledgements 9 Dutch summary 13 Summary 17 List of publications 21 1 A brief history of operations on polyhedra 23 1 Platonic, Archimedean and Catalan solids . 23 2 Conway polyhedron notation . 31 3 The Goldberg-Coxeter construction . 32 3.1 Goldberg ....................... 32 3.2 Buckminster Fuller . 37 3.3 Caspar and Klug ................... 40 3.4 Coxeter ........................ 44 4 Other approaches ....................... 45 References ............................... 46 2 Embedded graphs, tilings and polyhedra 49 1 Combinatorial graphs .................... 49 2 Embedded graphs ....................... 51 3 Symmetry and isomorphisms . 55 4 Tilings .............................. 57 5 Polyhedra ............................ 59 6 Chamber systems ....................... 60 7 Connectivity .......................... 62 References -

Wythoffian Skeletal Polyhedra
Wythoffian Skeletal Polyhedra by Abigail Williams B.S. in Mathematics, Bates College M.S. in Mathematics, Northeastern University A dissertation submitted to The Faculty of the College of Science of Northeastern University in partial fulfillment of the requirements for the degree of Doctor of Philosophy April 14, 2015 Dissertation directed by Egon Schulte Professor of Mathematics Dedication I would like to dedicate this dissertation to my Meme. She has always been my loudest cheerleader and has supported me in all that I have done. Thank you, Meme. ii Abstract of Dissertation Wythoff's construction can be used to generate new polyhedra from the symmetry groups of the regular polyhedra. In this dissertation we examine all polyhedra that can be generated through this construction from the 48 regular polyhedra. We also examine when the construction produces uniform polyhedra and then discuss other methods for finding uniform polyhedra. iii Acknowledgements I would like to start by thanking Professor Schulte for all of the guidance he has provided me over the last few years. He has given me interesting articles to read, provided invaluable commentary on this thesis, had many helpful and insightful discussions with me about my work, and invited me to wonderful conferences. I truly cannot thank him enough for all of his help. I am also very thankful to my committee members for their time and attention. Additionally, I want to thank my family and friends who, for years, have supported me and pretended to care everytime I start talking about math. Finally, I want to thank my husband, Keith. -

Naming Archimedean and Catalan Polyhedra and Tilings
-21- Naming Archimedean and Catalan Polyhedra and Tilings The book in which Archimedes enumerated the polyhedra that have regular faces and equivalent vertices is unfortunately lost; however, its contents were reconstructed by Kepler, from whom the tradi- tional names descend. In this chapter we explain these “Keplerian” names for the Archimedean and Catalan solids and extend them to the analogous tessellations of two- and three-dimensional Euclidean space. We shall describe the polyhedra in dual pairs indicated by the ar- rows, and at the same time give our abbreviations for them, starting with the five Platonic (or regular) ones: TC↔ OD↔ I Tetrahedron Cube Octahedron Dodecahedron Icosahedron Etymologically, the Greek stem “hedr-” is cognate with the Latin “sede-” and the English “seat,” so that, for instance, “dodecahedron” really means “twelve-seater.” (opposite page) The Archimedean solids and their duals can be nicely arranged so that their edges are mutually tangent, at their intersections, to a common sphere. 283 © 2016 by Taylor & Francis Group, LLC 284 21. Naming Archimedean and Catalan Polyhedra and Tilings Truncation and “Kis”ing These are followed by their “truncated” and “kis-” versions. Here, truncation means cutting off the corners in such a way that each regular n-gonal face is replaced by a regular 2n-gonal one. The dual operation is to erect a pyramid on each face, thus replacing a regular m-gon by m isoceles triangles. These give five Archimedean and five Catalan solids: truncated truncated truncated truncated truncated Tetrahedron Cube Octahedron Dodecahedron Icosahedron tT tC tO tD tI kT kC kO kD kI kisTetrahedron kisCube kisOctahedron kisDodecahedron kisIcosahedron The names used by Kepler for the Catalan ones were rather longer, namely, triakis tetrakis triakis pentakis triakis Downloaded by [University of Bergen Library] at 04:55 26 October 2016 tetrahedron hexahedron octahedron dodecahedron icosahedron and were usually printed as single words. -
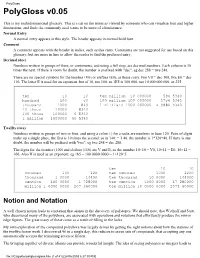
Polygloss V0.05
PolyGloss PolyGloss v0.05 This is my multidimensional glossary. This is a cut on the terms as viewed by someone who can visualise four and higher dimensions, and finds the commonly used terms to be more of a hinderance. Normal Entry A normal entry appears in this style. The header appears in normal bold font. Comment A comment appears with the header in italics, such as this entry. Comments are not suggested for use based on this glossary, but are more in line to allow the reader to find the preferred entry. Decimal (dec) Numbers written in groups of three, or continuous, and using a full stop, are decimal numbers. Each column is 10 times the next. If there is room for doubt, the number is prefixed with "dec", eg dec 288 = twe 248. There are no special symbols for the teenties (V0) or elefties (E0), as these carry. twe V0 = dec 100, twe E0 = dec 110. The letter E is used for an exponent, but of 10, not 100, so 1E5 is 100 000, not 10 000 000 000, or 235. ten 10 10 ten million 10 000000 594 5340 hundred 100 V0 100 million 100 000000 57V4 5340 thousand 1000 840 1 milliard 1000 000000 4 9884 5340 10 thous 10000 8340 100 thous 100000 6 E340 1 million 1000000 69 5340 Twelfty (twe) Numbers written in groups of two or four, and using a colon (:) for a radix are numbers in base 120. Pairs of digits make up a single place, the first is 10 times the second: so in 140: = 1 40, the number is 1*120+40. -

Collection Volume I
Collection volume I PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Thu, 29 Jul 2010 21:47:23 UTC Contents Articles Abstraction 1 Analogy 6 Bricolage 15 Categorization 19 Computational creativity 21 Data mining 30 Deskilling 41 Digital morphogenesis 42 Heuristic 44 Hidden curriculum 49 Information continuum 53 Knowhow 53 Knowledge representation and reasoning 55 Lateral thinking 60 Linnaean taxonomy 62 List of uniform tilings 67 Machine learning 71 Mathematical morphology 76 Mental model 83 Montessori sensorial materials 88 Packing problem 93 Prior knowledge for pattern recognition 100 Quasi-empirical method 102 Semantic similarity 103 Serendipity 104 Similarity (geometry) 113 Simulacrum 117 Squaring the square 120 Structural information theory 123 Task analysis 126 Techne 128 Tessellation 129 Totem 137 Trial and error 140 Unknown unknown 143 References Article Sources and Contributors 146 Image Sources, Licenses and Contributors 149 Article Licenses License 151 Abstraction 1 Abstraction Abstraction is a conceptual process by which higher, more abstract concepts are derived from the usage and classification of literal, "real," or "concrete" concepts. An "abstraction" (noun) is a concept that acts as super-categorical noun for all subordinate concepts, and connects any related concepts as a group, field, or category. Abstractions may be formed by reducing the information content of a concept or an observable phenomenon, typically to retain only information which is relevant for a particular purpose. For example, abstracting a leather soccer ball to the more general idea of a ball retains only the information on general ball attributes and behavior, eliminating the characteristics of that particular ball. -

Wythoff Construction and -Embedding
Wythoff construction and -embedding Michel Deza Serguei Shpectorov ENS/CNRS, Paris and ISM, Tokyo Bowling Green State University Mathieu Dutour-Sikiric Hebrew University, Jerusalem – p.1/47 I. Wythoff kaleidoscope construction W.A. Wythoff (1918) and H.S.M. Coxeter (1935) – p.2/47 Polytopes and their faces A polytope of dimension is defined as the convex hull ¢ of a finite set of points in ¡ . A valid inequality on a polytope £ is an inequality of the ¥§¦ ¨ ¤ ¤ £ £ form © on with linear. A face of is the set of ¥ ¨ ¤ £ ¦ points satisfying to on . A face of dimension , , , is called, respectively, vertex, edge, ridge and facet. – p.3/47 Face-lattice There is a natural inclusion relation between faces, which define a structure of partially ordered set on the set of faces. This define a lattice structure, i.e. every face is uniquely defined by the set of vertices, contained in it, or by the set of facets, in which it is contained. ¢¡¤£ ¢¡ ¨ ¦ ¥ ¥ § Given two faces of dimension © and ¨ ¨ , there are exactly two faces of dimension , such ¦ ¦ ¡¤£ ¥ ¡ ¥ that § . This is a particular case of the Eulerian property satisfied by the lattice: Nr. faces of even dimension=Nr. faces of odd dimension – p.4/47 Skeleton of polytope The skeleton is defined as the graph formed by vertices, with two vertices adjacent if they form an edge. The dual skeleton is defined as the graph formed by facets with two facets adjacent if their intersection is a ridge. In the case of -dimensional polytopes, the skeleton is a planar graph and the dual skeleton is its dual, as a plane graph. -
Geometric Realizations of Abstract Regular Polyhedra with Automorphism Group H3
Ateneo de Manila University Archīum Ateneo Mathematics Faculty Publications Mathematics Department 2-5-2020 Geometric realizations of abstract regular polyhedra with automorphism group H3 Mark L. Loyola Jonn Angel L. Aranas Follow this and additional works at: https://archium.ateneo.edu/mathematics-faculty-pubs Part of the Geometry and Topology Commons electronic reprint ISSN: 2053-2733 journals.iucr.org/a Geometric realizations of abstract regular polyhedra with automorphism group H 3 Jonn Angel L. Aranas and Mark L. Loyola Acta Cryst. (2020). A76, 358–368 IUCr Journals CRYSTALLOGRAPHY JOURNALS ONLINE Copyright c International Union of Crystallography Author(s) of this article may load this reprint on their own web site or institutional repository provided that this cover page is retained. Republication of this article or its storage in electronic databases other than as specified above is not permitted without prior permission in writing from the IUCr. For further information see https://journals.iucr.org/services/authorrights.html Acta Cryst. (2020). A76, 358–368 Aranas and Loyola · Geometric realizations of abstract regular polyhedra research papers Geometric realizations of abstract regular polyhedra with automorphism group H3 ISSN 2053-2733 Jonn Angel L. Aranas and Mark L. Loyola* Department of Mathematics, Ateneo de Manila University, Katipunan Avenue, Loyola Heights, Quezon City 1108, Philippines. *Correspondence e-mail: [email protected] Received 18 October 2019 Accepted 4 February 2020 A geometric realization of an abstract polyhedron P is a mapping that sends an i-face to an open set of dimension i. This work adapts a method based on Wythoff construction to generate a full rank realization of an abstract regular Edited by J.-G. -

Wythoff Construction
See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/288667991 Wythoff construction and l1-embedding Presentation · January 2009 DOI: 10.13140/RG.2.1.2599.1768 CITATIONS READS 0 50 3 authors, including: Michel Marie Deza Mathieu Dutour Sikiric Ecole Normale Supérieure de Paris Ruđer Bošković Institute 418 PUBLICATIONS 5,643 CITATIONS 155 PUBLICATIONS 1,517 CITATIONS SEE PROFILE SEE PROFILE Some of the authors of this publication are also working on these related projects: Curtis Tits Amalgams and Groups View project Sidki's Conjecture View project All content following this page was uploaded by Michel Marie Deza on 29 December 2015. The user has requested enhancement of the downloaded file. Wythoff construction and l1-embedding Michel Deza Serguei Shpectorov ENS, Paris, and JAIST, Ishikawa University of Birmingham Mathieu Dutour-Sikiric Rudjer Boskovic Institute, Zagreb – p. 1/54 I. Wythoff kaleidoscope construction W.A. Wythoff (1918) and H.S.M. Coxeter (1935) – p. 2/54 Polytopes and their faces A polytope of dimension d is defined as the convex hull of a finite set of points in Rd. A valid inequality on a polytope P is an inequality of the form f(x) ≥ 0 on P with f linear. A face of P is the set of points satisfying to f(x) = 0 on P . A face of dimension 0, 1, d − 2, d − 1 is called, respectively, vertex, edge, ridge and facet. – p. 3/54 Face-lattice There is a natural inclusion relation between faces, which define a structure of partially ordered set on the set of faces. -

Construction of Non-Wythoffian Perfect 4-Polytopes
Beitr¨agezur Algebra und Geometrie Contributions to Algebra and Geometry Volume 44 (2003), No. 1, 235-244. Construction of Non-Wythoffian Perfect 4-Polytopes G´abor G´evay Department of Geometry, University of Szeged Aradi v´ertan´uktere 1, H-6720 Szeged, Hungary e-mail: [email protected] Abstract. A polytope is perfect if its shape cannot be changed without changing the action of its symmetry group on its face-lattice. There was a conjecture by which perfect 4-polytopes formed a rather limited class of Wythoffian polytopes. It was disproved in a preceding paper of the author by showing that this class is much more wide. In the present paper we go even further by giving a construction that provides non-Wythoffian perfect 4-polytopes. The construction is based on including the copies of a suitable 3-polytope into the facets of a facet-transitive 4-polytope in a symmetry-preserving way. Keywords: nodal polytope, perfect polytope, regular polytope, semi-nodal poly- tope, Wythoff’s construction 1. Introduction The notion of a perfect polytope was introduced by S. A. Robertson [11], as a general- ization of regular polytopes. Intuitively, a polytope is perfect if it cannot be deformed to a polytope of different shape without altering its symmetry properties. Perfect polytopes are completely known in dimension 2 and 3. Namely, the perfect 2-polytopes coincide with the regular (convex) polygons, and the class of perfect 3-polytopes includes the Platonic solids, the cuboctahedron and icosidodecahedron (these are called “quasi-regular poly- hedra” by Coxeter [2]) along with their polars, the rhombic dodecahedron and rhombic triacontahedron discovered by Kepler.