The 1St MEC Student Conference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

THE DHOW May, June, July MEC Newsletter & August 2017
THE DHOW May, June, July MEC Newsletter & August 2017 ISO 9001: 2015 Certification MEC received the ISO 9001: 2015 Certification for Campus Services Department, Human Resources Dr. Kiran G.R. inducted as the Department, Admission Office and Registration Office from Bureau new Dean of Middle East College th Veritas Certification, UK, on 18 May Dr. Kiran Gopakumar Rajalekshmi is appointed as the Dean of 2017. MEC, effective 14th May 2017. Dr. Kiran has more than 20 years of Ambassador of the Republic of experience at the national and international level in areas related Korea to the Sultanate of Oman to higher education management, teaching, research, quality H.E. Ambassador KANG Do-ho, assurance, policy development, social computing, governance paid an official visit to Middle East reforms, e-governance, and ICT for development. College on Wednesday, 2nd August 2017. The ambassador was To quote Dr. Abdullah Saif Ahmed Al Sabahi, Chairman of Middle accompanied by Mr. Seonghun East College, “As a forward-looking leader, Dr. Kiran has been KIM, Third Secretary & Vice Consul, Embassy of the Republic instrumental in devising specific strategies for enhancing the of Korea in the Sultanate. student learning experience through the institutional adoption of active teaching approaches and has also led the College’s Professor John Latham, Vice- efforts to develop a research portfolio and played a major role in Chancellor and CEO of Coventry establishing our international academic partnerships.” University, UK, and Dr. David Pilsbury, Coventry University’s Dr. Saleh Al Shaaibi, Associate Dean, External Affairs and Deputy Vice-Chancellor (International), UK visited Middle Community Outreach, MEC said: “Dr. -

Unai Members List August 2021
UNAI MEMBER LIST Updated 27 August 2021 COUNTRY NAME OF SCHOOL REGION Afghanistan Kateb University Asia and the Pacific Afghanistan Spinghar University Asia and the Pacific Albania Academy of Arts Europe and CIS Albania Epoka University Europe and CIS Albania Polytechnic University of Tirana Europe and CIS Algeria Centre Universitaire d'El Tarf Arab States Algeria Université 8 Mai 1945 Guelma Arab States Algeria Université Ferhat Abbas Arab States Algeria University of Mohamed Boudiaf M’Sila Arab States Antigua and Barbuda American University of Antigua College of Medicine Americas Argentina Facultad de Ciencias Económicas de la Universidad de Buenos Aires Americas Argentina Facultad Regional Buenos Aires Americas Argentina Universidad Abierta Interamericana Americas Argentina Universidad Argentina de la Empresa Americas Argentina Universidad Católica de Salta Americas Argentina Universidad de Congreso Americas Argentina Universidad de La Punta Americas Argentina Universidad del CEMA Americas Argentina Universidad del Salvador Americas Argentina Universidad Nacional de Avellaneda Americas Argentina Universidad Nacional de Cordoba Americas Argentina Universidad Nacional de Cuyo Americas Argentina Universidad Nacional de Jujuy Americas Argentina Universidad Nacional de la Pampa Americas Argentina Universidad Nacional de Mar del Plata Americas Argentina Universidad Nacional de Quilmes Americas Argentina Universidad Nacional de Rosario Americas Argentina Universidad Nacional de Santiago del Estero Americas Argentina Universidad Nacional de -

Higher Education Revolutions in the Gulf
Higher Education Revolutions in the Gulf Over the past quarter century, the people of the Arabian Peninsula have wit- nessed a revolutionary transformation in higher education. In 1990, there were fewer than ten public universities that offered their Arabic- language curricula in sex- segregated settings to national citizens only. In 2015, there are hundreds of public, semi-public and private colleges and universities. Most of these institu- tions are open to expatriates and national citizens; a few offer gender- integrated instruction; and the language of instruction is much more likely to be in English than Arabic. Higher Education Revolutions in the Gulf explores the reasons behind this dramatic growth. It examines the causes of the sharp shift in educational prac- tices and analyses how these new systems of higher education are regulated, evaluating the extent to which the new universities and colleges are improving quality. Questioning whether these educational changes can be sustained, the book explores how the new curricula and language policies are aligned with offi- cial visions of the future. Written by leading scholars in the field, it draws upon their considerable experiences of teaching and doing research in the Arabian Gulf, as well as their different disciplinary backgrounds (linguistics and eco- nomics), to provide a holistic and historically informed account of the emer- gence and viability of the Arabian Peninsula’s higher education revolutions. Offering a comprehensive, critical assessment of education in the Gulf Arab states, this book represents a significant contribution to the field and will be of interest to students and scholars of Middle East and Gulf Studies, and essential for those focused on higher education. -

THE DHOW Jan-Feb 2017 MEC Newsletter
THE DHOW Jan-Feb 2017 MEC Newsletter Message from the Dean Prof. Dr. Sultan Abu Orabi Al-Edwan, the Secretary General of Association of Arab Universities (AARU) visited Middle East College In its 15th year, MEC’s progressive journey on 8th February 2017. continues… with its head held high... cruising on to destination next… like a Dhow. The Fall 2016 semester witnessed a series of achievements and events - the new Student Hub, Annual Graduation Ceremony, Community Outreach programmes, various Prof. Abdullah Al Zoubi, Vice President of Princess industry engagements and activities, student Sumaya University for Technology, visited achievements, “Day out with the Dean” MEC on Monday, 21st February 2017. During and many more. We had the privilege of his visit, he delivered a lecture on ‘Enhancing welcoming some very special guests from Quality of eLearning and Remote Laboratories in within and outside Oman. These activities Engineering Education’. and visits reinforced our innovative teaching and learning practices, improved campus life and gave us the opportunity to grow as an institution. This edition of Dhow, with its new look as a monthly newsletter, captures Prof. Nick Harris, UK consultant in HE, LLL and a glimpse of the special “moments” of the quality assurance, visited MEC during the month of semester. February 2017 as part of the collaboration between MEC, University of Barcelona (UB) and ANECA My sincere thanks to the DHOW team (The National Agency for Quality Assessment for their efforts in bringing out this special and Accreditation of Spain) on enhancing Quality newsletter! Assurance (QA) System at MEC. Students and staff make MEC what it is. -

The Forgotten Ones: How Rural Teachers in Mexico Are Facing the COVID-19 Pandemic
The Forgotten Ones: How Rural Teachers in Mexico are Facing the COVID-19 Pandemic The Forgotten Ones: How Rural Teachers in Mexico are Facing the COVID-19 Pandemic Brenda Cecilia Padilla Rodríguez Universidad Autónoma de Nuevo León Alejandro Armellini University of Portsmouth, United Kingdom John Traxler University of Wolverhampton, United Kingdom Abstract The COVID-19 global pandemic resulted in the cancellation of face-to-face classes in Mexico, as it did across the world. This paper focuses on the experiences of 75 rural teachers in Mexico, who represent a minority in a country where approximately 80% of the population lives in urban areas. An online survey was administered to participants, who taught in a variety of schools, including K-12 and university settings. These participants shared how they changed their teaching practice, the challenges they faced, and the support they required. The digital divide represented a key challenge for both teachers and their students. In the face of inconsistent, unclear, or non-existent government support, most rural teachers showed commitment, resilience, and resourcefulness. They took control of, and responsibility for, their professional development by seeking ways to fill gaps in their knowledge and continue supporting their learners. Recommendations for institutional authorities and policy makers are discussed. Keywords: Rural teachers, pandemic, COVID-19, educational changes, teaching practices, staff development, resourcefulness, emergency remote teaching, digital learning Padilla Rodríguez, -

A News Big Data Analysis of Issues in Higher Education in Korea Amid the COVID-19 Pandemic
sustainability Article A News Big Data Analysis of Issues in Higher Education in Korea amid the COVID-19 Pandemic Jangwan Ko 1, Seungsu Paek 2,*, Seoyoon Park 1 and Jiwoo Park 1 1 College of Education, Sungkyunkwan University, Seoul 04063, Korea; [email protected] (J.K.); [email protected] (S.P.); [email protected] (J.P.) 2 Graduate School of Education, Gachon University, Seongnam 13120, Korea * Correspondence: [email protected]; Tel.: +82-31-750-8625 Abstract: This paper examines the main issues regarding higher education in Korea—where college education experienced minimal interruptions—during the COVID-19 pandemic through a big data analysis of news articles. By analyzing policy responses from the government and colleges and examining prominent discourses on higher education, it provides a context for discussing the implications of COVID-19 on education policy and what the post-pandemic era would bring. To this end, we utilized BIgKinds, a big data research solution for news articles offered by the Korea Press Foundation, to select a total of 2636 media reports and conducted Topic Modelling based on LDA algorithms using NetMiner. The analyses are split into three distinct periods of COVID-19 spread in the country. Some notable topics from the first phase are remote class, tuition refund, returning Chinese international students, and normalization of college education. Preparations for the College Scholastic Ability Test (CSAT), contact and contactless classes, preparations for early admissions, and supporting job market candidates are extracted for the second phase. For the third phase, the extracted topics include CSAT and college-specific exams, quarantine on campus, social Citation: Ko, J.; Paek, S.; Park, S.; relations on campus, and support for job market candidates. -
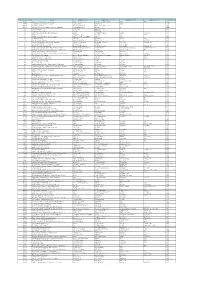
ORGANIZATION ID NAME ADDRESS LINE 1 ADDRESS LINE 2 ADDRESS LINE 3 ADDRESS LINE 4 COUNTRY ID 159828 Ministry of Foreign Affairs O
ORGANIZATION_ID NAME ADDRESS_LINE_1 ADDRESS_LINE_2 ADDRESS_LINE_3 ADDRESS_LINE_4 COUNTRY_ID 159828 Ministry of Foreign Affairs of Afghanistan Malik Asghar Square Shah Mahmood Ghazi Street Kabul 1000 AFG 150484 Aleksander Moisiu University of Durres Currila street Quarter no 1 Durres ALB 109400 IAE Business School Mariano Acosta s/n y Ruta 8 - Pilar - Buenos Aires ARG 138701 American University of Armenia - Office of Admissions 40 Baghramyan Ave Yerevan 19 ARM 13 IELTS Australia 1 Geils Court Deakin ACT 2600 AUS 52 University of New England Armidale NSW 2350 AUS 65 Sydney Institute of Business and Technology Level 4 255 Elizabeth Street Sydney NSW 2000 AUS 70 RMIT International 330 Swanston Street Melbourne Victoria 3000 AUS 72 UNSW - Admissions & Student Recruitment University of New South Wales Sydney 2052 AUS 73 La Trobe University Bundoora Melbourne Victoria 3086 AUS 75 Southern Cross University International Office PO Box 157 Lismore NSW 2480 AUS 85 University of Tasmania - International Admissions University of Tasmania Private Bag 11 Hobart TAS 7001 Tasmania 7000 AUS 86 University of Melbourne - Admissions Swanston Street Parkville Victoria 3010 AUS 99 Monash University - International International Recruitment 871 Dandenong road Caulfield East Victoria 3145 AUS 103 Australian National University - ANU Admissions Office Admissions & Student Services Building X-005 The Australian National Unv Canberra ACT 0200 AUS 112 SAIBT South Australian Institute of Business and Technology GPO Box 2471 Adelaide South Australia 5001 AUS 130 Charles -

UK Higher Education Engagement with the Cooperation Council for The
STATE OF THE RELATIONSHIP UK HIGHER EDUCATION ENGAGEMENT WITH THE COOPERATION COUNCIL FOR THE ARAB STATES OF THE GULF ACKNOWLEDGEMENTS This is an independent report produced by Finally, UUKi wishes to thank those universities Universities UK International (UUKi). The report which contributed case studies: was funded by the Department for Business, Energy • Cranfield University and Industrial Strategy. The primary research, data • Aston University analysis, and preparation of the report were led by Janet Ilieva of Education Insight. The project was • Muscat University managed by Emily Judson, Policy Officer, MENA • Heriot-Watt University at UUKi. • University of Strathclyde UUKi would also like to acknowledge contributions • Coventry University made by the following individuals: • Cardiff University • Daniel Hurley, Universities UK • University of Liverpool • Zahir Irani, University of Bradford • Cardiff Metropolitan University • Christine Bateman, University of Liverpool • Michael Peak, British Council UUKi UK HE engagement with the GCC 1 CONTENTS 1. REPORT OVERVIEW 2 1.1 Executive summary 3 1.2 Key findings from the UUKi sector survey 5 2. GLOBALLY MOBILE STUDENTS FROM THE GCC AND WIDER REGION 6 2.1 Demand for international education in the GCC and wider region 6 2.2 Overseas study destinations for students from the GCC and wider region 7 2.3 Section summary 8 3. UK UNIVERSITIES’ GCC ACTIVITIES, STRATEGY AND OPERATIONS 9 3.1 Activities 9 3.2 Strategy and operations 10 3.3 Outward mobility of UK students to GCC countries 11 3.4 GCC staff employment at UK universities 11 3.5 Section summary 11 4. GCC STUDENT ENROLMENTS AT UK HEIs 13 4.1 GCC student enrolment trends 13 4.2 Sources of funding for GCC students 15 4.3 Approaches to GCC student recruitment 18 4.4 Section summary 21 5. -

Student Handbook for Uow Programmes
In affiliation with University of Wolverhampton STUDENT HANDBOOK PART A – GENERAL REGULATIONS PART B – PROGRAMME REGULATIONS (GFP) PART C – PROGRAMME REGULATIONS (UG) MEC Student Handbook - UG Programmes (University of Wolverhampton) | 1 DISCLAIMER The statements and policies in this handbook are for informational purposes only and serve as guidelines for a successful campus life. The College reserves the right to revise or amend the information of this handbook at any time. Students will be informed of any such revisions or amendments made. 2 | MEC Student Handbook - UG Programmes (University of Wolverhampton) WELCOME FROM DEAN Dear Students, Welcome to Middle East College (MEC), one of the most reputed institutions of higher education in the Sultanate of Oman. We believe in contributing to the development of a harmonious and sustainable world through the pursuit of knowledge. Founded in 2002, MEC is one of the fastest growing higher education institutions in the Sultanate with around 5000 students from 25 different countries. MEC offers 13 undergraduate and 4 postgraduate programmes in academic partnerships with Breda University of Applied Sciences (Netherlands), Coventry University (UK), and University of Wolverhampton (UK). Middle East College is the first educational institution in the Gulf to offer specialized Diploma and Bachelor degrees in Contemporary Archives Science in collaboration with the National Records and Archives Authority of Oman. With a continuously evolving curriculum, various professional body memberships, university associations, and innovative teaching and learning practices at MEC, our students gain professional competence to stay abreast with the latest technologies in their field of study. Our students are provided with opportunities for developing their creativity, and a sense of community in an intercultural environment through various co- curricular and extra-curricular activities, supported by an expanding infrastructure. -

The Impact of COVID-19 on the Private Higher Education System and Students in Oman
Journal of University Teaching & Learning Practice Volume 18 Issue 3 Article 013 2021 The impact of COVID-19 on the private higher education system and students in Oman Mohammed Abushammala Middle East College, Oman Wajeeha Qazi Middle East College, Oman, [email protected] Ram Kishore Manchiryal Middle East College, Oman, [email protected] Follow this and additional works at: https://ro.uow.edu.au/jutlp Recommended Citation Abushammala, M., Qazi, W., & Manchiryal, R. (2021). The impact of COVID-19 on the private higher education system and students in Oman. Journal of University Teaching & Learning Practice, 18(3). https://ro.uow.edu.au/jutlp/vol18/iss3/013 Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] The impact of COVID-19 on the private higher education system and students in Oman Abstract The outbreak of novel coronavirus (COVID-19) worldwide has had a significant impact on the global higher education community. The governments around the world adopted social confinement measures to combat COVID-19, which has resulted in the closure of higher education institutions. Faced with multiple challenges, faculties rapidly converted curriculum to an online environment, which is anticipated to occur without sufficient eparpr ation. Therefore, this study conducted a survey of students in post- secondary private institutions throughout Oman, to understand different approaches adopted by academic institutions to deliver education during the COVID-19 restriction, and the consequences of these restrictions on academic activities and quality of education. Moreover, the extent to which personal and financial circumstances have created challenges for students to continue their education is also analyzed. -

Handbook PG 2019
STUDENT HANDBOOK POSTGRADUATE PROGRAMME PART A – GENERAL REGULATIONS PART B – PROGRAMME REGULATIONS Disclaimer The statements and policies in this handbook are for informational purposes only and serve as guidelines for a successful campus life. The College reserves the right to modify the information in this handbook and keep students advised of any such changes. 2 MEC Postgradute student Handbook WELCOME FROM DEAN Dear Students, Welcome to Middle East College (MEC), one of the most reputed institutions of higher education in the Sultanate of Oman. We believe in contributing to the development of a harmonious and sustainable world through the pursuit of knowledge. Founded in 2002, MEC is one of the fastest growing higher education institutions in the Sultanate with around 5000 students from around 25 different countries. MEC offers 13 undergraduate and 4 postgraduate programmes in academic partnerships with Breda University of Applied Science (Netherlands), Coventry University (UK), and University of Wolverhampton (UK). In collaboration with the National Records and Archives Authority of Oman, Middle East College is the first educational institution in the Gulf to offer specialized Diploma and Bachelor degrees in Contemporary Archives Science. With a continuously evolving curriculum, various professional body memberships, university associations and innovative teaching and learning practices at MEC, our students gain professional competence to stay abreast with evolving technologies in their field of study. Our students are provided with opportunities for developing creativity, and a sense of community in an intercultural environment through various co- curricular and extra-curricular activities, supported by an expanding infrastructure. As a responsible Higher Education institution, we focus on continuous improvement which is responsive to the needs of the community and making useful contributions to education, knowledge and society at large. -

Muscat College
Sultanate of Oman Ministry of Higher Education Directorate General of Private Universities & Colleges Department of programmes supervision Academic Programs in Private Higher Education Institutions 2019 - 2020 Academic Programs in Private Higher Education Institutions 2019-2020 Ministry of Higher Education P.O. Box 1079, Postal Code 111 Seeb- Sultanate of Oman www.mohe.gov.om His Majesty Sultan Qaboos Bin Said CONTENTS A’sharqiyah University 6 Arab Open University 9 Dhofar University 10 German University of Technology In Oman 12 Muscat University 14 National University of Science & Technology 15 Nizwa University 17 Sohar University 20 University Of Buraimi 22 Al Bayan College 23 Al Buraimi College 24 Al Zahra College 25 Global college of Engineering and Technology 26 Gulf College 27 International College Of Engineering & Management 28 International Maritime College Oman 29 Majan College 30 Mazoon College 23 Middle East College 24 Modern College Of Business And Science 36 National College of Automotive Technology 37 Muscat College 38 Oman College Of Management & Technology 39 Oman Dental College 40 Oman Tourism College 41 Scientific College Of Design 42 Sur University College 43 Waljat College 44 4 INTRODUCTION Education is one of the most important nation-building pillar and progress, and an integral part of the culture of society and its development. With this in mind came, his Majesty Sultan Qaboos bin Said’s Royal Care and keenness about the importance of science and knowledge and the need to Follow up its development by all means available, in a way that contributes to the advancement and progress of Omani citizen. In orderto encourage the sector,the Ministryprovides allthe necessaryfacilities,including (financial, material and moral support) to ensure the best educational levels.