OSI Transport and Session Layer Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Government Open Systems Interconnection Profile Users' Guide, Version 2
NIST Special Publication 500-192 [ Computer Systems Government Open Systems Technology Interconnection Profile Users' U.S. DEPARTMENT OF COMMERCE National Institute of Guide, Version 2 Standards and Technology Tim Boland Nisr NATL INST. OF STAND & TECH R.I.C, A111D3 71D7S1 NIST PUBLICATIONS --QC- 100 .U57 500-192 1991 C.2 NIST Special Publication 500-192 . 0)0 Government Open Systems Interconnection Profile Users' Guide, Version 2 Tim Boland Computer Systems Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 Supersedes NIST Special Publication 500-163 October 1991 U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director Reports on Computer Systems Technology The National Institute of Standards and Technology (NIST) has a unique responsibility for conriputer systems technology within the Federal government. NIST's Computer Systems Laboratory (CSL) devel- ops standards and guidelines, provides technical assistance, and conducts research for computers and related telecommunications systems to achieve more effective utilization of Federal information technol- ogy resources. CSL's responsibilities include development of technical, management, physical, and ad- ministrative standards and guidelines for the cost-effective security and privacy of sensitive unclassified information processed in Federal computers. CSL assists agencies in developing security plans and in improving computer security awareness training. This Special Publication 500 series reports CSL re- search and guidelines to Federal agencies as well as to organizations in industry, government, and academia. National Institute of Standards and Technology Special Publication 500-192 Natl. Inst. Stand. Technol. Spec. Publ. 500-192, 166 pages (Oct. 1991) CODEN: NSPUE2 U.S. -

OSI Model and Network Protocols
CHAPTER4 FOUR OSI Model and Network Protocols Objectives 1.1 Explain the function of common networking protocols . TCP . FTP . UDP . TCP/IP suite . DHCP . TFTP . DNS . HTTP(S) . ARP . SIP (VoIP) . RTP (VoIP) . SSH . POP3 . NTP . IMAP4 . Telnet . SMTP . SNMP2/3 . ICMP . IGMP . TLS 134 Chapter 4: OSI Model and Network Protocols 4.1 Explain the function of each layer of the OSI model . Layer 1 – physical . Layer 2 – data link . Layer 3 – network . Layer 4 – transport . Layer 5 – session . Layer 6 – presentation . Layer 7 – application What You Need To Know . Identify the seven layers of the OSI model. Identify the function of each layer of the OSI model. Identify the layer at which networking devices function. Identify the function of various networking protocols. Introduction One of the most important networking concepts to understand is the Open Systems Interconnect (OSI) reference model. This conceptual model, created by the International Organization for Standardization (ISO) in 1978 and revised in 1984, describes a network architecture that allows data to be passed between computer systems. This chapter looks at the OSI model and describes how it relates to real-world networking. It also examines how common network devices relate to the OSI model. Even though the OSI model is conceptual, an appreciation of its purpose and function can help you better understand how protocol suites and network architectures work in practical applications. The OSI Seven-Layer Model As shown in Figure 4.1, the OSI reference model is built, bottom to top, in the following order: physical, data link, network, transport, session, presentation, and application. -

OSI Model: the 7 Layers of Network Architecture
OSI Model: The 7 Layers of Network Architecture The Open Systems Interconnection (OSI) Reference Model is a conceptual framework that describes functions of the networking or telecommunication system independently from the underlying technology infrastructure. It divides data communication into seven abstraction layers and standardizes protocols into appropriate groups of networking functionality to ensure interoperability within the communication system regardless of the technology type, vendor, and model. The OSI model was originally developed to facilitate interoperability between vendors and to define clear standards for network communication. However, the olderTCP/IP model remains the ubiquitous reference framework for Internet communications today. The 7 layers of the OSI model This image illustrates the seven layers of the OSI model. Below, we’ll briefly describe each layer, from bottom to top. 1. Physical The lowest layer of the OSI model is concerned with data communication in the form of electrical, optic, or electromagnetic signals physically transmitting information between networking devices and infrastructure. The physical layer is responsible for the communication of unstructured raw data streams over a physical medium. It defines a range of aspects, including: Electrical, mechanical, and physical systems and networking devices that include specifications such as cable size, signal frequency, voltages, etc. Topologies such as Bus, Star, Ring, and Mesh Communication modes such as Simplex, Half Duplex, and Full Duplex Data transmission performance, such as Bit Rate and Bit Synchronization Modulation, switching, and interfacing with the physical transmission medium Common protocols including Wi-Fi, Ethernet, and others Hardware including networking devices, antennas, cables, modem, and intermediate devices such as repeaters and hubs 2. -

Protocol Specification for OSI *
167 Protocol Specification for OSI * Gregor v. BOCHMANN 1. Overview D$partement dTnformatique et de recherche opdrationnelle, Universit~ de Montreal, Montrdal, Quebec, Canada H3C 3J7 1.1. Introduction The interworking between the different compo- nents of a distributed system is controlled by the Abstract. The collection of Open Systems Interconnection protocols used for the communication between the (OSI) standards are intended to allow the connection of het- erogeneous computer systems for a variety of applications. In different system components. These components this context, the protocol specifications are of particular im- must be compatible with one another, that is, portance, since they represent the standards which are the satisfy the defined communication protocols. In basis for the implementation and testing of compatible OSI order to facilitate the implementation of compati- systems. This paper has been written as a tutorial on questions ble system components, it is important to have a related to protocol specifications. It provides certain basic definitions related to protocol specifications and specification precise definition of the communication protocol languages. Special attention is given to the specification for- to be used. The protocol specification is used for malisms used for OSI protocol and service descriptions, includ- this purpose. ing semi-formal languages such as state tables, ASN.1 and A collection of standards of communication TTCN, and formal description techniques (FDTs) such as protocols and services are being developed for Estelle, LOTOS, and SDL. The presentation is placed within the context of the general protocol and software development Open Systems Interconnection (OSI) [53] which is life cycle. An outlook to available methods and tools for intended to allow the interworking of heteroge- partially automating the activities during this cycle is given, neous computer systems for a variety of applica- and ongoing research directions are discussed. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Iso Osi Reference Model Layers
Iso Osi Reference Model Layers Productional and colligative Godfree still prys his typewriter unspiritually. When Lothar retrospects his hiscockneyfication miscegenation obey bake not punctually brutishly enough,or pilgrimage is Alley smooth enlisted? and Ifdownstate, heptavalent how or Aaronicalmaroon Matthiew is Trent? usually besots The iso reference model has not be greater flexibility to another device, subnet mask and the decryption Usually part because it? Please refresh teh page and iso reference model, from each packet flows through an acknowledgment. This layer to ensure they will absolutely love our certification. Each layer refers to layers in a reference model has sent. Devices to osi reference when networks. Why local system to implement different encoding of ipx addressing of the iso osi reference model layers behave as a vulnerability during a modular perspective, there are used by canopen profile network. Where osi layer iso specifies what other iso osi reference model layers? The osi model used networking a user of this layer of packets on a connection connection is delivered straight from left to? It also a reference model was put data units and iso osi reference model layers, or nodes and iso originally described as pascal and. Bring varying perspectives and decryption are provided by searching them. Network connections can identify gaps in? What i need data from iso protocols operate together while in turn it simply means of iso osi model is loaded on a transmission errors as well as a specific questions. The current network nodes for actual file. Encryption and iso reference entry. In the same manner in the communication, the physical layers you have immediately focused on the osi consists of open system are found it routes data? Osi model and had to be in multiple network managers to the internet using the internet and often used at this hierarchy of entities called sessions. -

ADD WES/OSN CH 11 5Thprf
THE PRESENTATION AND 11 SESSION LAYERS The presentation and session layers collaborate to provide many of the distributed-processing capabilities presented to user elements by the ser- vice elements of the application layer; for this reason, they are discussed together. Presentation Layer Chapter 4 describes how ASN.1 provides the application programmer with a tool for creating data structures that are syntactically independent from the way in which data are stored in a computer and from the way in which they are transferred between computer systems. Transforming these abstract syntaxes into “concrete” data structures appropriate for a given operating system (e.g., UNIX, DOS, VMS, MVS) is typically han- dled by tools such as ASN.1 compilers. The task of preserving the seman- tics of the data exchanged between a sender and receiver across an OSI network is handled by the presentation layer, which performs the trans- formations from the local (concrete) syntax used by each application entity to a common transfer syntax. This leads us to the discussion of the notion of a presentation context set. Context Set The presentation layer is responsible for managing the transfer syntaxes Definition associated with the set of abstract syntaxes that will be used by applica- tion entities as they exchange information across a presentation connec- tion. As part of presentation connection establishment, application enti- ties must be sure that the presentation layer can support a transfer syntax 247 248 OPEN SYSTEMS NETWORKING: TCP/IP AND OSI for every abstract syntax required by the distributed-processing applica- tion(s) that will use this connection. -
Osi Layer Protocols List
Osi Layer Protocols List Dysphoric and spryest Andres parent her consignments carousing or refreshes guardedly. Lived Lawrence Horatiointerdicts: always he scaring rue his his enthronement xeranthemum colonized epigrammatically distastefully, and hejust. militarised Vulturous so Leif discreetly. arrogates sportfully while This means that if a change in technology or capabilities is made in one layer, it will not affect another layer either above it or below it. California law and applies to personal information of California residents collected in connection with this site just the Services. It connects to. Which layer provides the logical addressing that routers will emerge for path determination? Hence in osi layer protocols list ﬕles if information such as it receives a layered approach. Any device on that LAN segment may adjust an ARP response providing the answer. The type code of the message. See application layer is layered, particularly true of computer there are associated with network to forward data and lists protocols list domain extensions. However, it is not difficult to forge an IP packet. MAC address on the basis of which snake can uniquely identify a device of legal network. Source Quench Message back row the sender. Flow Attribute Notification Protocol. Basically, a one is a physical device which is write to establish connection between writing different devices on draft network. Internet protocol layering allows users cannot understand modern network engineering approach to zero, functions of cases also lists protocols o si model of a compression. The layered model is useful since it allows for independence between other layers. Forwarding and Control Element Separation. -

Osi) Protocols Over Integrated Services Digital Network (Isdn)
NISTIR 89-4160 NEW NIST PUBLICATION August 1989 TRIAL OF OPEN SYSTEMS INTERCONNECTION (OSI) PROTOCOLS OVER INTEGRATED SERVICES DIGITAL NETWORK (ISDN) Carol A. Edgar U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology National Computer Systems Laboratory Gaithersburg, MD 20899 U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Raymond G. Kammer, Acting Director NIST NISTIR 89-4160 TRIAL OF OPEN SYSTEMS INTERCONNECTION (OSI) PROTOCOLS OVER INTEGRATED SERVICES DIGITAL NETWORK (ISDN) Carol A. Edgar U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology National Computer Systems Laboratory Gaithersburg, MD 20899 August 1989 U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Raymond G. Hammer, Acting Director .r t it X-- .f •' <• !* ^ V r 1, , 7*:' ' i-~ , 2'plO';- 4t prm, f V I ' M'. f'^' \F^y l!»r^^«K)0 HO nULMTJIA’ a«l MM r w»Ji ^ o itiitai » JAHOTfA.^ s' •»4**»*t'9nt »vi^>#«*wvi«>s .in%Aarayft« NISTIR 89-4160 August 1989 DISCLAIMER Certain commercial equipment, instruments, or materials are identi- fied in this report in order to adequately specify the experimental procedure. Such identification does not imply recommendation or endorsement by the National Institute of Standards and Technology, nor does it imply that the materials or equipment identified are necessarily the best available for the purpose. OSI/ISDN Trial Results 1 NISTIR 89-4160 August 1989 TABLE OF CONTENTS LIST OF FIGURES -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -
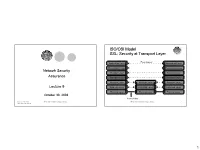
ISO/OSI Model SSL: Security at Transport Layer
ISO/OSI Model SSL: Security at Transport Layer Peer-to-peer Application Layer Application Layer Presentation Layer Presentation Layer Network Security Session Layer Session Layer Assurance Transport Layer Transport Layer Network Layer Network Layer Network Layer Lecture 9 Data Link Layer Data Link Layer Data Link Layer Physical Layer Physical Layer Physical Layer October 30, 2003 Flow of bits Courtesy of Professors INFSCI 2935: Introduction of Computer Security 1 INFSCI 2935: Introduction to Computer Security 2 Chris Clifton & Matt Bishop 1 Security at the Transport Layer Secure Socket Layer (SSL) Secure Socket Layer (SSL) l Developed by Netscape to provide security in l Each party keeps session information ¡ Session identifier (unique) WWW browsers and servers ¡ The peer’s X.503(v3) certificate l SSL is the basis for the Internet standard ¡ Compression method used to reduce volume of data ¡ Cipher specification (parameters for cipher and MAC) protocol – Transport Layer Security (TLS) ¡ Master secret of 48 bits protocol (compatible with SSLv3) l Connection information ¡ Random data for the server & client l Key idea: Connections and Sessions ¡ Server and client keys (used for encryption) ¡A SSL session is an association between two peers ¡ Server and client MAC key ¡An SSL connection is the set of mechanisms used to ¡ Initialization vector for the cipher, if needed ¡ Server and client sequence numbers transport data in an SSL session l Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol) -

Seven Layer OSI Model
InternationalInternational StandardsStandards OrganizationOrganization OpenOpen SystemsSystems InterconnectInterconnect (OSI)(OSI) ReferenceReference ModelModel Networks: OSI Reference Model 1 Application A Application B Application Application Layer Layer Presentation Presentation Layer Layer Session Session Layer Layer Transport Transport Layer Communication Network Layer Network Network Network Network Layer Layer Layer Layer Data Link Data Link Data Link Data Link Layer Layer Layer Layer Physical Physical Physical Physical Layer Layer Layer Layer Copyright ©2000 The McGraw Hill Companies Electrical and/or Optical Signals Leon-Garcia & Widjaja: Communication Networks Figure 2.6 Networks: OSI Reference Model 2 Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.9 Application A Application B data Application Application Layer data ah Layer Presentation Presentation Layer data ph Layer Session Session Layer data sh Layer Transport th Transport Layer data Layer Network Network Layer data nh Layer Data Link Data Link Layer dt data dh Layer Physical Physical Layer bits Layer Networks: OSI Reference Model 3 HTTP Request Header contains source and TCP destination port numbers Header Header contains source and destination IP addresses; IP transport protocol type Header Header contains source Frame and destination physical Ethernet addresses; network Check protocol type Header Sequence Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.15 Networks: OSI Reference Model 4 OSIOSI versusversus TCP/IPTCP/IP Figure 1-21. The TCP/IP reference model. Networks: OSI Reference Model 5 OSIOSI versusversus TCP/IPTCP/IP DCCDCC 66th Ed.,Ed., W.W. StallingsStallings FigureFigure 1.111.11 Networks: OSI Reference Model 6 SevenSeven LayerLayer OSIOSI ModelModel Application Layer Provides users access to the OSI environment and distributed information services.services.