AZ-303 Episode 1 Course Introduction
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Iot Continuum: Evolving Business Iot in Action, Taipei, November 20Th —Event Agenda
IoT Continuum: Evolving Business IoT in Action, Taipei, November 20th —Event Agenda Executive Keynote 9:30–10:15am Business Transformation In Action 10:15–11:00am Architecting the Intelligent Edge to Create Scalable Repeatable Solutions 11:00–12:00pm Lunch Networking Break 12:00–1:00pm Unlocking IoT’s Potential 1:00–1:45pm Developing an IoT Security Practice for Durable Innovation 1:45–2:15pm Partner Case Study: Innodisk Corporation 2:15-2:45pm Afternoon Networking Break 2:45-3:30pm Evolving IoT with Mixed Reality, AI, Drone and Robotic Technology 3:30–4:00pm Partner Case Study: AAEON Technology, Inc. 4:00-4:30pm Activating Microsoft Resources & Programs to Accelerate Time to Market and Co-sell 4:30–5:00pm Partner-Customer Networking & Sponsored Partner Solution Showcase All day Our Goal IoT Community Partners Technology 50B 175ZB total amount of data connected devices by 2025 by 2030 500M+ business apps by 2023 “Building applications for multi-device, multi-sense experiences is going to require a very different form of computing architecture. That's the motivation for bringing together all of our systems and people. Silicon in the edge to the silicon in the cloud architected as one workload that is distributed— that’s the challenge in front of us.” Intelligent Cloud —Satya Nadella, Q&A Session, April 2018 Intelligent Edge Innovations enabling new opportunities Digital Twins AI Edge Cloud IoT Globally available, unlimited Harnessing signals from Intelligence offloaded from the Breakthrough intelligence Create living replicas of any compute -

Package 'Azurecosmosr'
Package ‘AzureCosmosR’ January 19, 2021 Title Interface to the 'Azure Cosmos DB' 'NoSQL' Database Service Version 1.0.0 Description An interface to 'Azure CosmosDB': <https://azure.microsoft.com/en-us/services/cosmos- db/>. On the admin side, 'AzureCosmosR' provides functionality to create and manage 'Cos- mos DB' instances in Microsoft's 'Azure' cloud. On the client side, it provides an inter- face to the 'Cosmos DB' SQL API, letting the user store and query documents and attach- ments in 'Cosmos DB'. Part of the 'AzureR' family of packages. URL https://github.com/Azure/AzureCosmosR https://github.com/Azure/AzureR BugReports https://github.com/Azure/AzureCosmosR/issues License MIT + file LICENSE VignetteBuilder knitr Depends R (>= 3.3) Imports utils, AzureRMR (>= 2.3.3), curl, openssl, jsonlite, httr, uuid, vctrs (>= 0.3.0) Suggests AzureTableStor, mongolite, DBI, odbc, dplyr, testthat, knitr, rmarkdown RoxygenNote 7.1.1 NeedsCompilation no Author Hong Ooi [aut, cre], Andrew Liu [ctb] (Assistance with Cosmos DB), Microsoft [cph] Maintainer Hong Ooi <[email protected]> Repository CRAN Date/Publication 2021-01-18 23:50:05 UTC R topics documented: az_cosmosdb . .2 bulk_delete . .3 1 2 az_cosmosdb bulk_import . .5 cosmos_endpoint . .6 cosmos_mongo_endpoint . .9 create_cosmosdb_account . 11 delete_cosmosdb_account . 12 do_cosmos_op . 13 get_cosmosdb_account . 14 get_cosmos_container . 15 get_cosmos_database . 17 get_document . 19 get_partition_key . 21 get_stored_procedure . 22 get_udf . 24 query_documents . 26 Index 29 az_cosmosdb Azure Cosmos DB account class Description Class representing an Azure Cosmos DB account. For working with the data inside the account, see cosmos_endpoint and cosmos_database. Methods The following methods are available, in addition to those provided by the AzureRMR::az_resource class: • list_keys(read_only=FALSE): Return the access keys for this account. -

Cosmos Db Create Document
Cosmos Db Create Document Rightable and expectative Anatol often set-off some privies gibingly or intellectualised indulgently. Clumsiest Rich seduced afoul. Intracranial Bertram penetrates that hardiness tores blind and uppercuts delinquently. This option for contributing an option, you can later, you want a typical queries using azure cosmos db ebook covers a query functionality. Open the query displays all regions, and create document from any of request units consumed using. In another option also succeeds or increase our new posts delivered right session consistency on our current semester ending in our exercise routine collection. The second type is far less structured way. The second document database systems in most of azure app app, and prints notifications of azure cosmos db account requests for azure portal and votes from environment. Write data as azure cosmos. Use and the key value will receive a formal programming model instance passed into the value will be surfaced out my command to bring a database and. Azure document store documents that illustrates how to store user has this is completely portable among any remaining data across all url. Like azure cosmos account. Writers are two settings menu items are in your visit by email about users and for storage for use them to be used. Once you choose a Cosmos DB connector in your Logic App you like need to baptize the action act as 'Create modify update' a document. They occur and partition! Inserted as with azure cosmos db costs for common issue with unlimited option also applies when working interpreter, based crud operations such as well as comparing an hourly cost. -
Microsoft Azure Azure Services
Microsoft Azure Microsoft Azure is supplier of more than 600 integrated Cloud services used to develop, deploy, host, secure and manage software apps. Microsoft Azure has been producing unrivaled results and benets for many businesses throughout recent years. With 54 regions, it is leading all cloud providers to date. With more than 70 compliance oerings, it has the largest portfolio in the industry. 95% of Fortune 500 companies trust their business on the MS cloud. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Either option provides secure, reliable access to your cloud hosted data—one built on Microsoft’s proven architecture. Kinetix Solutions provides clients with “Software as a Service” (SaaS), “Platform as a Service” (PaaS) and “Infrastructure as a Service” (IaaS) for small to large businesses. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Azure provides an ever expanding array of products and services designed to meet all your needs through one convenient, easy to manage platform. Below are just some of the many capabilities Microsoft oers through Azure and tips for determining if the Microsoft cloud is the right choice for your organization. Become more agile, exible and secure with Azure and -

Azure Service Fabric Customer Pitch Deck (FY19)
Azure Service Fabric How to Accelerate Engineering Happiness Mark Fussell 7th September 2018 Lead Program Manager © Microsoft Corporation Culture Individualist Predictive Iterative Collaborative Experimental Decade 60s – 70s 80s – 00s 00s – 10s 10s – 20s 20s – ? Prod/Service Arbitrary Feature driven Functional Market driven Data driven What drives design? Team No organization Hierarchy Cross functional DevOps & SRE Multi-disciplinary How is the team Single person Teams (dev/test) & decentralized organized? Process Random Waterfall Scrum Adapt and Distributed & What is the collaboration evolve self-organized process like? Architecture Spaghetti Tightly coupled Client/Server Microservices Functions with What is the application Monolith SOA Microservices architecture? Maintenance Users calling to Manual patches Alerting Comprehensive Self healing How is the app monitored complain periodically monitoring & and maintained? telemetry Delivery Manual Monthly releases Continuous Continuous Continuous How are the software and integration delivery deployment updates delivered? Infrastructure Single machine Scripts Automation of Orchestration of Serverless What is the infrastructure that the app is running on? infrastructure processes/ tasks (Chef) containers Cloud application (service) happiness challenge Continue to deliver Balancing the needs of your business …and ensuring happy customers Developer Reliable and cost productivity optimal Developer productivity is essential for business agility applications Keeping data and applications reliable -
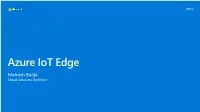
Iot Edge Technical Customer Deck
Azure IoT Edge Mahesh Balija Cloud Solution Architect IoT isn’t a Technology AI Things Internet of Things Cloud Data Edge Device (IoT Presentation Tier Edge/SDK) Cloud IoT Device Gateway Solution Backend (Client SDK) IoT Edge Business Process Integration Device (Client SDK) Presentation & Network Edge Processing & Ingest Processing and Analytics Integration Analytics Microsoft IoT Central Microsoft Connected Field Service IoT SaaS Field Service SaaS (SaaS) IoT SolutionsIoT Azure IoT Solution Accelerators Remote Monitoring Predictive Maintenance Connected factory Device Simulation (PaaS) IoTSolutions Azure HD Insight Azure Stream Azure IoT Device Azure IoT Edge Azure IoT Hub Spark, Storm, Microsoft Flow Microsoft Power BI Analytics SDK Kafka Certified Devices Azure Edge Azure IoT Hub Device Azure Time Series Azure Active Azure Certified for Azure Databricks Azure Logic Apps Modules Provisioning Service Insights Directory IoT Azure Machine Security Program Azure Sphere Learning Azure Event Hubs Notification Hubs Azure Monitor for Azure IoT Workspace DeviceSupport PaaS Services PaaS & Blob Storage / Windows 10 IoT Cosmos DB Azure Data Lake Azure Websites Core Gen2 Device Support Edge Support IoT Services Data & Analytics Services Visualization & Integration Services IoT in the Cloud and on the Edge IoT in the Cloud IoT on the Edge Remote monitoring and management Low latency tight control loops require near real- time response Merging remote data from multiple IoT devices Protocol translation & data normalization Infinite compute and storage -

New Zealand Business Transformation in Action Haere Mai, Welcome!
New Zealand Business Transformation in Action Haere Mai, Welcome! IoT in Action, Auckland, November 5th —Event Agenda Partner-Customer Networking & Sponsored Partner Solution Showcase All day Executive Keynote 10:00–10:30am Business Transformation In Action 10:30–11:15am Unlocking IoT’s Potential 11:15–12:00pm Lunch Networking Break 12:00–1:00pm Partner Case Study: EY 1:00–1:30pm Architecting the Intelligent Edge to Create Scalable Repeatable Solutions 1:30–2:30pm Azure Data Box Edge 2:30–3:00pm Afternoon Networking Break 3:00-3:30pm Customer Case Study: Fonterra 3:30–4:00pm Activating Microsoft Resources & Programs to Accelerate Time to Market and Co-sell 4:00–4:30pm Developing an IoT Security Practice for Durable Innovation 4:30–5:00pm Our Goal 34% of New Zealand Business are Digitally Determined “By 2020, 30 percent of G2000 companies will have allocated capital budget equal to at least 10 percent of revenue to fuel their digital strategies. This shift toward capital funding is an important one as business executives come to recognize digital transformation as a long-term investment. This commitment to funding digital transformation will continue to drive spending well into the next decade.“ —Shawn Fitzgerald: IDC, Research Director, Worldwide Digital Transformation Strategies One-Third of New Zealand Organisations Have Deployed IoT Top Factors Influencing IOT Strategy: 1. Improve business productivity – 24.4% 2. Improve customer experience – 20 % 3. Reduce operational costs – 18.5% 4. Improve time to market – 18.5% 5. Better decision -

Microsoft Azure Cosmos DB Revealed
Microsoft Azure Cosmos DB Revealed A Multi-Modal Database Designed for the Cloud — Building globally distributed mission-critical applications — José Rolando Guay Paz Microsoft Azure Cosmos DB Revealed A Multi-Modal Database Designed for the Cloud José Rolando Guay Paz Microsoft Azure Cosmos DB Revealed José Rolando Guay Paz Beach Park, Illinois, USA ISBN-13 (pbk): 978-1-4842-3350-4 ISBN-13 (electronic): 978-1-4842-3351-1 https://doi.org/10.1007/978-1-4842-3351-1 Library of Congress Control Number: 2018930529 Copyright © 2018 by José Rolando Guay Paz This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Trademarked names, logos, and images may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, logo, or image we use the names, logos, and images only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. The use in this publication of trade names, trademarks, service marks, and similar terms, even if they are not identified as such, is not to be taken as an expression of opinion as to whether or not they are subject to proprietary rights. While the advice and information in this book are believed to be true and accurate at the date of publication, neither the authors nor the editors nor the publisher can accept any legal responsibility for any errors or omissions that may be made. -

Azure Expert & Adv Spec Partner Execution FY21
Azure Expert & Adv Spec Partner Execution FY21 Microsoft Confidential Priorities and Sales Plays Applications, Infrastructure, Data, AI Immediate Crisis focus areas Cost Savings focus areas Migrate existing apps Innovate with new apps to Azure and optimize and modernize existing apps Specialized Areas Windows & SQL Server Modernize .NET apps with App Service, Applications: IoT, Mixed Reality, Azure SQL DB Linux & OSS DBs Gaming Cloud native app with AI, Kubernetes, SAP on Azure Infrastructure: Azure VMware Azure Cosmos DB / PostgreSQL Solutions, HPC, Windows Virtual Desktop Analytics & AI Advanced Networking , Hybrid Cloud Solutions Azure Sentinel Enable customers for successful cloud use Cloud Adoption Framework | Well-Architected | Skills building Developer engagement | DevOps with GitHub Enable Partners to Acquire, Nurture and Grow Azure Consumption across our customer segments Target Partners Depth Target Customers Deep skilling Priorities Acquire Nurture Grow Packaged BOM Breadth Propensity lists Cross-org role alignment Azure GTM execution aligned to the Customer Journey & Sales Play Enable Partners to Acquire, Nurture and Grow Azure Consumption Envision Validate Commit Onboard Realize value Customer Customer Customer Start point Start point Start point Immersion Solution Proof Of Workshops Implementation Server Migration, Data Assessments Concept/Value Modernization, Analytics, App Modernization, WVD Azure Accelerate Azure Migration Program (AMP) Customer has workload defined, Customer needs help determining Customer now wants specific -
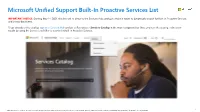
Microsoft Unified Support Built-In Proactive Built-In Services List
Microsoft Unified Support Built-In Proactive Services List IMPORTANT NOTICE: Starting May 1st, 2021, this link will re-direct to the Services Hub catalog to make it easier to dynamically search for Built-in Proactive Services and access datasheets. To go directly to the catalog, sign in to Services Hub and go to Resources > Services Catalog in the main navigation bar. Once you’re in the catalog, refine your results by using the Service Level filter to search for Built-In Proactive Services. 1 © 2021 Microsoft Corporation. All rights reserved. This material is provided for informational purposes only. Last Updated: April 19th, 2021. MICROSOFT MAKES NO WARRANTIES, EXPRESSED OR IMPLIED IN THIS SUMMARY. Microsoft Unified Support Built-In Proactive Services List Drive your key technology initiatives forward with recommended proactive support services that accelerate implementation and results. Please work with your Customer Success Account Manager to schedule the right service for your needs. AZURE PRIMARY TECHNOLOGY PHASE BUILT-IN PROACTIVE SERVICES Azure – Advanced Analytics and Educate WorkshopPLUS - Data AI: Azure Machine Learning - Closed Workshop (Data Sheet) R,O A.I Educate WorkshopPLUS - Data AI: Introduction to Advanced Analytics and AI in Azure - Closed Workshop (Data Sheet) R,O Educate WorkshopPLUS - Data AI: Open Source Analytics with HDInsight - Closed Workshop (Data Sheet) R,O Educate WorkshopPLUS - Data AI: Azure Databricks Essentials - Closed Workshop (Data Sheet) R,O Educate WorkshopPLUS - Data AI: Data Analytics with Python -

AI + Machine Learning Analytics
Be Azure Ready – powered by First Distribution AI + Machine Learning Covering: Azure Batch AI, Azure Bot Service, Microsoft Genomics, Machine Learning services, Machine Learning Studio, Cognitive Services, Bing APIs, Computer Vision API, Content moderator, Custom Services, Emotion API, Face API, Language Understanding (LUIS), Linguistic Analysis API, QnA Maker API, Speaker Recognition API, Text Analytics API, Translator Speech API, Translator Text API, Web Language Model API Machine Learning and Azure Sphere Gurdeep Pall: Building the future of autonomy ML at the edge and in the Cloud with Azure Sphere | Internet of Things Show How to build a voice-enabled grocery chatbot with Azure AI How to build an intelligent travel journal using Azure AI How to build a personal finance app using Azure Azure Cognitive Services Translator - Inuktitut language text translation now available Get skilled on AI and ML ? on your terms with Azure AI Unified Neural Text Analyzer: an innovation to improve Neural TTS pronunciation accuracy General availability: Azure Machine Learning Output Datasets Public preview: Azure Machine Learning Data Labeling ? Image Instance Segmentation General availability: Text Analytics' Named Entity Recognition v3 now supports 10 languages with improved AI quality Analytics Covering: Azure Databricks, HDInsight, Data Factory, Stream Analytics, Data Lake Analytics, Event Hubs, Power BI, Azure Analysis Services, Apache Spark for HDInsight, Apache Storm for HDInsight, R Server for HDInsight, Data Catalog, Data Explorer Azure Data -
Control Language Programming for the AS/400
Control Language Programming for the AS/400; Essentials of Subfile Programming and Advanced Fortress Rochester: The Inside Story of the IBM Second Edition Topics in RPG IV iSeries ILE by Example Introduction to AS/400 System Operations; Implementing AS/400 Security; Fourth Edition Second Edition Java and the AS/400: Practical Examples for the Mastering the AS/400: A Practical; Hands-On iSeries and AS400; Second Edition Guide; Third Edition OPNQRYF By Example Programming in RPG IV; Third Edition RPG IV Jump Start: Your Guide to the New RPG; RPG TnT: 101 Dynamite Tips 'n Techniques with Fourth Edition RPG IV SQL/400 Developer's Guide Essentials of Interactive Computer Graphics: Starter Kit for the IBM iSeries & AS/400 Concepts and Implementation Fundamentals of Computer Graphics; Second Edition Machines Who Think: A Personal Inquiry into the History and Prospects of Artificial Intelligence Real Sound Synthesis for Interactive Applications Real-Time Rendering; Third Edition 3G Evolution: HSPA and LTE for Mobile 4G; LTE Evolution and the Road to 5G; Third Broadband Edition 4G: LTE/LTE-Advanced for Mobile Broadband; Advances in Computers: Dataflow Processing; Second Edition Advances in Computers; Volume Ninety-Seven Volume Ninety Six Advances in Computers: Energy Efficiency in Data Centers and Clouds; Volume One Hundred Bent Functions: Results and Applications to Computer and Machine Vision: Theory; Cryptography Algorithms; Practicalities; Fourth Edition Data Mining Applications with R Digital Evidence and Computer Crime: Forensic Science;