The Android - a Widely Growing Mobile Operating System with Its Mobile Based Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mobile Gaming Victor Bahl 8.13.2012 Internet & Devices Growth (Obligatory Slide)
mobile gaming Victor Bahl 8.13.2012 internet & devices growth (obligatory slide) Apps are ~$10 Billion market, growing at ~100% per year Fun Fact: Getting to 1 M users: AOL: 9 years; Facebook: 9 months; “Draw Something”: 9 days Mobility & Networking, Microsoft Research bandwidth demand! 1 ~ 10 billion mobile devices in 2016 10B (1.4 devices / human) 6B 6 2007 2011 2007 2011 2016 2011-2016 ~ 18X growth in mobile data traffic2 (~ 10 exabytes / month) Source: (1) GSMA; (2) Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2011–2016 Mobility & Networking, Microsoft Research gaming today Source: Strategy Analytics - Apptrax4 Mobility & Networking, Microsoft Research …but you already knew that Some things I heard today: . how game analytics was used to increase dwell time . how in-the-wild user behavior may be modeled (& used) . The challenges in getting to MMOG games . wireless peer-to-peer games . power management by making use of saliency All great stuff, let me say a few words about some things I didn’t hear ….. Mobility & Networking, Microsoft Research services behind the games Fun fact: in 2011 ~$12 billion was spent on social/mobile games in 2015 revenue is projected to be ~24 billion (19% CGR) Apps that connect to backends receive higher rankings and more downloads because they are likely dynamic with more fresh content and are more social and contextual - Kinvey Inc., 2012 Xbox LIVE 30% growth year over year 40+ Million Users 2.1 billion hours played per month 35 Countries 176,802,201,383 Gamer Points scored -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

A Survey Onmobile Operating System and Mobile Networks
A SURVEY ONMOBILE OPERATING SYSTEM AND MOBILE NETWORKS Vignesh Kumar K1, Nagarajan R2 (1Departmen of Computer Science, PhD Research Scholar, Sri Ramakrishna College of Arts And Science, India) (2Department of Computer Science, Assistant Professor, Sri Ramakrishna College Of Arts And Science, India) ABSTRACT The use of smartphones is growing at an unprecedented rate and is projected to soon passlaptops as consumers’ mobile platform of choice. The proliferation of these devices hascreated new opportunities for mobile researchers; however, when faced with hundreds ofdevices across nearly a dozen development platforms, selecting the ideal platform is often met with unanswered questions. This paper considers desirable characteristics of mobileplatforms necessary for mobile networks research. Key words:smart phones,platforms, mobile networks,mobileplatforms. I.INTRODUCTION In a mobile network, position of MNs has been changing due todynamic nature. The dynamic movements of MNs are tracked regularlyby MM. To meet the QoS in mobile networks, the various issuesconsidered such as MM, handoff methods, call dropping, call blockingmethods, network throughput, routing overhead and PDR are discussed. In this paper I analyse the five most popular smartphone platforms: Android (Linux), BlackBerry, IPhone, Symbian, and Windows Mobile. Each has its own set of strengths and weaknesses; some platforms trade off security for openness, code portability for stability, and limit APIs for robustness. This analysis focuses on the APIs that platforms expose to applications; however in practice, smartphones are manufactured with different physical functionality. Therefore certain platform APIs may not be available on all smartphones. II.MOBILITY MANAGEMENT IP mobility management protocols proposed by Alnasouri et al (2007), Dell'Uomo and Scarrone (2002) and He and Cheng (2011) are compared in terms of handoff latency and packet loss during HM. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz-Allen-Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

Detective 11.0 October 2018
OXYGEN FORENSIC® DETECTIVE 11.0 OCTOBER 2018 USE NEW WHATSAPP EXTRACTION METHOD AQCUIRE IOT DEVICES WhatsApp is without doubt the most popular messenger Digital assistants are already a part of everyday life and in the world with over 1.5 billion users globally. Thus, have been successfully used to solve several crimes. extracting complete WhatsApp content from all possible Oxygen Forensic® Detective v.11 brings support for the sources is essential for any investigation. two most popular digital assistants – Amazon Alexa and Google Home. Commonly used methods of WhatsApp data acquisition involve extracting data from mobile devices and their You can access Amazon Alexa cloud using a username cloud backups. Oxygen Forensic® Detective v.11 and password or token. A token can be found on the introduces an industry-first alternative method of device’s associated computer with Oxygen Forensic® WhatsApp data extraction. KeyScout and used in Cloud Extractor. The software acquires a complete evidence set from Amazon Alexa, In the new software version, you can access complete including account and device details, contacts, messages, WhatsApp data by scanning a QR code from a mobile calendars, notifications, lists, activities, skills, etc. app or using the WhatsApp token from a PC. This token can be extracted by our KeyScout utility from the Google Home data can be extracted via Google WhatsApp desktop app or from desktop Web browsers. username/password or a master token found in mobile devices. Extracted Google Home data includes account Once data is extracted, you will be able to download and device details, voice commands, and information WhatsApp communications from the subject’s account about users.Google Home data can also be acquired from any time later when an investigation requires by using a the Google Home mobile app on Apple iOS and Android specially generated WhatsApp QR token available in the devices. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz Allen Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition – Insights and Considerations | 1
MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 1 Introduction A shift in the mobile operating system landscape has occurred over the last several years. The transition from legacy Windows® is well underway. While there remain several distinct choices on the roadmap, the tradeoffs and compromises associated with each have become clearer. This paper will elaborate on these points and provide the reader with guidance on recommended solutions. Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 2 Table of contents 3 Mobile Operating System History 4 Legacy Operating Systems 5 Android Enterprise Evolution 6 How Honeywell Helps 8 Android Lifecycle Management 10 Conclusion and Recommendations Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 3 Mobile Operating System History For the open source Android operating system, Google OEMs and third parties began developing extensions that enabled device management capabilities, provided more control over user actions, and added support for Ten years ago, operating systems for mobile devices in the enterprise space were provided by Microsoft. Windows CE and Windows Mobile (later Windows Embedded Handheld) offered industrial Wi-Fi features and capabilities needed for enterprise deployment, while a robust ecosystem of networks and developer tools and third-party offerings allowed customers to create the solution needed barcode scanning to effectively operate and manage their businesses. Apple had only recently shown the first capabilities. iPhone®. Google acquired Android™ a few years earlier and had yet to see a phone come to market. Other options available at that time were largely focused around the white collar professional user and proved largely unsuitable for the unique needs of the purpose-built enterprise environment. -

The Application of Personal Digital Assistants As Mobile Computing Device on Construction Site
The Application of Personal Digital Assistants as Mobile Computing Device on Construction Site Kenji Kimoto, Kazuyoshi Endo, Satoru Iwashita and Mitsuhiro Fujiwara Konoike Construction Co., Ltd., Research Institute of Technology 1-20-1 Sakura, Tsukuba-Science City, IBARAKI 305-0003, Japan. {kimoto_kj, Iwashita_st, fujiwara_mh}@konoike.co.jp . Kogakuin University, Department of Architecture, 1-24-2 Nishishinjuku, Shinjyuku-ku, TOKYO 163-8677, Japan. [email protected] ABSTRACT: Construction managers need to access the real construction site to manage the construction project. They have recently handled various types of digital information such as drawings, specification, checklists and daily reports. They usually use sheets of paper and/or field notes. As a result, a gap in time and space between the outdoor construction site and the office, which leads to the low efficiency, occurs. This paper reports the application of PDA (Personal Digital Assistants) as mobile computing device for construction managers on construction sites. First, this paper describes the aim and the essential element of the mobile systems. This also shows the analysis of necessary functions as mobile computing device through the discussion with construction managers, and the concept of development of this computer-aided engineering system. Secondly, this paper describes the outline of below subsystems with PDA: Progress Monitoring System, Inspection System and Position Check System. Subsystems have two programs: the data input program in PDA and the output program in PC. Finally, this paper indicates the development of more refined process of construction management with the mobile computing device on construction site. • Progress Monitoring System has been built for construction managers to monitor the progress of works. -
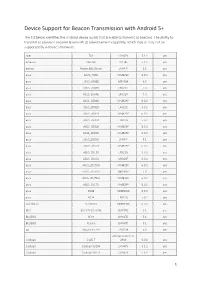
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

ARCHOS Unveils Complete Selection of Connected Objects During CES 2014
ARCHOS presentará una completa selección de Objetos Conectados durante la próxima edición de CES 2014 El ecosistema más amplio de la industria de dispositivos conectados para el hogar y personal estará expuesto en el Hall Central Stand 9844 30 de diciembre de 2013 - ARCHOS, pionero en dispositivos Android™, te invita a estar conectado en cualquier momento y lugar, con la selección más completa de objetos conectados para el hogar y para uno mismo, incluyendo una estación meteorológica, cámara doméstica, registro de actividad, monitor de la presión arterial, smartwatches y mucho más. Aprovechando la amplia experiencia de la empresa en dispositivos móviles y Android, la selección ARCHOS de objetos conectados bien diseñados ofrece una solución asequible con el objetivo de mejorar la conectividad en el hogar y mejorar la salud personal y bienestar. Los dispositivos conectados ARCHOS son compatibles tanto con plataformas Android como iOS, proporcionan monitorización de información en tiempo real desde cualquier lugar y utilizan conectividad Bluetooth de bajo consumo para garantizar un uso prolongado sin necesidad de recarga. Completamente inalámbricos y fáciles de vincular, los dispositivos conectados ARCHOS son miniaturizados y modernos para integrarse en su entorno familiar. "Los dispositivos móviles se han convertido en el centro de nuestra vida y nuestra demanda de acceso instantáneo a la información crea aún más la necesidad de interconectividad", explica Loic Poirier, director general de ARCHOS. "La nueva línea de objetos conectados ARCHOS -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations.