Leveraging Data from Open-Source Intrusion Detection Systems for Enhancing Security of Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Science DMZ
The Science DMZ Brian Tierney, Eli Dart, Eric Pouyoul, Jason Zurawski ESnet Supporting Data-Intensive Research Workshop QuestNet 2013 Gold Coast, Australia July 2, 2013 What’s there to worry about? © Owen Humphreys/National Geographic Traveler Photo Contest 2013 7/2/13 2 Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science The Science DMZ in 1 Slide Consists of three key components, all required: “Friction free” network path • Highly capable network devices (wire-speed, deep queues) • Virtual circuit connectivity option • Security policy and enforcement specific to science workflows • Located at or near site perimeter if possible Dedicated, high-performance Data Transfer Nodes (DTNs) • Hardware, operating system, libraries all optimized for transfer • Includes optimized data transfer tools such as Globus Online and GridFTP Performance measurement/test node • perfSONAR Details at http://fasterdata.es.net/science-dmz/ Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science Overview Part 1: • What is ESnet? • Science DMZ Motivation • Science DMZ Architecture Part 2: • PerfSONAR • The Data Transfer Node • Data Transfer Tools Part 3: • Science DMZ Security Best Practices • Conclusions Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science The Energy Sciences Network (ESnet) A Department of Energy Facility Naonal Fiber footprint Distributed Team of 35 Science Data Network Internaonal Collaboraons Mul3ple 10G waves 5 Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science ESnetSC Supports Supports Research DOE at More Office than 300 of Institutions Science Across the U.S. Universities DOE laboratories The Office of Science supports: 27,000 Ph.D.s, graduate students, undergraduates, engineers, and technicians 26,000 users of open-access facilities 300 leading academic institutions 17 DOE laboratories 6 Lawrence Berkeley National Laboratory U.S. -

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Set up Mail Server Documentation 1.0
Set Up Mail Server Documentation 1.0 Nosy 2014 01 23 Contents 1 1 1.1......................................................1 1.2......................................................2 2 11 3 13 3.1...................................................... 13 3.2...................................................... 13 3.3...................................................... 13 4 15 5 17 5.1...................................................... 17 5.2...................................................... 17 5.3...................................................... 17 5.4...................................................... 18 6 19 6.1...................................................... 19 6.2...................................................... 28 6.3...................................................... 32 6.4 Webmail................................................. 36 6.5...................................................... 37 6.6...................................................... 38 7 39 7.1...................................................... 39 7.2 SQL.................................................... 41 8 43 8.1...................................................... 43 8.2 strategy.................................................. 43 8.3...................................................... 44 8.4...................................................... 45 8.5...................................................... 45 8.6 Telnet................................................... 46 8.7 Can postfix receive?.......................................... -

การติดตั้ง Webserver โดยใช้ Freebsd
การติดต้งั WebServer โดยใช ้ FreeBSD 8.2 Rev001: Apr 1,2011 § การตดติ งั้ WebServer โดยใช ้ FreeBSD 8.2 § กรณีศกษาึ www.mu-ph.org โดย เสรมพิ นธั ุ ์ นตยิ นรา์ Email: [email protected] 1 เมษายน 2554 [** Rev01 : Apr 01,2011 **] * * * * * * * * * Objective: ต้องการทาํ WebServer ของ องค์กร ให้ทุกฝ่ ายในองค์กรม ี WebSite ใช้งาน โดยให้เนือท้ ฝี่ ่ ายละ 1 GBytes Specifications ของเครื่องที่ใช้ www# dmesg Copyright (c) 1992-2011 The FreeBSD Project. Copyright (c) 1979, 1980, 1983, 1986, 1988, 1989, 1991, 1992, 1993, 1994 The Regents of the University of California. All rights reserved. FreeBSD is a registered trademark of The FreeBSD Foundation. FreeBSD 8.2-RELEASE #0: Fri Feb 18 02:24:46 UTC 2011 [email protected]:/usr/obj/usr/src/sys/GENERIC i386 Timecounter "i8254" frequency 1193182 Hz quality 0 CPU: Intel(R) Xeon(TM) CPU 2.40GHz (2392.06-MHz 686-class CPU) Origin = "GenuineIntel" Id = 0xf29 Family = f Model = 2 Stepping = 9 Features=0xbfebfbff<FPU,VME,DE,PSE,TSC,MSR,PAE,MCE,CX8,APIC,SEP,MTRR,PGE,MCA,CMOV,PAT,PSE36,CLFLUSH,DTS,ACPI, MMX,FXSR,SSE,SSE2,SS,HTT,TM,PBE> Features2=0x4400<CNXT-ID,xTPR> real memory = 1073741824 (1024 MB) avail memory = 1036226560 (988 MB) ACPI APIC Table: <DELL PE1600SC> FreeBSD/SMP: Multiprocessor System Detected: 4 CPUs FreeBSD/SMP: 4 package(s) x 1 core(s) cpu0 (BSP): APIC ID: 0 cpu1 (AP): APIC ID: 1 cpu2 (AP): APIC ID: 6 cpu3 (AP): APIC ID: 7 แบ่ง partition ดังนี ้ www# df Filesystem 1K-blocks Used Avail Capacity Mounted on /dev/amrd0s1a 1012974 176512 755426 19% / devfs 1 1 0 100% /dev /dev/amrd0s1h 63488502 4 58409418 0% /backups /dev/amrd0s1g 1012974 12 931926 0% /tmp /dev/amrd0s1e 5077038 832996 3837880 18% /usr /dev/amrd0s1f 50777034 4 46714868 0% /usr/local/www /dev/amrd0s1d 15231278 278 14012498 0% /var www# โปรแกรมทลงี่ 1. -

Webserver-Freebsd-7-2.Pdf
µ¦·´Ê WebServer Ã¥Äo FreeBSD 7.2 § дѥішѧчшѤѸк WebServer ѱчѕѲнҖ FreeBSD 7.2 § діцѨћѩдќѥ www.mu-ph.org ѱчѕ ѯѝіѧєёѤьыѫҙ ьѧшѕҙьіѥ Email: [email protected] 12 ѝѧкўѥзє 2552 * * * * * * * * * Objective: шҖѠкдѥіъѼѥ WebServer еѠк Ѡкзҙді ѲўҖъдѐѫ ҐѥѕѲьѠкзҙдієѨ WebSite ѲнҖкѥь ѱчѕѲўҖ ѯьѪѸѠъзьјѣѨѷ 5 GBytes Specifications °Á¦ºÉ°¸ÉÄo CPU: Intel(R) Xeon(R) CPU E5405 @ 2.00GHz (1995.01-MHz 686-class CPU) Origin = "GenuineIntel" Id = 0x1067a Stepping = 10 Ram 2G HardDisk IDE 500G ¨³ 250 εª°o° o°Â¦ 500G ¦oµ / , swap ¨³ /backups o°¸É° 250G ¦oµ /var , /tmp , /usr ¨³ /usr/local Lan card 1 Ä (onboard) Ân partion ´¸Ê www# df Filesystem 1K-blocks Used Avail Capacity Mounted on /dev/ad5s1a 507630 146844 320176 31% / devfs 1 1 0 100% /dev /dev/ad7s1g 400913540 16644420 352196038 5% /backups /dev/ad7s1e 1012974 12 931926 0% /tmp /dev/ad7s1f 10154158 1150928 8190898 12% /usr /dev/ad5s1d 231978828 4 213420518 0% /usr/local /dev/ad7s1d 60931274 1066 56055708 0% /var www# ѱюіѰдієъѨѷјк 1. ÂoŠ¢j¤¸ÉεÁ} 2. Compile Kernel Á¡ºÉ°Ä®o¦°¦´ Firewall ¨³ Quota 3. Update ports tree 4. µ¦·´Ê Firewall 5. µ¦Îµ Quota 6. ·´Ê mysql50-server 7. ·´Ê Apache22 8. ·´Ê PHP5 9. ·´Ê PHP5-extensions 10. ·´Ê ZendOptimizer 11. ·´Ê webmin 12. ·´Ê phpmyadmin 13. ·´Ê vsftp 14. ·´Ê awstats 15. ·´Ê ntp 16. ·´Ê clamav 17. ·´Ê hostsentry 18. ·´Ê portsentry 19. ·´Ê lynx 20. ·´Ê phpbb3 21. ·´Ê denyhosts 22. µ¦ Backup Áª µ¦·´Ê WebServer Ã¥Äo FreeBSD 7.2 Ã¥ Á¦·¤¡´»r ¥· r¦µ Page 1 µ¦·´Ê WebServer Ã¥Äo FreeBSD 7.2 јѼѥчѤэъѨѷ 1). -
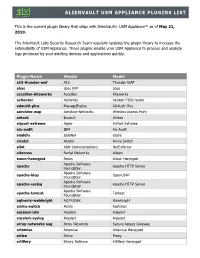
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

Reflection for Secure IT for UNIX
User's Guide Reflection for Secure IT for UNIX Version 8.0 SP2 Copyrights and Notices © 2016 Attachmate Corporation, a Micro Focus company. All rights reserved. No part of the documentation materials accompanying this Micro Focus software product may be reproduced, transmitted, transcribed, or translated into any language, in any form by any means, without the written permission of Micro Focus or its affiliates. The content of this document is protected under copyright law even if it is not distributed with software that includes an end user license agreement. The content of this document is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Micro Focus. Micro Focus assumes no responsibility or liability for any errors or inaccuracies that may appear in the informational content contained in this document. Micro Focus, the Micro Focus logo, FileXpress, and Reflection are registered trademarks of Micro Focus or its subsidiaries or affiliated companies in the United Kingdom, United States and other countries. All other trademarks, trade names, or company names referenced herein are used for identification only and are the property of their respective owners. 1Installation 7 Which Package do I Need? . 8 Replace an Earlier Version or other Existing Secure Shell Program . 9 Install and Uninstall on Linux . 10 Set up High Availability Red Hat Clusters . 11 Install and Uninstall on Oracle Solaris 10 . 12 Install and Uninstall on Oracle Solaris 11. 13 Install and Uninstall on HP-UX. 17 Install and Uninstall on IBM AIX . 17 Migrate Settings from Existing Configuration Files. -

Nextcloud Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 10, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 35 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 5 Nextcloud configuration 49 5.1 Warnings on admin page......................................... 49 5.2 Using the occ command........................................ -

Web Hosting Use Ispconfig
CHAPTER 5 IMPLEMENTATION AND TESTING 5.1 Implementation Linux Installation 1. According to illustration 5.1 the first step is select the language to install linux. And then create a partition for the linux operating system that will be installed. The partition that will be used in the installation of linux is the swap partition and partition/. 2. According to illustration 5.2 The next step is select the location to determine the timezone in linux. And then select the keyboard layout is used. 3. According to illustration 5.3 the next step is to create a username and password to login to a linux operating system that has been installed. After that the linux installation process will start. 4. According to illustration 5.4 After the installation process is complete restart the computer that has been installed linux. After that login with username and passsword that have been created. 10 11 Illustration 5.1 Display To Select The Language To Install Linux And Create Patition. Illustration 5.2 Display To Select Timezone And Keyboard Layout. 12 Illustration 5.3 Display To Create User And Password And Installation Process Illustration 5.4 Linux Installation Is Complete. ISP Config Installation 1. Open the terminal and sign in as user root. sudo su 2. The next step was to reconfigure the dpkg and select no to use the dash as the default system shell in the bin/sh directory. 13 Illustration 5.5 Reconfigure Dpkg. 3. Disable apparmor. service apparmor stop update-rc.d -f apparmor remove And Remove Apparmor apt-get remove apparmor apparmor-utils Apparmor is a linux security system that can interfere with the installation in the isp config. -

Cisco Telepresence Conductor XC2.2 Open Source Documentation
Open Source Used In Cisco TelePresence Conductor XC2.2 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-37690785 Open Source Used In Cisco TelePresence Conductor XC2.2 1 This document contains the licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of the source code to which you are entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-37690785 Contents 1.1 acpid 1.0.10 :2.1.el6 1.1.1 Available under license 1.2 apache 2.4.2 1.2.1 Available under license 1.3 apr 1.4.6 1.3.1 Available under license 1.4 apr-util 1.4.1 1.4.1 Available under license 1.5 bash 4.2 1.5.1 Available under license 1.6 bind 9.7.1 1.6.1 Available under license 1.7 binutils 2.23.1 1.7.1 Available under license 1.8 boost 1.49.0 1.8.1 Notifications 1.8.2 Available under license 1.9 bzip2 1.0.6 1.9.1 Available under license 1.10 c-ares 1.7.4 1.10.1 Available under license 1.11 checkpolicy 2.1.11 1.11.1 Available under license 1.12 coreutils 8.15 1.12.1 Available under license 1.13 coverage 3.4 Open Source Used In Cisco TelePresence Conductor XC2.2 2 1.13.1 Available under license 1.14 cracklib -

SANS Institute Linux Security Checklist
Interested in learning more about securing Linux? SANS Institute Security Consensus Operational Readiness Evaluation This checklist is from the SCORE Checklist Project. Reposting is not permited without express, written permission. Linux Security Checklist Copyright SANS Institute Author Retains Full Rights Linux Security Checklist Prepared by: Lori Homsher Contributor: Tim Evans Table of Contents I ntroduction ............................................................................................................... 1 C hecklist ................................................................................................................... 2 B oot and Rescue Disk ........................................................................................... 2 S ystem Patches .................................................................................................... 2 D isabling Unnecessary Services ........................................................................... 3 C heck for Security on Key Files ............................................................................ 3 D efault Password Policy ........................................................................................ 3 L imit root access using SUDO .............................................................................. 4 O nly allow root to access CRON ........................................................................... 4 W arning Banners ..................................................................................................