Detective 11.0 October 2018
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

7.5W Fast-Charging Mode and 5W Standard Mode
Before you start: For Anker 7.5W Wireless Chargers This document will help you identify problems and get the most out of your experience with our wireless chargers. It is important to note that although wireless chargers are a transformatively convenient way to charge, they are not yet capable of the charging speeds provided by traditional wired chargers. Attachments (Must-Read!) If you're experiencing interrupted or slow charging, check the following: The back of your phone should not have any metal, pop sockets, or credit cards. Put the phone in the center of the charging surface (this lets the charging coil in your phone line up with the one inside the wireless charger). The wireless charging coil on Sony phones is located slightly below center. Phone cases should be no thicker than 5 mm for effective charging. Choose the correct adapter for your wireless charger: Quick Charge or Power Delivery adapter for Fast Charge Modes. 5V/2A adapter for Standard Charge Mode. Not compatible with 5V/1A adapters. Phone Brands & Power Input For Anker 7.5W Wireless Chargers Apple iPhone X iPhone XS iPhone XS Max iPhone 8 / 8 Plus iPhone XR Two charging modes: 7.5W fast-charging mode and 5W standard mode. For the best results, use a Quick Charge wall charger, desktop charger, car charger, power strip (output power of 9V/2A or 12V/1.5A). For standard 5W charging mode, use with wall chargers, desktop chargers, car chargers, and power strips with an output of 5V/2A or above.Not compatible with the iPhone stock charger (5V/1A). -

MPP System Control Module User Guide /V1.0 Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni
nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni MPP System Control Module User Guide /V1.0 nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Document version:V1.0 Release Date:2017.4.13 nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Copyright © Zhuhai Allwinner Technology Co., Ltd. 2018. All rights reserved. No part or all of the contents of this document may be copied or reproduced without the written permission of the company, and may not be used.What form of communication. nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Trademark statement 、Allwinner and other Allwinner trademarks are trademarks of Zhuhai Allwinner Technology Co., Ltd.All other trademarks or registered trademarks mentioned in this document are the property of their respective owners. Note The products, services or features you purchase are subject to the terms and conditions of the company and all or part of the products, services or features described in this document may not be covered by your purchase or use. Unless otherwise agreed by the contract, Allwinner Company makes no representations or warranties, nulllindeni expressnulllindenior implied, regarnulllindeniding the contentsnulllindeniof this document.nulllindeni nulllindeni nulllindeni nulllindeni The contents of this document -

Lista Device Compatibili.Xlsx
Android iOS (Cloud Anchors Only) iOS Acer Chromebook Tab 10 [1] iPhone XR iPhone XS ROG Phone iPhone XS and XS Max iPhone XS Max Zenfone 6 iPhone X iPhone XR Asus Zenfone AR iPhone 8 and 8 Plus iPhone X iPhone Zenfone ARES iPhone 7 and 7 Plus iPhone 8 General GM 9 Plus iPhone 6S and 6S Plus iPhone 8 Plus Mobile Nexus 5X [2] iPhone SE iPhone 7 Nexus 6P [3] Pixel, Pixel XL Google Pixel 2, Pixel 2 XL Pixel 3, Pixel 3 XL Pixel 3a, Pixel 3a XL Nokia 6 (2018) [4] Nokia 6.1 Plus Nokia 7 Plus HMD Nokia 7.1 Global Nokia 8 [5] Nokia 8 Sirocco Nokia 8.1 Honor 8X, Honor 10 Honor View 10 Lite Honor V20 Mate 20 Lite, Mate 20, Mate 20 Pro, Mate 20 X Nova 3, Nova 3i Huawei Nova 4 P20, P20 Pro P30, P30 Pro Porsche Design Mate RS, Porsche Design Mate 20 RS Y9 2019 G6 [6] G7 Fit, G7 One, G7 ThinQ [7] G8 ThinQ [8] Q6 Q8 LG V30, V30+, V30+ JOJO, LG Signature Edition 2017 [9] V35 ThinQ, LG Signature Edition 2018 [10] V40 ThinQ V50 ThinQ [11] Moto G5S Plus Moto G6, Moto G6 Plus Moto G7, Moto G7 Plus, Moto G7 Power, Moto G7 Play Motorola Moto One, Moto One Power Moto X4 [12] Moto Z2 Force [13] Moto Z3, Moto Z3 Play OnePlus 3T [14] OnePlus 5, OnePlus 5T OnePlus OnePlus 6, OnePlus 6T OnePlus 7, OnePlus 7 Pro, OnePlus 7 Pro 5G R17 Pro Oppo Reno 10x Zoom Galaxy A3 (2017) [15] Samsung Galaxy A5 (2017) Android iOS (Cloud Anchors Only) iOS Galaxy A6 (2018) Galaxy A7 (2017) Galaxy A8, Galaxy A8+ (2018) Galaxy A30, Galaxy A40, Galaxy A50, Galaxy A60, Galaxy A70, Galaxy A80 Galaxy J5 (2017), Galaxy J5 Pro [16] Galaxy J7 (2017), Galaxy J7 Pro [17] Galaxy Note8 Galaxy Note9 -

ZS673KS User Guide E17161 April 2021 First Edition
ROG PHONE ZS673KS User Guide E17161 April 2021 First Edition Care and safety Guidelines Road safety comes first. We strongly recommend not to use your device when driving or operating any type of vehicle. This device should only be used in environments with ambient temperatures between 0°C (32°F) and 35°C (95°F). Turn off your device in restricted areas where the use of mobile devices is prohibited. Always obey rules and regulations when in restricted areas, such as, in aircraft, movie theater, in hospitals or near medical equipment, near gas or fuel, construction sites, blasting sites and other areas. Use only AC adapters and cables approved by ASUS for use with this device. Refer to the rating label on the bottom of your device and ensure that your power adapter complies with this rating. Do not use damaged power cables, accessories, and other peripherals with your device. Keep your device dry. Do not use or expose your device near liquids, rain, or moisture. You can put your device through x-ray machines (such as those used in conveyor belts for airport security), but do not expose the device to magnetic detectors and wands. The device screen is made of glass. If the glass gets broken, stop using the device and do not touch the broken glass parts. Immediately send device for repair to ASUS-qualified service personnel. Do not listen at high volume levels for long periods to prevent possible hearing damage. Disconnect the AC power before cleaning your device. Use only a clean cellulose sponge or chamois cloth when cleaning your device screen. -

(Step) Green Paper
10 April 2013 Solving the E-Waste Problem (StEP) Green Paper E-waste Country Study Ethiopia Andreas Manhart, Öko-Institut e.V. Tadesse Amera, PAN Ethiopia Mehari Belay, PAN Ethiopia ISSN: 2219-6579 (Online) ISSN: 2219-6560 (In-Print) Solving the E-Waste Problem (StEP) Initiative Green Paper 0 E-waste Country Study Ethiopia United Nations University/StEP Initiative 2013 This work is licensed under the Creative Commons by-nc-nd License. To view a copy of this license, please visit http://creativecommons.org/licenses/by-nc-nd/3.0/ This publication may thus be reproduced in whole or in part and in any form for educational or non-profit purposes without special permission from the copyright holder, provided acknowledgement of the source is made. No use of this publication may be made for resale or for any other commercial purpose whatsoever without prior permission in writing from the StEP Initiative/United Nations University. The StEP Initiative/United Nations University would appreciate receiving a copy of any pub- lication that uses this publication as a source. Disclaimer StEP Green Paper Series The StEP Green Paper Series is a publication tool for research findings which meet the core principles of StEP and contribute to its objectives towards solving the e-waste prob- lem. StEP members agreed on this support of the author(s) work, but do not necessarily endorse the conclusions made. Hence, StEP Green Papers are not necessarily reflecting a common StEP standpoint. The StEP Green Paper series is published complimentary to the StEP White Paper Series for publication of findings generated within StEP which have been endorsed by its mem- bers. -
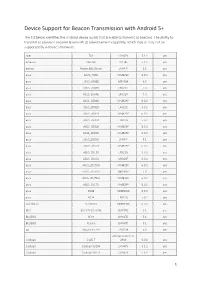
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Passmark - Android Device List
PassMark - Android Device List https://www.androidbenchmark.net/device_list.php AndroidTM Benchmarks Performance Comparison of Android Devices Below is an alphabetical list of all Android device types that appear in the charts. Clicking on a specific device name will take you to the charts where it appears in and will highlight it for you. PassMark Rating CPUMark Rating PassMark Rank Android Device Type Samples (higher is better) (higher is better) (lower is better) 4G R17S 1,572 4,088 1253 1 A-gold BV9500Plus 5,052 13,068 375 1 A-gold BV9800 4,450 11,400 487 1 A-gold F1 4,237 10,869 531 7 A-gold S3_Pro 4,392 11,219 504 2 A-gold Z2_PRO 4,406 11,246 499 1 A1 Alpha 20+ 4,753 12,266 435 1 Acer A3-A40 1,982 5,269 1082 1 Acer AO722 519 1,272 1725 1 1 z 62 2020-10-14, 12:02 PassMark - Android Device List https://www.androidbenchmark.net/device_list.php PassMark Rating CPUMark Rating PassMark Rank Android Device Type Samples (higher is better) (higher is better) (lower is better) AGM A10 2,030 8,521 1066 1 ALCATEL A574BL 497 1,202 1736 1 AlcatelOneTouch Alcatel_5044R 438 1,129 1759 1 Alco CT9223W97 1,214 3,111 1384 1 ALLDOCUBE M8 2,730 7,274 882 5 ALLDOCUBE T701 1,092 4,554 1437 1 ALLDOCUBE U1006H 1,902 4,931 1125 1 ALLVIEW P7_PRO 1,691 4,543 1210 1 ALLVIEW X4_Soul 2,536 6,938 925 1 Alps Acer One 8 T4-82L 2,539 6,526 924 1 Alps Tablet18T 1,201 3,043 1394 1 Alps tb8788p1_64_bsp 2,343 5,784 983 2 Amazon KFKAWI 712 1,701 1589 4 Amazon KFMAWI 2,306 5,640 992 19 Amazon KFONWI 1,082 2,588 1442 3 Amlogic A95X-A3 1,228 3,182 1381 1 Amlogic ABOX A4 397 -

ARCHOS Unveils Complete Selection of Connected Objects During CES 2014
ARCHOS presentará una completa selección de Objetos Conectados durante la próxima edición de CES 2014 El ecosistema más amplio de la industria de dispositivos conectados para el hogar y personal estará expuesto en el Hall Central Stand 9844 30 de diciembre de 2013 - ARCHOS, pionero en dispositivos Android™, te invita a estar conectado en cualquier momento y lugar, con la selección más completa de objetos conectados para el hogar y para uno mismo, incluyendo una estación meteorológica, cámara doméstica, registro de actividad, monitor de la presión arterial, smartwatches y mucho más. Aprovechando la amplia experiencia de la empresa en dispositivos móviles y Android, la selección ARCHOS de objetos conectados bien diseñados ofrece una solución asequible con el objetivo de mejorar la conectividad en el hogar y mejorar la salud personal y bienestar. Los dispositivos conectados ARCHOS son compatibles tanto con plataformas Android como iOS, proporcionan monitorización de información en tiempo real desde cualquier lugar y utilizan conectividad Bluetooth de bajo consumo para garantizar un uso prolongado sin necesidad de recarga. Completamente inalámbricos y fáciles de vincular, los dispositivos conectados ARCHOS son miniaturizados y modernos para integrarse en su entorno familiar. "Los dispositivos móviles se han convertido en el centro de nuestra vida y nuestra demanda de acceso instantáneo a la información crea aún más la necesidad de interconectividad", explica Loic Poirier, director general de ARCHOS. "La nueva línea de objetos conectados ARCHOS -
Asus Google Nexus 7 Inch 32Gb Android 4 1 Black Tablet User Guides
Asus google nexus 7 inch 32gb android 4 1 black tablet User Guides Asus google nexus 7 inch 32gb android 4 1 black tablet . Asus google nexus 7 inch 32gb android 4 1 black tablet Staples. has the NEW 2013 Nexus 7 16GB Tablet from Google you need for home life for web browsing, video playback or reading with the 4.2V1 Li-Pllyner battery Google Nexus 7 Tablet, 32GB (NEXUS7ASUS-2B32): 4.5stars: (213reviews) Reviews for Case Logic 7 Tablet Sleeve, Black: 5.0stars: (1 reviews). Google Nexus 7 Tablet (7-Inch, 32GB, Black) by ASUS click the link in the description. ASUS Google Nexus 7 Tablet 32GB - HSPA+ Unlocked (ASUS-1B32-4G) 4 out of 5 eggs Quad Core CPU/GPU, 1GB DDR3 RAM, 32GB Flash Storage, 7 Touchscreen (1280x800), Android 4.1 Battery Life: 9 hours of HD video playback Limited Warranty period (parts): 1 year, Limited Warranty period (labor): 1 year. ASUS Google Nexus 7 7 32 GB Android 4.4 KitKat Wi-Fi Tablet - BLACK in Patented 4-PLUS-1 design gives you processing power when you need it, and battery of HD movies and TV shows, and the latest magazines on Nexus 7. ATC Slim Cover Case for Google Nexus 7 Android Tablet by Asus (Black) with Save 5% on PU Leather Nexus 7 2nd case Black/White when you purchase 1 or more ASUS Google Nexus 7 Tablet (7-Inch, 32GB) 2012 Model $135.38. Running on the Android 4.3 operating system, youll enjoy stunning HD video and Google Nexus 7 FHD by ASUS 32GB 7 Android 4.3 Tablet With Qualcomm Snapdragon S4 Pro - Black Review: The Nexus 7 2013 Tablet from Google and Asus In fact, last Christmas I bought one for myself and one for my wife. -

ASUS A002 2 Asus Zenfone AR ASUS A002 1 Asus Zenfone AR (ZS571KL) ASUS A002
FAQ for Toyota AR MY (iOS and Android) Q1. What types of devices are required to operate Toyota AR MY? A1. Toyota AR MY requires the latest high-end Apple and Android mobile devices with ARKit and ARcore to operate smoothly. Q2. What types of Apple devices can support Toyota AR MY? A2. The Apple iPhone (iPhone 6S and above), iPhone SE, iPad Pro (2nd Generation and above) and iPad (5th Generation and above). Q3. What types of Android mobile devices support Toyota AR MY? A3. Android devices such as AndroidOS 8 and above support the AR core framework. Other supporting Android devices are listed as below: Manufacturer Model Name Model Code Asus ROG Phone ASUS_Z01QD_1 Asus ZenFone Ares (ZS572KL) ASUS_A002_2 Asus ZenFone AR ASUS_A002_1 Asus ZenFone AR (ZS571KL) ASUS_A002 Manufacturer Model Name Model Code Google Pixel 3 blueline Google Pixel sailfish Google Pixel 2 walleye Google Pixel XL marlin Google Pixel 3 XL crosshatch Google Pixel 2 XL taimen Manufacturer Model Name Model Code Huawei Honor 8X HWJSN-H Huawei Honor 8X Max HWJSN-HM Huawei P20 Pro HWCLT Huawei P20 Pro HW-01K Huawei Honor 10 HWCOL Huawei P20 lite HWANE Huawei Nexus 6P angler Huawei Mate 20 X HWEVR Huawei Mate 20 Pro HWLYA Huawei nova 3 HWPAR Huawei Honor Magic 2 HWTNY Huawei HUAWEI Y9 2019 HWJKM-H Huawei Mate 20 HWHMA Huawei Mate 20 lite HWSNE Huawei nova 3i HWINE Manufacturer Model Name Model Code LG Electronics Q8 anna LG Electronics Q8 cv7an LG Electronics G7 One phoenix_sprout LG Electronics LG G6 lucye LG Electronics JOJO L-02K LG Electronics LG G7 ThinQ judyln LG Electronics -

042Cf377-Ed0c-4715-9260-770F680082fc.Pdf
WiFi Tablets 70 Neon + The ARCHOS 70 Neon Plus is one of the most affordable tablets on the market. It includes a powerful quad-core processor running the latest Android operating system: Android™ 5.1 Lollipop®. The 7-inch IPS display provides incredible colors and wide viewing angles, perfect for enjoying your content on-the-go. The ARCHOS 70 Neon Plus is designed to offer a unique multimedia experience. AndroidTM 5.1, Lollipop® Android™ 5.1, “Lollipop” 7” IPS Capacitive Screen 1024x 600 pixels Rockchip 3126 Quad-Core CPU @ 1.3 GHz 1 GB RAM 8 GB flash memory (+ microSD slot) GB Micro SD Wifi WiFi, dual cameras, micro USB host, G-sensor, speaker... 8 4 5 90b Neon Featuring a powerful 1.2 GHz Quad-core processor and Dual-core graphics processor, the ARCHOS 90b Neon has a super smooth interface. At an affordable price, the ARCHOS 90b Neon delivers an amazing experience to meet all your needs: emails, movies, photos, web browsing… Android™ 4.4, “Kitkat” 9” Capacitive Screen 1024 x 600 pixels All Winner A33 Quad-Core CPU @ 1.2 GHz 512 MB RAM 8 GB flash memory (+ microSD slot) GB Wifi WiFi, dual cameras, micro USB host, G-sensor, 8 speaker... 6 7 101d Neon A mix between large screen and productivity, the ARCHOS 101d Neon includes a large 10.1” screen and ARCHOS media applications, perfect for your multimedia, wherever you are. Featuring a powerful Quad-core processor and Quad-core graphics processor, the ARCHOS 101d Neon offers a super smooth interface for an affordable price and delivers an amazing experience to meet all your needs. -

CHINA DAILY for Chinese and Global Markets
OLD MOBILES CHANCE RELATIONS LOTUS FROM SPACE Outlining the high stakes Flower seeds made Showroom opening to attract > p13 in future China-US ties a tour beyond Earth buyers of hand-assembled cars > ACROSS AMERICA, PAGE 2 > CHINA, PAGE 7 WEDNESDAY, June 19, 2013 chinadailyusa.com $1 The ‘Long March’ to Tinseltown By LIU WEI in shanghai “It is a long way to go,” he [email protected] says, “but I believe as the Chi- nese = lm market keeps growing The next Kung Fu Panda so fast, it is totally possible that will be the brainchild of both Chinese capital will hold shares American and Chinese film- in the major six Hollywood stu- makers and production will dios. It is just a matter of time.” start in August, says Peter Li, China’s Wanda Cultural managing director of China Group is one of the pioneers Media Capital, co-investor of in this process. In 2012 Wanda Oriental DreamWorks, a joint acquired AMC, the second venture with DreamWorks largest theater chain in North Animation. America, for $2.6 billion. CMC co-founded Oriental What Ye Ning, the group’s DreamWorks in 2012 with vice-president, has learned DreamWorks, Shanghai Media from the following integration Group and Shanghai Alliance is, = rst of all, trust and respect. Investment, with the aim of “The managing team of CHARACTER BUILDING producing and distributing ani- AMC was worried that we mated and live-action content would send a group of yellow PHOTO BY SUN CHENBEI / CHINA DAILY for Chinese and global markets. faces to replace them,” Ye says, From le : Li Xiaolin, president