A User-Interactive Browser Extension to Prevent the Exploitation of Preferences
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cross-Platform Analysis of Indirect File Leaks in Android and Ios Applications
Cross-Platform Analysis of Indirect File Leaks in Android and iOS Applications Daoyuan Wu and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University fcsdwu, [email protected] This paper was published in IEEE Mobile Security Technologies 2015 [47] with the original title of “Indirect File Leaks in Mobile Applications”. Victim App Abstract—Today, much of our sensitive information is stored inside mobile applications (apps), such as the browsing histories and chatting logs. To safeguard these privacy files, modern mobile Other systems, notably Android and iOS, use sandboxes to isolate apps’ components file zones from one another. However, we show in this paper that these private files can still be leaked by indirectly exploiting components that are trusted by the victim apps. In particular, Adversary Deputy Trusted we devise new indirect file leak (IFL) attacks that exploit browser (a) (d) parties interfaces, command interpreters, and embedded app servers to leak data from very popular apps, such as Evernote and QQ. Unlike the previous attacks, we demonstrate that these IFLs can Private files affect both Android and iOS. Moreover, our IFL methods allow (s) an adversary to launch the attacks remotely, without implanting malicious apps in victim’s smartphones. We finally compare the impacts of four different types of IFL attacks on Android and Fig. 1. A high-level IFL model. iOS, and propose several mitigation methods. four IFL attacks affect both Android and iOS. We summarize these attacks below. I. INTRODUCTION • sopIFL attacks bypass the same-origin policy (SOP), Mobile applications (apps) are gaining significant popularity which is enforced to protect resources originating from in today’s mobile cloud computing era [3], [4]. -

1 Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administra
Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Kyle Andeer, Vice President, Corporate Law, Apple, Inc. 1. Does Apple permit iPhone users to uninstall Safari? If yes, please describe the steps a user would need to take in order to do so. If no, please explain why not. Users cannot uninstall Safari, which is an essential part of iPhone functionality; however, users have many alternative third-party browsers they can download from the App Store. Users expect that their Apple devices will provide a great experience out of the box, so our products include certain functionality like a browser, email, phone and a music player as a baseline. Most pre-installed apps can be deleted by the user. A small number, including Safari, are “operating system apps”—integrated into the core operating system—that are part of the combined experience of iOS and iPhone. Removing or replacing any of these operating system apps would destroy or severely degrade the functionality of the device. The App Store provides Apple’s users with access to third party apps, including web browsers. Browsers such as Chrome, Firefox, Microsoft Edge and others are available for users to download. 2. Does Apple permit iPhone users to set a browser other than Safari as the default browser? If yes, please describe the steps a user would need to take in order to do so. If no, please explain why not. iPhone users cannot set another browser as the default browser. -

Website Nash County, NC
Website Nash County, NC Date range: Week 13 October - 19 October 2014 Test Report Visits Summary Value Name Value Unique visitors 5857 Visits 7054 Actions 21397 Maximum actions in one visit 215 Bounce Rate 46% Actions per Visit 3 Avg. Visit Duration (in seconds) 00:03:33 Website Nash County, NC | Date range: Week 13 October - 19 October 2014 | Page 2 of 9 Visitor Browser Avg. Time on Browser Visits Actions Actions per Visit Avg. Time on Bounce Rate Conversion Website Website Rate Internet Explorer 2689 8164 3.04 00:04:42 46% 0% Chrome 1399 4237 3.03 00:02:31 39.24% 0% Firefox 736 1784 2.42 00:02:37 50% 0% Unknown 357 1064 2.98 00:08:03 63.87% 0% Mobile Safari 654 1800 2.75 00:01:59 53.36% 0% Android Browser 330 1300 3.94 00:02:59 41.21% 0% Chrome Mobile 528 2088 3.95 00:02:04 39.02% 0% Mobile Safari 134 416 3.1 00:01:39 52.24% 0% Safari 132 337 2.55 00:02:10 49.24% 0% Chrome Frame 40 88 2.2 00:03:36 52.5% 0% Chrome Mobile iOS 20 46 2.3 00:01:54 60% 0% IE Mobile 8 22 2.75 00:00:45 37.5% 0% Opera 8 13 1.63 00:00:26 62.5% 0% Pale Moon 4 7 1.75 00:00:20 75% 0% BlackBerry 3 8 2.67 00:01:30 33.33% 0% Yandex Browser 2 2 1 00:00:00 100% 0% Chromium 1 3 3 00:00:35 0% 0% Mobile Silk 1 8 8 00:04:51 0% 0% Maxthon 1 1 1 00:00:00 100% 0% Obigo Q03C 1 1 1 00:00:00 100% 0% Opera Mini 2 2 1 00:00:00 100% 0% Puffin 1 1 1 00:00:00 100% 0% Sogou Explorer 1 1 1 00:00:00 100% 0% Others 0 0 0 00:00:00 0% 0% Website Nash County, NC | Date range: Week 13 October - 19 October 2014 | Page 3 of 9 Mobile vs Desktop Avg. -

XCSSET Update: Abuse of Browser Debug Modes, Findings from the C2 Server, and an Inactive Ransomware Module Appendix
XCSSET Update: Abuse of Browser Debug Modes, Findings from the C2 Server, and an Inactive Ransomware Module Appendix Introduction In our first blog post and technical brief for XCSSET, we discussed the depths of its dangers for Xcode developers and the way it cleverly took advantage of two macOS vulnerabilities to maximize what it can take from an infected machine. This update covers the third exploit found that takes advantage of other popular browsers on macOS to implant UXSS injection. It also details what we’ve discovered from investigating the command-and-control server’s source directory — notably, a ransomware feature that has yet to be deployed. Recap: Malware Capability List Aside from its initial entry behavior (which has been discussed previously), here is a summarized list of capabilities based on the source files found in the server: • Repackages payload modules to masquerade as well-known mac apps • Infects local Xcode and CocoaPods projects and injects malware to execute when infected project builds • Uses two zero-day exploits and trojanizes the Safari app to exfiltrate data • Uses a Data Vault zero-day vulnerability to dump and steal Safari cookie data • Abuses the Safari development version (SafariWebkitForDevelopment) to inject UXSS backdoor JS payload • Injects malicious JS payload code to popular browsers via UXSS • Exploits the browser debugging mode for affected Chrome-based and similar browsers • Collects QQ, WeChat, Telegram, and Skype user data in the infected machine (also forces the user to allow Skype and -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Clearing Commonly Used Browser's Internet Cache Desktops
Clearing Commonly Used Browser’s Internet Cache Clearing Commonly Used Browser’s Internet Cache For information on how to clear the cache of commonly used internet browsers, please see below. NOTE: If your browser is not listed, please refer to the documentation that came with your device or the browser software on how to clear its cache. REMINDER: To protect your privacy and prevent unauthorized use of your System ID, 1) sign out of the Self-Service application, 2) clear the browser’s cache, and 3) close all web browser windows. Desktops Internet Explorer 7 1. From the Tools menu, select Internet Options. 2. Under "Browsing history", click Delete. 3. To delete your cache, click Delete files. 4. Click Close, and then click OK to exit. 5. After the cache is cleared, click the X to close the browser window and confirm ALL browser windows are closed. Internet Explorer 9, 10, and 11 1. Select Tools (via the Gear icon) 2. Select Safety 3. Select Delete Browsing History… NOTE: You can also access this menu by holding Ctrl + Shift + Delete 4. Make sure to uncheck Preserve Favorites websites data and check both Temporary Internet Files and Cookies then click Delete. Microsoft Edge 1. Click the Hub icon. 2. Click the History icon. 3. Click the link labeled Clear all History. 4. Check the boxes for each item you want to clear. 5. Click the Clear button. The message “All Clear!” will appear. Android To clear cache: 1. Start your browser. 2. Tap Menu, and then tap More. 3. Select Settings. -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.4 | November 2016 UFED LOGICAL ANALYZER, UFED READER
NOW SUPPORTING 20,854 DEVICE PROFILES +2,851 APP VERSIONS UFED TOUCH2, UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.4 | November 2016 UFED LOGICAL ANALYZER, UFED READER HIGHLIGHTS WE’VE ADDED SUPPORT TO MORE MOTOROLA ANDROID DEVICES! DEVICE SUPPORT Physical extraction and decoding from 26 popular Motorola Android devices ◼ Bootloader-based physical extraction for 17 MTK Android (up to and including OS 5.0.1). devices running the following MediaTek chipsets: MT6735 and MT6753. ◼ Physical extraction and decoding from 26 popular A BRAND NEW USER INTERFACE Motorola Android devices. Due to popular demand, we ◼ Following the previous announcement in version 5.1, are excited to introduce the we have added physical extraction while bypassing new interface for UFED Physical user lock for 18 additional Huawei devices, running Analyzer, UFED Logical Analyzer and UFED Reader 5.4. HiSilicon chipsets. We have redesigned the user interface to deliver a more ◼ Logical extraction and decoding is enabled for the new intuitive user experience. Google Pixel Android devices (Apps data not included). APPS SUPPORT ◼ 26 new Applications supported for iOS and PINPOINT YOUR SUBJECTS’ Android devices. LOCATIONS WITH MORE ACCURACY! ◼ Facebook Messenger: Decoding supported for multiple users of a single device. ◼ 569 updated application versions. FUNCTIONALITY ◼ Pinpoint your subjects’ locations with more accuracy. ◼ Organize and review case evidence with enhanced To fully utilize the large volume of locations data available in a searching, filtering and grouping capabilities. mobile device, UFED Physical Analyzer 5.4 allows you to convert ◼ Analyze more data in Timeline view quicker. the BSSID values (wireless networks) and cell towers into location ◼ Identify critical case information up to 50% faster. -

Taskstream Technical & System Faqs
Taskstream Technical & System FAQs 71 WEST 23RD STREET, NEW YORK, NY 10010 · T 1.800.311.5656 · e [email protected] Taskstream FAQs Taskstream FAQs Click the links in each question or description to navigate to the answer: System Requirements FAQs . What Internet browsers can I use to access Taskstream? . Can I use Taskstream on a Mac or a PC? on a desktop or laptop computer? . Does Taskstream work on iPad, iPhone or Android-based devices? . Do I need additional plugins or add-ons to use Taskstream? . Can I access Taskstream offline? . Does Taskstream require JavaScript to be enabled? . Does Taskstream require cookies to be enabled? . Does Taskstream use pop-ups? . How can I import and export data within Taskstream? Technical FAQs . Can I have Taskstream open in more than one window at a time? . Is Taskstream's site accessible to users with disabilities? . What is a Comma Separated Value (CSV) file? . How do I print my work? . How do I format my text? . How do I add special characters, such as math symbols or special punctuation, to my text? . What is WebMarker File Markup? . What is Turnitin® Originality Reporting? . Can I change the size of the Taskstream text/fonts? Troubleshooting . When I click on a button nothing occurs. Some of the features within the Taskstream site are missing. When I try to download/view a file attachment, nothing happens. I am not receiving emails from Taskstream. I uploaded a file on my Mac, but the attached file does not open. My file is too large to upload. Taskstream is reporting that I have entered unsafe text. -
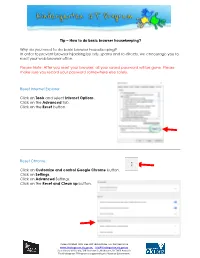
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal