Automated Network Security with Exceptions Using Sdn
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

Set up Mail Server Documentation 1.0
Set Up Mail Server Documentation 1.0 Nosy 2014 01 23 Contents 1 1 1.1......................................................1 1.2......................................................2 2 11 3 13 3.1...................................................... 13 3.2...................................................... 13 3.3...................................................... 13 4 15 5 17 5.1...................................................... 17 5.2...................................................... 17 5.3...................................................... 17 5.4...................................................... 18 6 19 6.1...................................................... 19 6.2...................................................... 28 6.3...................................................... 32 6.4 Webmail................................................. 36 6.5...................................................... 37 6.6...................................................... 38 7 39 7.1...................................................... 39 7.2 SQL.................................................... 41 8 43 8.1...................................................... 43 8.2 strategy.................................................. 43 8.3...................................................... 44 8.4...................................................... 45 8.5...................................................... 45 8.6 Telnet................................................... 46 8.7 Can postfix receive?.......................................... -

Leveraging Data from Open-Source Intrusion Detection Systems for Enhancing Security of Systems
Leveraging Data from Open-Source Intrusion Detection Systems for Enhancing Security of Systems Viren Chhabria A Dissertation Presented to the University of Dublin, Trinity College in partial fulfilment of the requirements for the degree of Master of Science in Computer Science (Data Science) Supervisor: Dr. Stephen Farrell August 2019 Declaration I, the undersigned, declare that this work has not previously been submitted as an exercise for a degree at this, or any other University, and that unless otherwise stated, is my own work. Viren Chhabria August 14, 2019 Permission to Lend and/or Copy I, the undersigned, agree that Trinity College Library may lend or copy this thesis upon request. Viren Chhabria August 14, 2019 To my mother, Bhavna R Chhabria and father, Rajkumar T Chhabria, for their endless love and support! Acknowledgments I would like to express my sincere gratitude to my supervisor Dr. Stephen Farrell for his constant support and supervision. His knowledge and experience helped me over- come challenging situations during the course of this dissertation. A big thank you to my parents and family for enabling me to pursue my MSc program at Trinity College Dublin and supporting me throughout this wonderful journey. I would like to thank Prof. Khurshid Ahmad, for mentoring, motivating and support- ing me. Last, but not the least, I would like to thank my friends. Ankita for motivating me throughout the project. Arun and Debrup for providing me innovative ideas and technical guidance. Rohit, for helping me with machine learning during the project. Dr. Husanbir Singh Pannu for motivating me and providing tips for efficient writing. -
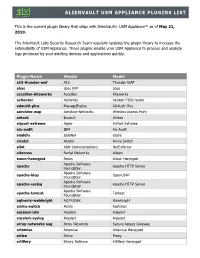
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

Nextcloud Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 10, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 35 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 5 Nextcloud configuration 49 5.1 Warnings on admin page......................................... 49 5.2 Using the occ command........................................ -

Web Hosting Use Ispconfig
CHAPTER 5 IMPLEMENTATION AND TESTING 5.1 Implementation Linux Installation 1. According to illustration 5.1 the first step is select the language to install linux. And then create a partition for the linux operating system that will be installed. The partition that will be used in the installation of linux is the swap partition and partition/. 2. According to illustration 5.2 The next step is select the location to determine the timezone in linux. And then select the keyboard layout is used. 3. According to illustration 5.3 the next step is to create a username and password to login to a linux operating system that has been installed. After that the linux installation process will start. 4. According to illustration 5.4 After the installation process is complete restart the computer that has been installed linux. After that login with username and passsword that have been created. 10 11 Illustration 5.1 Display To Select The Language To Install Linux And Create Patition. Illustration 5.2 Display To Select Timezone And Keyboard Layout. 12 Illustration 5.3 Display To Create User And Password And Installation Process Illustration 5.4 Linux Installation Is Complete. ISP Config Installation 1. Open the terminal and sign in as user root. sudo su 2. The next step was to reconfigure the dpkg and select no to use the dash as the default system shell in the bin/sh directory. 13 Illustration 5.5 Reconfigure Dpkg. 3. Disable apparmor. service apparmor stop update-rc.d -f apparmor remove And Remove Apparmor apt-get remove apparmor apparmor-utils Apparmor is a linux security system that can interfere with the installation in the isp config. -

Cisco Telepresence Conductor XC2.2 Open Source Documentation
Open Source Used In Cisco TelePresence Conductor XC2.2 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-37690785 Open Source Used In Cisco TelePresence Conductor XC2.2 1 This document contains the licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of the source code to which you are entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-37690785 Contents 1.1 acpid 1.0.10 :2.1.el6 1.1.1 Available under license 1.2 apache 2.4.2 1.2.1 Available under license 1.3 apr 1.4.6 1.3.1 Available under license 1.4 apr-util 1.4.1 1.4.1 Available under license 1.5 bash 4.2 1.5.1 Available under license 1.6 bind 9.7.1 1.6.1 Available under license 1.7 binutils 2.23.1 1.7.1 Available under license 1.8 boost 1.49.0 1.8.1 Notifications 1.8.2 Available under license 1.9 bzip2 1.0.6 1.9.1 Available under license 1.10 c-ares 1.7.4 1.10.1 Available under license 1.11 checkpolicy 2.1.11 1.11.1 Available under license 1.12 coreutils 8.15 1.12.1 Available under license 1.13 coverage 3.4 Open Source Used In Cisco TelePresence Conductor XC2.2 2 1.13.1 Available under license 1.14 cracklib -

Fail2ban "…FAILURE IS DELAY, NOT DEFEAT…" – DENIS WAITLEY Agenda
Fail2Ban "…FAILURE IS DELAY, NOT DEFEAT…" – DENIS WAITLEY Agenda What is fail2ban? My story And then there was DoS A look at fail2ban Summary Intrusion Detection vs Prevention What is fail2ban? Fail2Ban is an intrusion prevention software framework that protects computer servers from brute-force attacks. Fail2Ban scans log files and bans IP addresses of hosts that have too many failures within a specified time window. Think of it as a dynamic firewall. It detects incoming connection failures, and dynamically adds a firewall rule to block that host after too many failures. My Story On my Linux servers, I do not allow username/password authentication Users must use SSH with PKI But I still didn't like the barrage of remote login attempts My fear was an unknown zero-day, race condition, buffer overflow or other vulnerability was still a threat So I looked for intrusion detection and prevention software I found, installed, learned and started using fail2ban to block unwanted ssh connection attempts I was right. We fell victim to a previously unknown Denial of Service vulnerability Under Attack In May of 2016, we suffered a SLOW denial of service attack Something was causing our web site to hang every 5-15 minutes Restarting Apache would fix the problem, but the site would just hang again in 5-15 minutes We did not have an unusually high volume of HTTP GET/POSTs We had what seemed like an unusually high amount of Baidu spider traffic Baidu Spider Baidu ignores your robot.txt file, and they do whatever the h*ll they want Baidu -

Supported Software
The following table identifies the log types that the Binary Defense SIEM supports out of the box. SUPPORTED SOFTWARE Vendor Supported Software A10 Thunder WAF Abas ERP Abas Accellion Kiteworks Actiontec Verizon FIOS router Adtran NetVanta Aerohive Networks Wireless Access Point Alcatel Arista Switch AlienVault Agent | Availability-Monitoring | HIDS | Monit | Monitor |Netflow Alerts | NIDS | Nmap Hosts | Nmap Monitor | OCS Monitor | Ping Monitor | Post-Correlation | TCPTrack Monitor | USBdev | User Activity | Whois Monitor | WMI Application Logger | WMI Monitor | WMI Security Logger | WMI System Logger Allot Communications NetEnforcer Amun Amun Honeypot Anti-Spam SMTP Proxy Anti-Spam SMTP Proxy Apache Software Foundation Apache HTTP Server | OpenLDAP | SpamAssassin | Tomcat | Apple AirPort Extreme | OS-X AQTRONiX WebKnight Arbor Networks Pravail APS Arista Switches Arpalert Arpalert Array Networks Secure Access Gateway Artemisa Artemisa Honeypot Artica Proxy Aruba Networks Airwave | ClearPass | Mobility Access Switches | Wireless Asterisk VoIP AsusTek Wireless Router Automatic Software Solutions HoneyBOT Automation Access Tarantella Avast Free Antivirus Avaya Media Gateway | VSP switches | Wireless LAN Barracuda Link Balancer | Next Gen Firewall | Spam Firewall | SSL VPN | Web Application Firewall | Web Filter Binary Defense Artillery Honeypot Bitdefender GravityZone Blackboard Learn Blue Coat PacketShaper | ProxySG Bomgar Remote Support and Privileged Access Bro Bro NSM Broadweb IPS-Netkeeper | Netkeeper NIDS Brocade Brocade Devices -

Fail2ban Jail Base Specification File # # HOW to ACTIVATE JAILS: # # YOU SHOULD NOT MODIFY THIS FILE
# Fail2Ban jail base specification file # # HOW TO ACTIVATE JAILS: # # YOU SHOULD NOT MODIFY THIS FILE. # # It will probably be overwitten or improved in a distribution update. # # Provide customizations in a jail.local file or a jail.d/customisation.local. # For example to change the default bantime for all jails and to enable the # ssh-iptables jail the following (uncommented) would appear in the .local file. # See man 5 jail.conf for details. # # [DEFAULT] # bantime = 3600 # # [ssh-iptables] # enabled = true # Comments: use '#' for comment lines and ';' (following a space) for inline com ments # The DEFAULT allows a global definition of the options. They can be overridden # in each jail afterwards. [DEFAULT] # "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not # ban a host which matches an address in this list. Several addresses can be # defined using space separator. ignoreip = 127.0.0.1/8 # External command that will take an tagged arguments to ignore, e.g. <ip>, # and return true if the IP is to be ignored. False otherwise. # # ignorecommand = /path/to/command <ip> ignorecommand = # "bantime" is the number of seconds that a host is banned. bantime = 1200 # A host is banned if it has generated "maxretry" during the last "findtime" # seconds. findtime = 1200 # "maxretry" is the number of failures before a host get banned. maxretry = 10 # "backend" specifies the backend used to get files modification. # Available options are "pyinotify", "gamin", "polling" and "auto". # This option can be overridden in each jail as well. # # pyinotify: requires pyinotify (a file alteration monitor) to be installed. -
Linux: Configuring and Securing Your Server Howto Guide
Linux: Configuring and securing your server howto guide A technical howto document presented to H3ABioNet Created by The System Administrator Task-force Prepared for The greater H3ABioNet and H3Africa Consortium community Document Control Date Author Authorization By Version Description 27 June 2014 Suresh System Administrator 1.0 First draft Maslamoney Task-force Contributors Last Name First Name Institution Country Alibi Mohamed Pasteur Institute of Tunis (IPT) Tunisia Brown David Rhodes University (RU) South Africa Indome David Noguchi Memorial Institute for Medical Research Ghana (NMIMR) Scheepers Inus Centre for High Performance Computing (CHPC) South Africa Maslamoney Suresh Computational Biology Group – UCT (CBIO) South Africa Panji Sumir Computational Biology Group – UCT (CBIO) South Africa Van Heusden Peter South African National Bioinformatics (SANBI) South Africa Marcello Lucio (CIDRES) Burkina Faso Reviewers Last Name First Name Institution Country HowTo: Linux Server Management and Configuration Guide Page 2 of 33 Acronyms and Abbreviations Acronym and Abbreviations Description CLI The Command Line Interface refers to the actual local terminal on the Linux server used to navigate, configure and manage the system NIC A Network Interface Card is a physical network card installed the physical server OS A Operating System is a piece of software which is installed on a computer system and manages communication between the physical hardware and user based applications SL Scientific Linux Operating System HowTo: Linux Server Management -

Detecting Distributed Brute Force Attack on a Single Target
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 738 ISSN 2229-5518 DBFST: Detecting Distributed Brute Force Attack on a Single Target AL-Zwuiany Muhanad M. K., Prof. Huang Dongjun Abstract— While reading this paper, a lot of servers may be coming under attack by hackers at different sites of the Internet. The actions of these hackers have different motivations and purposes and brute force attack is one of common ways of attack deployed by hackers. Secure Shell (SSH) is one of the widespread attacked servers. SSH tunnels are commonly used to provide two types of privacy protection. First one is protecting the privacy of the data being exchanged between two peers, such as passwords and so on. The second one is protect the privacy of the behavior of end-users, by preventing an unauthorized observer from detecting which application protocol is being transported by the SSH tunnel. Wherefore it has become the default remote access method for those using UNIX systems. It is very common for public Internet servers to experience attacks that attempt use brute force to obtain usernames and passwords combinations via SSH. In this paper we shall examine these attacks depending on SSH log file to find unsuccessful logins and then establish if these unsuccessful authorized IP’s belong to attackers or to trusted users. Then develop a strategy to determine who should transact with the IP addresses based on the IP kind, and prevent the attackers IP's from attempting to login to the system. Index Terms— Brute force, SSH, Iptables, Fail2ban, Denyhosts and white list.