A Basic Linux Tutorial
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
RED HAT ENTERPRISE LINUX 5, 6, AND 7 SOFTWARE MANAGEMENT NETWORKING Common administrative commands TASK RHEL TASK RHEL yum install iptables and ip6tables 5 6 5 yum groupinstall /etc/sysconfig/ip*tables Install software iptables and ip6tables 1 Be aware of potential issues when using subscription-manager yum install 7 Configure firewall /etc/sysconfig/ip*tables 6 SYSTEM BASICS on Red Hat Enterprise Linux 5: https://access.redhat.com/ yum group install system-config-firewall solutions/129003. TASK RHEL yum info firewall-cmd 2 Subscription-manager is used for Satellite 6, Satellite 5.6 with 5 6 7 SAM and newer, and Red Hat’s CDN. yum groupinfo firewall-config /etc/sysconfig/rhn/systemid 5 3 RHN tools are deprecated on Red Hat Enterprise Linux 7. View software info /etc/hosts yum info 5 6 rhn_register should be used for Satellite server 5.6 and newer 7 /etc/resolv.conf /etc/sysconfig/rhn/systemid yum group info View subscription information 6 only. For details, see: Satellite 5.6 unable to register RHEL 7 Configure name subscription-manager identity client system due to rhn-setup package not included in Minimal resolution /etc/hosts installation (https://access.redhat.com/solutions/737373) Update software yum update 5 6 7 /etc/resolv.conf 7 subscription-manager identity 7 nmcli con mod rhn_register 5 Upgrade software yum upgrade 5 6 7 /etc/sysconfig/network 5 6 subscription-manager 1 Configure hostname hostnamectl rhn_register Configure software subscription-manager repos 5 6 7 /etc/hostname 7 rhnreg_ks 6 /etc/yum.repos.d/*.repo Configure -

Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR
Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR FORMATTING A DISKETTE Formatting is the preparation of diskettes for storage of information. There are several different versions of the format command that can be used. The version that you use depends upon the type of diskette and the type of disk drive in which the diskette is being formatted. In order for us to be able to read the Tuition Grant diskettes you send, the diskettes should be properly formatted. Below is a table that identifies the more commonly used diskette types and disk drive specifications. The correct version of the format command will appear in the row for your diskette type and drive type. The format command uses the parameter “d:” to indicate the disk drive designation. For example, your 5 ¼ drive may be the “A:” drive. Instead of typing “FORMAT D:”, replace the drive designation with “A:” and type “FORMAT A:”. To verify that the disks were formatted correctly, perform the CHKDSK command on the newly formatted diskette. The format for the CHKDSK command is “CHKDSK d:”. When the command returns the disk information, compare it to the information in the fourth column of the table that corresponds to your diskette type and disk drive.. If the “total disk space” numbers are the same, the diskette is formatted correctly. DISK TYPE DRIVE TYPE FORMAT COMMAND SPACE INFO. 5 ¼” DSDD DSDD FORMAT d: 362,496 bytes total disk space 5 ¼” DSDD HD FORMAT d: /T:40 /N:9 362,496 bytes total disk space 5 ¼” HD DSDD Cannot be formatted 5 ¼” HD HD FORMAT d: 1,213,952 bytes total disk space 3 ½” DSDD DSDD FORMAT d: 730,112 bytes total disk space 3 ½” DSDD HD FORMAT d: /T:80 /N:9 730,112 bytes total disk space 3 ½” HD DSDD Cannot be formatted 3 ½” HD HD FORMAT d: 1,457,664 bytes total disk space 3 ½” DSHD FORMAT d: 1,457,664 bytes total disk space. -

PGP Desktop for Mac OS X Quick Start Guide Version 10.0
PGP Desktop for Mac OS X Quick Start Guide Version 10.0 In addition, use PGP Desktop to: What is PGP Desktop? y Use part of your hard drive space as an encrypted virtual disk volume with its own drive letter. PGP Desktop provides comprehensive security for desktops Create protected Zip archives. and laptops, making it possible for enterprises, workgroups, y and individuals to protect sensitive information without y Completely destroy files and folders so that nothing can changing the existing IT infrastructure or disrupting work recover them. processes. This award winning, easy-to-use solution encrypts email, files, virtual volumes, and entire disks from a single New to PGP Desktop? desktop application. Use this step-by-step guide to get started. You will find that, The PGP Desktop family of applications have been combined with PGP Desktop, protecting your data will be as easy as into several bundles. turning a key in a lock. y PGP Desktop Professional includes PGP Desktop Email y This Quick Start Guide helps you install PGP Desktop and and PGP Whole Disk Encryption get started. y PGP Whole Disk Encryption includes PGP Whole Disk y The PGP Desktop User’s Guide provides more detailed Encryption information on PGP Desktop. In it, you will learn what a keypair is, why you might want to create one, how to create one, and how to exchange keys with others so you can encrypt your own data and share data securely with Contents others. y What is PGP Desktop? (page 1) Note: A PGP Desktop license provides you with access to y New to PGP Desktop? (page 1) a certain set of PGP Desktop features. -

F.A.Q. Series ROM-DOS TM
21520 30th Drive SE #110 Bothell, WA 98021 USA Tel: (425) 951-8086 Fax: (425) 951-8095 [email protected] [email protected] www.datalight.com TM ROM-DOS F.A.Q. Series Question: Assuming they don't want FAT32, Long Filename support, or Sockets, why should my customer upgrade to the newest ROM-DOS? Answer: Since our first FAT32 and LFN release 4.00.1091, there have been several improvements to the core ROM- DOS kernel. This core code is used primarily for our DOS 6.22 compatible compilations, and then extended in the case of a FAT32 or Long Filename build. The 4.00.1091 release is also a new code base and there will be no further upgrades to the previous DOS 6.22 code. In order to obtain new features, fixes, and support a customer must upgrade to release 4.00.1091 or greater. Along with the performance enhancements for both size and speed, several corrections have been made to the ROM-DOS kernel. These include stack and memory issues, disk access issues, and compatibility with the former market leader in DOS. Most of the ROM-DOS utilities have also been improved for size and speed, along with bug fixes. The major changes happened with the XCOPY, HIMEM, MSCDEX, CHKDSK, FDISK and FORMAT utilities. In the realm of international support, the Euro was added to the keyboard and display driver code. ROM- DOS and PC-DOS 2000 are the only non-GUI operating systems to support the Euro. Finally, new ROM-DOS utilities have been added. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -

The Ask Leo! ® Guide to Routine Maintenance 2 Contents the Ask Leo! Manifesto
The Ask Leo! Guide to Routine Maintenance Simple steps to make your computer last longer and run faster. By Leo A. Notenboom An Ask Leo! ebook ISBN: 978-1-937018-10-8 (pdf) Copyright © 2013 The Ask Leo! ® Guide to Routine Maintenance 2 http://askleo.com Contents The Ask Leo! Manifesto ......................................................................................................................................... 7 Be sure to register your book! ................................................................................................................................. 8 Introduction – 12 months or 12,000 miles .............................................................................................................. 9 Back Up ................................................................................................................................................................ 10 Creating a System Repair Disk ............................................................................................................................. 11 Creating a Windows 7 System Repair disc ....................................................................................................... 11 A System Repair disc might not be all you think ............................................................................................. 12 A System Repair disc is not a System Installation disc .................................................................................... 13 A System Installation disc IS a System Repair disc -
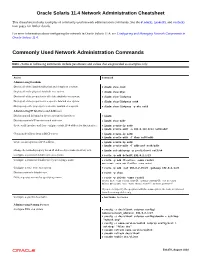
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

Carbon Copy Cloner Documentation: English
Carbon Copy Cloner Documentation: English Getting started with CCC System Requirements, Installing, Updating, and Uninstalling CCC CCC License, Registration, and Trial FAQs Trouble Applying Your Registration Information? Establishing an initial backup Preparing your backup disk for a backup of Mac OS X Restoring data from your backup What's new in CCC Features of CCC specific to Lion and greater Release History Carbon Copy Cloner's Transition to a Commercial Product: Frequently Asked Questions Credits Example backup scenarios I want to clone my entire hard drive to a new hard drive or a new machine I want to backup my important data to another Macintosh on my network I want to backup multiple machines or hard drives to the same hard drive I want my backup task to run automatically on a scheduled basis Backing up to/from network volumes and other non-HFS volumes I want to back up my whole Mac to a Time Capsule or other network volume I want to defragment my hard drive Backup and archiving settings Excluding files and folders from a backup task Protecting data that is already on your destination volume Managing previous versions of your files Automated maintenance of CCC archives Advanced Settings Some files and folders are automatically excluded from a backup task The Block-Level Copy Scheduling Backup Tasks Scheduling a task and basic settings Performing actions Before and After the backup task Deferring and skipping scheduled tasks Frequently asked questions about scheduled tasks Email and Growl notifications Backing Up to Disk Images -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

Doskey Singleton MVP Her Independent, Colleges and Knew She Was in Senior Universities of Wisconsin Operate Trouble When She Year
WTG Achievers Vol. 11, No. 4 November 2010 About the WTG Basketball star finds her stride again with WTG The twenty private, or Doskey Singleton MVP her independent, colleges and knew she was in senior universities of Wisconsin operate trouble when she year. And without taxpayer support, but fl unked an informa- thanks to a provide an invaluable public tion technology class suggestion service to the state, educating in her fi rst semester from her more than 60,000 students a at Silver Lake Col- basketball year. Many of Wisconsin’s best lege. coach, Dos- and brightest need financial help key visited to attend the college of their Doskey is the fi rst to Silver Lake. choice. admit that she didn't start out as the best Doskey The State of Wisconsin created student. Attend- joined the Wisconsin Tuition Grant ing three different DoskeyDoskey Singleton,Singleton, Milwaukee,Milwaukee, faced her share of chal-chal- the SLC (WTG) in 1965 to help qualified Milwaukee high lenges as a freshman, but says she’s stronger now. basketball Wisconsin citizens to succeed. schools, she fi nally team last fall, Fully one-third of the low-income found the right fi t at a school I would have never made but the transition to college students who apply for the WTG that helped her integrate her it to college,” Doskey says. wasn’t easy as she struggled are turned away every year studies and life goals. “If At Destiny, Doskey was the academically. “When I was for lack of funds. Each month it wasn’t for Destiny High, school’s leading scorer and continued on page 2 WTG Achievers brings you success stories of Wisconsinites for whom the WTG has made a WTG helps senior “pay it forward” as graduation looms significant difference.