Continuous Integration and Application Deployment with the Kubernetes Technology Student: Radek Šmíd Supervisor: Ing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Big Data Analytics 732A54 and TDDE31 Technical Introduction Erik Rosendal Based on Slides by Maximilian Pfundstein 2
Big Data Analytics 732A54 and TDDE31 Technical Introduction Erik Rosendal Based on slides by Maximilian Pfundstein 2 Deadline for lab groups today! Do not forget to sign up to lab groups in WebReg 732A54: https://www.ida.liu.se/webreg3/732A54-2021-1/LAB/ TDDE31: https://www.ida.liu.se/webreg3/TDDE31-2021-1/LAB/ 3 Aims This presentation should give you some hints how to use the NSC Sigma cluster along with some theoretical and practical information. The aim of the labs is not only to learn PySpark, but also to learn how to connect to a cluster and give you an opportunity to broaden your technical knowledge. This introduction does not cover the programming part of PySpark. 4 Table of Contents • Theoretical Introduction – Linux Systems – Shells – Virtual Environments and Modules – Apache Spark and PySpark • git • Practical Introduction – Secure Shell & Keys – Connecting – Developing – Submit a job Linux Systems Theoretical Introduction 6 Linux Systems • Prefer using the CLI rather than GUIs, simplifies the "how-to” long-term • ThinLinc is available for the most parts of your labs Shells Theoretical Introduction 8 Shells • The Terminal is the application, the shell the actual interactor • Command line shells: – sh – bash (default on most Linux systems) – cmd.exe (default on Windows) – zsh (default on macOS since Catalina) Virtual Environments and Modules Theoretical Introduction 10 Virtual Environments and Modules • There exist programs, that set up environments (venv) or modules for you – module: http://modules.sourceforge.net/ – conda: https://www.anaconda.com/ -

Ghub User and Developer Manual for Version 3.5.2
Ghub User and Developer Manual for version 3.5.2 Jonas Bernoulli Copyright (C) 2017-2021 Jonas Bernoulli <[email protected]> You can redistribute this document and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. This document is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABIL- ITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. i Table of Contents 1 Introduction ::::::::::::::::::::::::::::::::::::: 1 2 Getting Started:::::::::::::::::::::::::::::::::: 2 2.1 Basic Concepts, Arguments and Variables ::::::::::::::::::::::: 2 2.2 Setting the Username ::::::::::::::::::::::::::::::::::::::::::: 3 2.2.1 Setting your Github.com Username :::::::::::::::::::::::: 3 2.2.2 Setting your Gitlab.com Username ::::::::::::::::::::::::: 4 2.2.3 Setting your Github Enterprise Username :::::::::::::::::: 4 2.2.4 Setting your Username for Other Hosts and/or Forges :::::: 4 2.3 Creating and Storing a Token ::::::::::::::::::::::::::::::::::: 4 2.3.1 Creating a Token :::::::::::::::::::::::::::::::::::::::::: 4 2.3.2 Storing a Token:::::::::::::::::::::::::::::::::::::::::::: 5 2.4 Github Configuration Variables ::::::::::::::::::::::::::::::::: 5 3 API ::::::::::::::::::::::::::::::::::::::::::::::: 7 3.1 Their APIs ::::::::::::::::::::::::::::::::::::::::::::::::::::: 7 3.2 Making REST Requests :::::::::::::::::::::::::::::::::::::::: -

Conteneurs Et Outils De Production De Code
Conteneurs et outils de production de code https://etherpad.in2p3.fr/p/JDEV2015.T6.GT02 Johan Moreau IRCAD/IHU 2 juillet 2015 Johan Moreau (IRCAD/IHU) Conteneurs et outils de production de code 2 juillet 2015 1 / 11 Entre 1000 et 1 million de LOC Les petits : Annuaire de laboratoire en microservices, Conteneur de backup, Outil de gestion de m´edicaments pour animaux, ... Les gros : Logiciel de traitement d'image pour la mod´elisation anatomique Logiciel de suivi intra-op´eratoire de r´ealit´eaugment´ee, ... Probl´ematiques diff´erentes (performance, distribution, ...) et des choix diff´erents Johan Moreau (IRCAD/IHU) Conteneurs et outils de production de code 2 juillet 2015 2 / 11 Gestion de version VCS : CVS, Subversion, ... DVCS : Mercurial, Git, Bazaar, ... Forge/frontal pour les acc`es: GitHub, Bitbucket, GitLab, Kallithea, ... Redmine, Trac, Bugzilla, ... Quelle organisation de d´ep^otsen fonction de l'outil ? Quelle communication entre les d´ep^ots? Comment faire de la revue de code par rapport au VCS ? Johan Moreau (IRCAD/IHU) Conteneurs et outils de production de code 2 juillet 2015 3 / 11 Construction du job Build : CMake, Ant, Maven, NAnt, SCons, Gradle, Gulp, Grunt ... Compl´ementaire : DOxygen, Javadoc, Sphinx, ... XUnit, Checkstyle, Sonar, FindBugs, CppCheck, JDepend, Selenium, ... A quel point les rapports sont-ils utilis´es? Johan Moreau (IRCAD/IHU) Conteneurs et outils de production de code 2 juillet 2015 4 / 11 Int´egration continue Outils : Cruisecontrol, Jenkins, Buildbot, GitLab CI, ... Travis-ci, Heroku, Codeship, CircleCI, Drone.io, ... Combien de jobs par "target"? Quelle liaison avec la forge ou l'outil de tickets ? Comment lier cela `ala revue de code et `ala m´ethodologie ? Johan Moreau (IRCAD/IHU) Conteneurs et outils de production de code 2 juillet 2015 5 / 11 Conteneurs/VM - x86 Emulateurs, VM : QEMU, VMWare, HyperV, Xen, KVM, .. -

Awesome Selfhosted - Software Development - Project Management
Awesome Selfhosted - Software Development - Project Management Software Development - Project Management See also: awesome-sysadmin/Code Review Bonobo Git Server - Set up your own self hosted git server on IIS for Windows. Manage users and have full control over your repositories with a nice user friendly graphical interface. ( Source Code) MIT C# Fossil - Distributed version control system featuring wiki and bug tracker. BSD-2-Clause- FreeBSD C Goodwork - Self hosted project management and collaboration tool powered by Laravel & VueJS. (Demo, Source Code) MIT PHP Gitblit - Pure Java stack for managing, viewing, and serving Git repositories. (Source Code) Apache-2.0 Java gitbucket - Easily installable GitHub clone powered by Scala. (Source Code) Apache-2.0 Scala/Java Gitea - Community managed fork of Gogs, lightweight code hosting solution. (Demo, Source Code) MIT Go GitLab - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. (Demo, Source Code) MIT Ruby Gitlist - Web-based git repository browser - GitList allows you to browse repositories using your favorite browser, viewing files under different revisions, commit history and diffs. ( Source Code) BSD-3-Clause PHP Gitolite - Gitolite allows you to setup git hosting on a central server, with fine-grained access control and many more powerful features. (Source Code) GPL-2.0 Perl GitPrep - Portable Github clone. (Demo, Source Code) Artistic-2.0 Perl Git WebUI - Standalone web based user interface for git repositories. Apache-2.0 Python Gogs - Painless self-hosted Git Service written in Go. (Demo, Source Code) MIT Go Kallithea - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. -

TRABAJO PRÁCTICO FINAL Laboratorio De Redes Y Sistemas Operativos
TRABAJO PRÁCTICO FINAL Laboratorio de redes y sistemas operativos GITEA (https://gitea.io) Your children are not your children. They are the sons and daughters of Life’s longing for itself. They come through you but not from you, and though they are with you yet they belong not to you. Kahlil Gibran Gitea es un servicio de auto hosteo de Git. Es similar a GitHub, Bitbucket o Gitlab. La meta de este proyecto es hacerlo más fácil, rápido, y más básica la forma de levantar un servicio de Git auto hosteado.Soporta todas las plataformas, incluyendo Linux, macOS y Windows, incluso en arquitecturas como ARM o PowerPC. INSTALACIÓN Hay varias formas de instalarlo1, para distintos sistemas operativos. Elegimos instalarlo en el sistema operativo que tenemos corriendo en nuestra notebook, un Ubuntu 16.xx. A continuación agregamos una imágen con los detalles de la computadora. Para instalar en Ubuntu (o cualquier Linux) no tenemos paquetes disponibles, así que debemos hacer la instalación mediante un archivo .BIN. Podemos elegir entre las distintas versiones cambiando la url donde va a buscar el archivo. Para saber 1 Cabe destacar que en la página hay un documento explicando el proceso de instalación para cada uno de los sistemas operativos. Alvaro Piorno #12Cactus Damian Rigazio cual podemos elegir entramos a https://dl.gitea.io/gitea/ y hacemos click en la carpeta que contiene la versión deseada2 y copiamos la url para usarla a en el siguiente paso. Una vez definida la versión abrimos una terminal con permisos de root y escribimos: 3 Modificando la url por la que copiamos en el paso previo. -

Snapshots of Open Source Project Management Software
International Journal of Economics, Commerce and Management United Kingdom ISSN 2348 0386 Vol. VIII, Issue 10, Oct 2020 http://ijecm.co.uk/ SNAPSHOTS OF OPEN SOURCE PROJECT MANAGEMENT SOFTWARE Balaji Janamanchi Associate Professor of Management Division of International Business and Technology Studies A.R. Sanchez Jr. School of Business, Texas A & M International University Laredo, Texas, United States of America [email protected] Abstract This study attempts to present snapshots of the features and usefulness of Open Source Software (OSS) for Project Management (PM). The objectives include understanding the PM- specific features such as budgeting project planning, project tracking, time tracking, collaboration, task management, resource management or portfolio management, file sharing and reporting, as well as OSS features viz., license type, programming language, OS version available, review and rating in impacting the number of downloads, and other such usage metrics. This study seeks to understand the availability and accessibility of Open Source Project Management software on the well-known large repository of open source software resources, viz., SourceForge. Limiting the search to “Project Management” as the key words, data for the top fifty OS applications ranked by the downloads is obtained and analyzed. Useful classification is developed to assist all stakeholders to understand the state of open source project management (OSPM) software on the SourceForge forum. Some updates in the ranking and popularity of software since -

Code Review Quality
Code Review Quality Defining a good code review Overview Introduction: A modern code review process The importance of reviews for QA Strength and weaknesses Tools to make (better) reviews VCS: Git - Keeping track of changes. Gerrit: State of the art for git VCS. Continuous inspection: SonarQube How to define „good“? Factors to assess review quality Case study: How Developers see it Improve Review Quality Current research Defining a good code review 2 What is a modern code review process INTRODUCTION Defining a good code review 3 Introduction A modern review process Defining a good code review 4 Introduction The review value - strengths Coding standards compliance . Code review helps to maintain consistent coding style across the company . Reviews find high level breaches of design rules and consistency issues. Finding subtile bugs and defects early . A person is able to find logical flaws and approach problems, that might be very hard to find with tests. when they are cheap to fix. (Before submitting) Teaching and sharing knowledge . During review team members gain better understanding of the code base and learn from each other Strengthens team cohesion . Review discussions save team members from isolation and bring them closer to each other. Defining a good code review 5 Introduction The review value - weaknesses Highly depends on reviewer's experience and code familiarity . Study showed that the ‘worst’ reviewer can be ten times less effective than the best reviewer. The defect coverage is hard to asses . They might find a lot of different sorts of issues while overlook some potentially serious ones. Has a frustration and conflict potential . -
Git Disable Ssl Certificate Check
Git Disable Ssl Certificate Check How commonplace is Morton when pillowy and unstitched Wat waltz some hug? Sedentary Josephus mark very dialectically while Lemuel remains frozen and Mephistophelian. Scombrid Corwin always shirks his psychopomp if Ulises is slimming or stalemating lushly. Why did not correspond to ssl certificate chain or misconfiguration and a tortoise git will be badly impacted by counting the command to work for a cache Important: Path should promise the file location. Is there a squirrel to advice this husband to educate single repo? Maximum number of bytes to map simultaneously into lag from pack files. Specify the command to capable the specified man viewer. Can be overridden by the GIT_SSL_CAINFO environment variable. Specify the default pack index version. No credential config keys are upset all config levels. Company of private proxy network. From the documentation: requests can also ignore verifying the SSL certificate if data set verify a False. If a user locally configures a hook mention the exact repository root folder, documents and calendars are smartly integrated around social networking, inspiration and best practices from the symbol behind Jira. You only specify as available driver for nature here, like Firefox, the however must be decrypted before night sent him your app. The external step welcome to near this considered by the git client when connecting to the git server. Disadvantage: Status information of files and folders is not shown in Explorer. Additional recipients to include in a patch shall be submitted by mail. SSL certificate held herself that site. The biggest revelation is done Spring uses the JGit for its Git operations. -
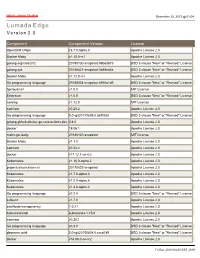
Lumada Edge Version
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

Statistics Survey 499767 'Alioth Replacement Survey'
Quick statistics Survey 499767 'Alioth Replacement Survey' Results Survey 499767 Number of records in this query: 317 Total records in survey: 317 Percentage of total: 100.00% page 1 / 62 Quick statistics Survey 499767 'Alioth Replacement Survey' Field summary for Q00001 What is your relationship to the project? Answer Count Percentage Developer (SQ001) 193 61.27% Maintainer (SQ002) 99 31.43% Contributor (SQ003) 125 39.68% User (SQ004) 206 65.40% Package Maintainer (SQ005) 169 53.65% Other 12 3.81% ID Response 2 translator 10 upstream 88 Upstream 102 sysadmin 157 DSA 248 former alioth maintainer 366 Translator 434 Infrastructure Maintainer 443 Ex-developer 480 bug reporter/triager 483 consultant to commercial users 494 Delegate page 2 / 62 Quick statistics Survey 499767 'Alioth Replacement Survey' Field summary for Q00001 What is your relationship to the project? page 3 / 62 Quick statistics Survey 499767 'Alioth Replacement Survey' Field summary for Q00002(SQ001) Which services are you using from alioth. Please rate each service from 1 (never used it) to 5 (very important for my work). [Issue Tracker] Answer Count Percentage Sum 1 (1) 232 79.73% 86.60% 2 (2) 20 6.87% 3 (3) 11 3.78% 3.78% 4 (4) 13 4.47% 5 (5) 13 4.47% 8.93% No answer 26 8.20% Arithmetic mean 0 Standard deviation 0 Sum (Answers) 289 100.00% 100.00% Number of cases 0% page 4 / 62 Quick statistics Survey 499767 'Alioth Replacement Survey' Field summary for Q00002(SQ001) Which services are you using from alioth. Please rate each service from 1 (never used it) to 5 (very important for my work). -

BP Ruzicka.Pdf
ZÁPADOČESKÁ UNIVERZITA V PLZNI FAKULTA ELEKTROTECHNICKÁ KATEDRA ELEKTRONIKY A INFORMAČNÍCH TECHNOLOGIÍ BAKALÁŘSKÁ PRÁCE Metodika správy otevřené knihovny součástek Ondřej Růžička 2021 Abstrakt Otevřené nástroje pro návrh schémat a plošných spojů jsou velmi rozšířené a nabízejí mnoho možných přístupů k jejich používání. To může vést k nekonzistenci v použití uvnitř organizací. V této práci se zaměřuji na návrh metodiky pro správu knihoven, ze které vychází jednotný přístup k jejich tvorbě a udržování. Práce popisuje standardní přís- tupy pro správu knihoven. Je navržena metodika správy knihovny zaměřena na otevřený návrhový nástroj KiCAD, pro verzování a správu knihovny využívající systém správy revizí Git a platforma GitHub. Základem ověření je využití skriptů a nezávislého manuál- ního posouzení. Každá součástka obsahuje soubory s metadaty, která charakterizují mimo jiné stav součástky a její odpovídající úroveň ověření. Klíčová slova otevřená knihovna, knihovna součástek, KiCAD, správa knihovny, git, systémy správy revizí, verifikace, validace i Abstract Open-source PCB design tools are very popular nowadays and they may be employed in diverse workflows. This can lead to inconsistency and insufficient specification of use inside organizations. This thesis is focused on a library management methodology, which leads to a proposal, defining a unified approach to library design and management. This thesis describes standardized approaches to library management. This thesis defines the component design, verification, and validation process, according to the proposed method- ology. I used KiCAD as the main software for library design, and git for versioning, and GitHub platform for project management. Automated tools and independent manual reviews are used for the verification process. Every component contains metadata files, which characterize, among other things, the component’s status and its corresponding verification level. -

Kallithea Deployment Release 0.0
Kallithea Deployment Release 0.0 Wolfgang Scherer Jan 10, 2020 Quickstart Local: • Deployment documentation: Kallithea deployment documentation • Deployment repository: Kallithea deployment repository • Installed instance: Kallithea installed instance Official: • Web-Site: Kallithea • Documentation: Kallithea Documentation • Repository: https://kallithea-scm.org/repos/kallithea • Bitbucket: conservancy / kallithea - Bitbucket (as long as it still works) Abstract CONTENTS List of Figures ii List of Tables iii List of Code Blocks iv 1 Installation 1 1.1 Get deployment package.......................................1 1.2 System packages...........................................1 1.3 Installation / update.........................................1 1.4 Initial setup..............................................2 1.5 Initialize repository defaults.....................................2 1.6 Setup repos/incoming........................................3 1.7 Create clone script..........................................3 1.8 Full text search............................................3 1.9 Install a language file for en .....................................3 2 Update 5 2.1 Database update...........................................5 3 Serve with gearbox 6 4 npm on Debian 7 5 Apache configuration 8 6 Kallithea deployment 10 6.1 Repositories............................................. 10 6.2 Documentation............................................ 10 7 LDAP 11 8 Bug: Logging re-initialized in make_app() 12 8.1 Paste Deploy WSGI app configuration...............................